
[thread 🧵] Kerberos basics & (ab)use of Certificates within Active Directory (i.e. AD CS and PKINIT)
- Kerberos 101
- Pass-the-Certificate
- UnPAC-the-Hash
- Shadow Credentials
- AD CS escalation (ESC1 to ESC8)
(Links and credits at the end)
- Kerberos 101
- Pass-the-Certificate
- UnPAC-the-Hash
- Shadow Credentials
- AD CS escalation (ESC1 to ESC8)
(Links and credits at the end)
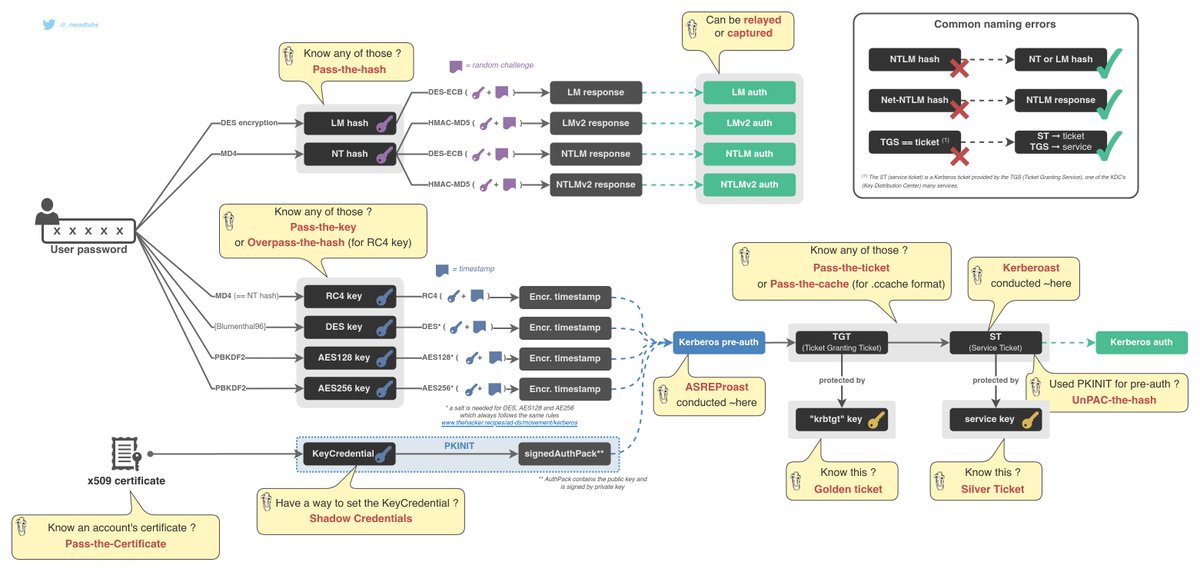
[Kerberos 101 ⬇️]
AD-DS offer two main auth protocols: NTLM and Kerberos. Kerberos works with tickets in order to authenticate a user.
A TGT (Ticket Granting Ticket) can be used to obtain a Service Ticket. A Service Ticket can be used to access a service. This is how it works.
AD-DS offer two main auth protocols: NTLM and Kerberos. Kerberos works with tickets in order to authenticate a user.
A TGT (Ticket Granting Ticket) can be used to obtain a Service Ticket. A Service Ticket can be used to access a service. This is how it works.
1. User requests a TGT (Ticket Granting Ticket)
2. Domain Controller requires pre-authentication
3. User pre-auths and receives a TGT
4. User requests a Service Ticket and gives his TGT
5. DC sends the Service Ticket
6. User can now use the ST and access a service
2. Domain Controller requires pre-authentication
3. User pre-auths and receives a TGT
4. User requests a Service Ticket and gives his TGT
5. DC sends the Service Ticket
6. User can now use the ST and access a service

Let's focus on how pre-auth works.
2. DC requires pre-auth
2.a. Users sends an timestamp, encrypted with on of his Kerberos keys (DES, RC4, AES128 or AES256)
2.a. Alternatively, the user can "use a certificate" (sends a public key, signed by the private key.)
2. DC requires pre-auth
2.a. Users sends an timestamp, encrypted with on of his Kerberos keys (DES, RC4, AES128 or AES256)
2.a. Alternatively, the user can "use a certificate" (sends a public key, signed by the private key.)
TL;DR: Kerberos pre-authentication can be symmetric (Kerberos key derived from password) or asymmetric (public & private key pair --> x509 certificate).
Kerberos asymmetric pre-auth is called PKINIT
Kerberos asymmetric pre-auth is called PKINIT

If an attacker knows a user's Kerberos key, he can do some "pass-the-key" to authenticate.
In NTLM, if an attacker knows a user's NT or LM hash, he can do some "pass-the-hash" to authenticate.
In NTLM, if an attacker knows a user's NT or LM hash, he can do some "pass-the-hash" to authenticate.
Back to Kerberos, if an attacker knows a user's RC4 Kerberos key, which is in fact an NT hash, the attacker will "overpass-the-hash".
If an attacker knows a user's TGT or Service ticket, he will "pass-the-ticket"
[Kerberos 101 ☑️]
If an attacker knows a user's TGT or Service ticket, he will "pass-the-ticket"
[Kerberos 101 ☑️]
[Pass-the-Certificate ⬇️]
If an attacker knows a user's x509 Certificate (or public/private key pair), I dub that "pass-the-certificate".
[Pass-the-Certificate ☑️]
If an attacker knows a user's x509 Certificate (or public/private key pair), I dub that "pass-the-certificate".
[Pass-the-Certificate ☑️]

[UnPAC-the-Hash ⬇️]
When using validating Kerberos pre-auth asymmetrically (PKINIT), attackers can recover the user's LM or NT hash. This is UnPAC-the-Hash.
"It's a feature not a vuln" because it indirectly brings support for Certificates with NTLM.
[UnPAC-the-Hash ☑️]
When using validating Kerberos pre-auth asymmetrically (PKINIT), attackers can recover the user's LM or NT hash. This is UnPAC-the-Hash.
"It's a feature not a vuln" because it indirectly brings support for Certificates with NTLM.
[UnPAC-the-Hash ☑️]
[Shadow Credentials ⬇️]
We now what we can do with certificates, but how can we obtain those.
In short, if an attacker has control over an AD principal able to edit another's msDs-KeyCredentialLink (KCL) attribute, he can gain control over that user or computer principal
We now what we can do with certificates, but how can we obtain those.
In short, if an attacker has control over an AD principal able to edit another's msDs-KeyCredentialLink (KCL) attribute, he can gain control over that user or computer principal
1. the attacker creates a public & private key pair and generates a x509 certificate from those
2. the attacker creates a specific binary structure containing the cert's infos and public key.
3. that structure is added to the target's KCL attribute
4. pass-the-certificate
2. the attacker creates a specific binary structure containing the cert's infos and public key.
3. that structure is added to the target's KCL attribute
4. pass-the-certificate
Shadow Credentials is an Access Control (DACLs/ACEs) abuse scenario. It allows for lateral movement and account persistence.
[Shadow Credentials ☑️]
[Shadow Credentials ☑️]
[AD CS escalation ⬇️]
A legitimate way accounts rely on for obtaining certificates is Active Directory Certificate Services (Microsoft's PKI implementation, often enabled and used within orgs IT)
This set of services is dense and extends the attack surface
A legitimate way accounts rely on for obtaining certificates is Active Directory Certificate Services (Microsoft's PKI implementation, often enabled and used within orgs IT)
This set of services is dense and extends the attack surface
AD CS is subject to many theft, escalation and persistence vectors. Let's focus on the escalation vectors here. The OG researchers (credits & resources at the end) identified 8 vectors and dubbed them from ESC1 to ESC8.
Escalation vectors identified on:
- misconfigured certificate templates (ESC1 to ESC3)
- dangerous CA configuration (ESC6)
- access control vulnerabilities (ESC4, ESC5, ESC7)
- NTLM relay vulnerability related to the web endpoints of AD CS (ESC8)
- misconfigured certificate templates (ESC1 to ESC3)
- dangerous CA configuration (ESC6)
- access control vulnerabilities (ESC4, ESC5, ESC7)
- NTLM relay vulnerability related to the web endpoints of AD CS (ESC8)

Simply put, those escalation vectors mostly allow attackers to obtain a certificate for another account. Attackers can then take control over the other account with Pass-the-Certificate + UnPAC-the-hash
(Attackers can combine Pass-the-Certificate with S4U2Self to gain access to the target account's services (or host).)
AD CS presents an enormous attack surface that tends to be very vulnerable.
[AD CS escalation ☑️]
[AD CS escalation ☑️]
[The Hacker Recipes 🧑🍳]
Want to know more and have practical abuse info?
- Pass-the-Certificate thehacker.recipes/ad/movement/ke…
- UnPAC-the-Hash thehacker.recipes/ad/movement/ke…
- Shadow Credentials thehacker.recipes/ad/movement/ke…
- AD CS escalation thehacker.recipes/ad/movement/ad…
Want to know more and have practical abuse info?
- Pass-the-Certificate thehacker.recipes/ad/movement/ke…
- UnPAC-the-Hash thehacker.recipes/ad/movement/ke…
- Shadow Credentials thehacker.recipes/ad/movement/ke…
- AD CS escalation thehacker.recipes/ad/movement/ad…
- AD CS escalation
---> ESC1,2,3 - misconfigured certificate templates thehacker.recipes/ad/movement/ad…
---> ESC6 - dangerous CA configuration thehacker.recipes/ad/movement/ad…
---> ESC4,5,6 - access control vulnerabilities thehacker.recipes/ad/movement/ad…
---> ESC8 - web endpoints thehacker.recipes/ad/movement/ad…
---> ESC1,2,3 - misconfigured certificate templates thehacker.recipes/ad/movement/ad…
---> ESC6 - dangerous CA configuration thehacker.recipes/ad/movement/ad…
---> ESC4,5,6 - access control vulnerabilities thehacker.recipes/ad/movement/ad…
---> ESC8 - web endpoints thehacker.recipes/ad/movement/ad…
[credits ⭐️]
Let's combine crediting and #FF
You all need to follow these MVPs
@harmj0y @tifkin_ @iansus @gentilkiwi @_dirkjan @ExAndroidDev @MGrafnetter @elad_shamir @_wald0 @podalirius_ and many other researchers and contributors that I'm probably forgetting
Let's combine crediting and #FF
You all need to follow these MVPs
@harmj0y @tifkin_ @iansus @gentilkiwi @_dirkjan @ExAndroidDev @MGrafnetter @elad_shamir @_wald0 @podalirius_ and many other researchers and contributors that I'm probably forgetting
I hope you like reading this thread.
Something's wrong? Have any question? comments and DMs are welcome :)
Next thread incoming on Kerberos delegation 🐕🦺
Something's wrong? Have any question? comments and DMs are welcome :)
Next thread incoming on Kerberos delegation 🐕🦺
• • •
Missing some Tweet in this thread? You can try to
force a refresh




