Governance attack! Attacker profited ~$1M. etherscan.io/tx/0x4227bca8e…
https://twitter.com/AudiusProject/status/1551000725169180672
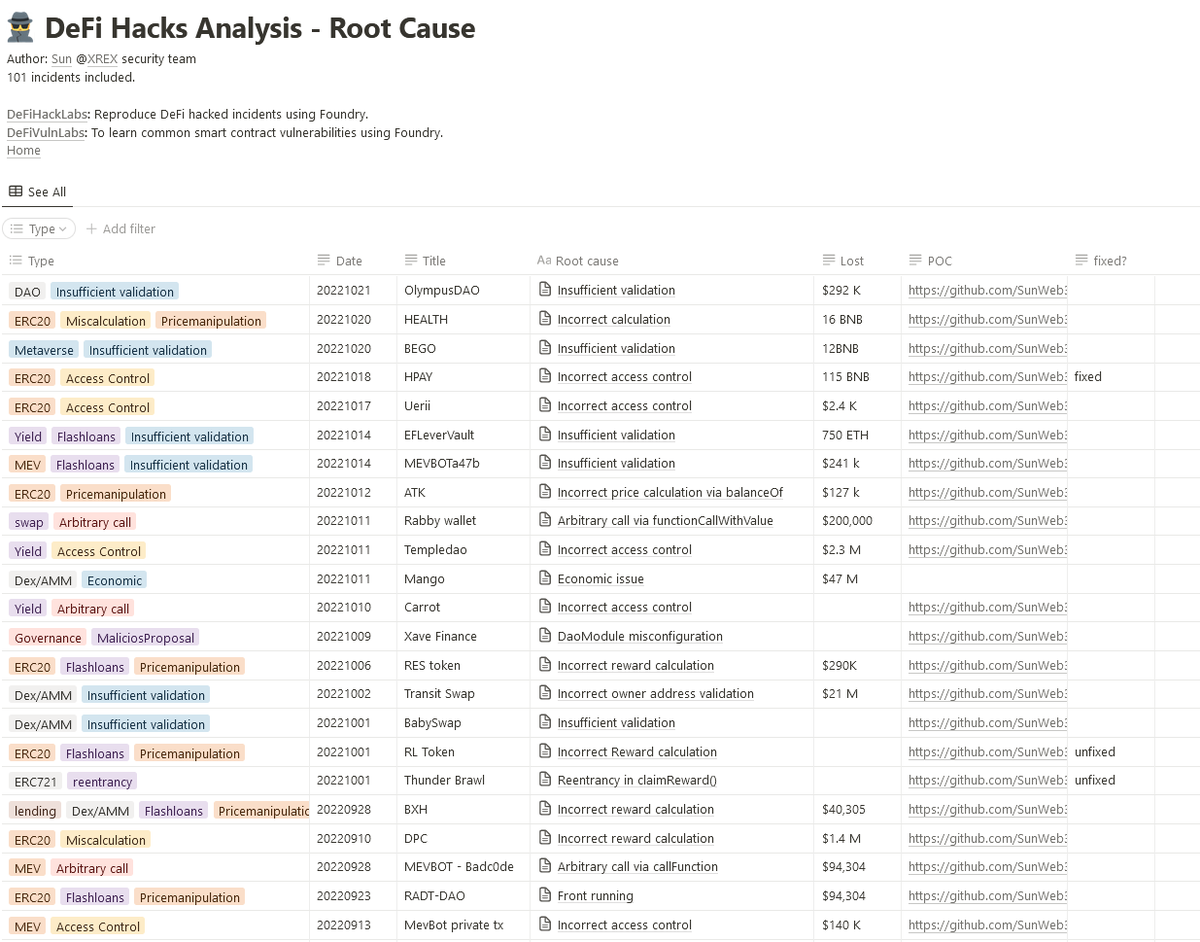
The bug was in Audius community treasury contract.
Exploited steps:
Tx (1): initialize + ProposalSubmitted + Staked.
Attacker called initialize() to modify configurations:
_votingPeriod to 3 blocks,
_executionDelay to 0 block
_guardianAddress
etherscan.io/tx/0xfefd829e2…
Exploited steps:
Tx (1): initialize + ProposalSubmitted + Staked.
Attacker called initialize() to modify configurations:
_votingPeriod to 3 blocks,
_executionDelay to 0 block
_guardianAddress
etherscan.io/tx/0xfefd829e2…

Tx (1), cont: submitted malicious proposal ID:85, which requested a transfer to attacker ~18M AUDIO tokens.
#AUDIO #web3 #web3sec
#AUDIO #web3 #web3sec

Tx (2): ProposalVoteSubmitted.
etherscan.io/tx/0x3c09c6306…
etherscan.io/tx/0x3c09c6306…
Tx (4): Over uniswap to swap all AUDIO to 704 ETH (~$1M).
etherscan.io/tx/0x82fc23992…
etherscan.io/tx/0x82fc23992…
• • •
Missing some Tweet in this thread? You can try to
force a refresh