
Here are few more details/thoughts of mine about Stark, Parrot and their relation with modern Apple Watch interfacing
@zhuowei found out that Stark is ST60A3, a wireless USB chip used since Series 6
And I posses 2 boards that know (and can handle?) these technologies...
@zhuowei found out that Stark is ST60A3, a wireless USB chip used since Series 6
And I posses 2 boards that know (and can handle?) these technologies...
https://twitter.com/zhuowei/status/1448484147274649613
First of all, I've already showcased Koko
Today I'm also disclosing few new details about Needle:
It's not recognized by Astris, but it provides VCP interface with a menu similar to Koko's - with "parrot" and "stark" commands
(Thanks @_cc999 for both)



Today I'm also disclosing few new details about Needle:
It's not recognized by Astris, but it provides VCP interface with a menu similar to Koko's - with "parrot" and "stark" commands
(Thanks @_cc999 for both)
https://twitter.com/nyan_satan/status/1434916033203212292
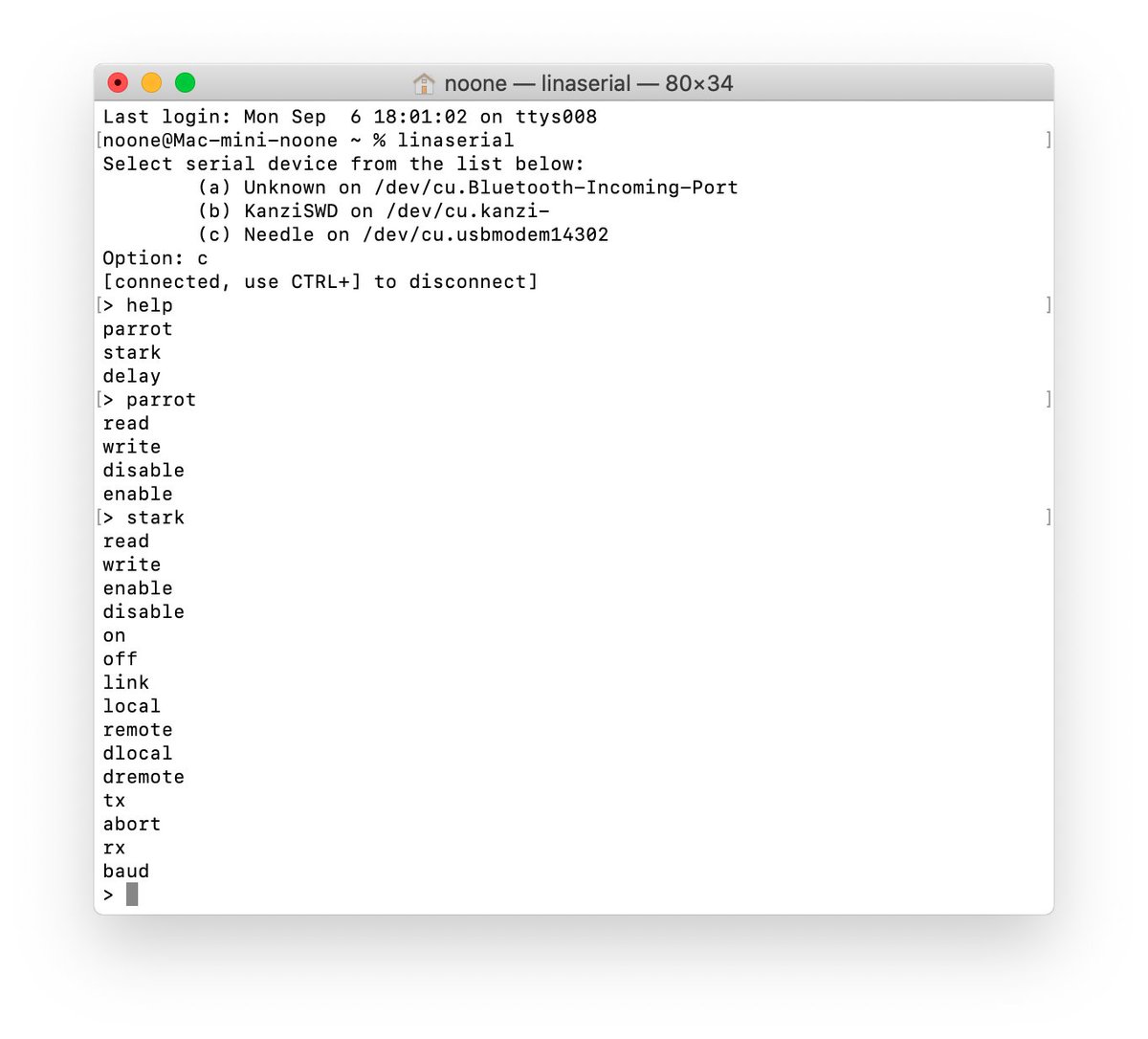


Now we know what Stark is
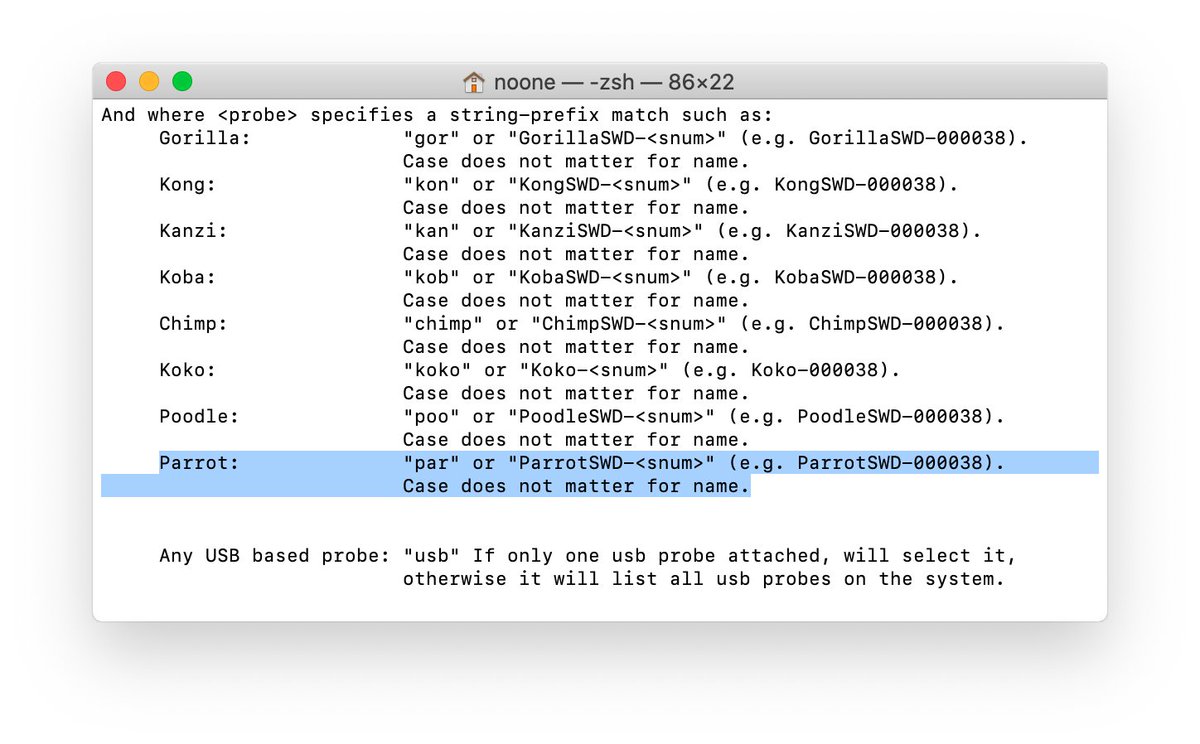
But what's Parrot? There's a probe called "ParrotSWD", which has been supported by Astris for quite a while. And more than a year ago I heard a rumor that it's a wireless probe!
It all (slowly) comes together, doesn't it?
But what's Parrot? There's a probe called "ParrotSWD", which has been supported by Astris for quite a while. And more than a year ago I heard a rumor that it's a wireless probe!
It all (slowly) comes together, doesn't it?
• • •
Missing some Tweet in this thread? You can try to
force a refresh











