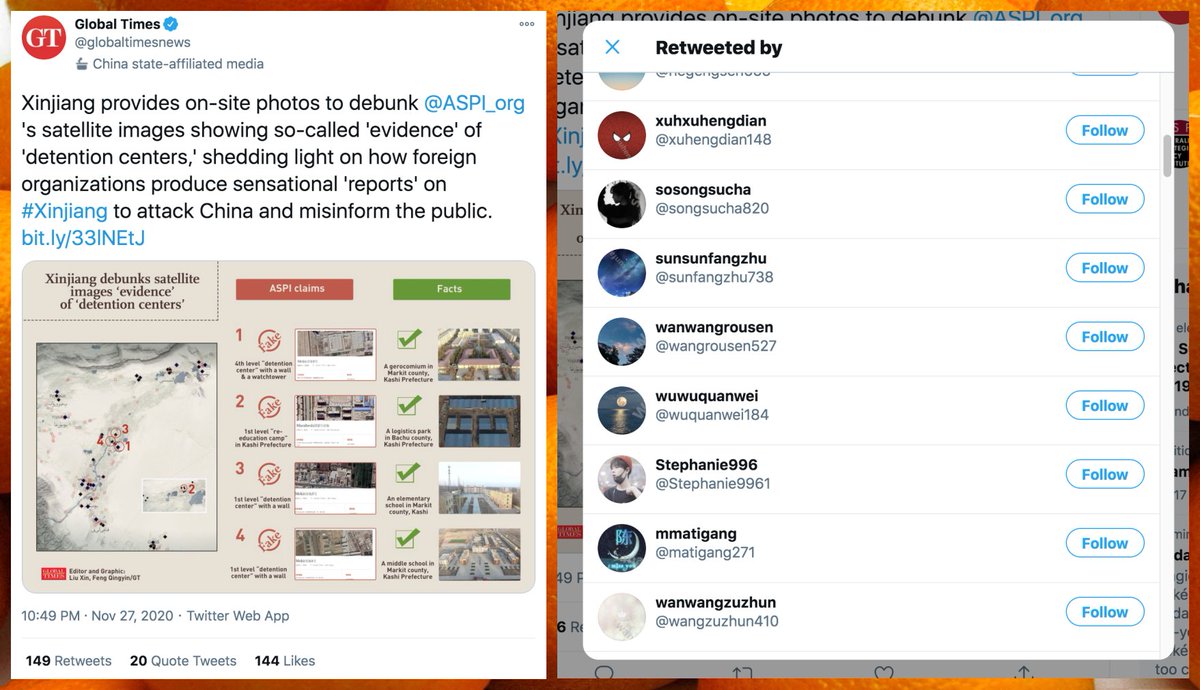
How did this video get 8.5K views despite the tweets having no retweets or likes and the accounts having no followers?
cc: @ZellaQuixote
cc: @ZellaQuixote

Answer: the video, originally tweeted by @CindyScarbrou17, has been embedded in 1353 tweets from 1140 different accounts. Although none of the individual tweets got much attention, the video racked up a decent view count due to the the sheer number of tweets containing it. 

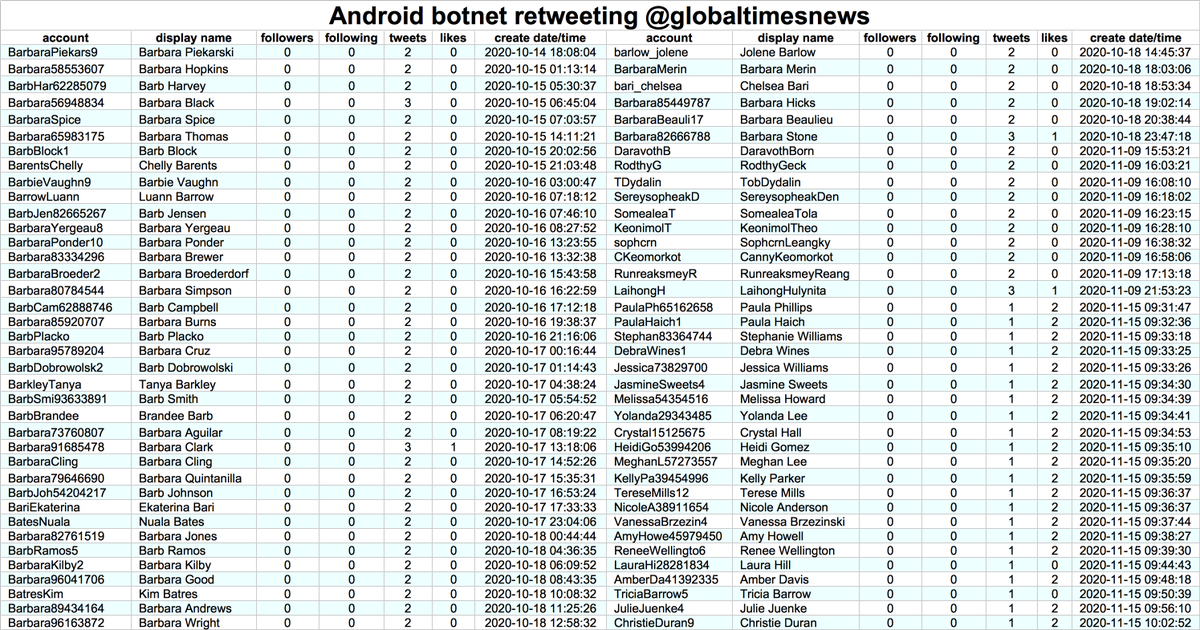
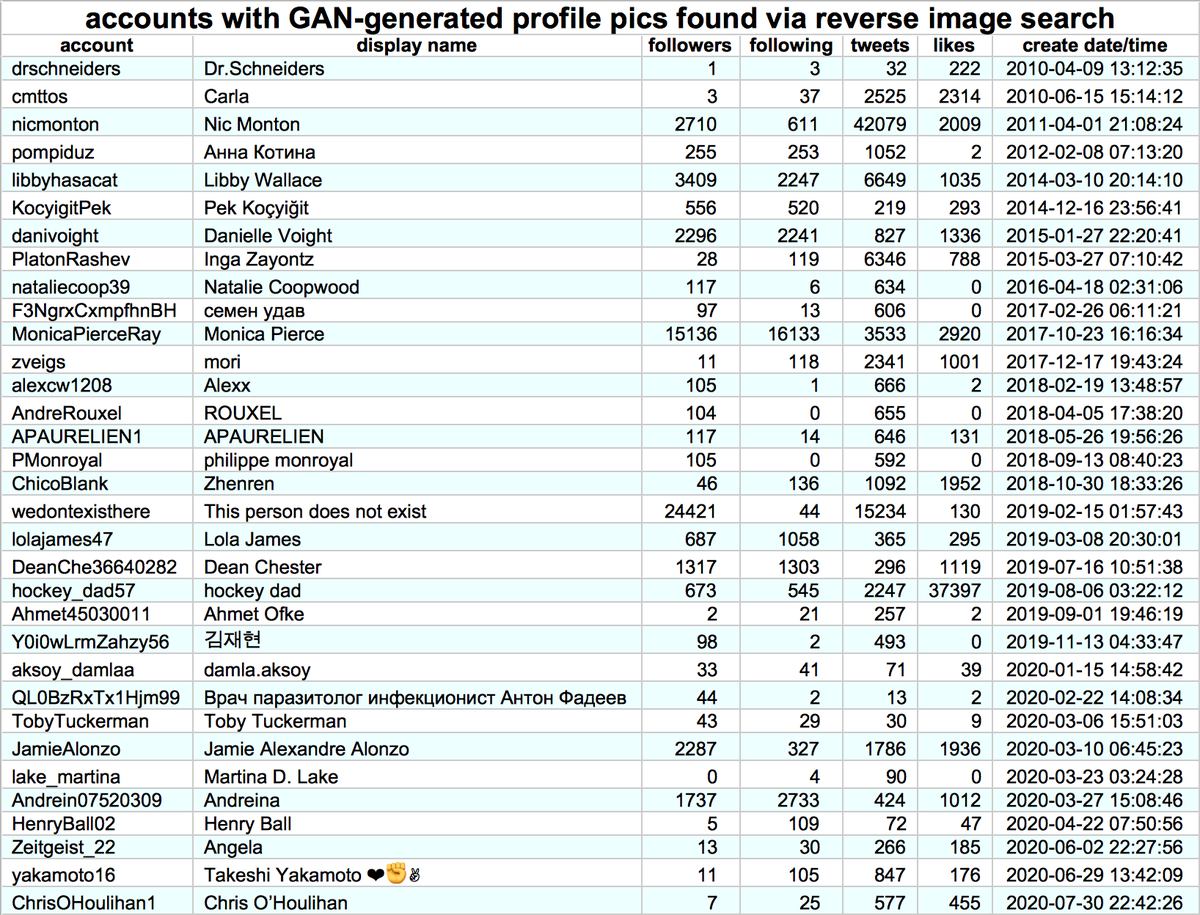
These accounts are part of a Korean-language pornbot network consisting of (at least) 4291 accounts with repetitive naming schemes, created in batches between September 30th and November 18th, 2020. The older accounts host the original videos, and the newer ones embed them. 





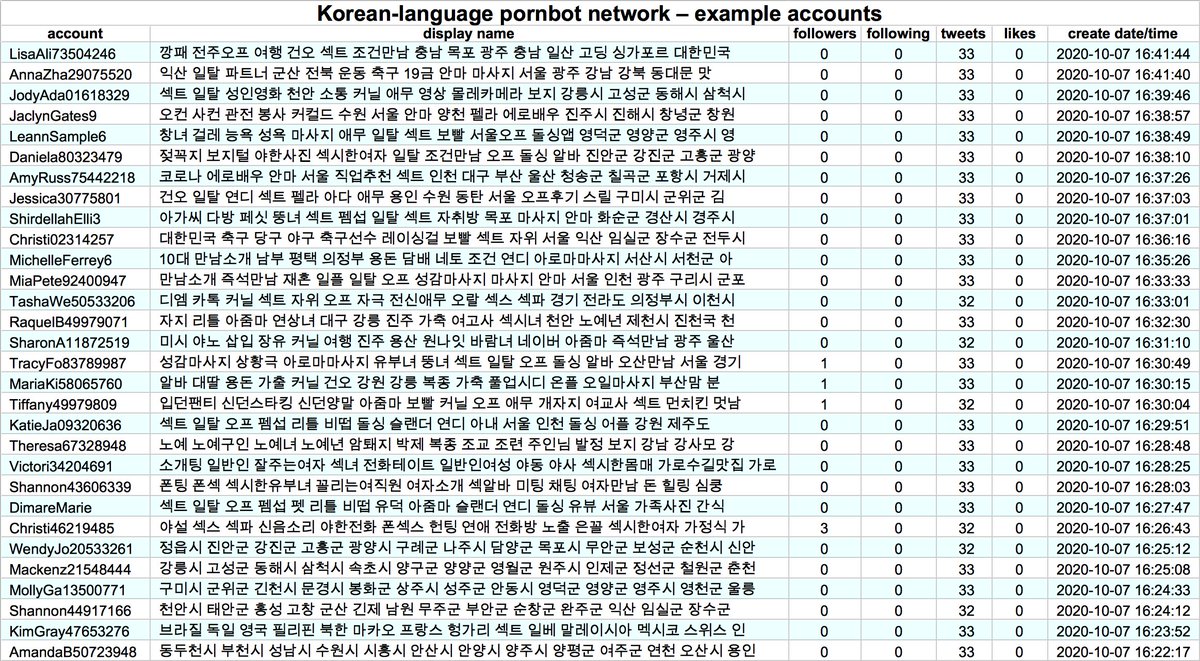

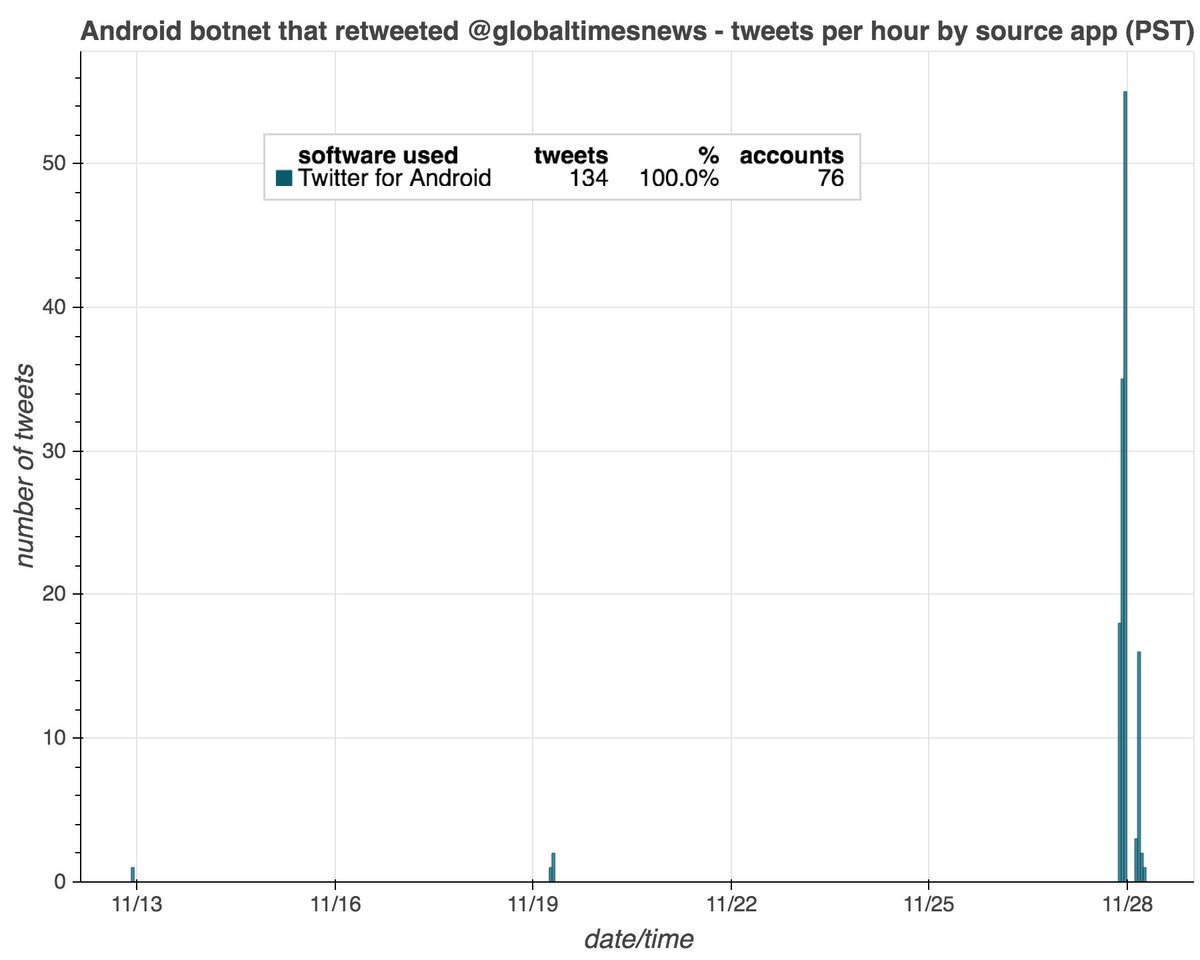
The accounts in this network all (allegedly) tweet via the Twitter Web App, but due to the sheer number of accounts and the repetitive nature of the content, we suspect they are automated rather than human-operated. All tweets containing text are in Korean. 



Did we mention this botnet is quite repetitive? Although it has tweeted 101205 times, it has only shared 383 unique pieces of content (mostly video, with a few still images thrown in). The most frequently tweeted video was posted 3280 times on 2170 distinct accounts. 

• • •
Missing some Tweet in this thread? You can try to
force a refresh