
#CommunityAlert 🚨
@FlurryFi’s Vault contracts were attacked leading to around $293K worth of assets being stolen from Vault contracts
Incident Analysis 👇
@FlurryFi’s Vault contracts were attacked leading to around $293K worth of assets being stolen from Vault contracts
Incident Analysis 👇
The attacker deployed a malicious token contract, which is also used as the attack contract, and created a PancakeSwap pair for the token and $BUSD.
Attacker: bscscan.com/address/0x0f3c…
Malicious token contract: bscscan.com/address/0xb7a7…
PancakeSwap pair: bscscan.com/address/0xca95…
Attacker: bscscan.com/address/0x0f3c…
Malicious token contract: bscscan.com/address/0xb7a7…
PancakeSwap pair: bscscan.com/address/0xca95…
The attacker flashloaned from Rabbit Bank contract and triggered StrategyLiquidate's execute method.
The execute method decodes input data as the LP token address, the attacker is able to execute code implemented in the malicious token contract.
The execute method decodes input data as the LP token address, the attacker is able to execute code implemented in the malicious token contract.
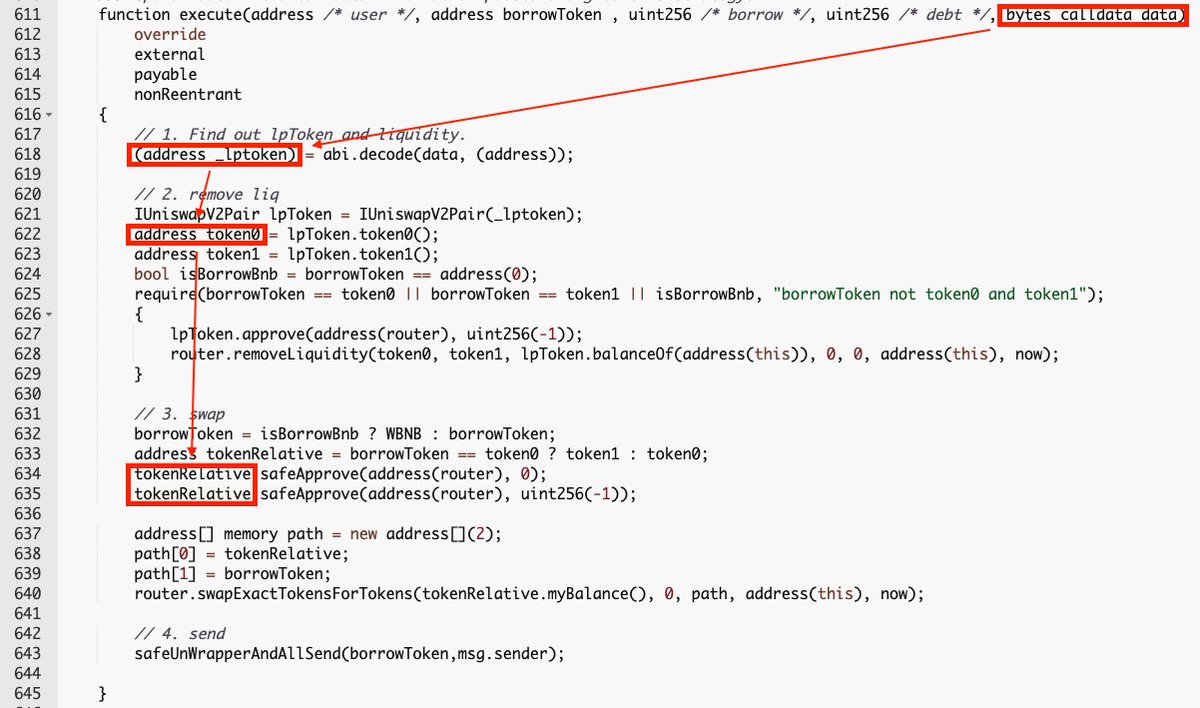
The malicious token contract called “FlurryRebaseUpkeep.performUpkeep()” rebases all vaults and updates multipliers for Rho Tokens.
The update is based on all strategies' balances.
The update is based on all strategies' balances.
The update was triggered in the process of a flashloan and the tokens borrowed from the Bank contract were not returned yet, the low balance led to a low multiplier.
FlurryRebaseUpkeep contract: bscscan.com/address/0x10f2…
One of the Vault contracts: bscscan.com/address/0xec7f…
FlurryRebaseUpkeep contract: bscscan.com/address/0x10f2…
One of the Vault contracts: bscscan.com/address/0xec7f…

The attacker returned the flashloan and finished the preparation transaction.
In the next transaction, the attacker deposited tokens with the low multiplier, updated the multiplier to a higher (normal) value, and withdrew the tokens with the high multiplier.
In the next transaction, the attacker deposited tokens with the low multiplier, updated the multiplier to a higher (normal) value, and withdrew the tokens with the high multiplier.
For example, in one of the transactions the multiplier was updated to 4.1598e35 (image 1) and in the next transaction, the multiplier was updated to 4.2530e35 (image 2) 

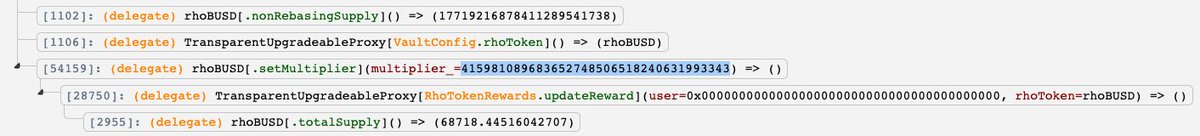

Because the multiplier is one of the factors deciding the RhoToken balance, the attacker's RhoToken balance was increased in the transaction so they were able to withdraw more tokens than they deserve from the Vault.
The attacker repeated this process multiple times.
The attacker repeated this process multiple times.
Note: Flurry Finance is a CertiK client but the exploit was caused by external dependencies.
• • •
Missing some Tweet in this thread? You can try to
force a refresh









