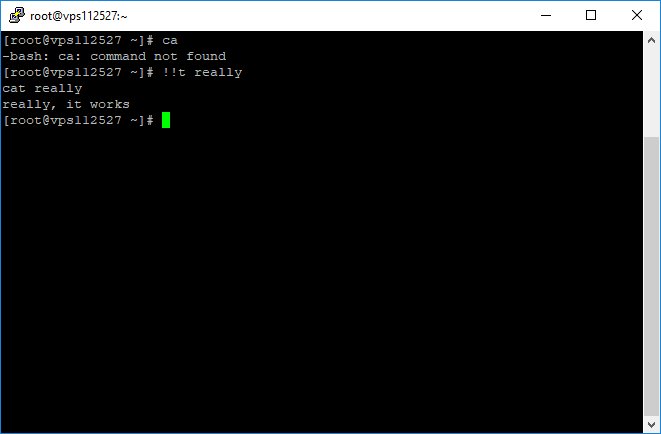
netstat -nalp
#DFIR #threathunting #forensics
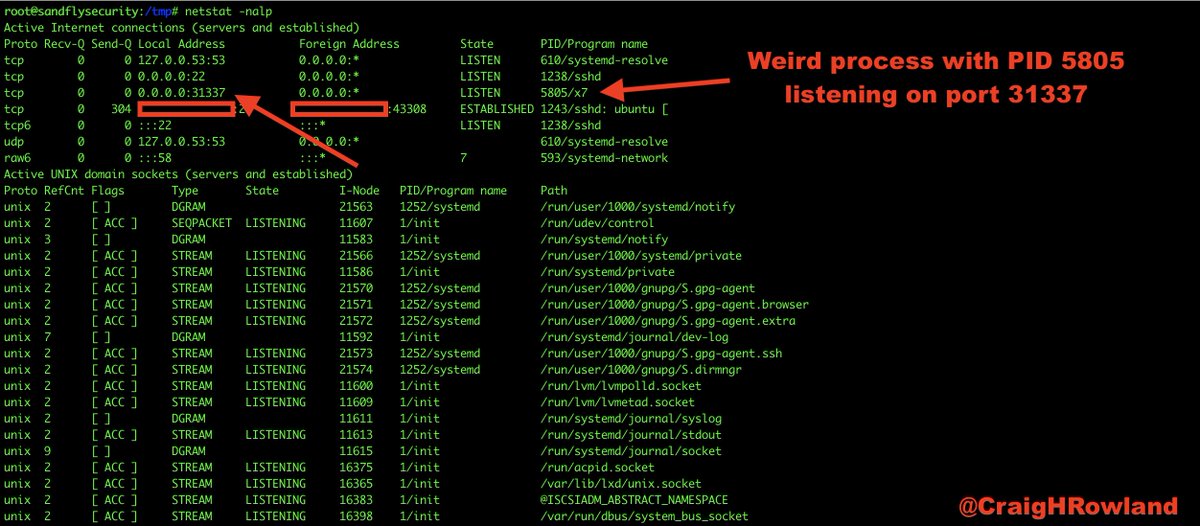
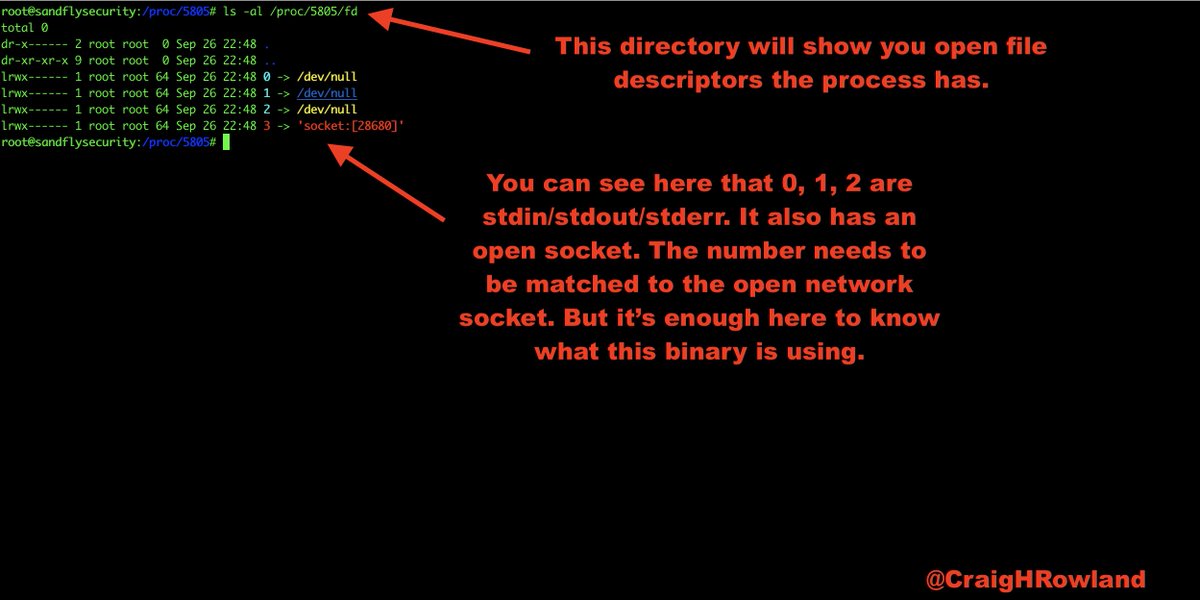
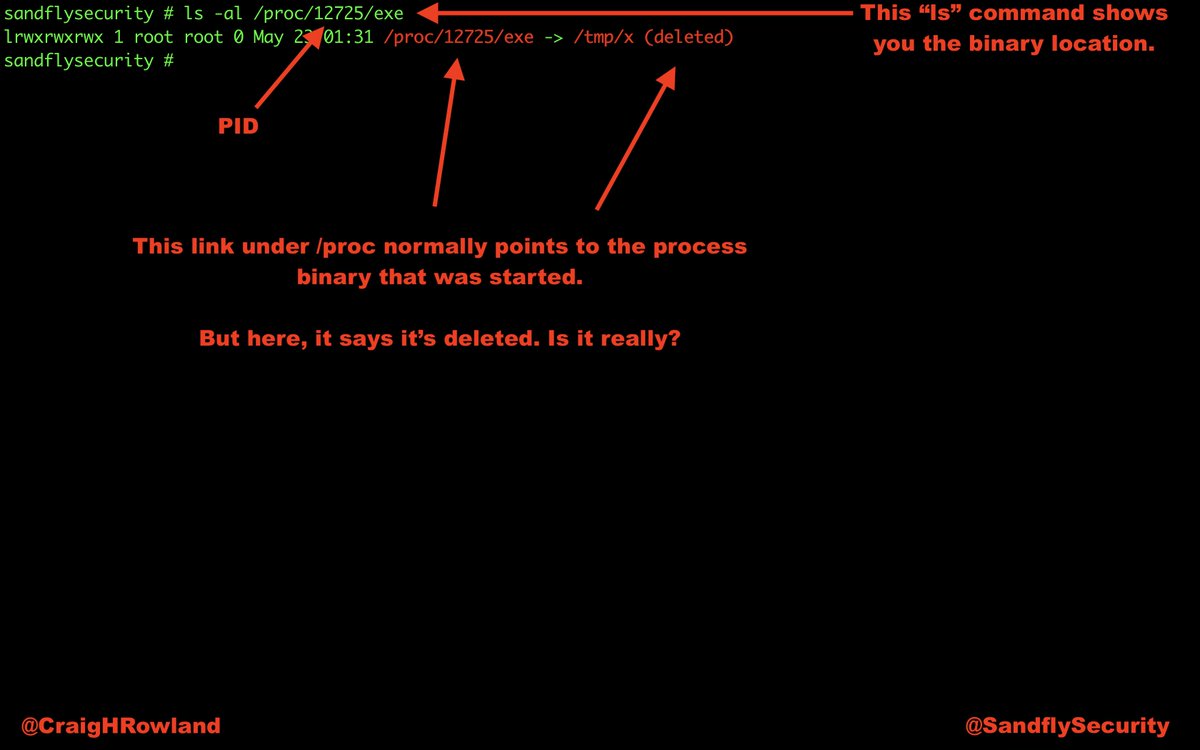
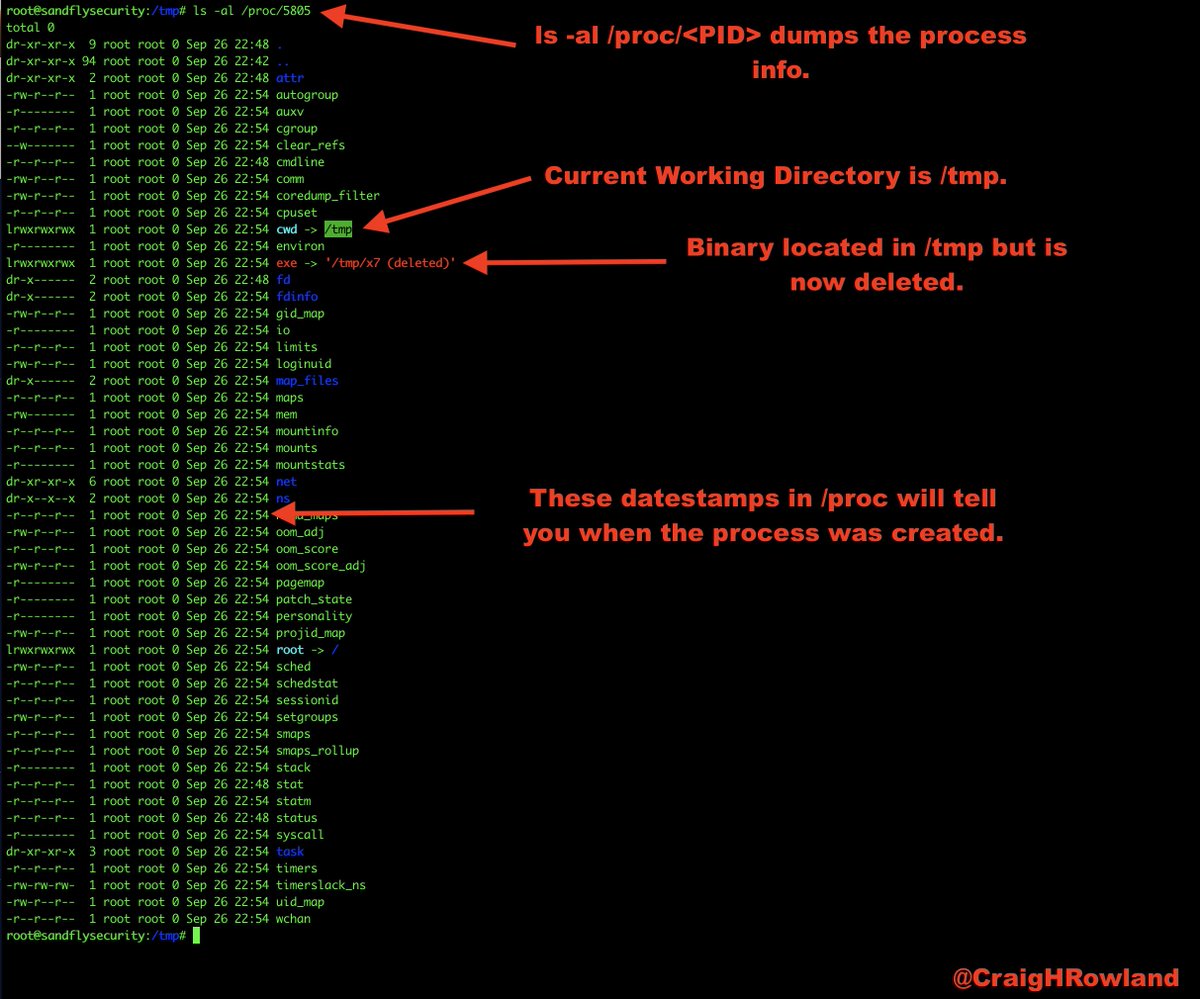
ls -al /proc/5805
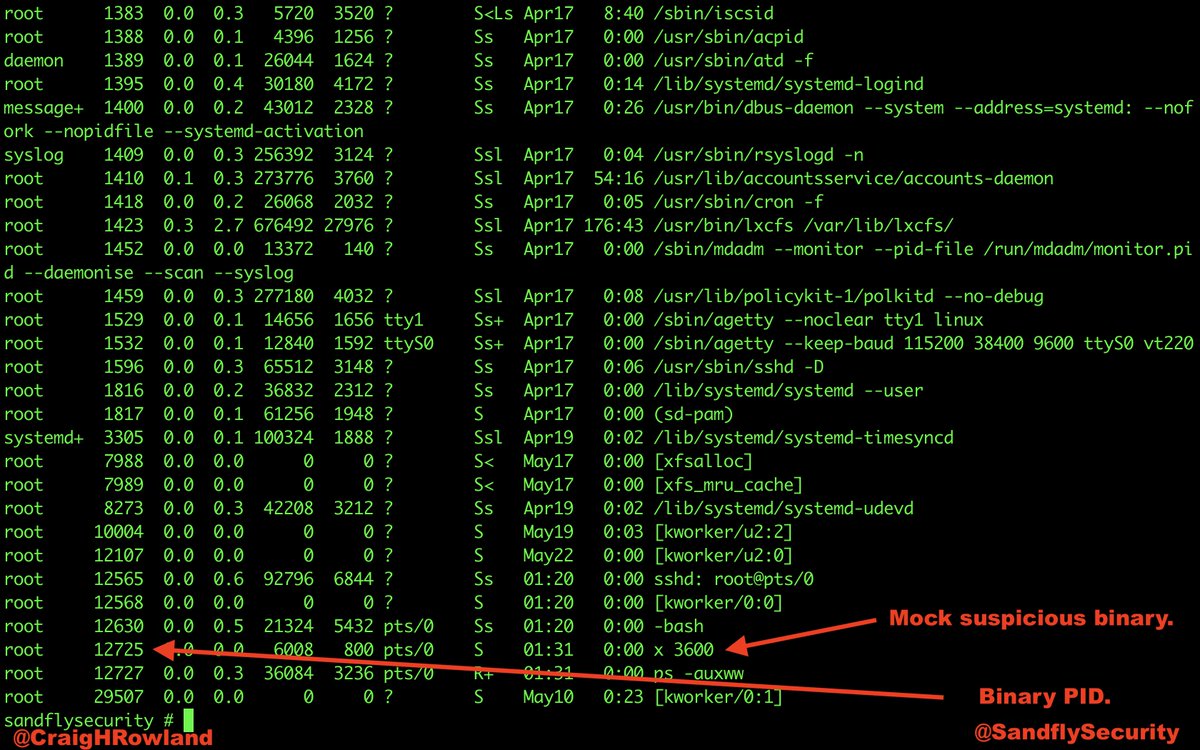
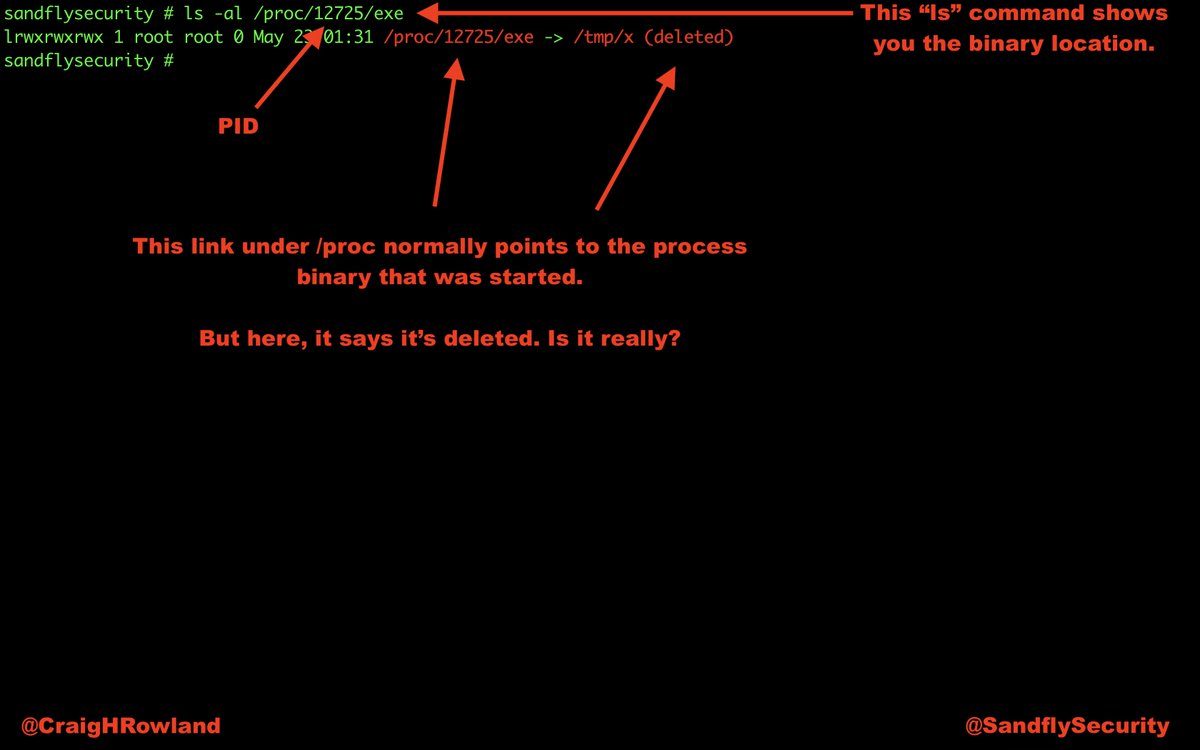
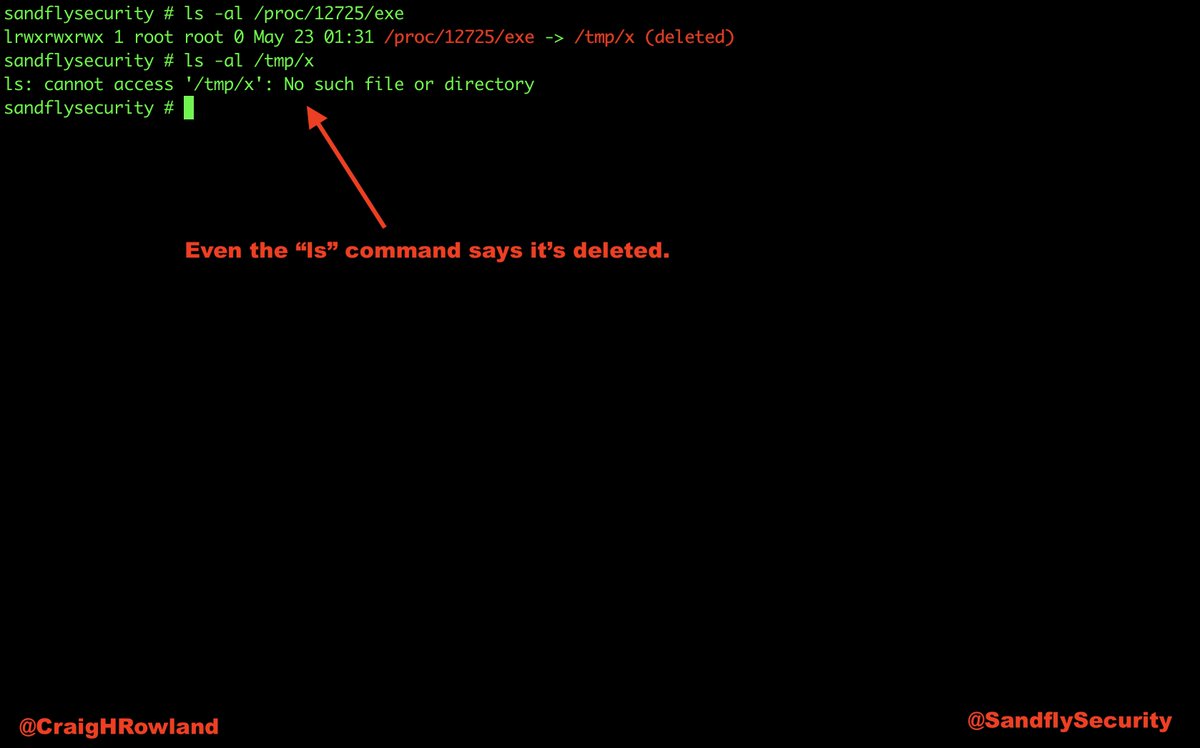
The current working directory is /tmp. The binary was in /tmp, but was deleted. A lot of exploits work out of /tmp and /dev/shm on Linux. This is a major red flag. #DFIR
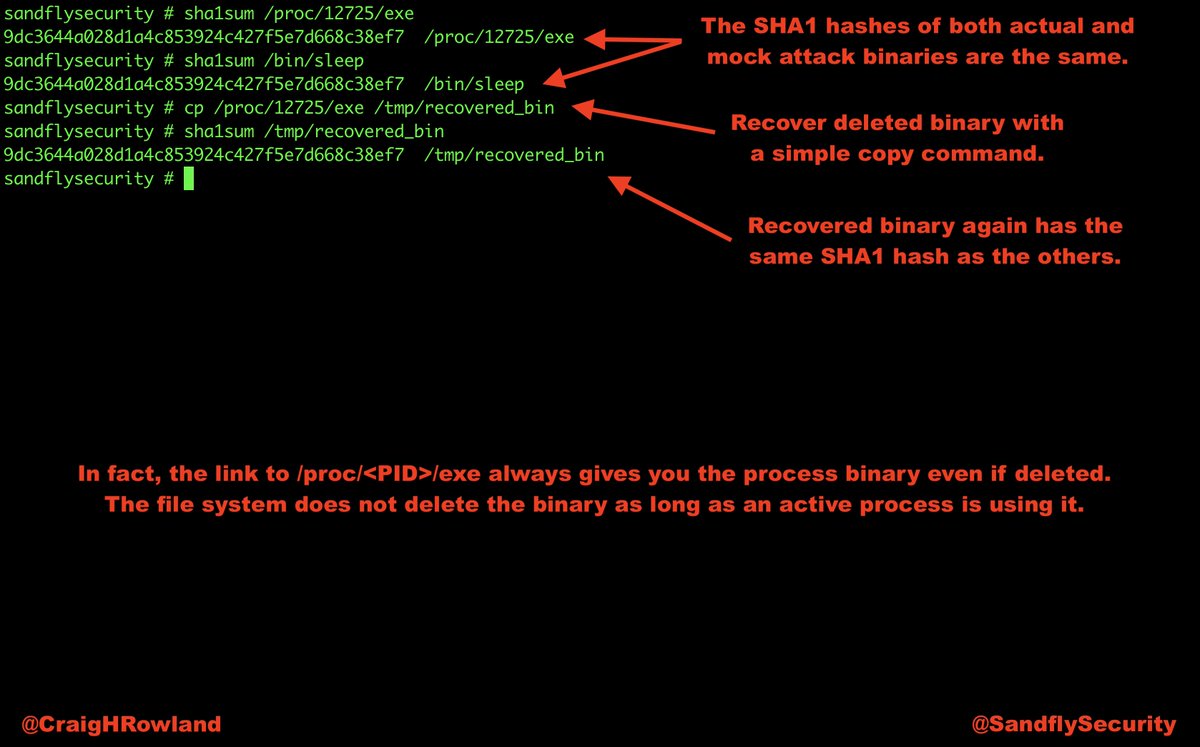
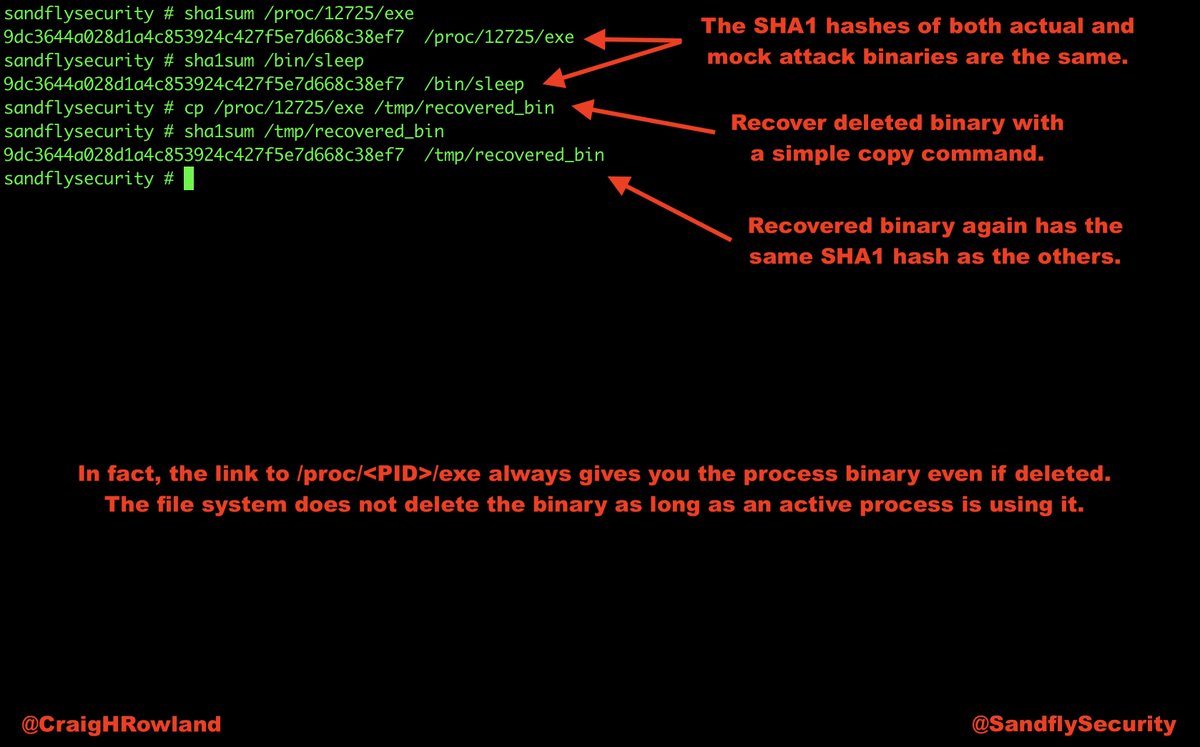
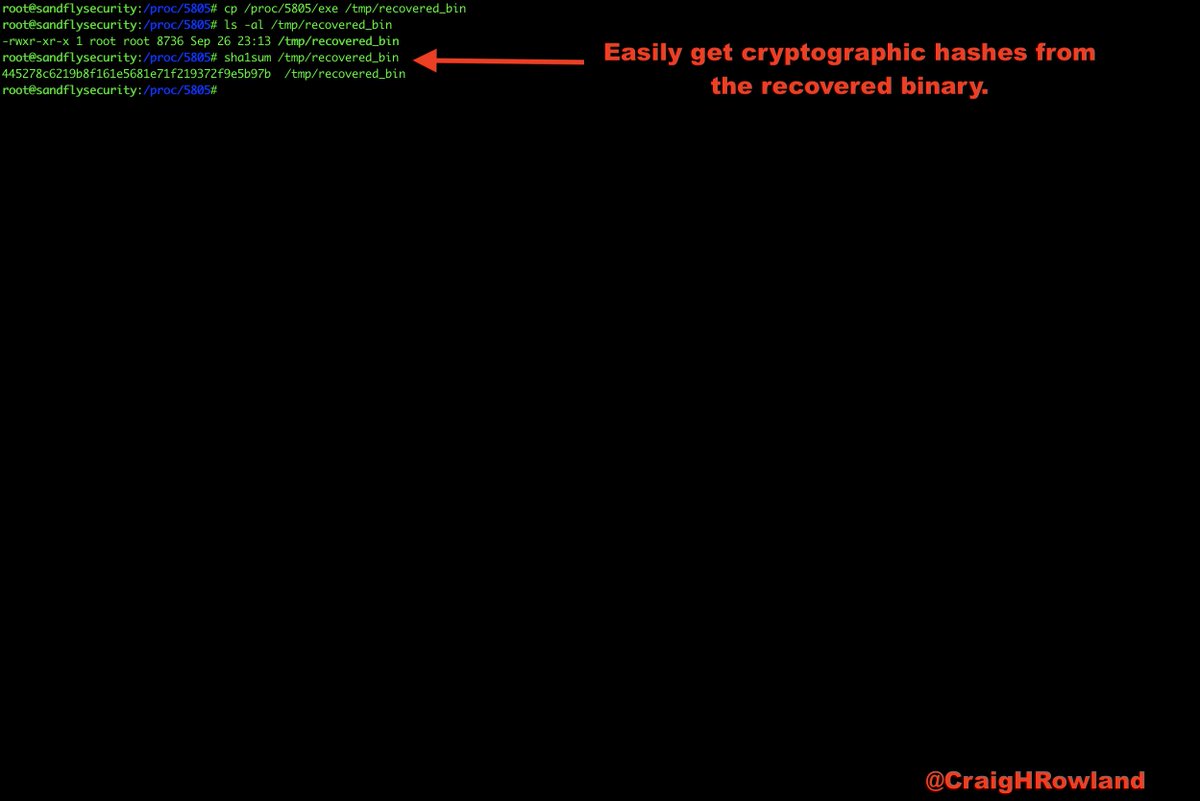
cp /proc/<PID>/exe /destination_dir/recovered_bin
#DFIR

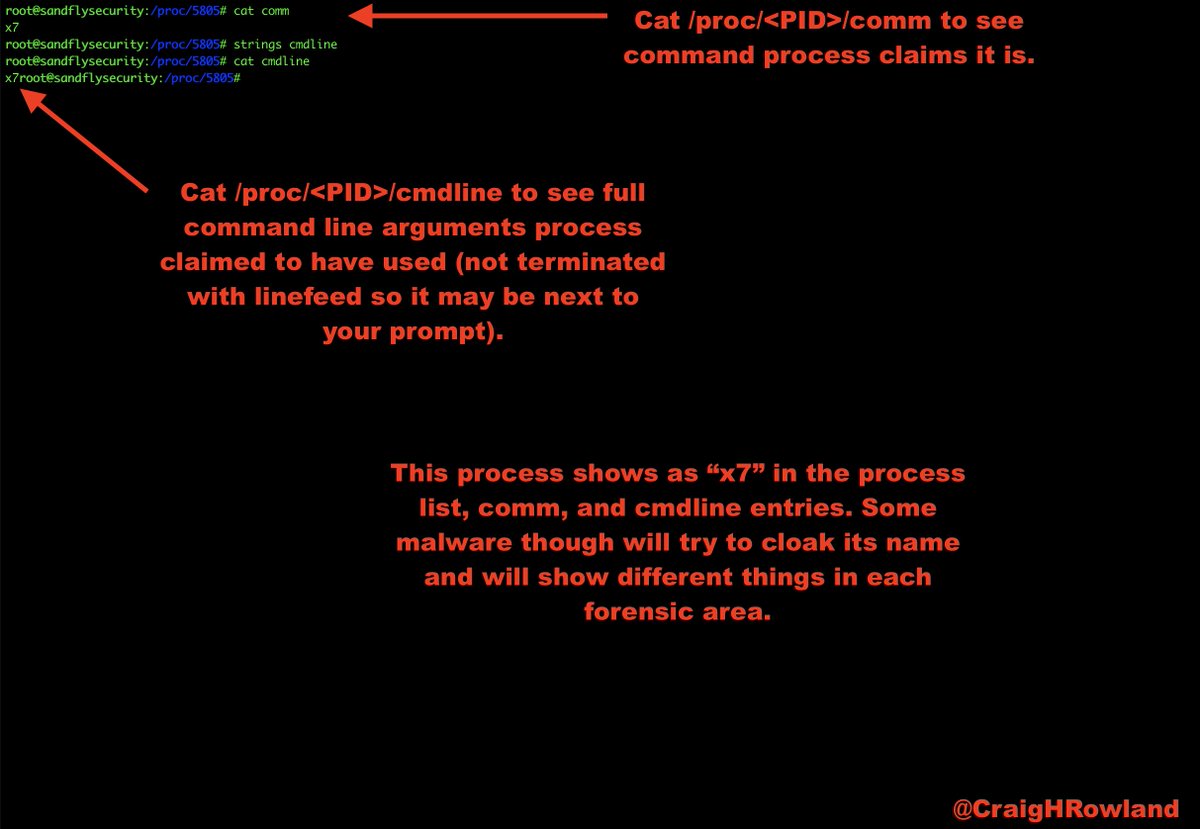
cat /proc/<PID>/comm
cat /proc/<PID>/cmdline
#DFIR
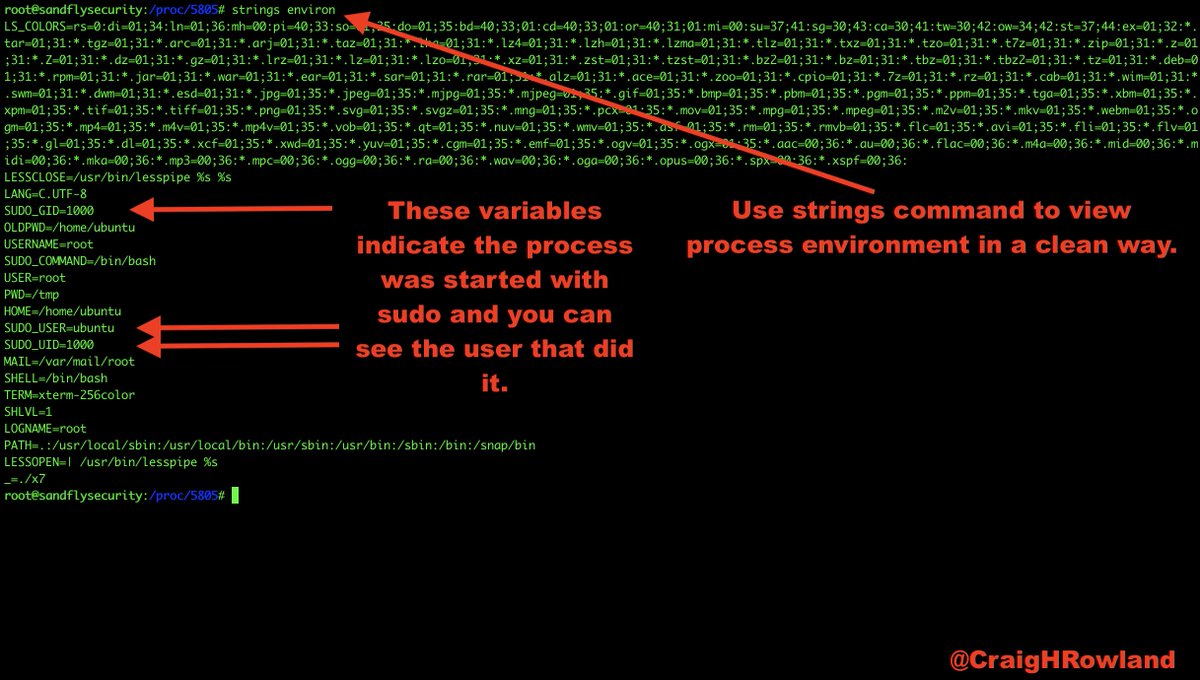
strings /proc/<PID>/environ
#DFIR
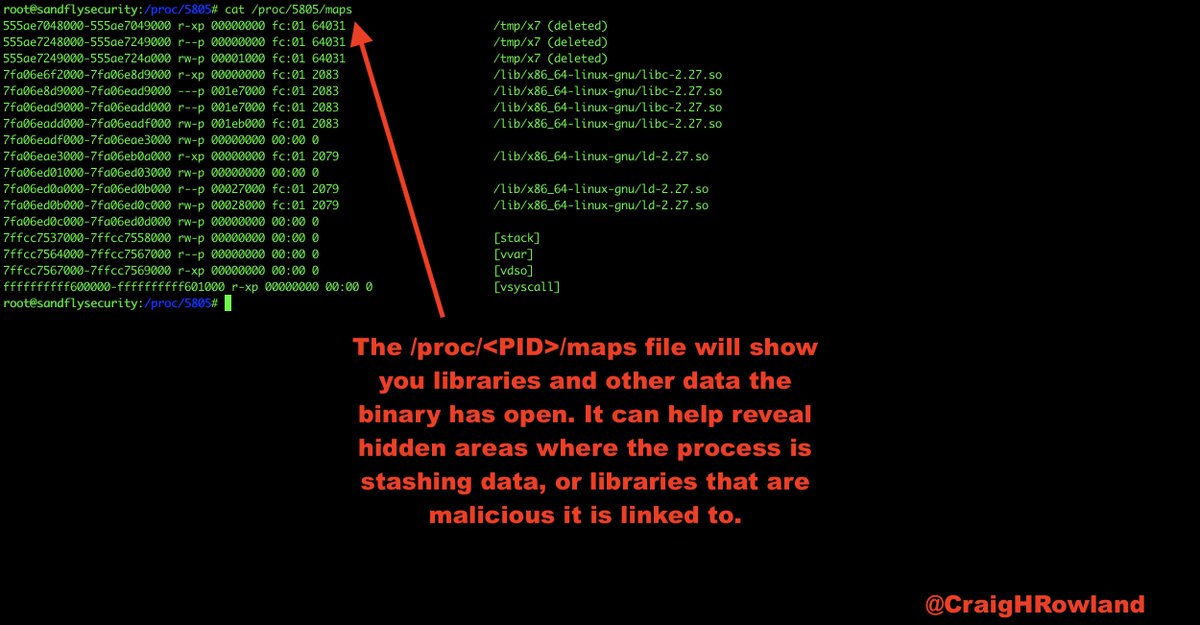
cat /proc/<PID>/maps
#DFIR #forensics
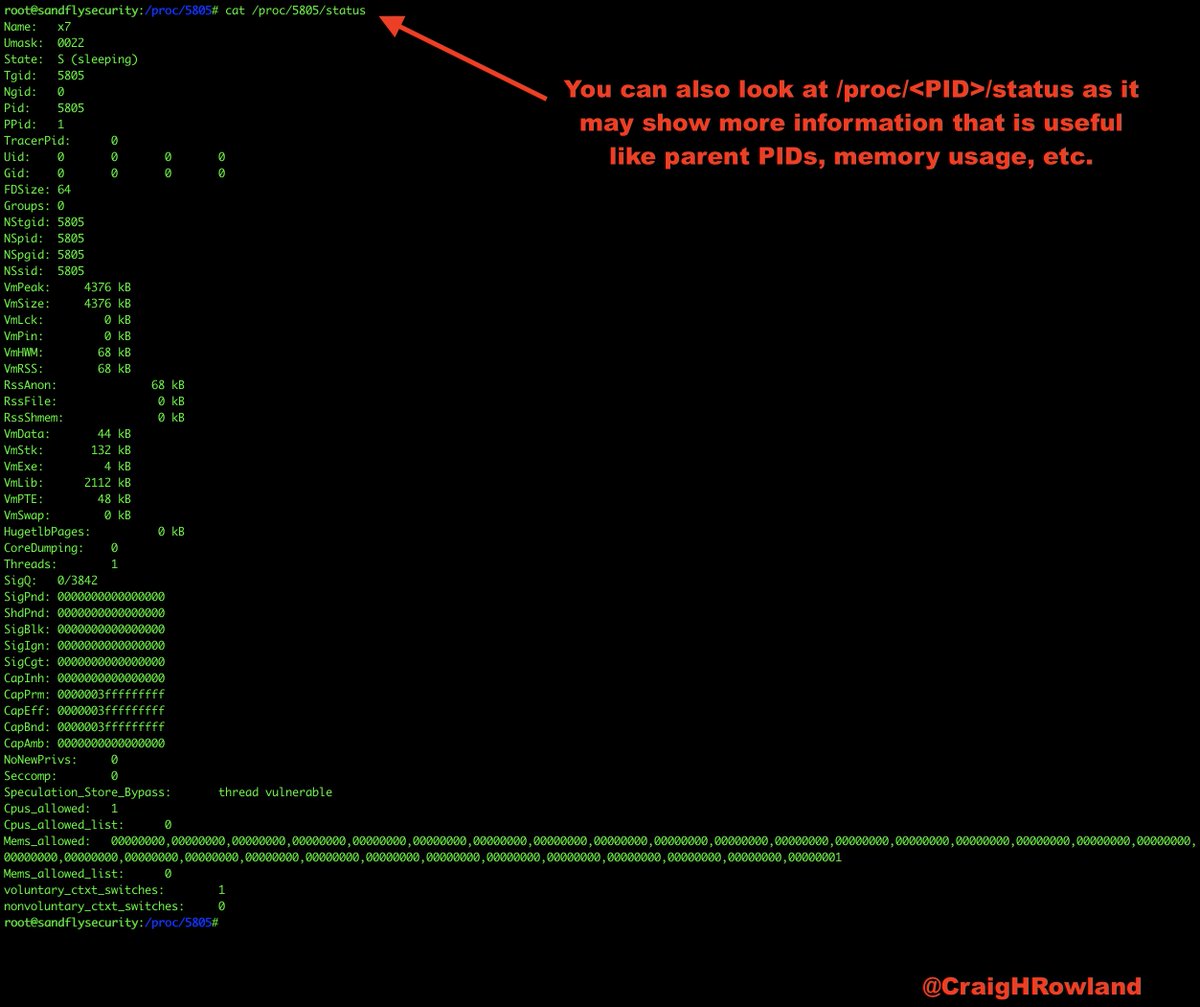
cat /proc/<PID>/status
#DFIR
sandflysecurity.com/blog/compromis…
#DFIR #threathunting #linux #malware