🧵1/
The #Pegasus documentary by @frontlinepbs confirms a lot of my research into the false Pegasus narrative
It starts off in the year 2020 filming @FbdnStories offices in France, they speak about a massive leak of 50,000 NSO Pegasus targets
"There are numbers but no names"
The #Pegasus documentary by @frontlinepbs confirms a lot of my research into the false Pegasus narrative
It starts off in the year 2020 filming @FbdnStories offices in France, they speak about a massive leak of 50,000 NSO Pegasus targets
"There are numbers but no names"

2/
The documentary speak about the 50,000 number and says the following about it.
1. The list doesn't have any names
2. It has phone numbers
3. Country Code
4. Sometime stamps
5. It's a list from 2016-2020
"We can't explain where the list is coming from"
The documentary speak about the 50,000 number and says the following about it.
1. The list doesn't have any names
2. It has phone numbers
3. Country Code
4. Sometime stamps
5. It's a list from 2016-2020
"We can't explain where the list is coming from"

3/
This information falls directly in line with what I reported in my white paper called Exonerating Rwanda: The spyware case of Carine Kanimba
@OCCRP & @FbdnStories claimed Kanimba's phone was found in a list of 3,500 Rwandan numbers, but Kanimba never had a Rwandan number
This information falls directly in line with what I reported in my white paper called Exonerating Rwanda: The spyware case of Carine Kanimba
@OCCRP & @FbdnStories claimed Kanimba's phone was found in a list of 3,500 Rwandan numbers, but Kanimba never had a Rwandan number

4/
The statement that Carine Kanimba was found in the #PegasusProject 50,000 list was elevated by @CNN & was then retracted by @OCCRP & @FbdnStories for being false
Kanimba & @citizenlab then testified @HouseIntel July, 2022 saying her Belgian phone number had #Pegasus
The statement that Carine Kanimba was found in the #PegasusProject 50,000 list was elevated by @CNN & was then retracted by @OCCRP & @FbdnStories for being false
Kanimba & @citizenlab then testified @HouseIntel July, 2022 saying her Belgian phone number had #Pegasus

5/
@ckanimba & @jsrailton were @HouseIntel claiming an American had been spied on. This is a false flag narrative & a clever ruse as I previously noted
Kanimba is American with a Belgian number, this was changed to an American's phone number was spied on
@ckanimba & @jsrailton were @HouseIntel claiming an American had been spied on. This is a false flag narrative & a clever ruse as I previously noted
Kanimba is American with a Belgian number, this was changed to an American's phone number was spied on
https://twitter.com/jonathandata1/status/1603409264172830722?s=20&t=YmPuoVQk2RnCUs7C0pmCVQ
6/
Here is the article where @OCCRP claims Kanimba is part of the 3,500 numbers found in the 50,000 number list
Here is the article where @OCCRP claims Kanimba is part of the 3,500 numbers found in the 50,000 number list
https://twitter.com/jonathandata1/status/1585346171979313153?s=20&t=YmPuoVQk2RnCUs7C0pmCVQ
7/
This 50,000 number list is significant b/c it is being used in attempts to exonerate convicted criminals by appealing to International Criminal Tribunals @IntlCrimCourt
Carine Kanimba's false narrative of being found in the 3,500 Rwandan numbers is referenced in this case
This 50,000 number list is significant b/c it is being used in attempts to exonerate convicted criminals by appealing to International Criminal Tribunals @IntlCrimCourt
Carine Kanimba's false narrative of being found in the 3,500 Rwandan numbers is referenced in this case

8/
Continuing with the documentary, it speaks about American phone numbers with +1 country code cannot be targeted by Pegasus
Further showing that Carine Kanimba & John Scott-Railton's testimony to @HouseIntel was intentionally deceptive, as Belgium's country code is +32
Continuing with the documentary, it speaks about American phone numbers with +1 country code cannot be targeted by Pegasus
Further showing that Carine Kanimba & John Scott-Railton's testimony to @HouseIntel was intentionally deceptive, as Belgium's country code is +32

9/
Recap
@ckanimba & @jsrailton @citizenlab testified to @HouseIntel 2022
Both asserted Kanimba had Pegasus even though NSO says their software cannot target US numbers with a +1 code
Kanimba submits a +32 code report & says b/c she is American she was spied, that is false
Recap
@ckanimba & @jsrailton @citizenlab testified to @HouseIntel 2022
Both asserted Kanimba had Pegasus even though NSO says their software cannot target US numbers with a +1 code
Kanimba submits a +32 code report & says b/c she is American she was spied, that is false

10/
The documentary continues & focuses on the 50,000 alleged Pegasus list
Journalist gathered in Paris at the Height of COVID-19 & were tasked by @FbdnStories to put names to the phone number list
They were told that most of the countries doing the spying are very dangerous
The documentary continues & focuses on the 50,000 alleged Pegasus list
Journalist gathered in Paris at the Height of COVID-19 & were tasked by @FbdnStories to put names to the phone number list
They were told that most of the countries doing the spying are very dangerous

11/
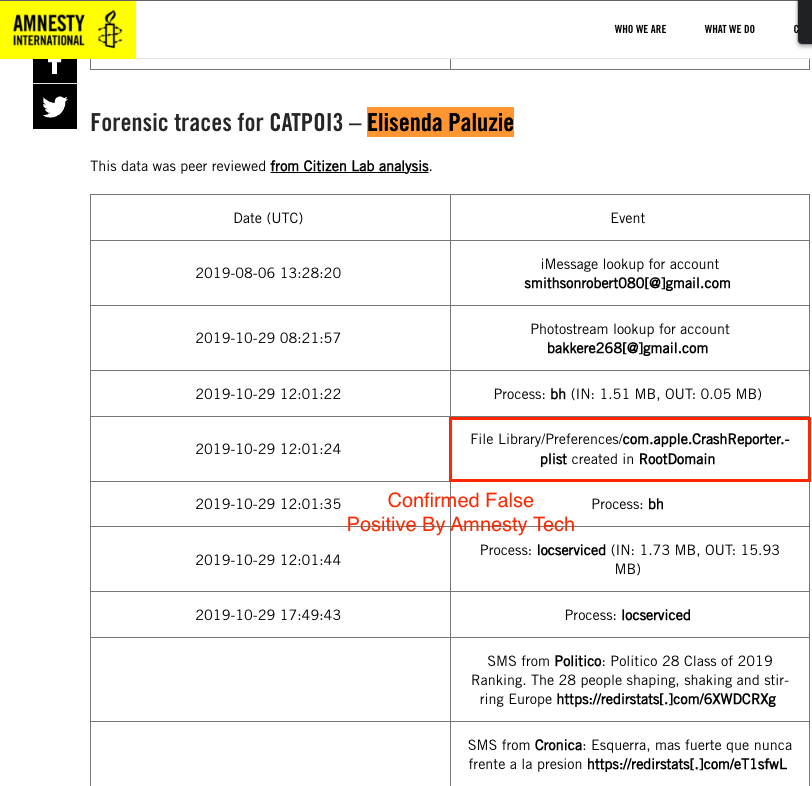
Claudio Guarnieri @botherder of @AmnestyTech now enters the documentary & says Pegasus is code that looks very similar to whats running on your phone but designed to do something different
He is referring to indicators of compromise which Amnesty has many false positives
Claudio Guarnieri @botherder of @AmnestyTech now enters the documentary & says Pegasus is code that looks very similar to whats running on your phone but designed to do something different
He is referring to indicators of compromise which Amnesty has many false positives

12/
Claudio is viewing a STIX2 file which is an alleged list of IOCs with undisclosed attribution. It is used with MVT-Tool, software written to "detect" Pegasus
Since the release of MVT July, 2021 it has been delivering false positives as noted by @zackwhittaker of @TechCrunch
Claudio is viewing a STIX2 file which is an alleged list of IOCs with undisclosed attribution. It is used with MVT-Tool, software written to "detect" Pegasus
Since the release of MVT July, 2021 it has been delivering false positives as noted by @zackwhittaker of @TechCrunch

13/
I have written extensively about the false positive results that have derived from @AmnestyTech's MVT-Tool
Each time false positives are found Amnesty does not announce a correction, nor do they reexamine alleged devices
I raised this issue with Amnesty and was dismissed
I have written extensively about the false positive results that have derived from @AmnestyTech's MVT-Tool
Each time false positives are found Amnesty does not announce a correction, nor do they reexamine alleged devices
I raised this issue with Amnesty and was dismissed

14/
These false positives impact many countries that @FbdnStories @AmnestyTech & @citizenlab are accusing of espionage
#Spain #Rwanda #India #France & #Morocco are just a few accused of spying on civil society & their "victims" have false results
github.com/mvt-project/mv…
These false positives impact many countries that @FbdnStories @AmnestyTech & @citizenlab are accusing of espionage
#Spain #Rwanda #India #France & #Morocco are just a few accused of spying on civil society & their "victims" have false results
github.com/mvt-project/mv…
15/
Claudio shows the list of IOCs in another frame in the documentary.
The scientific methodology used to attribute this publicly available malicious list has never been shared with the public, but yet this list has been used to confirm hundreds of Pegasus victims
Claudio shows the list of IOCs in another frame in the documentary.
The scientific methodology used to attribute this publicly available malicious list has never been shared with the public, but yet this list has been used to confirm hundreds of Pegasus victims

16/
We now move into a popular & never confirmed #Pegasus #Hacking association
The the murder of Jamal Khashoggi
The documentary features @danapriest of @washingtonpost as she investigates the Pegasus list
She says two phone numbers were found
Jamals Wife & Jamal's Fiancé
We now move into a popular & never confirmed #Pegasus #Hacking association
The the murder of Jamal Khashoggi
The documentary features @danapriest of @washingtonpost as she investigates the Pegasus list
She says two phone numbers were found
Jamals Wife & Jamal's Fiancé

17/
Through my extensive research over the years, into the specific claim that #Pegasus was used to hack Jamal Kashoggi I found disinformation coming from @AmnestyTech's partners which include @citizenlab
Through my extensive research over the years, into the specific claim that #Pegasus was used to hack Jamal Kashoggi I found disinformation coming from @AmnestyTech's partners which include @citizenlab
18/
The video I created shows Bill Marczak of @citizenlab speaking to @CNN in 2018 saying
It is 100 percent clear that [Jamal Khashoggi] received one of these [Pegasus] text messages containing a link
Then John Scott-Railton in 2022 says "we don't have the device to confirm"
The video I created shows Bill Marczak of @citizenlab speaking to @CNN in 2018 saying
It is 100 percent clear that [Jamal Khashoggi] received one of these [Pegasus] text messages containing a link
Then John Scott-Railton in 2022 says "we don't have the device to confirm"

19/
When I first posted the disinformation @citizenlab was spreading about the Jamal Khashoggi #Pegasus hacking, I was attacked by @runasand & @maldr0id.
They said I was spreading disinformation & that I edited the CNN video to make it seem like @citizenlab was speaking of Jamal
When I first posted the disinformation @citizenlab was spreading about the Jamal Khashoggi #Pegasus hacking, I was attacked by @runasand & @maldr0id.
They said I was spreading disinformation & that I edited the CNN video to make it seem like @citizenlab was speaking of Jamal

20/
The smear campaign run by Runa & Lukasz, Accused me of cutting CNN footage to make it look like @citizenlab said Jamal was hacked. That came to a halt when I presented a Media article from @intifada written in 2018 showing exactly what I presented.
electronicintifada.net/blogs/tamara-n…
The smear campaign run by Runa & Lukasz, Accused me of cutting CNN footage to make it look like @citizenlab said Jamal was hacked. That came to a halt when I presented a Media article from @intifada written in 2018 showing exactly what I presented.
electronicintifada.net/blogs/tamara-n…

21/
The original @CNN interview with Bill Marczak of The Citizen Lab saying with 100% certainty that Pegasus was used to hack Jamal Khashoggi can be viewed here
The original @CNN interview with Bill Marczak of The Citizen Lab saying with 100% certainty that Pegasus was used to hack Jamal Khashoggi can be viewed here
22/
Moving forward in the documentary we see how "Forensics" are conducted by @FbdnStories & @AmnestyTech
@danapriest travels to Istanbul to meet w/Jamal Khashoggi's fiance & asks her if she would want her phone forensically examined
Then calls Claudio in Berlin for results
Moving forward in the documentary we see how "Forensics" are conducted by @FbdnStories & @AmnestyTech
@danapriest travels to Istanbul to meet w/Jamal Khashoggi's fiance & asks her if she would want her phone forensically examined
Then calls Claudio in Berlin for results

23/
The way @AmnestyTech & @citizenlab conduct "Forensics" is by using iCloud backups
A physical forensics examination could potentially reconstruct memory to find deleted data, but Director of The Citizen Lab an @AmnestyTech partner says having the mobile might not be useful
The way @AmnestyTech & @citizenlab conduct "Forensics" is by using iCloud backups
A physical forensics examination could potentially reconstruct memory to find deleted data, but Director of The Citizen Lab an @AmnestyTech partner says having the mobile might not be useful

24/
Forensics firm @ElcomSoft stated that only using an iCloud backup is not proper & you will be missing a lot.
They published an article
The Worst Mistakes in iOS Forensics
"Proper logical acquisition is not limited to backups. In fact, backups are just the beginning."
Forensics firm @ElcomSoft stated that only using an iCloud backup is not proper & you will be missing a lot.
They published an article
The Worst Mistakes in iOS Forensics
"Proper logical acquisition is not limited to backups. In fact, backups are just the beginning."

25/
As I continue to watch the documentary, we see how Amnesty & Citizen Lab both use backups for their forensics analysis
@danapriest meets with Khashoggi's wife in D.C
Khashoggi's wife allowed Dana to download her phone & send a copy to Claudio and Bill Marczak at Citizen Lab
As I continue to watch the documentary, we see how Amnesty & Citizen Lab both use backups for their forensics analysis
@danapriest meets with Khashoggi's wife in D.C
Khashoggi's wife allowed Dana to download her phone & send a copy to Claudio and Bill Marczak at Citizen Lab

26/
Bill Marczak of @citizenlab now enters & says he conducted an analysis on all the available data from 2 Android OS phones belonging o Khashaggi's wife Hanan
If Marczak had the physical device there would be more data, & now the phone's integrity has been compromised
Bill Marczak of @citizenlab now enters & says he conducted an analysis on all the available data from 2 Android OS phones belonging o Khashaggi's wife Hanan
If Marczak had the physical device there would be more data, & now the phone's integrity has been compromised

27/
This is a common theme with @citizenlab & @AmnestyTech, they allow the alleged victim to continue to use the device that has been said to be infected which compromises all data integrity
No chain of custody, no quarantine, & the examination is not performed in a clean lab
This is a common theme with @citizenlab & @AmnestyTech, they allow the alleged victim to continue to use the device that has been said to be infected which compromises all data integrity
No chain of custody, no quarantine, & the examination is not performed in a clean lab
28/
Bill Marczak speaks about analyzing Android OS devices for Pegasus in 2020 but not a single Android OS device was analyzed in 2022 when 65 Catalans were said to be infected with Pegasus
Citizen Lab says "Android which is more difficult to forensically analyse"
#CatalanGate
Bill Marczak speaks about analyzing Android OS devices for Pegasus in 2020 but not a single Android OS device was analyzed in 2022 when 65 Catalans were said to be infected with Pegasus
Citizen Lab says "Android which is more difficult to forensically analyse"
#CatalanGate

29/
We now start to get into some interesting details. @danapriest relays Bill Marczak's finding of Hanan's Android OS devices, He says a browser tab was opened by UAE officials while Hanan was detained, and then the URL installed Pegasus
We now start to get into some interesting details. @danapriest relays Bill Marczak's finding of Hanan's Android OS devices, He says a browser tab was opened by UAE officials while Hanan was detained, and then the URL installed Pegasus

30/
Marczak says they have the smoking gun, the traces of the spyware. He says "Almost certainly the spyware was installed and exfiltrated information from her phone"
"Almost certainly" is not definitive, but @citizenlab likes to present "strong circumstantial evidence" as fact
Marczak says they have the smoking gun, the traces of the spyware. He says "Almost certainly the spyware was installed and exfiltrated information from her phone"
"Almost certainly" is not definitive, but @citizenlab likes to present "strong circumstantial evidence" as fact

31/
"Saudi Arabia has said claims that it used spyware are baseless"
This is 100% accurate
There is no science, reproducible evidence, data integrity is compromised & @citizenlab's lack of rigor shows in their latest false Pegasus infection of Toni Comín Member of EU Parliament
"Saudi Arabia has said claims that it used spyware are baseless"
This is 100% accurate
There is no science, reproducible evidence, data integrity is compromised & @citizenlab's lack of rigor shows in their latest false Pegasus infection of Toni Comín Member of EU Parliament

32/
NSO Group has also denied all involvement of their technology in the murder of Jamal Khashoggi. @amnesty and @citizenlab have been consistently accusing NSO Group's technology of spying on members of civil society for over 5 years without any evidence.
NSO Group has also denied all involvement of their technology in the murder of Jamal Khashoggi. @amnesty and @citizenlab have been consistently accusing NSO Group's technology of spying on members of civil society for over 5 years without any evidence.

33/
What many do not known, is @citizenlab has received many donations from spyware firm Palantir, & Dir Ron Deibert of @citizenlab calls Palantir the darling of the defense & intelligence community in his Book Black Code: Surveillance, Privacy, and the Dark Side of the Internet
What many do not known, is @citizenlab has received many donations from spyware firm Palantir, & Dir Ron Deibert of @citizenlab calls Palantir the darling of the defense & intelligence community in his Book Black Code: Surveillance, Privacy, and the Dark Side of the Internet

@citizenlab 34/
The documentary takes us to Mexico & we are told that Carmen Aristegui @aristeguicnn has been a victim of Pegasus since 2015
This is contrary to @AmnestyTech's report showing Carmen was infected in 2014
Why am I pointing this out?
b/c details matter when seeking truth
The documentary takes us to Mexico & we are told that Carmen Aristegui @aristeguicnn has been a victim of Pegasus since 2015
This is contrary to @AmnestyTech's report showing Carmen was infected in 2014
Why am I pointing this out?
b/c details matter when seeking truth

35/
Carmen @aristeguicnn says her sister is among the 50,000 phone number list of Pegasus targets & says her sister is not political & not an activist
@OsloFF said it costs $1M per phone infection with Pegasus
Mexico was said to have 15,000+ numbers that is ~$15B USD needed
Carmen @aristeguicnn says her sister is among the 50,000 phone number list of Pegasus targets & says her sister is not political & not an activist
@OsloFF said it costs $1M per phone infection with Pegasus
Mexico was said to have 15,000+ numbers that is ~$15B USD needed

36/
Carmen @aristeguicnn says she knew her phone was tapped when she and her son started to get strange text messages...
Strange texts does not mean tapped
During COVID-19 receiving texts w/short URLs was common around the world. 20 ppl could be included it's called spam/junk
Carmen @aristeguicnn says she knew her phone was tapped when she and her son started to get strange text messages...
Strange texts does not mean tapped
During COVID-19 receiving texts w/short URLs was common around the world. 20 ppl could be included it's called spam/junk

37/
Now the Anonymous blacked out face person with a voice changer comes into the documentary, we'll call them Anon
Anon says these were the steps to infect
1. Get the victims number
2. Do Social Eng/OSINT
3. Construct some text to send
4. Hope they click
5. Spyware installs
Now the Anonymous blacked out face person with a voice changer comes into the documentary, we'll call them Anon
Anon says these were the steps to infect
1. Get the victims number
2. Do Social Eng/OSINT
3. Construct some text to send
4. Hope they click
5. Spyware installs

38/
Anon is a Mexican insider providing info to @FbdnStories & @frontlinepbs, but Anon's story is different from what Citizen Lab told Financial Times about the spyware in Mexico
1. No Social Eng/OSINT needed
2. @citizenlab says with "high confidence" this is how Pegasus works
Anon is a Mexican insider providing info to @FbdnStories & @frontlinepbs, but Anon's story is different from what Citizen Lab told Financial Times about the spyware in Mexico
1. No Social Eng/OSINT needed
2. @citizenlab says with "high confidence" this is how Pegasus works

39/
Former President Enrique Nieto has denied using Pegasus to spy on journalists.
The big questions are...
Why are real professionals not performing mobile forensics on these alleged infected devices?
Why are the physical mobile devices not going through analysis?
Former President Enrique Nieto has denied using Pegasus to spy on journalists.
The big questions are...
Why are real professionals not performing mobile forensics on these alleged infected devices?
Why are the physical mobile devices not going through analysis?

40/
The documentary moves to Turkey to meet with journalist @Khadija_Ismayil Khadija Ismayilova of Azerbaijan
Miranda Patrucic @MirandaOCCRP of the @OCCRP is present and tells Khadija that Pegasus is a Zero-Click technology, this is the year 2020
The documentary moves to Turkey to meet with journalist @Khadija_Ismayil Khadija Ismayilova of Azerbaijan
Miranda Patrucic @MirandaOCCRP of the @OCCRP is present and tells Khadija that Pegasus is a Zero-Click technology, this is the year 2020

41/
The first alleged Pegasus Zero-Click was discovered in 2021
Then, in 2022 Citizen Lab said they found a different Pegasus Zero-Click dating back from 2017-2020 on Catalan phones
Miranda says she's aware of a Zero-Click in 2020 during this filming, where is the CVE?
The first alleged Pegasus Zero-Click was discovered in 2021
Then, in 2022 Citizen Lab said they found a different Pegasus Zero-Click dating back from 2017-2020 on Catalan phones
Miranda says she's aware of a Zero-Click in 2020 during this filming, where is the CVE?

42/
Digital espionage & forensics are my core research focuses, most people & orgs in this documentary have either blocked me, called me a fraud, conspiracy theorist, said i'm on NSO payroll, etc..
But @OCCRP claims to know of a Zero-Click attack in 2020 & have never reported
Digital espionage & forensics are my core research focuses, most people & orgs in this documentary have either blocked me, called me a fraud, conspiracy theorist, said i'm on NSO payroll, etc..
But @OCCRP claims to know of a Zero-Click attack in 2020 & have never reported

• • •
Missing some Tweet in this thread? You can try to
force a refresh