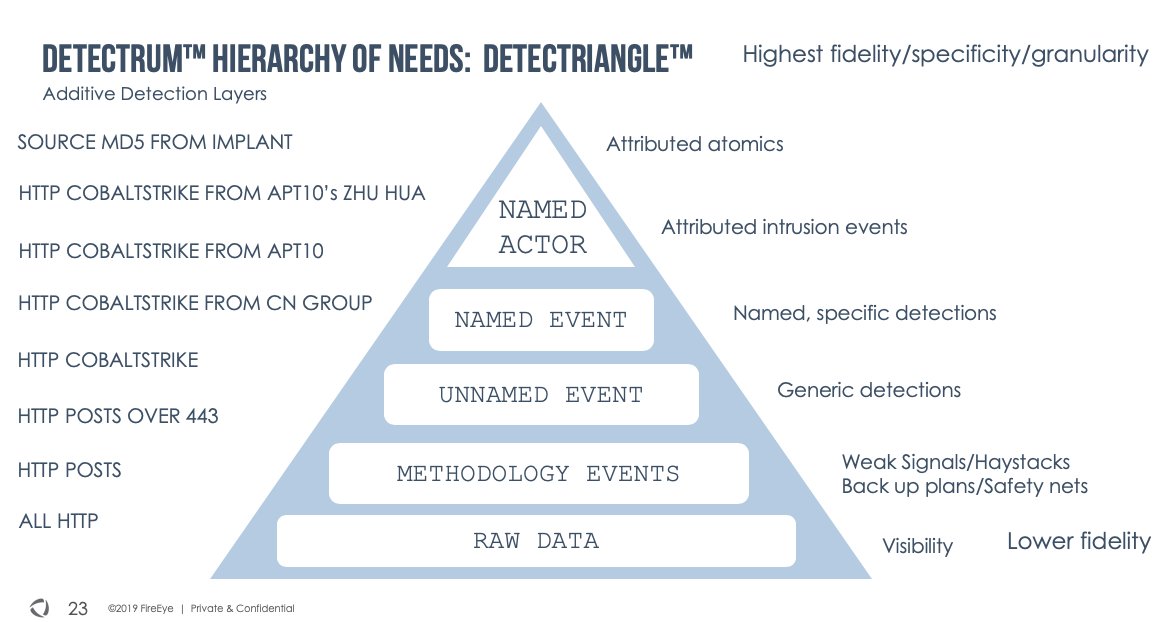
(a #dailyyara thread)
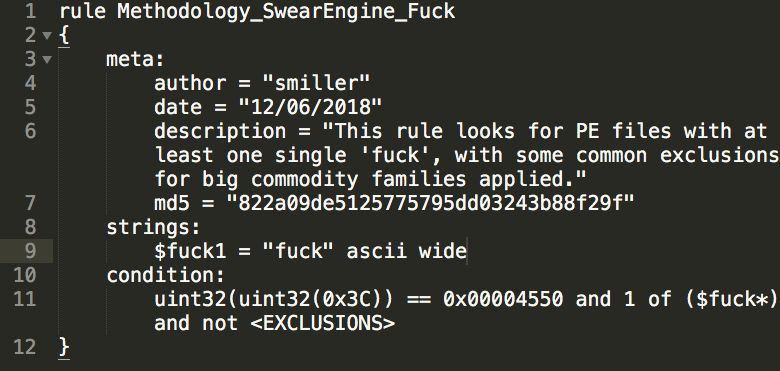
PE files w/ exported functions often contain an image directory entry that we usually call something like "PE DLL name" or "export DLL name"
This string is "analytically rich" and is surfaced in many tools
loader(x64).dll
pupyx64d.dll
uacdll(x64).dll
x86Dll.dll
tindll_x86.dll
reflective_dll.x64.dll
Predictable convention for all devs perhaps, but a strong presence in malware too.
hotcore
airbreak
crosswalk
kpot
lootjack
scrapmint
ransack
dridex
wavekey
cozycar
childsplay
blackcoffee
apocalipto
highnoon
frontshell
stalemate
rdfsniffer
trickbot
anchor
cozycar
soregut
whiteout
badflick
sleepykey
zxshell
babymetal
carbanak
poet
irishmate
pupyrat
milotrick
crosswalk
jumpkick
slub
slowpeek
bullstand
pillowmint
navrat
fiddlewood
bookpigeon
whinybear
wonderland
miniswipe
wetlink
torrentlocker
sadflower
eviltoss
xthief
uroburos
meterpreter
cardswipe
pocodownloader
bossnail
birdpen
darkmirror
facade
apt19
apt29
apt33
apt34
apt35
apt38
apt40
apt41
fin6
fin7
and 30+ UNC groups, including our own @Mandiant red team -- i see y'all :D
gist.github.com/stvemillertime…
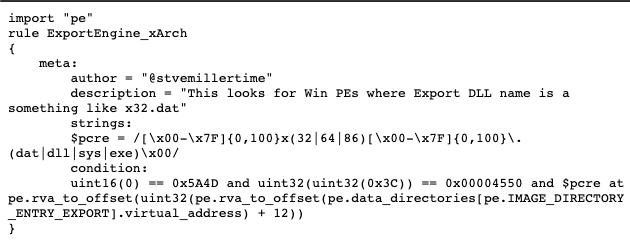
gist.github.com/stvemillertime…
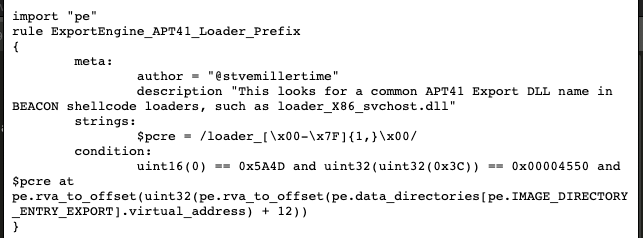
github.com/stvemillertime…
fireeye.com/blog/threat-re…
Once you've maxed out your Yara ideas for the export DLL name string itself, you can move on to export function names and function anomalies.