(1/2) TL;DR "DLL sideloading attack is the most successful
attack as most EDRs fail to detect, let alone block, it." A scholarly and unbiased examination of how top EDR detects APT threats by @MDPIOpenAccess mdpi.com/2624-800X/1/3/…
attack as most EDRs fail to detect, let alone block, it." A scholarly and unbiased examination of how top EDR detects APT threats by @MDPIOpenAccess mdpi.com/2624-800X/1/3/…
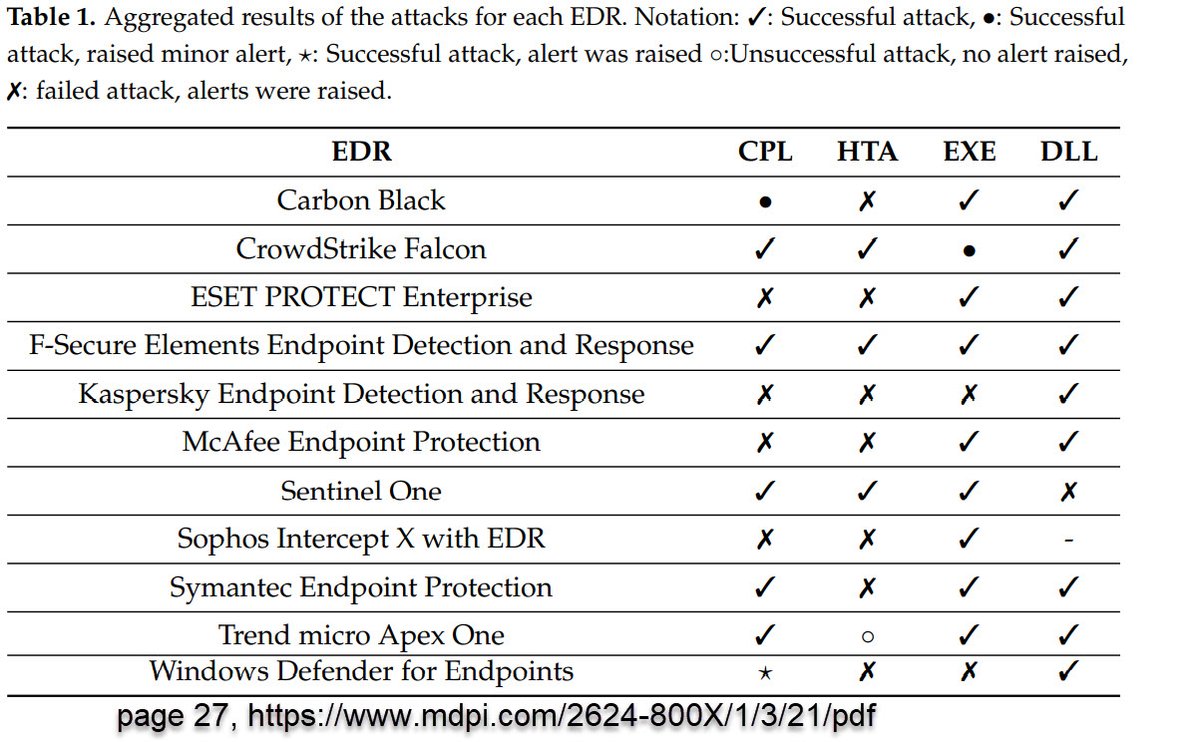
It would be cool if EDR had network-based UEBA to detect these anomalous egress network connections. While some network gateways offer this, it would be more beneficial to have it detected at endpoint due to #WorkFromHome
• • •
Missing some Tweet in this thread? You can try to
force a refresh