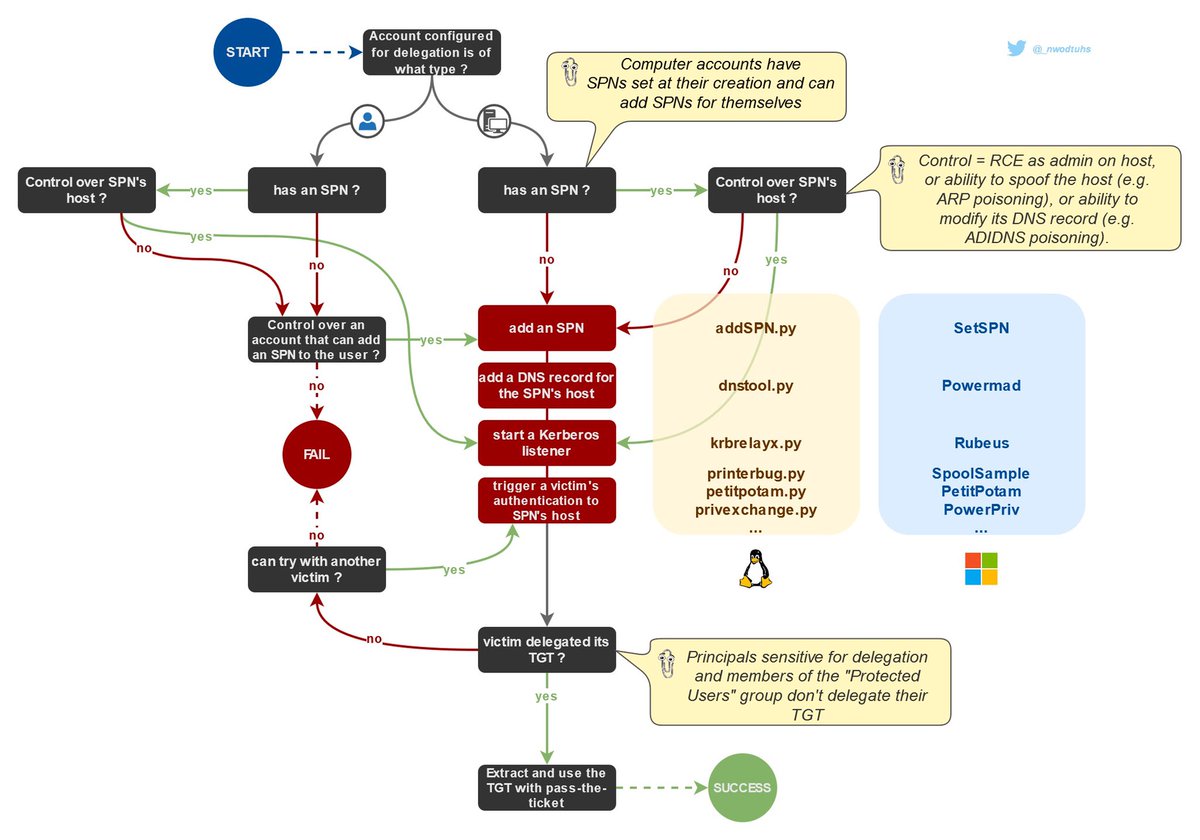
User granted with the SeEnableDelegationPrivilege right in the domain (really high priv ⚠️) can configure service accounts for delegation (unconstrained or constrained).
If an attacker owns a service account configured for Unconstrained Delegation, escalation to domain ad rights is almost guaranteed. The service account can act on behalf of any* other AD principal on any service.
*Principals « sensitive for delegation » or member of the « Protected Users » group cannot be delegated
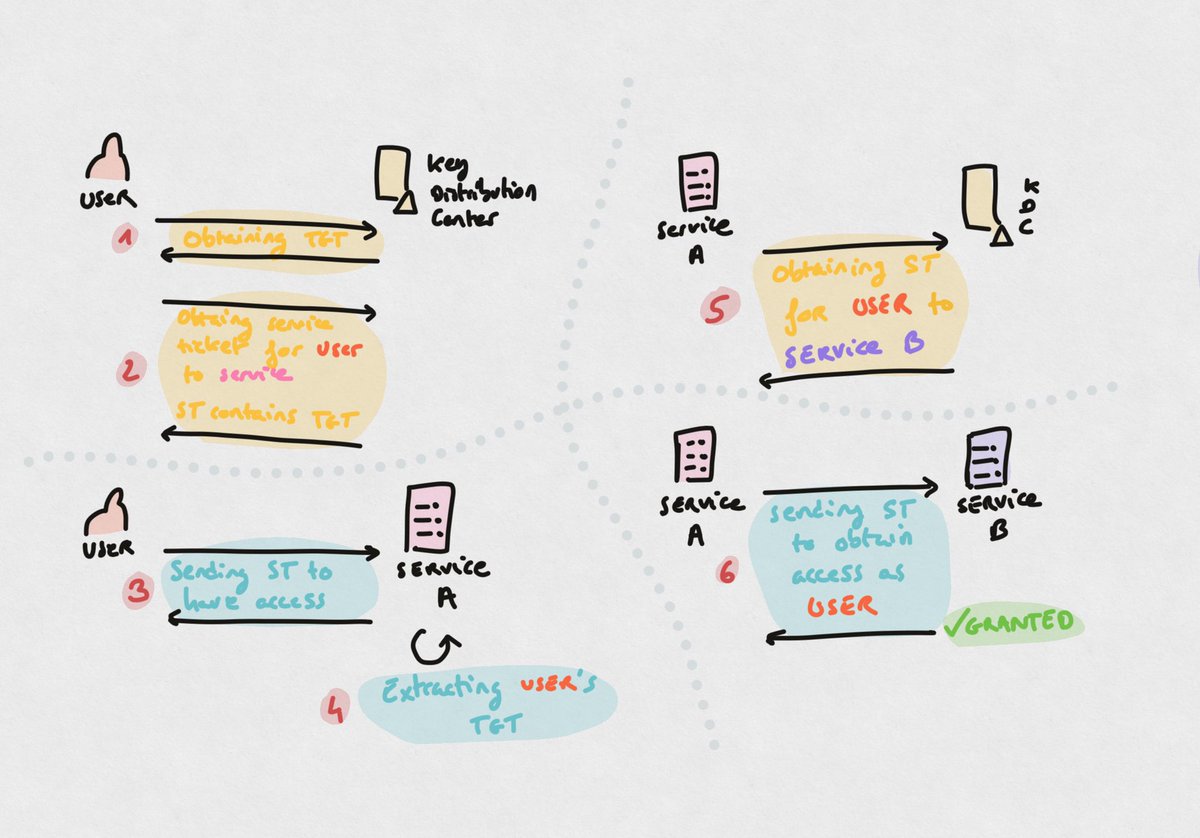
This is how KUD works
1. Service configured for KUD receives is accessed by a user
2. The user sent his Service Ticket in order to have access
3. The ST included the user’s own TGT because the target service was configured for KUD. We say the user « delegated his TGT »
1. Service configured for KUD receives is accessed by a user
2. The user sent his Service Ticket in order to have access
3. The ST included the user’s own TGT because the target service was configured for KUD. We say the user « delegated his TGT »
Now how can we abuse this? We need control over the KUD service (service A) in the drawing above. But what does « control over » mean?
Kerberos delegations can only be possible from accounts that have at least one SPN, and we need control over one of the account’s SPNs’ host part.
Let’s say serviceA has the cifs/serviceA.domain.local SPN, we need to control the « serviceA.domain.local » machine
Let’s say serviceA has the cifs/serviceA.domain.local SPN, we need to control the « serviceA.domain.local » machine
An alternative is to add an SPN to serviceA, pointing to our own attacker machine: cifs/attacker.domain.local.
In order to achieve this, we need enough privileges to add the SPN, and a way to make the SPN’s host part resolve to the attacker’s IP address (e.g. ADIDNS poisoning)
In order to achieve this, we need enough privileges to add the SPN, and a way to make the SPN’s host part resolve to the attacker’s IP address (e.g. ADIDNS poisoning)
Attackers will then need to capture Service Tickets, extract the TGT delegated in it, and use the TGT with pass-the-ticket to access other resources.
This can be achieved with Rubeus or krbrelayx.
Here are more practical info on this thehacker.recipes/ad/movement/ke…
This can be achieved with Rubeus or krbrelayx.
Here are more practical info on this thehacker.recipes/ad/movement/ke…
• • •
Missing some Tweet in this thread? You can try to
force a refresh