SRUM is maybe one of the best Windows digital forensic artefacts, if you’re willing to roll your sleeves up.
You can get proof of execution and execution runtime, as well as proof of network communication and the bytes sent and received
Let's take a look in this #DFIR thread🧵
You can get proof of execution and execution runtime, as well as proof of network communication and the bytes sent and received
Let's take a look in this #DFIR thread🧵
Since Win8, System Resource Usage Monitor (SRUM) monitors a bunch!
What we’re most interested in is its detailed record of programs and network activity.
SRUM has a LONG memory compared to some of the other more ephemeral artefacts📜
What we’re most interested in is its detailed record of programs and network activity.
SRUM has a LONG memory compared to some of the other more ephemeral artefacts📜
To put SRUM to forensic work, grab its .DAT file
C:\Windows\System32\sru\SRUDB.dat
To gain extra contextual data, we're advised to also collect the SOFTWARE hive.
I didn't do that however, because I am a bad person 😞
C:\Windows\System32\sru\SRUDB.dat
To gain extra contextual data, we're advised to also collect the SOFTWARE hive.
I didn't do that however, because I am a bad person 😞

We'll leverage one of @EricRZimmerman's brilliant tools to parse out the .DAT
f001.backblazeb2.com/file/EricZimme…
And we can simply execute with : `.\SrumECmd.exe -f .\SRUDB.dat --csv .`
f001.backblazeb2.com/file/EricZimme…
And we can simply execute with : `.\SrumECmd.exe -f .\SRUDB.dat --csv .`
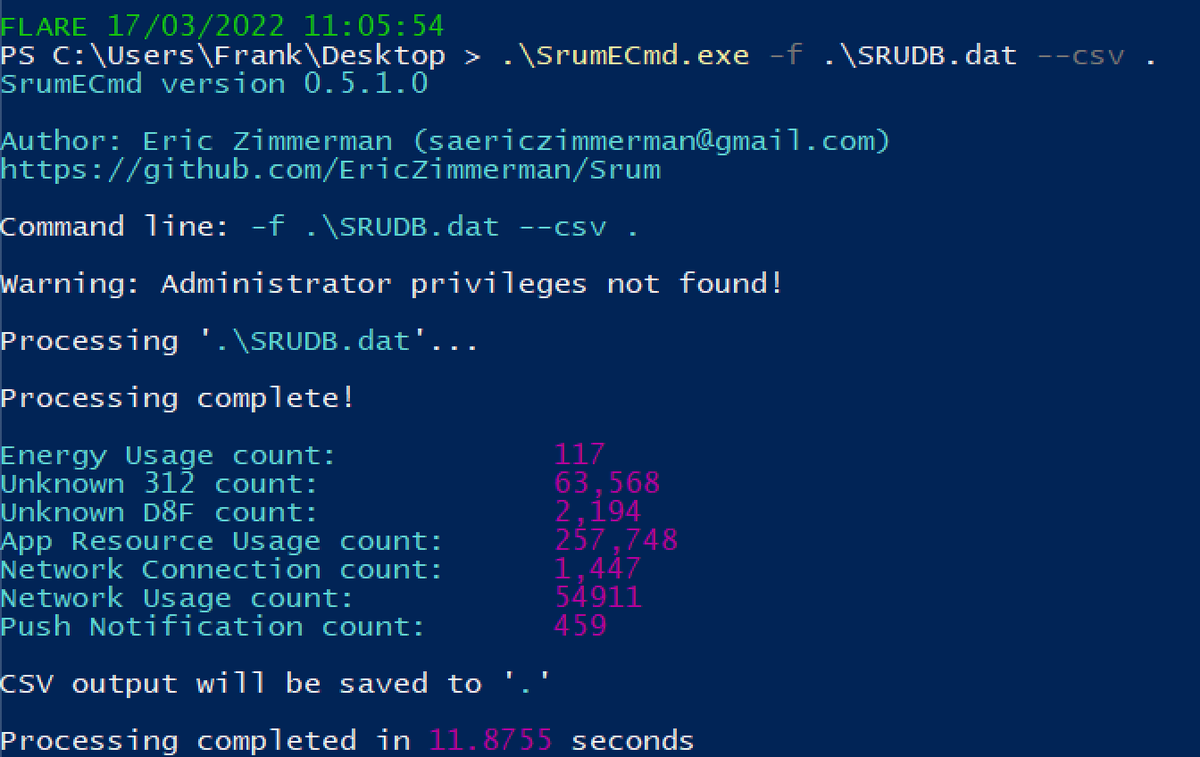
You should get a bunch of CSV files
I tend to prioritise the following ones:
- SrumECmd_NetworkUsages_Output.csv
- SrumECmd_AppResourceUseInfo_Output.csv
- SrumECmd_Unknown*_Output.csv (occasionally)
But maybe you'll find use from the others?
I tend to prioritise the following ones:
- SrumECmd_NetworkUsages_Output.csv
- SrumECmd_AppResourceUseInfo_Output.csv
- SrumECmd_Unknown*_Output.csv (occasionally)
But maybe you'll find use from the others?

Let's take a look at the results. I'll be using Excel because (again) I am a bad person.
SRUM seems to write once an hour and at shutdown, so don’t trust the timestamps as complete gospel.
SRUM seems to write once an hour and at shutdown, so don’t trust the timestamps as complete gospel.
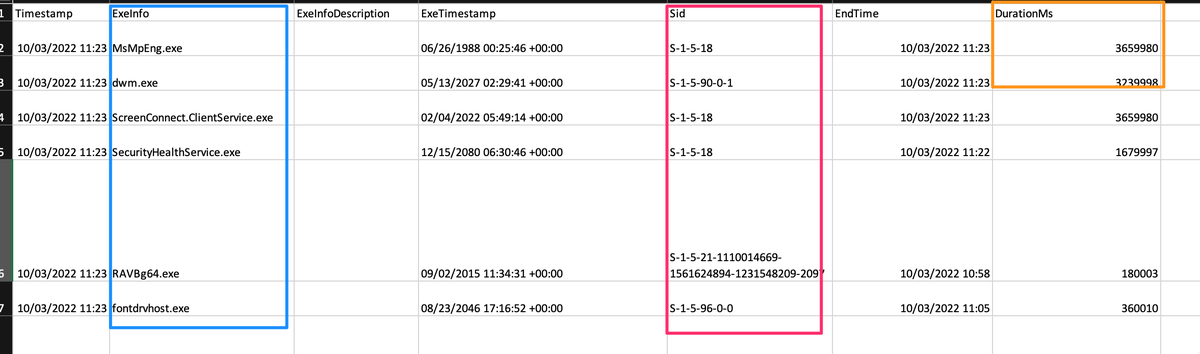
S͟r͟u͟m͟E͟C͟m͟d͟_N͟e͟t͟w͟o͟r͟k͟U͟s͟a͟g͟e͟s͟_O͟u͟t͟p͟u͟t͟.c͟s͟v͟
When tidied up has some cool fields. Most noteworthy in the orange box are the network bytes IN/OUT
When tidied up has some cool fields. Most noteworthy in the orange box are the network bytes IN/OUT

If you’re looking for possible indicator of C2 or data exfil, try this:
Convert these columns into a graph. I'd separate graphs for bytes in/out, initially.
You can then click on these points in the graph, and it will highlight the EXE back in your table.

Convert these columns into a graph. I'd separate graphs for bytes in/out, initially.
You can then click on these points in the graph, and it will highlight the EXE back in your table.


S͟r͟u͟m͟E͟C͟m͟d͟_A͟p͟p͟R͟e͟s͟o͟u͟r͟c͟e͟U͟s͟e͟I͟n͟f͟o͟_O͟u͟t͟p͟u͟t͟.c͟s͟v͟
We can use it to see programmes more / less resource intensive.
Maybe it will snitch on coin miners using a lot of resource, or quiet backdoors using fewer.
We can use it to see programmes more / less resource intensive.
Maybe it will snitch on coin miners using a lot of resource, or quiet backdoors using fewer.

S͟r͟u͟m͟E͟C͟m͟d͟_U͟n͟k͟n͟o͟w͟n͟3͟1͟2͟_O͟u͟t͟p͟u͟t͟.c͟s͟v͟
This one is a real mixed bag. Sometimes it’s gold, other times trash. It will show runtime with okayish accuracy
I tend to sort by shortest runtime when looking here.

This one is a real mixed bag. Sometimes it’s gold, other times trash. It will show runtime with okayish accuracy
I tend to sort by shortest runtime when looking here.

U͟s͟i͟n͟g͟ I͟R͟L͟
I had a case where an alert claimed some kind of process injection.
But I couldn’t find any other evidence to triangulate that finding. Maybe SRUM can help?
From SRUM's CSV formatted data, let's zero in on that window of time from the alert (23:52)


I had a case where an alert claimed some kind of process injection.
But I couldn’t find any other evidence to triangulate that finding. Maybe SRUM can help?
From SRUM's CSV formatted data, let's zero in on that window of time from the alert (23:52)



ScreenConnect - a remote management tool - appeared during our window of time.
I graphed out all of the ScreenConnect data SRUM held, with a focused on bytes in and out.
And look at the that wild spike in network communication?!

I graphed out all of the ScreenConnect data SRUM held, with a focused on bytes in and out.
And look at the that wild spike in network communication?!

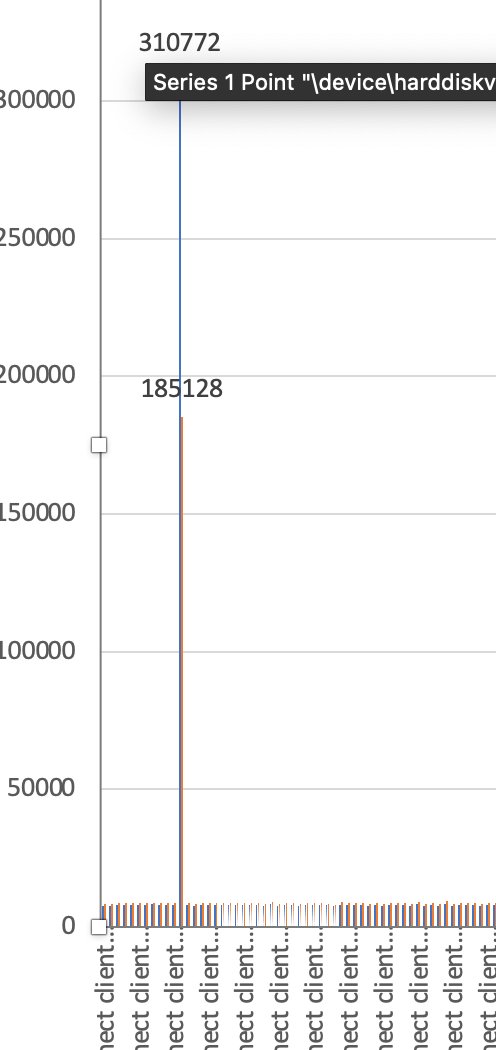
Drilling into the specific ScreenConnect spike, we can see it’s recorded 𝘢𝘯 𝘩𝘰𝘶𝘳 𝘭𝘢𝘵𝘦𝘳 than our initial alert time
I considered this suspicious nonetheless for three reasons:
1. When baselined, that colossal byte in/out was anomalous compared to previous activity
2.
I considered this suspicious nonetheless for three reasons:
1. When baselined, that colossal byte in/out was anomalous compared to previous activity
2.

We already contextualised this window of time as suspicious, from the initial alert.
3. We know that SRUM timestamps are not always accurate. Neither are alerts sometimes! An hour's flexibility is more than satisfactory to connect the potential sus activity.
3. We know that SRUM timestamps are not always accurate. Neither are alerts sometimes! An hour's flexibility is more than satisfactory to connect the potential sus activity.
I then initiated a ScreenConnect investigation, to see if anything here would contextualise the initial process inject alert
But that's for another day!
I hope this thread has brought SRUM to your attention, and equipped you with a foundation to explore SRUM's data yourself 💪
But that's for another day!
I hope this thread has brought SRUM to your attention, and equipped you with a foundation to explore SRUM's data yourself 💪
Here are some much better resources on SRUM by @velocidex and @13CubedDFIR
Thanks for your time 🧵
velociraptor.velocidex.com/digging-into-t….

Thanks for your time 🧵
velociraptor.velocidex.com/digging-into-t….

• • •
Missing some Tweet in this thread? You can try to
force a refresh