What happens when Microsoft accidentally gives BUILTIN\Users the ability to read the Windows 10 SAM:
Mimikatz lsadump::sam as a non-admin user, for example.
Some installs off of very-recent ISO builds are not vulnerable. But assume you are vulnerable until you prove otherwise.
Mimikatz lsadump::sam as a non-admin user, for example.
Some installs off of very-recent ISO builds are not vulnerable. But assume you are vulnerable until you prove otherwise.

What makes things tricky here is now where you are, but how you got there. e.g.
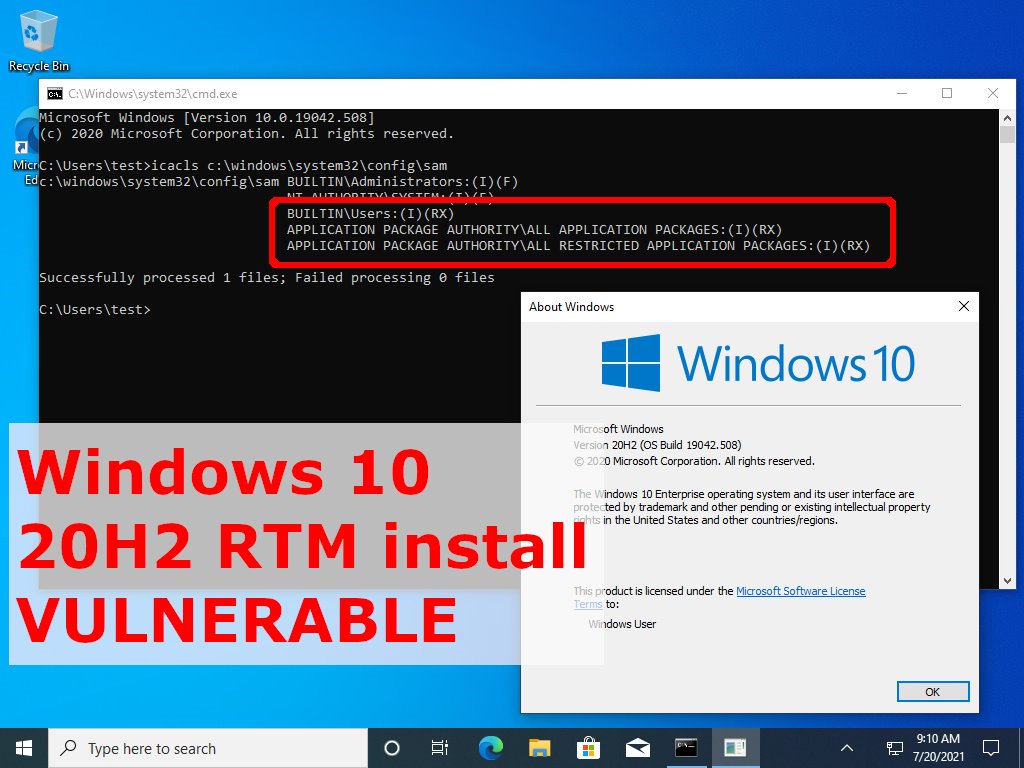
Windows 10 20H2 RTM install: VULNERABLE
Windows 10 20H2 RTM install + Windows Update: VULNERABLE
20H2 November install - NOT VULNERABLE
Do you remember which install media you used to get Windows 10?


Windows 10 20H2 RTM install: VULNERABLE
Windows 10 20H2 RTM install + Windows Update: VULNERABLE
20H2 November install - NOT VULNERABLE
Do you remember which install media you used to get Windows 10?


But wait... 21H1 came out after 20H2 November update, right?
Both the 21H1 RTM install and the 21H1 June-update install are both vulnerable.
There may be some non-vulnerable Win10 installs out there, but I fail to find logic behind it.
Maybe it's accidentally fixed in some cases?

Both the 21H1 RTM install and the 21H1 June-update install are both vulnerable.
There may be some non-vulnerable Win10 installs out there, but I fail to find logic behind it.
Maybe it's accidentally fixed in some cases?


I don't predict myself making a flowchart to give you an answer to whether or not you're vulnerable, as there seem to be too many variables.
Just check for yourself to be sure!
I've published VU#506989 on this issue:
kb.cert.org/vuls/id/506989
Just check for yourself to be sure!
I've published VU#506989 on this issue:
kb.cert.org/vuls/id/506989
• • •
Missing some Tweet in this thread? You can try to
force a refresh