Can one use search engines to find Twitter accounts with GAN-generated profile pics? #ThanksgivingShenaniGANs
(GAN = "generative adversarial network", the AI technology behind websites like thispersondoesnotexist.com)
cc: @ZellaQuixote
(GAN = "generative adversarial network", the AI technology behind websites like thispersondoesnotexist.com)
cc: @ZellaQuixote
It turns out that when one reverse image searches a GAN-generated face pic, some of the results are other GAN-generated face pics. We used Yandex, as it was more effective than Google and is easier to automate. (This doesn't work with TinEye, which only finds exact matches.) 
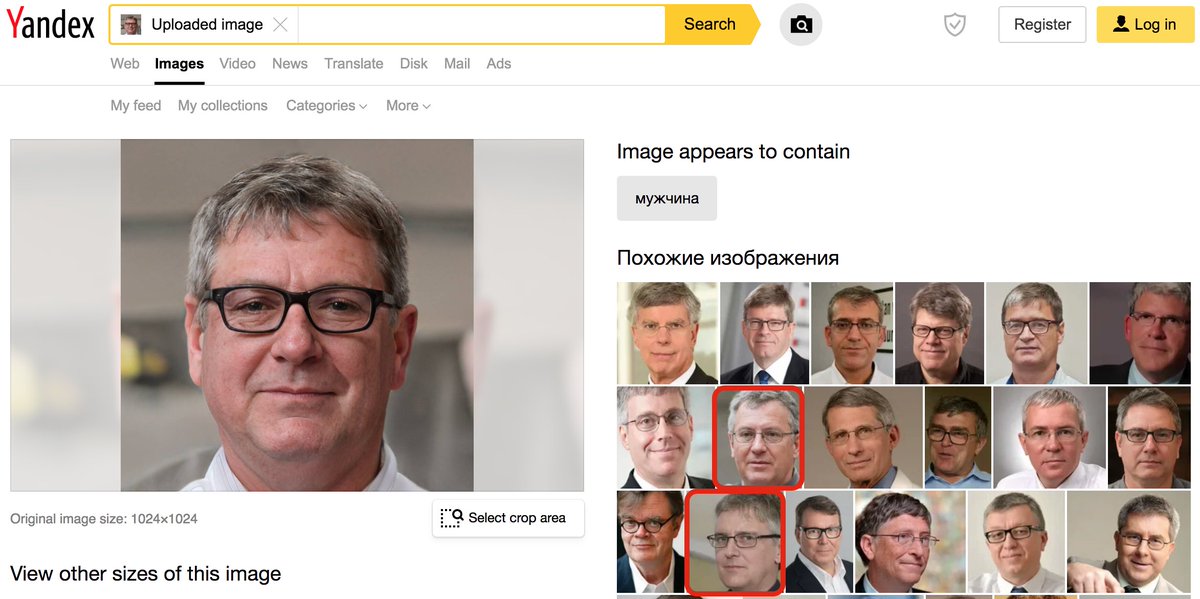
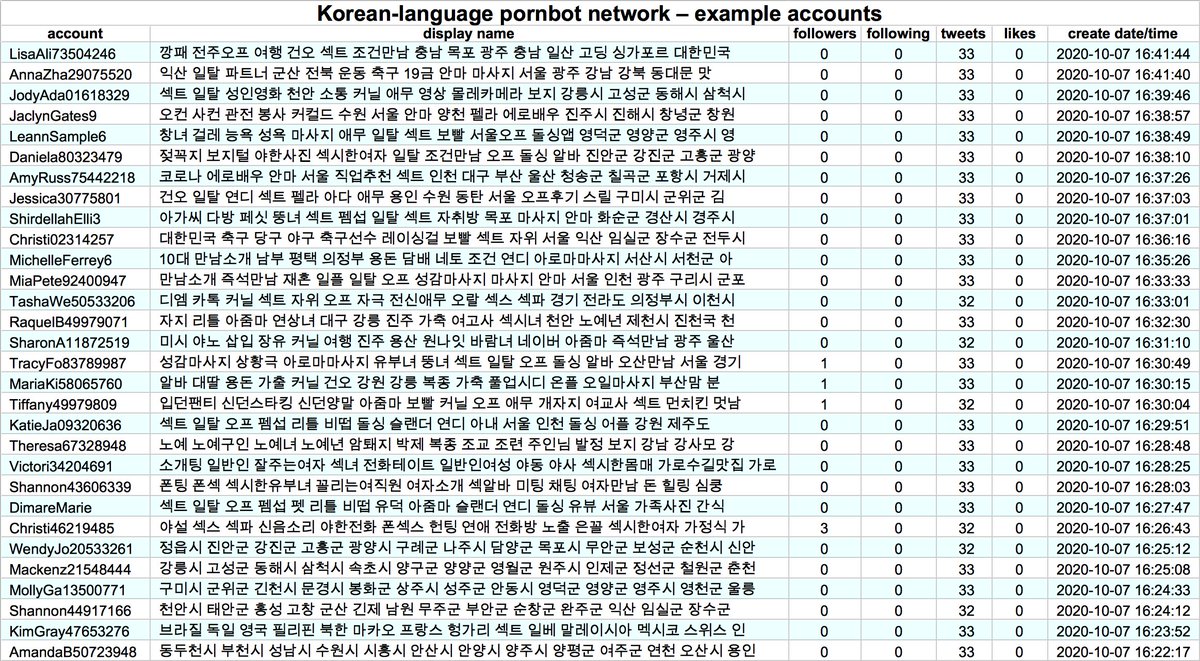
We generated 500 face pics using thispersondoesnotexist(dot)com, reverse searched them using Yandex, and filtered the results to Twitter profile pics, yielding 35 accounts (plus a few suspended ones). As usual, the major facial features are in the same place on each image. 




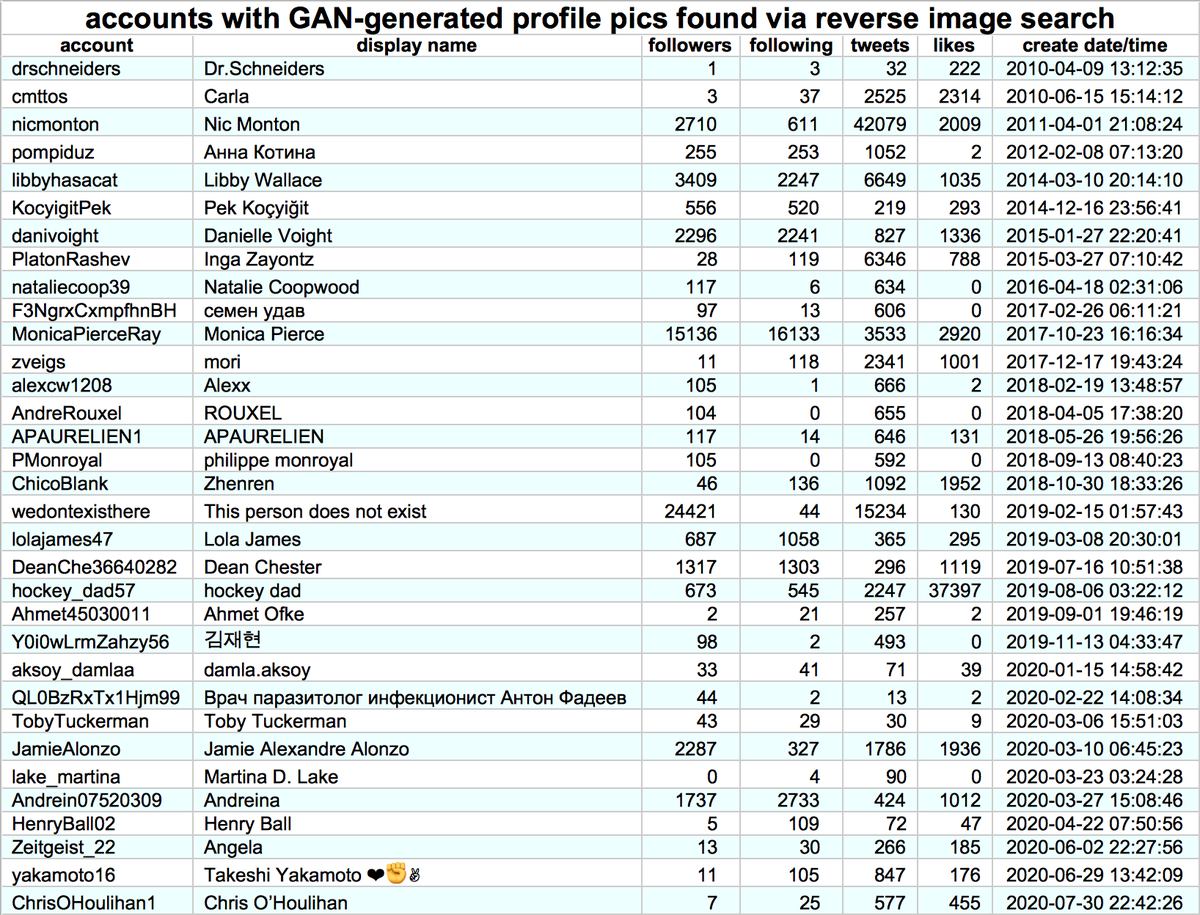
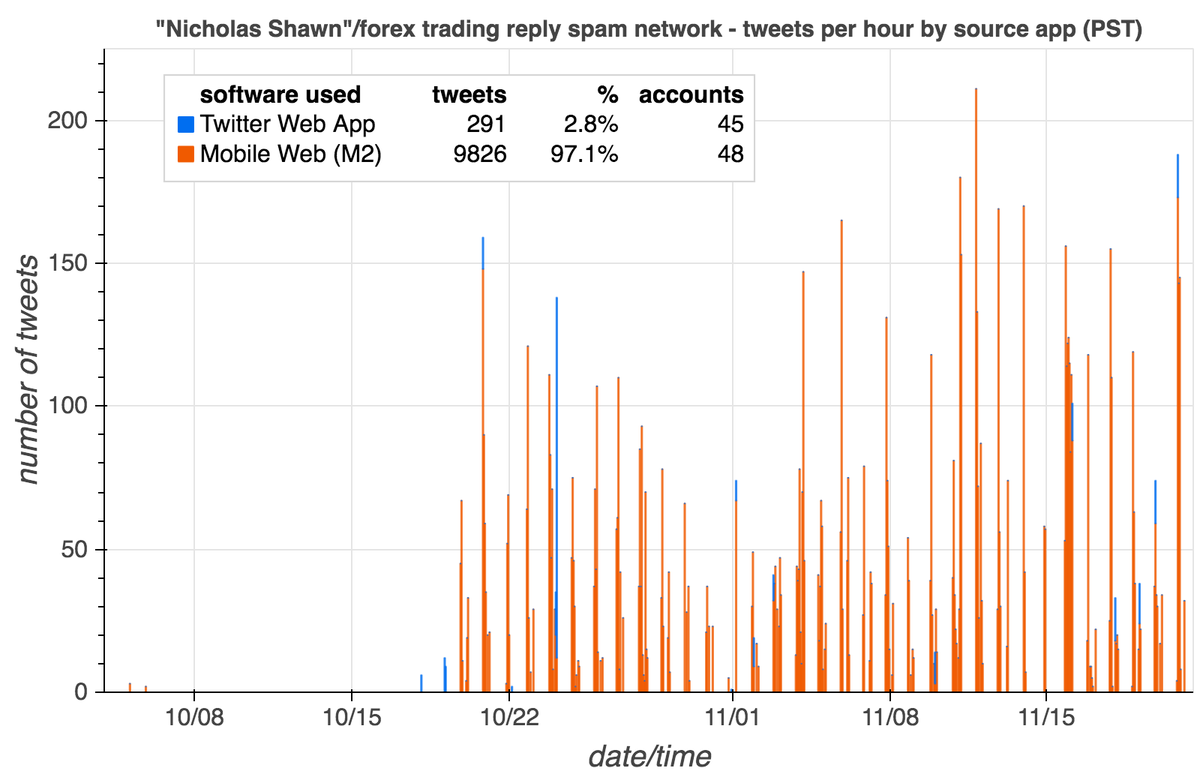
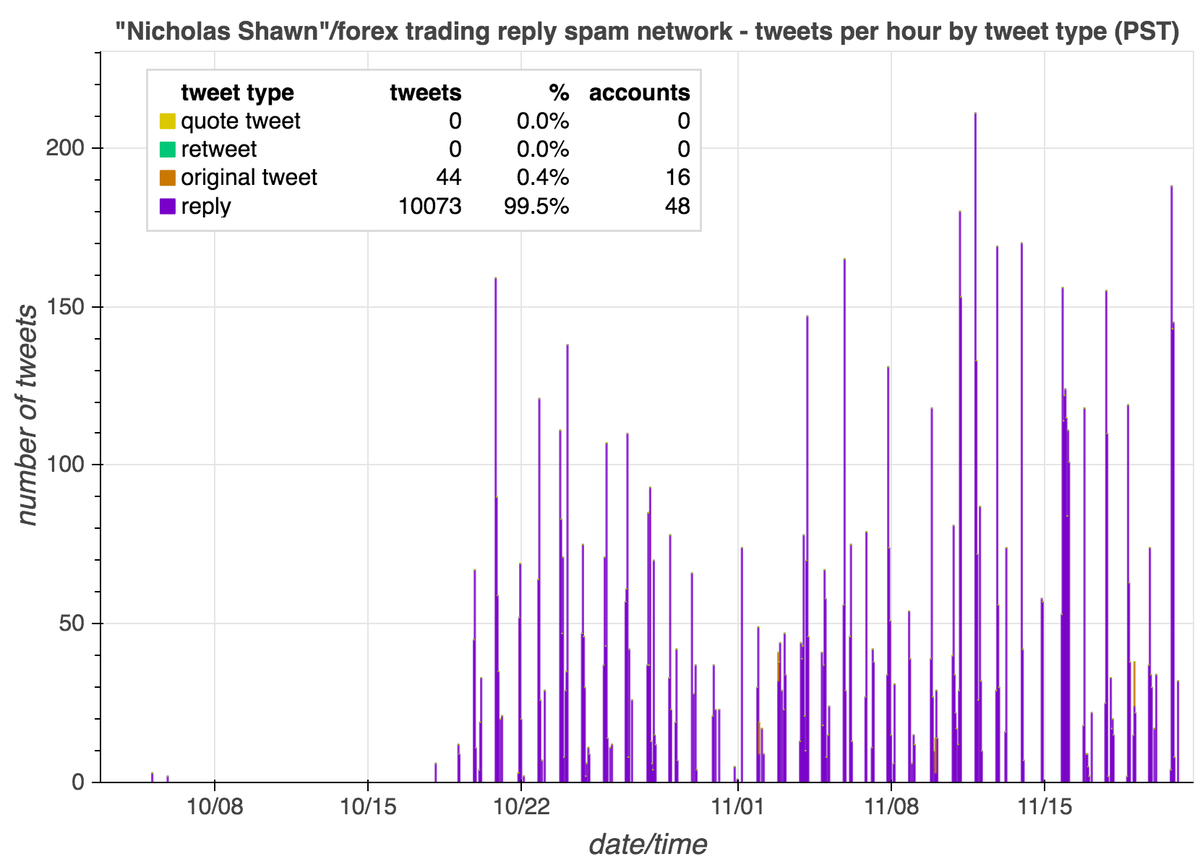
Although most of the accounts using GAN-generated face pics we found via reverse image search appear to be solo acts, we did find a small botnet. This botnet consists of 7 Russian-language accounts tweeting via Tweetdeck on identical schedules. 



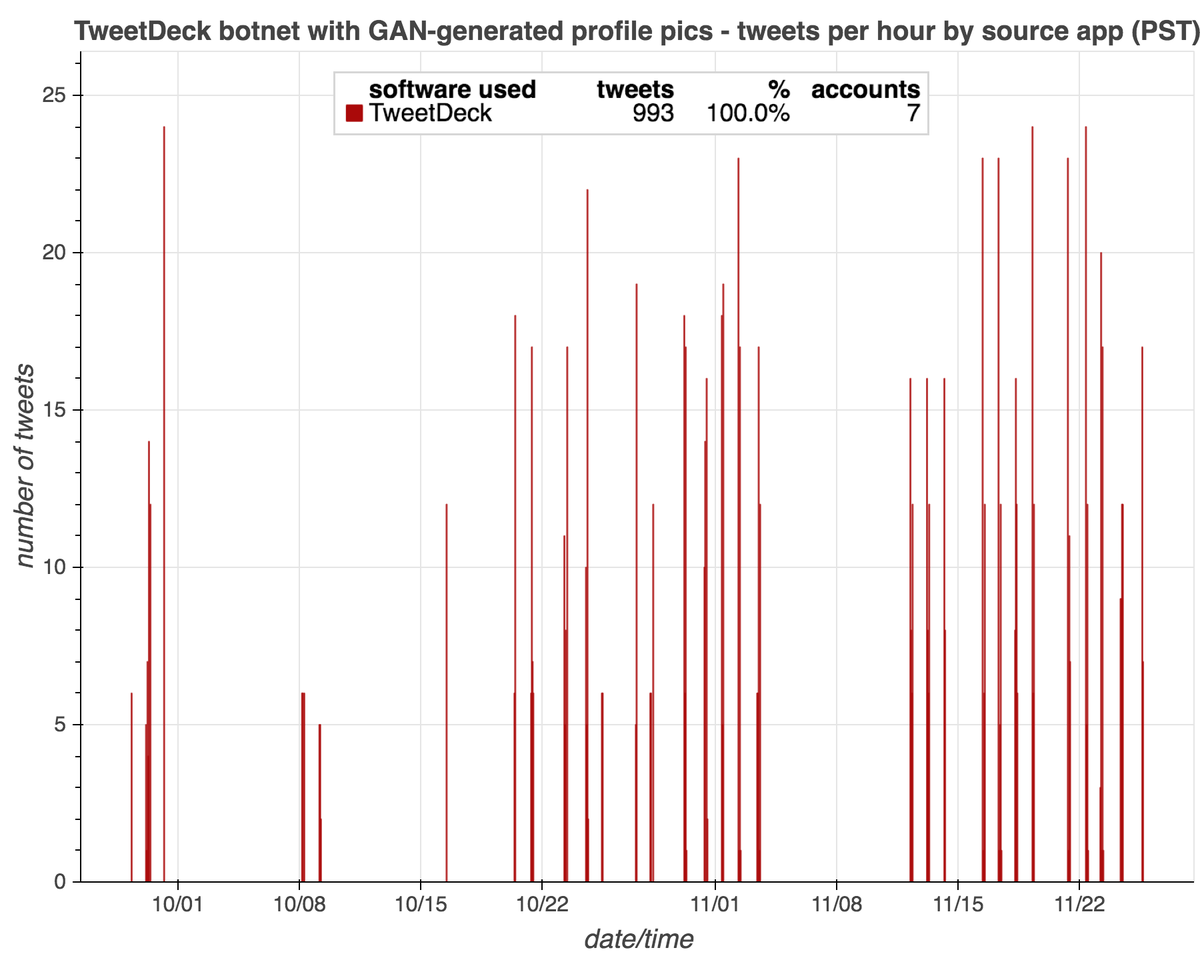
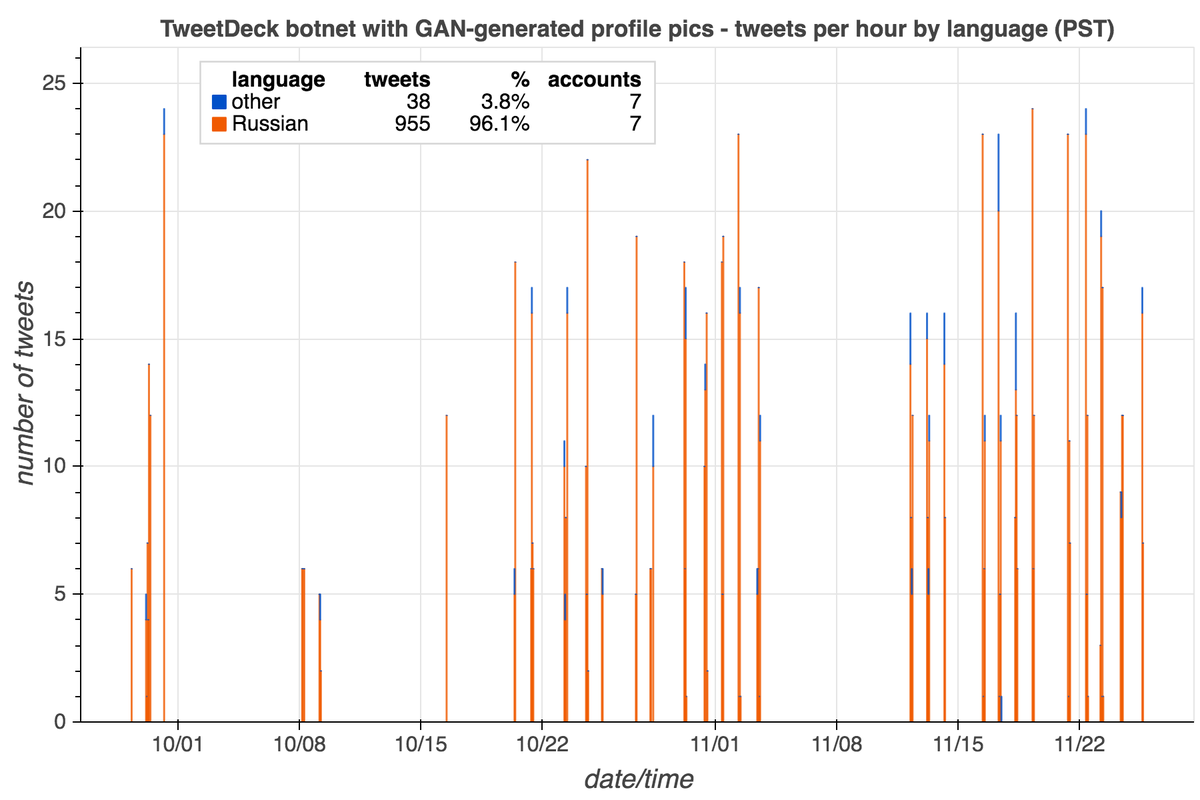
These bots do two things:
• Tweet links to a variety of websites (these appear to be small sites selling various things, with the caveat that we don't speak Russian)
• Tweet sentence fragments, often repeated across accounts

• Tweet links to a variety of websites (these appear to be small sites selling various things, with the caveat that we don't speak Russian)
• Tweet sentence fragments, often repeated across accounts

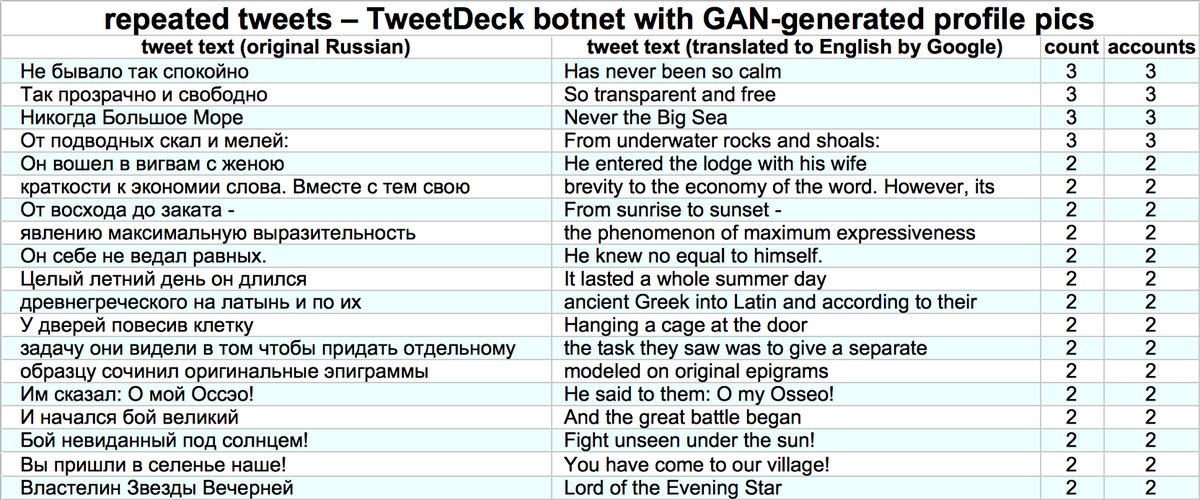
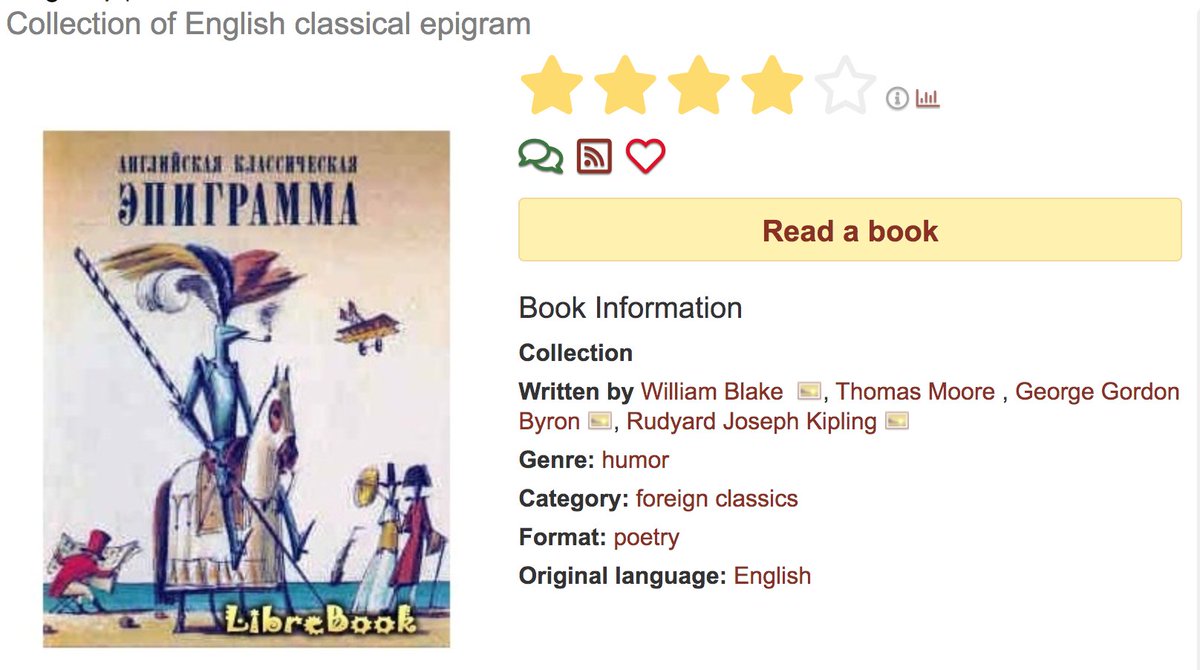
We searched for the origin of the repeated sentence fragment tweets, and they appear to be from a book called "Английская классическая эпиграмма" ("English Classical Epigrams", per Google Translate) that contains Russian translations of text from famous English authors. 


(Some other threads on GAN-generated profile pics and their use on Twitter, for those interested in further reading material)
https://twitter.com/conspirator0/status/1322704400226394112
• • •
Missing some Tweet in this thread? You can try to
force a refresh