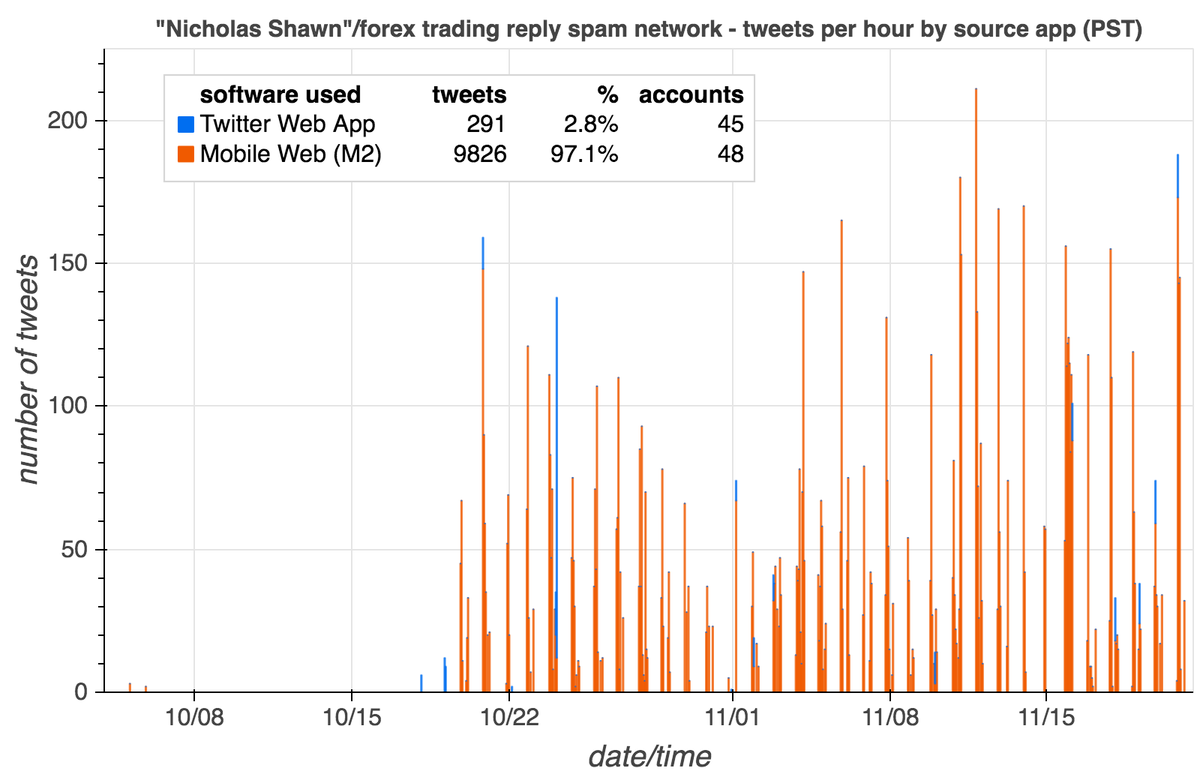
What's with all these similarly-named accounts retweeting this @globaltimesnews tweet? #SundaySpam
cc: @ZellaQuixote
cc: @ZellaQuixote
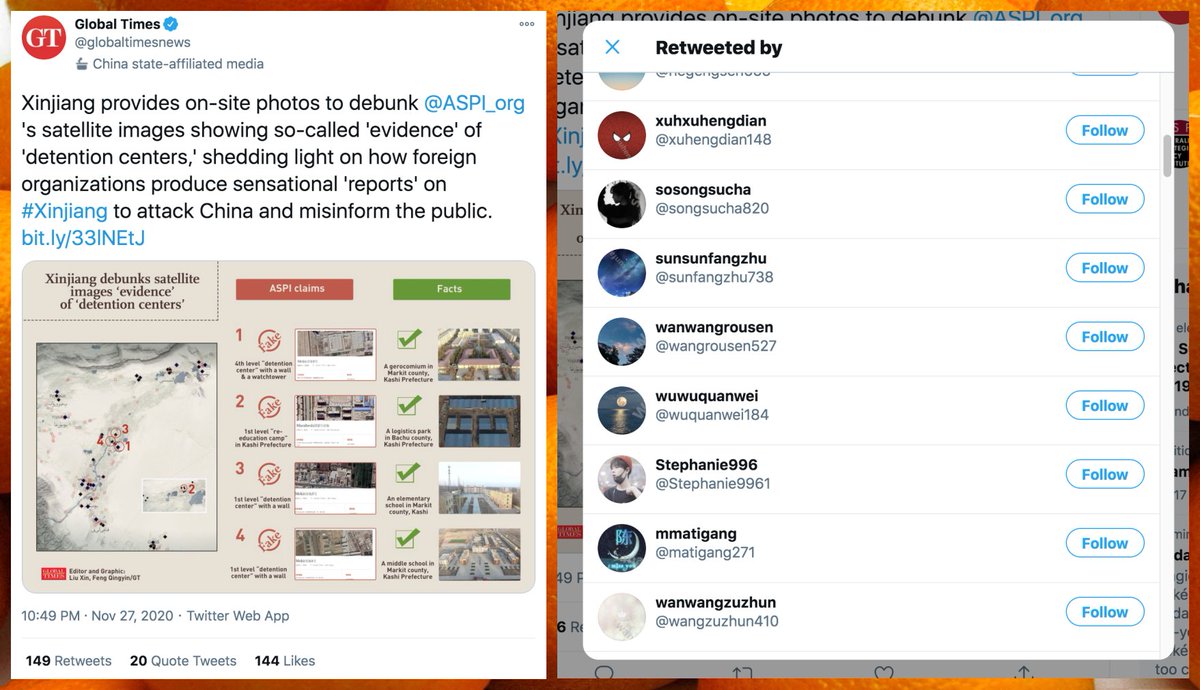
Answer: a few recent @globaltimesnews tweets have been amplified by two distinct groups of bots. (It's possible that they are part of the same network, but we can't prove this, so we treated them as two separate botnets for the sake of this analysis.) #ATaleOfTwoBotnets
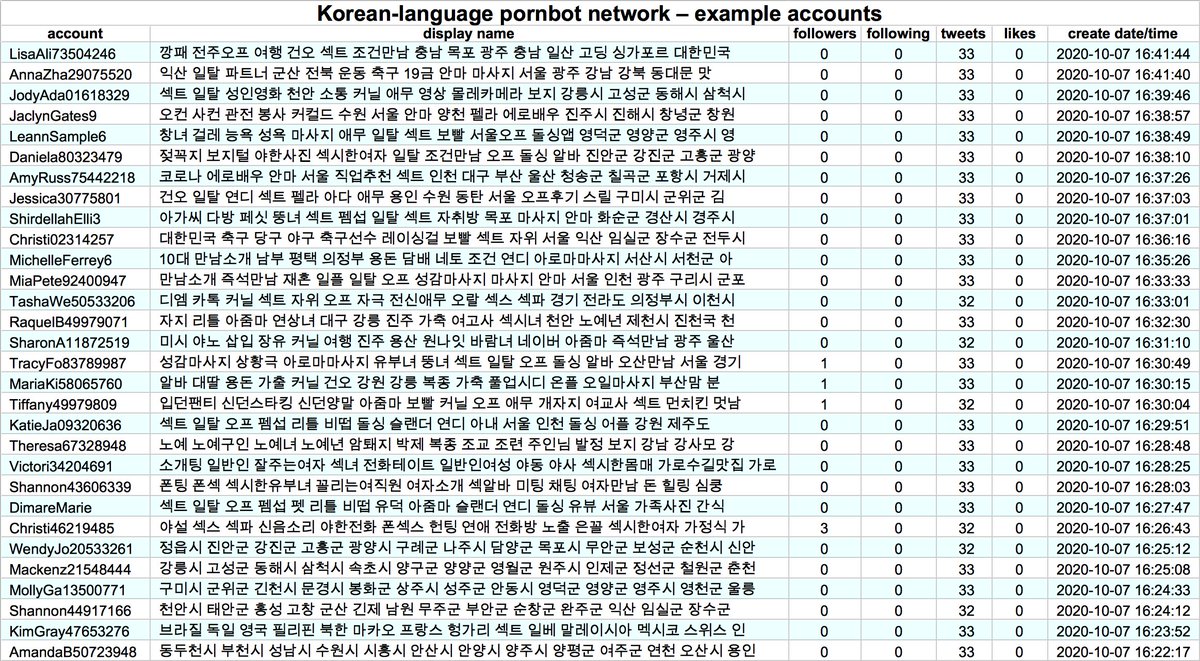
The smaller of the two botnets consists of 76 accounts created in October and November 2020, all (allegedly) tweeting via the Twitter Android App. In an apparent lapse of creativity on the part of the botnet operators, 36 of the accounts are named either "Barb" or "Barbara". 

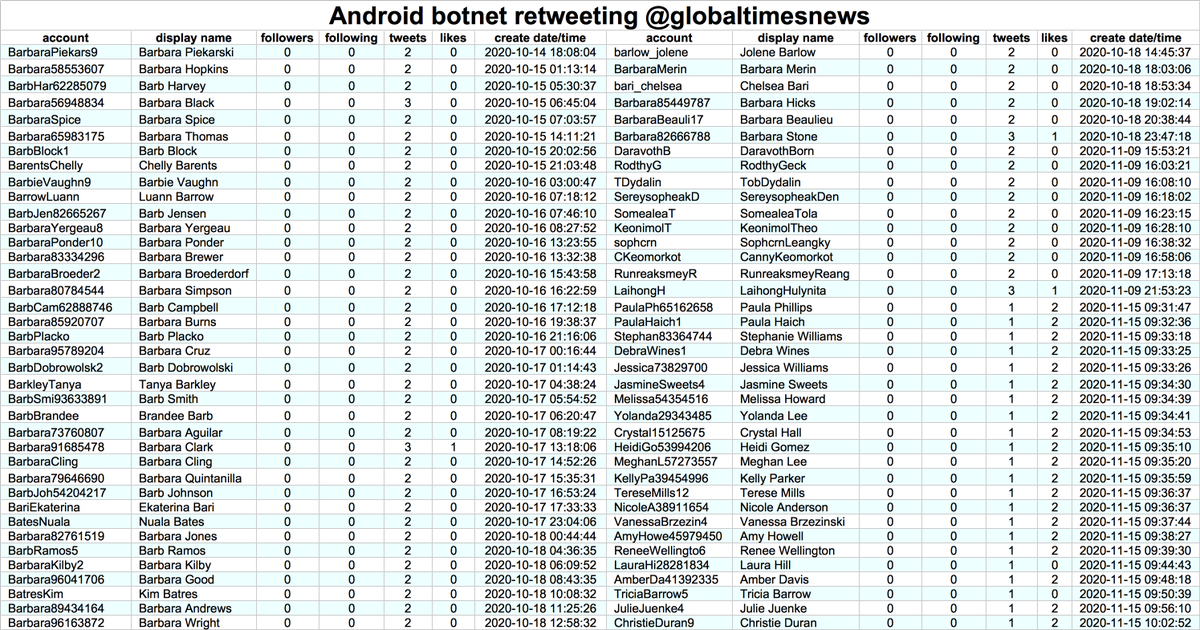
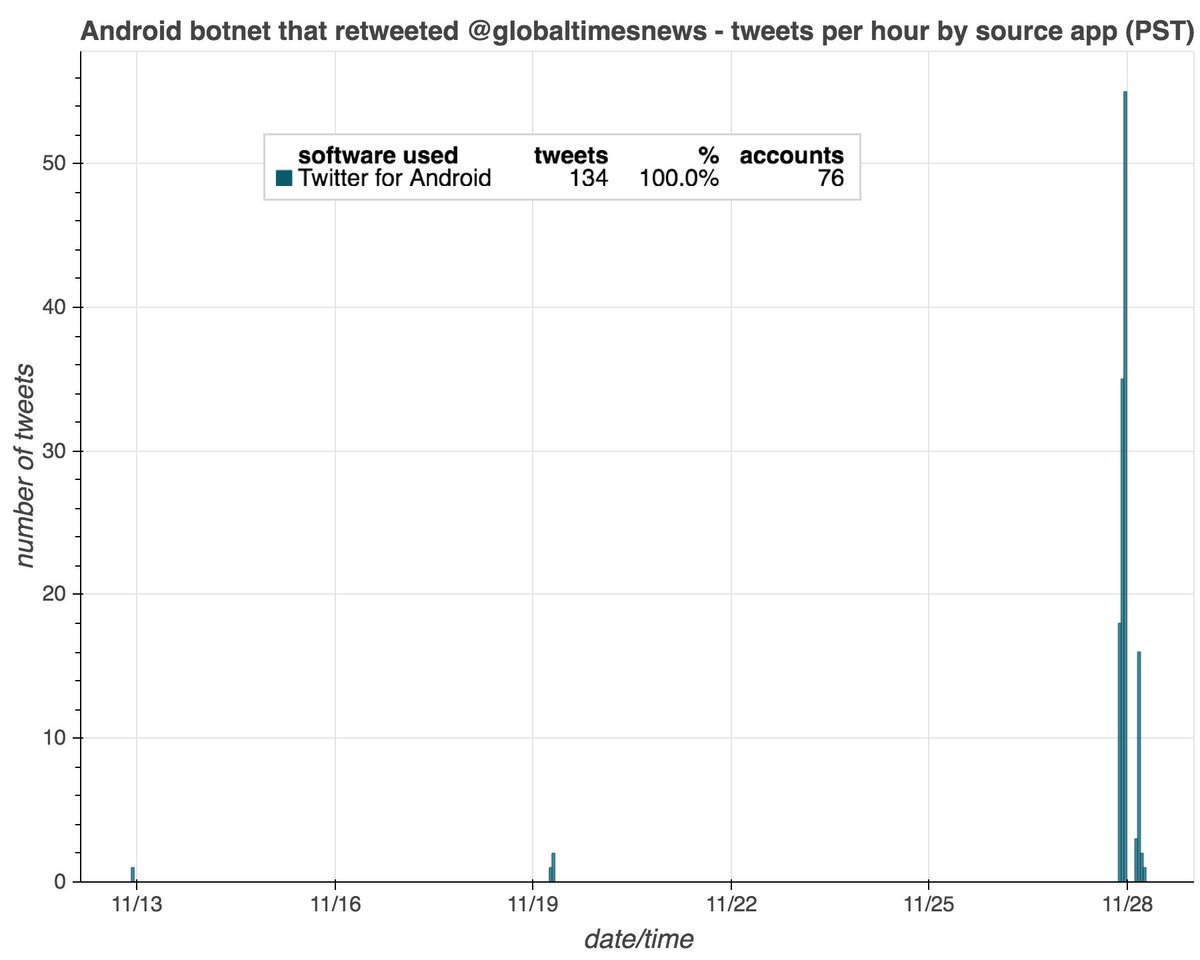
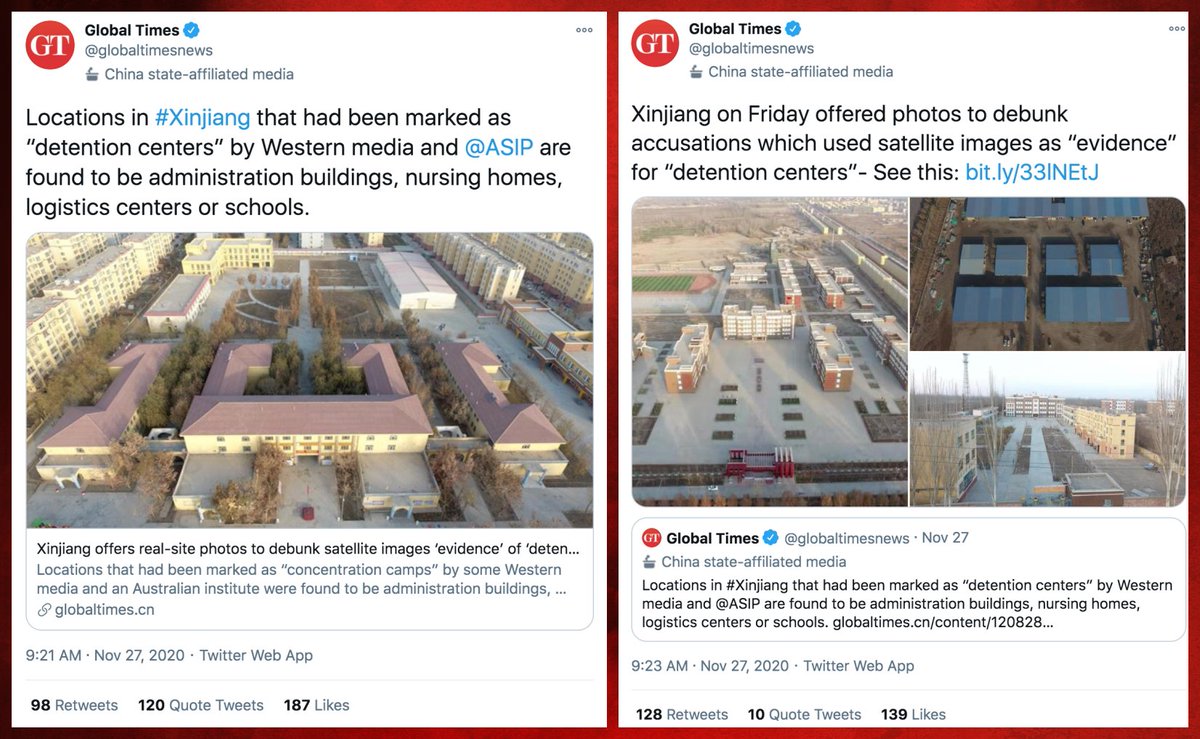
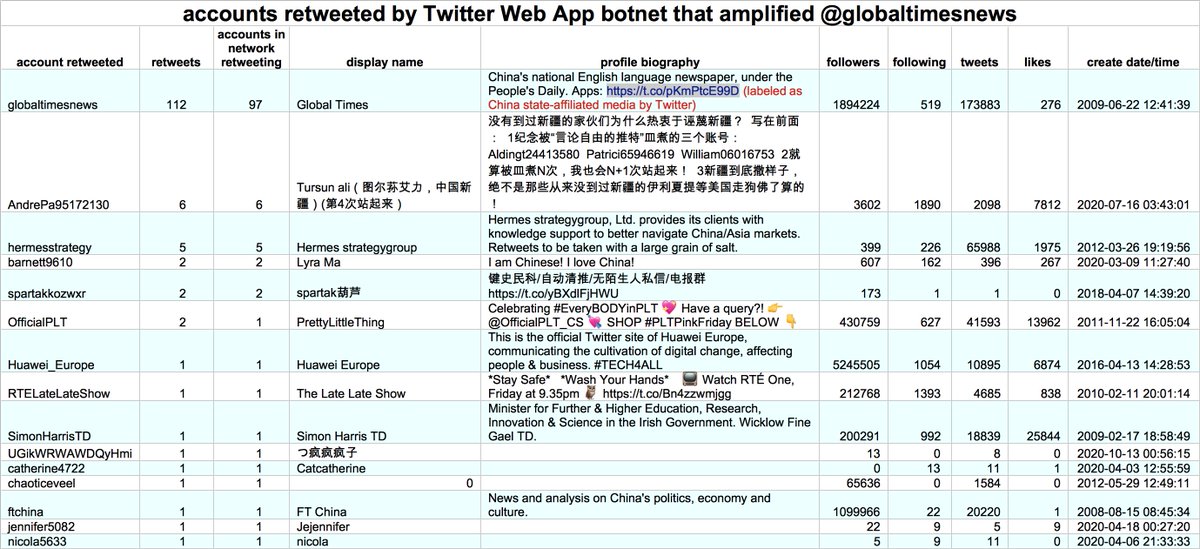
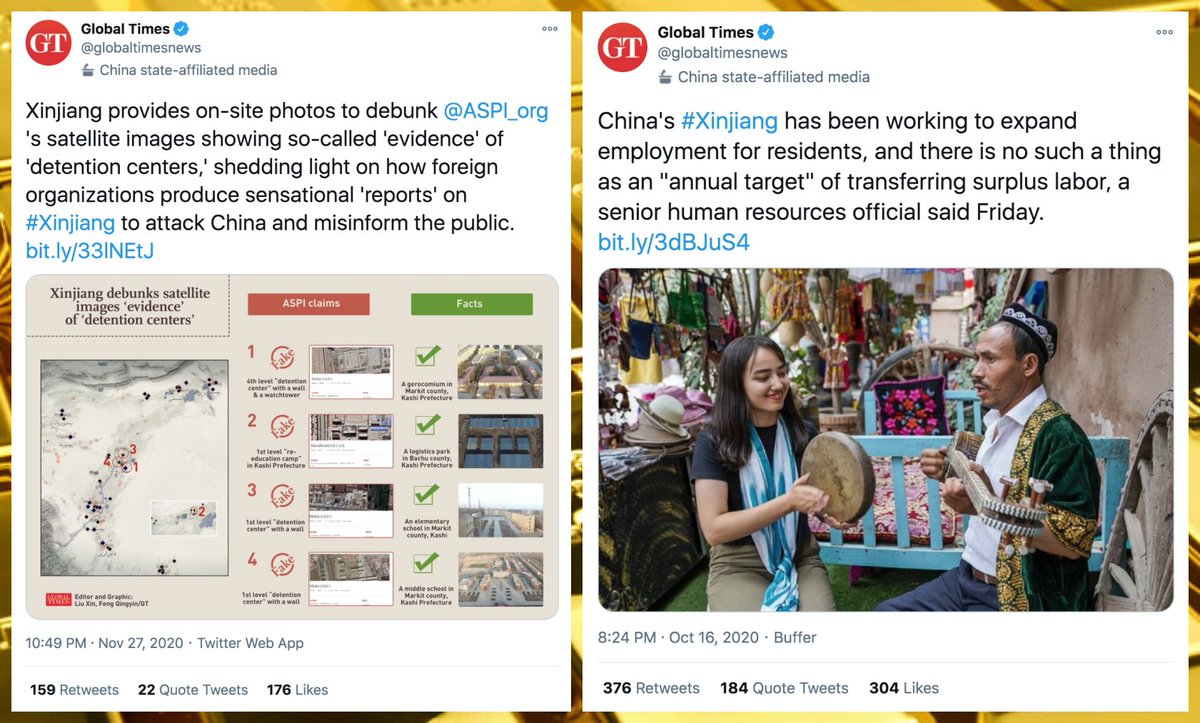
What does this botnet do? Almost all of its content (130 of 134 tweets) consists of retweets of two @globaltimesnews tweets supposedly "debunking" the existence of detention centers in Xinjiang.
(debunking of the "debunking" here:
(debunking of the "debunking" here:
https://twitter.com/Nrg8000/status/1332637550586912768)
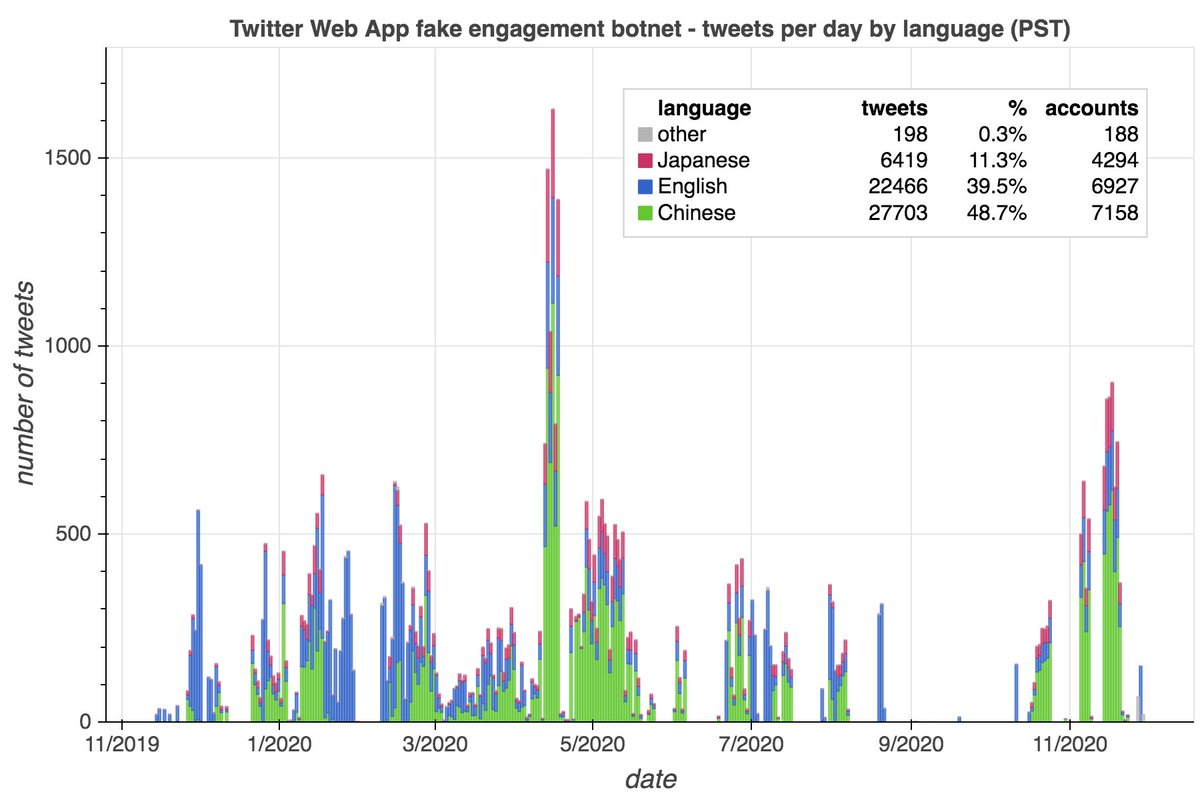
The larger of the two botnets that amplified @globaltimesnews consists of 7258 accounts created between November 2019 and April 2020. All have lowercase names ending in 2 to 4 numbers, and tweet exclusively via the Twitter Web App. 


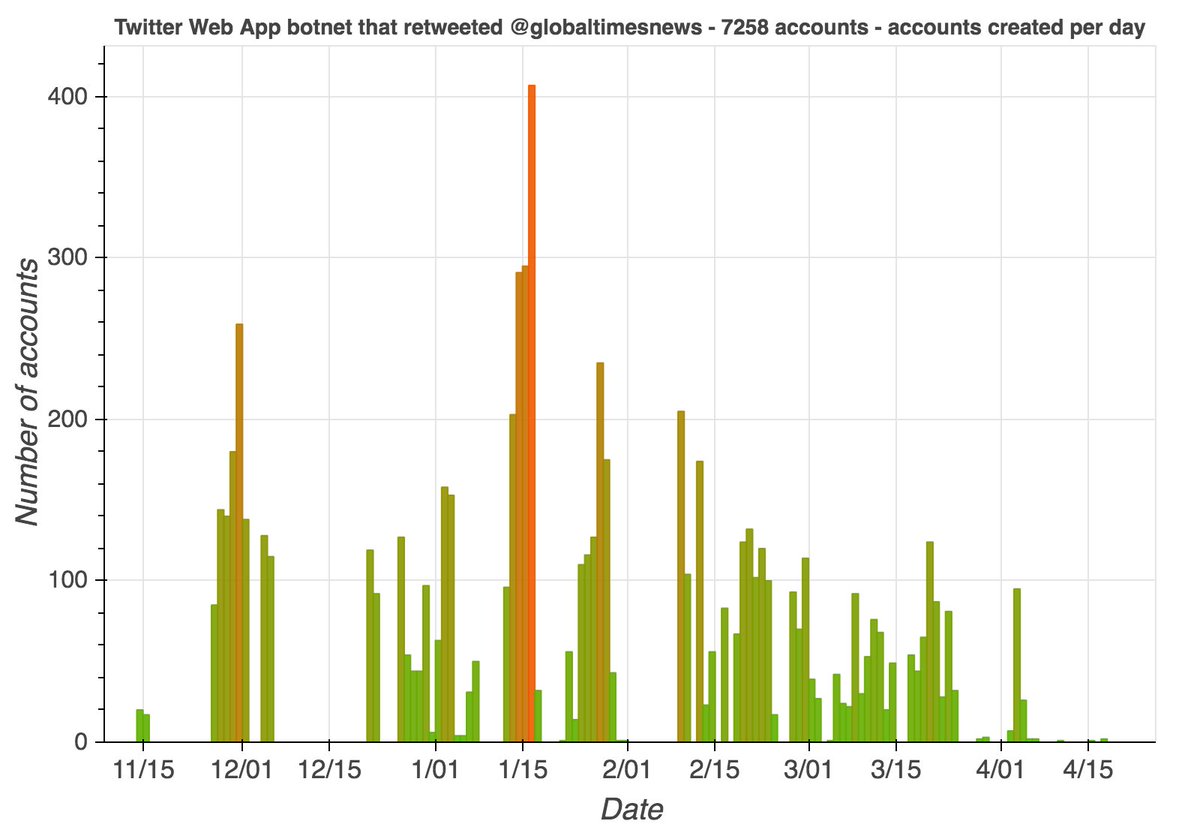
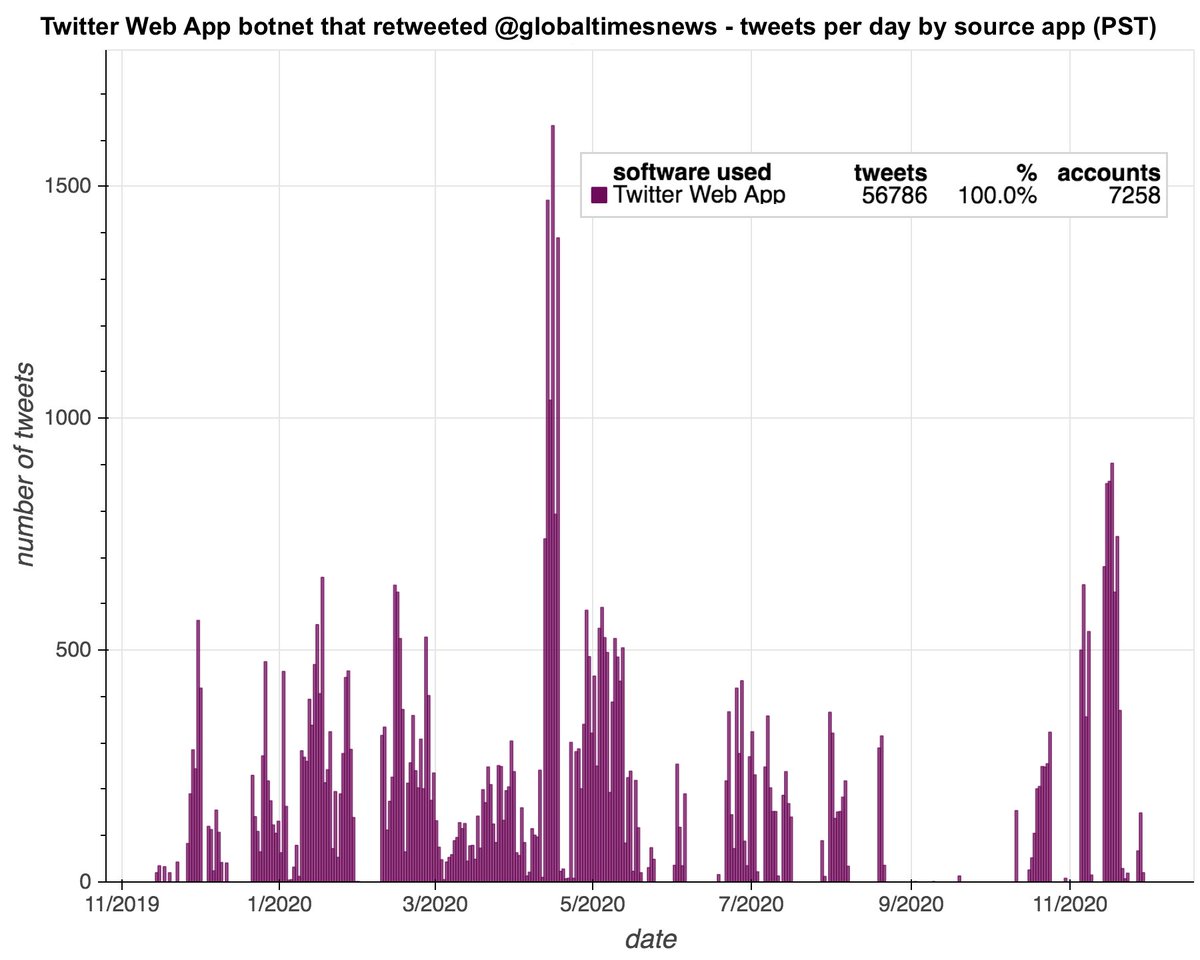
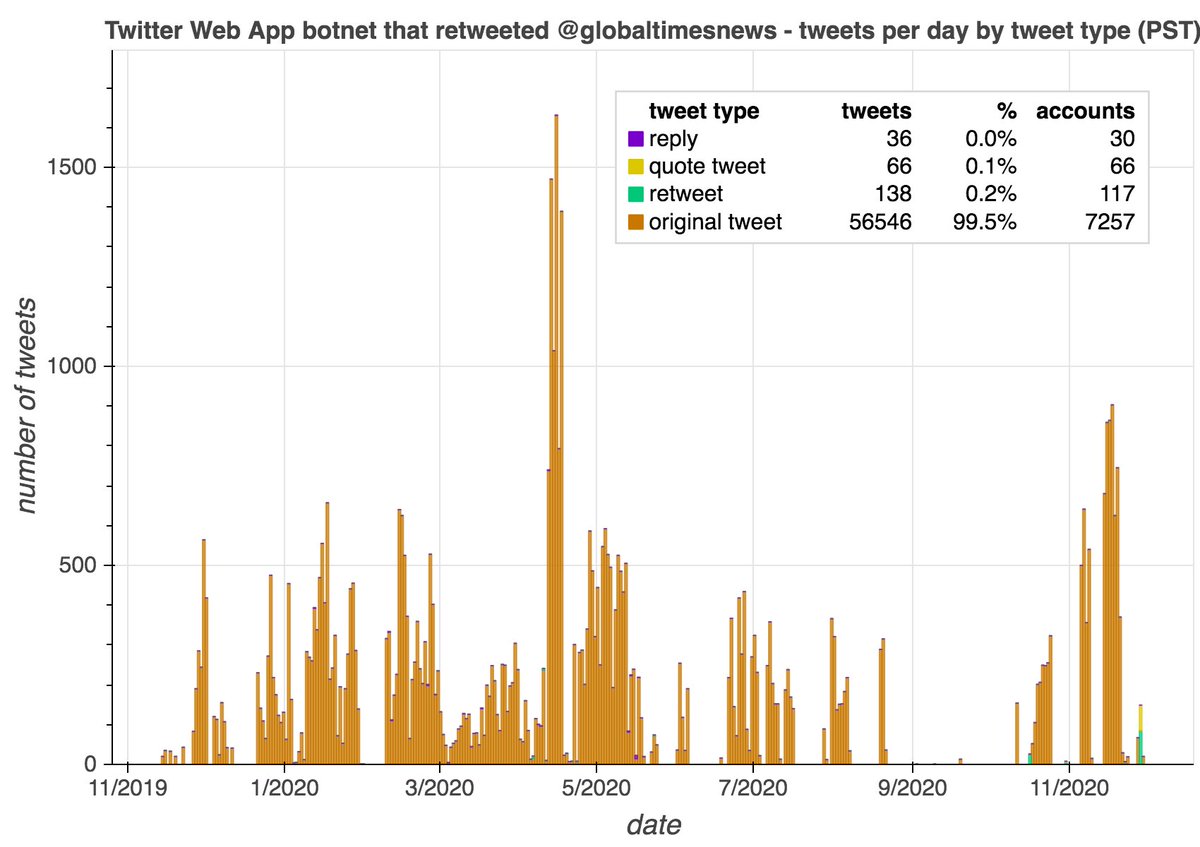
The majority of this botnet's content to date is original tweets rather than retweets. Almost all of its retweets thus far are retweets of one of two @globaltimesnews tweets. As with the first botnet, both of the @globaltimesnews tweets it amplified are related to Xinjiang. 


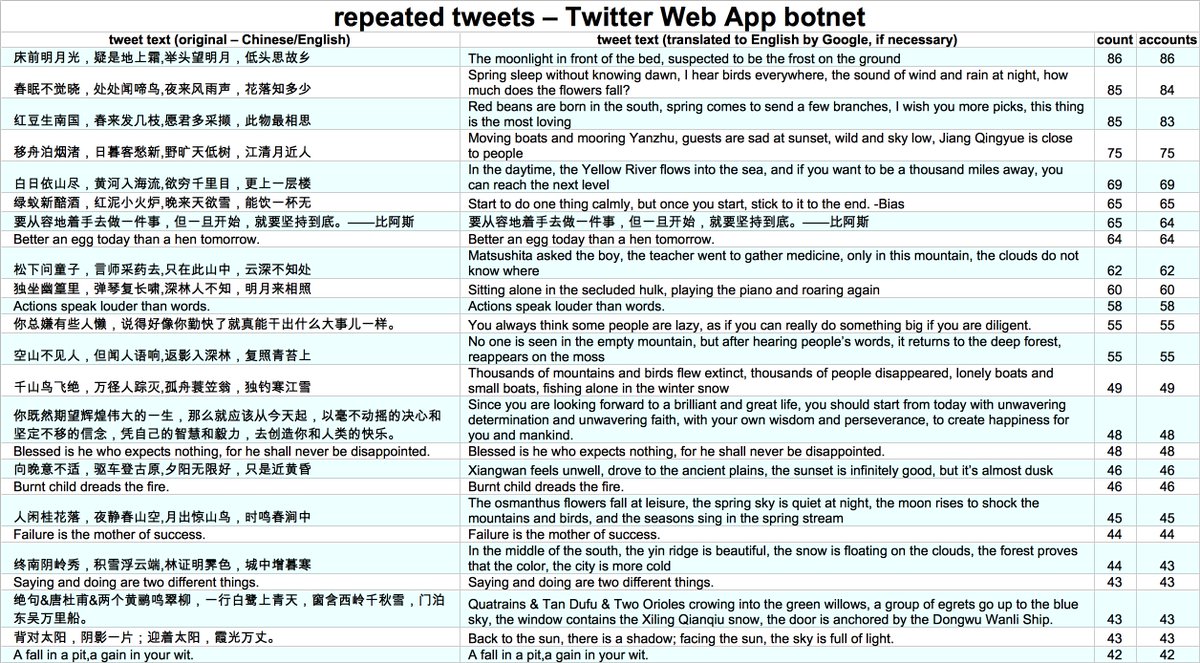
The original tweets produced by this botnet are repetitive, with many duplicated across dozens of accounts. They appear to be sayings/aphorisms in both Chinese and English rather than news/political tweets. (As always, skepticism of Google Translate output is warranted.) 

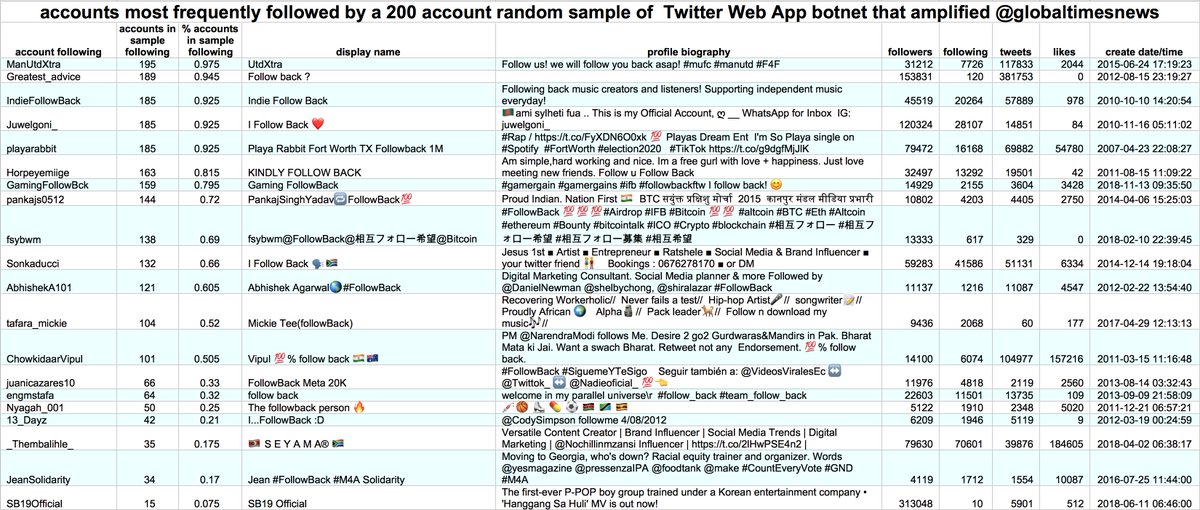
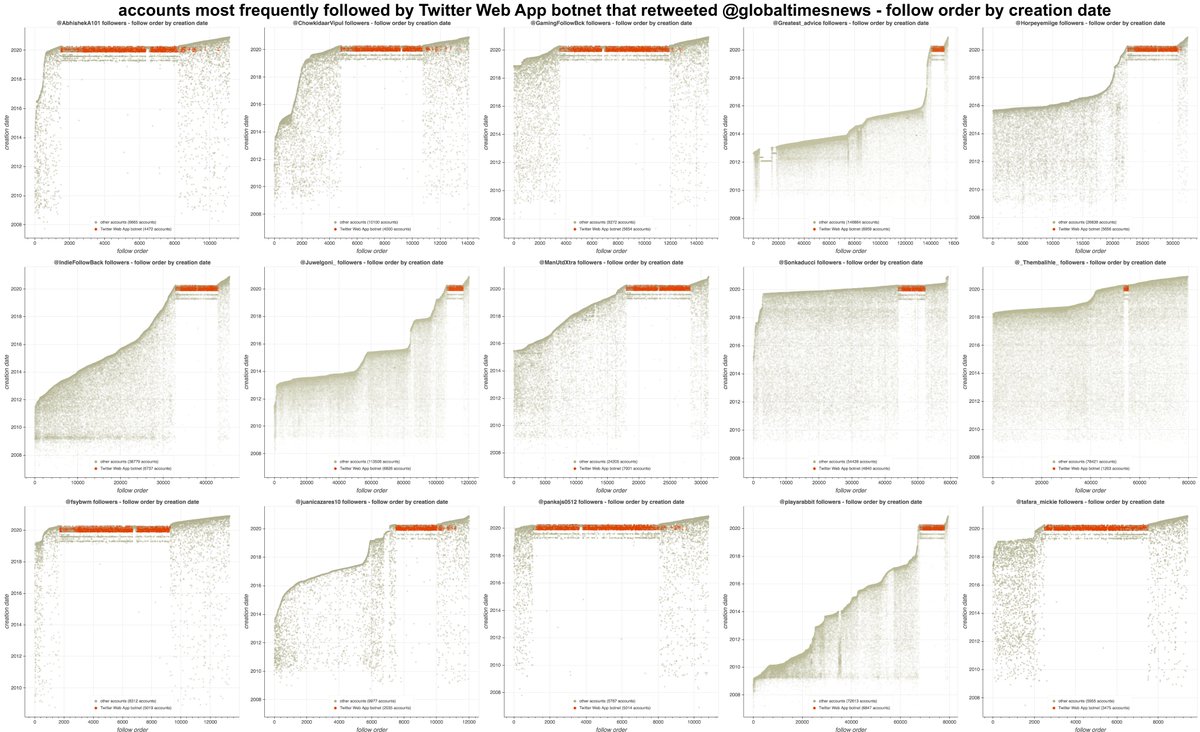
In addition to tweeting random sayings and retweeting @globaltimesnews, this botnet also followed a bunch of accounts en masse. Many of them appear to be large followback accounts, although they mostly didn't follow the bots back. 

H/T @Nrg8000 for drawing our attention to these botnets:
https://twitter.com/Nrg8000/status/1332662954622238720
• • •
Missing some Tweet in this thread? You can try to
force a refresh