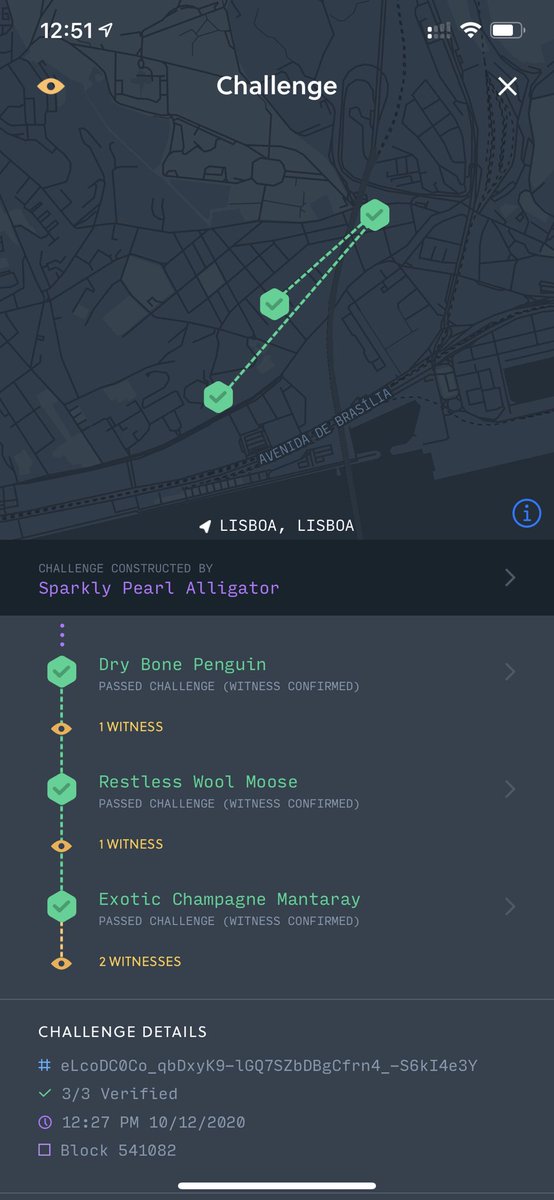
One of the more unique aspects of the @Helium Network is the Consensus Protocol. Proof-of-Coverage (#PoC) is used for sybil resistance and to periodically select a new #HoneyBadgerBFT group. 

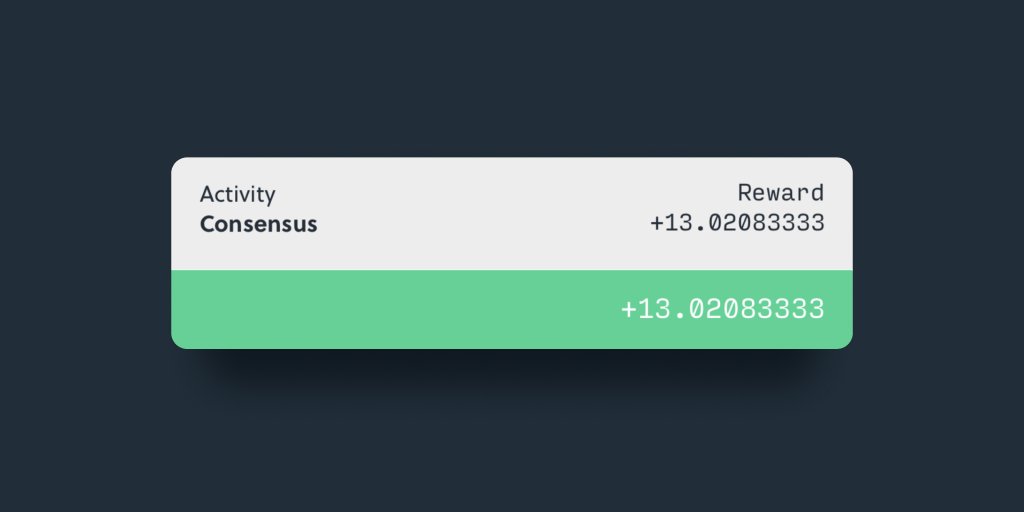
Ask any Hotspot host and they will tell you how they dream of joining the coveted Consensus Group - a small group of Hotspots on #ThePeoplesNetwork that receives 6% of all $HNT mined per epoch. 
Let’s take a walk back in time, shall we? We first read @socrates1024 #HoneyBadgerBFT paper in 2018. Our implementation was similar to @ethereum, using the GHOST protocol and @bitcoin #NakamotoConsensus to select a winner for each block. 

It turned out #NakamotoConsensus was not ideal due to its deterministic nature. We wanted something with instant block finality that was fast, tolerant of high latency, and censorship resistant.
Unlike @filecoin and others, the @Helium Network is comprised of many low power nodes running on consumer grade backhaul. Tolerance of latency and the ability to process messages asynchronously is a must.
#HoneyBadgerBFT met all these criteria. In the @Helium Network a new Consensus Group is elected every 35 blocks based on activity and #PoC performance. The new group runs a distributed key generation process, implemented from a paper written by @aniketpkate. 

There are at least a couple of other #HoneyBadgerBFT implementations including @poanetwork, but we implemented directly from @socrates1024 paper on the subject: eprint.iacr.org/2016/199.pdf
All transactions in the @Helium Network are encrypted. Each member of the #HoneyBadgerBFT group only has a shard of the complete private key, and a majority of group members are required to decrypt messages before validating them and adding them to blocks. 

To dive deeper into the @Helium Consensus Protocol and the $HNT mining process that’s associated, make sure to check out our #developer documentation: bit.ly/3lLznNE
The Consensus Group rotates between more than 10,000 active members, making @Helium one of the most diverse censorship #blockchain networks that we know of. What other projects are doing interesting things with diversity and censorship resistance? 

• • •
Missing some Tweet in this thread? You can try to
force a refresh