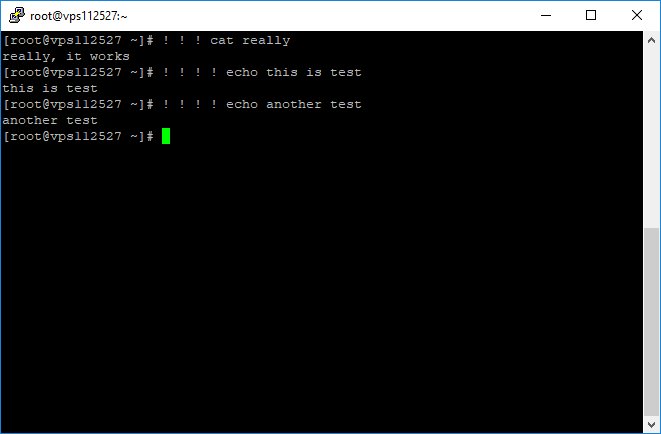
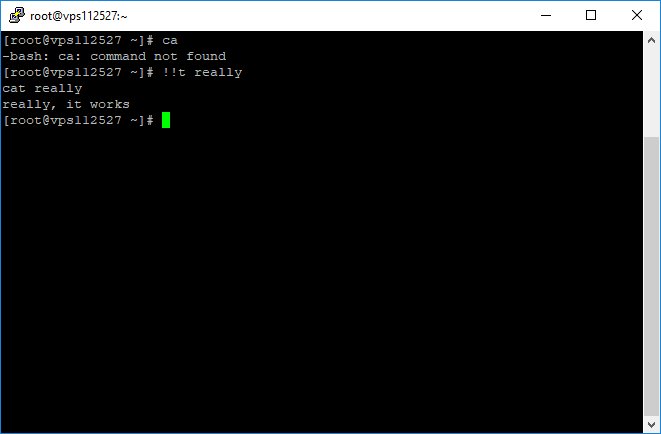
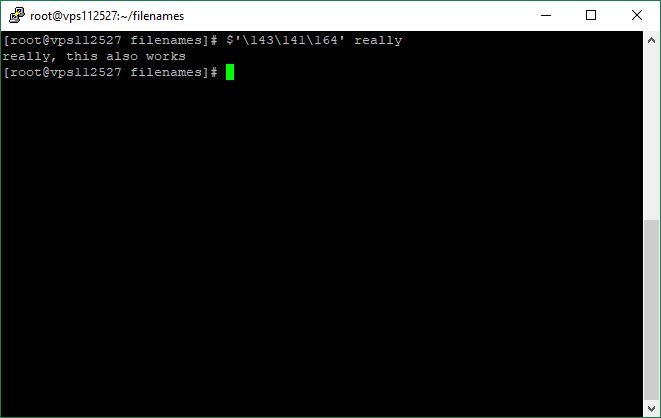
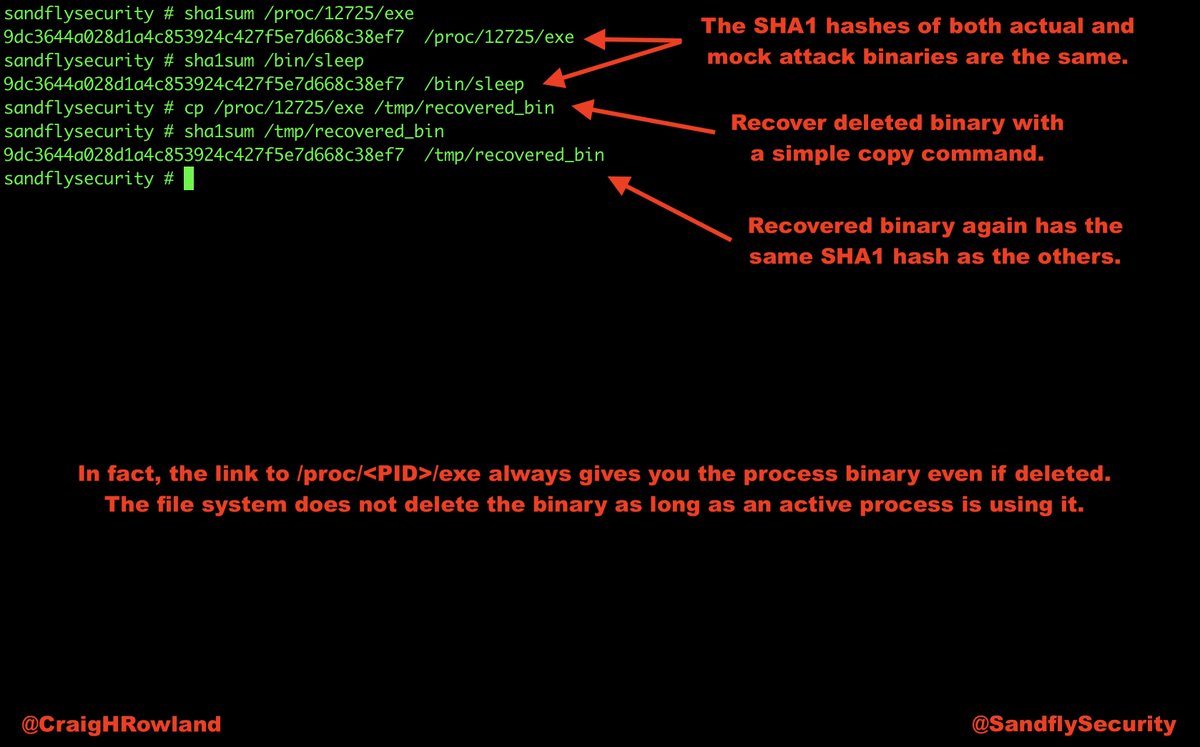
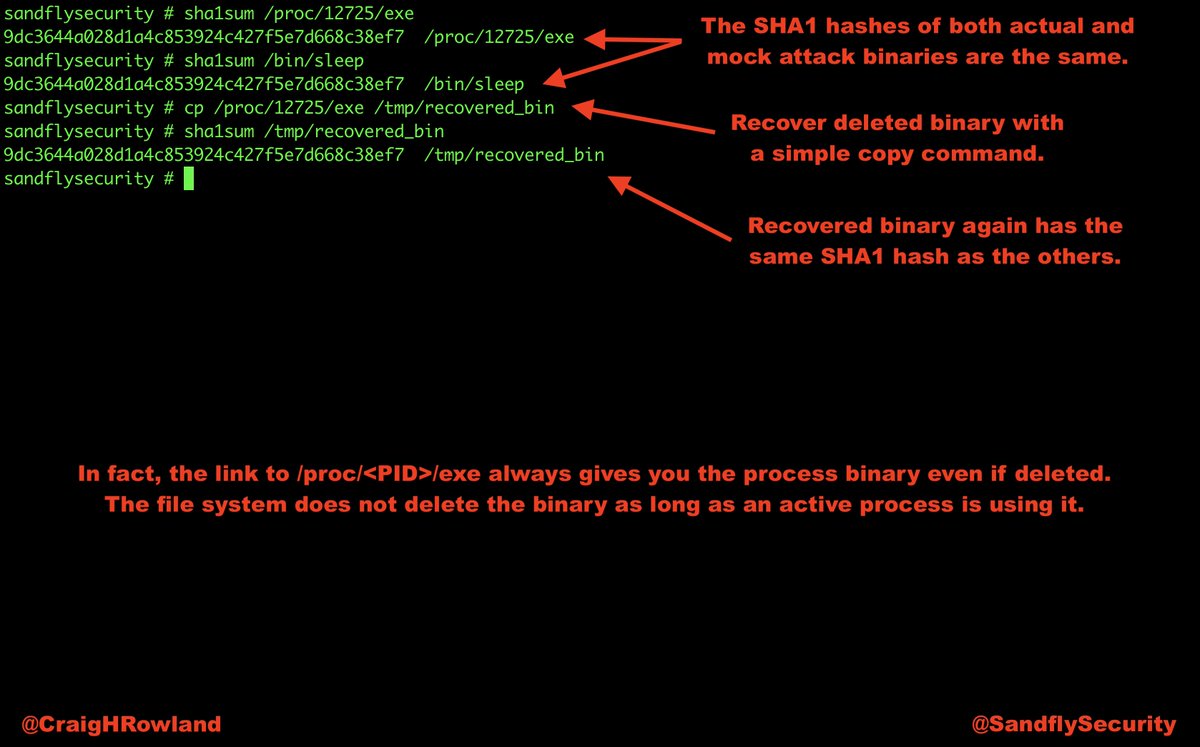
cp /proc/<PID>/exe /tmp/recovered_bin
Let's see how this works. #DFIR #threathunting #forensics

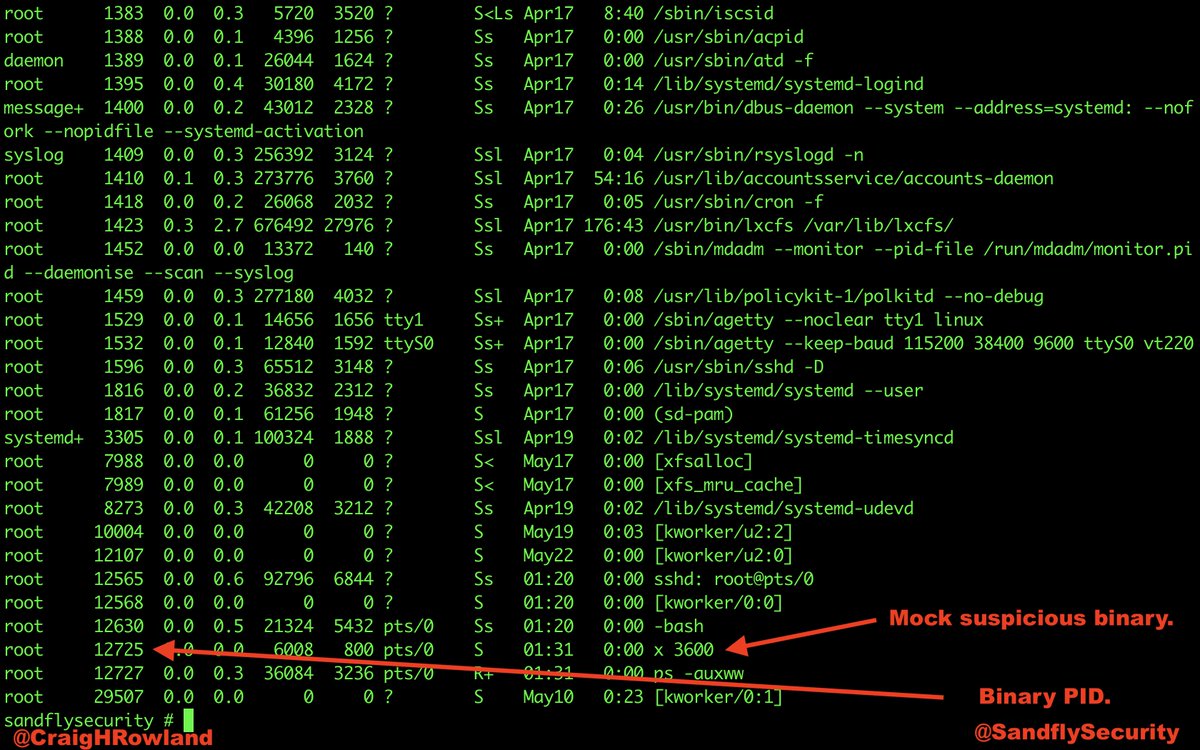
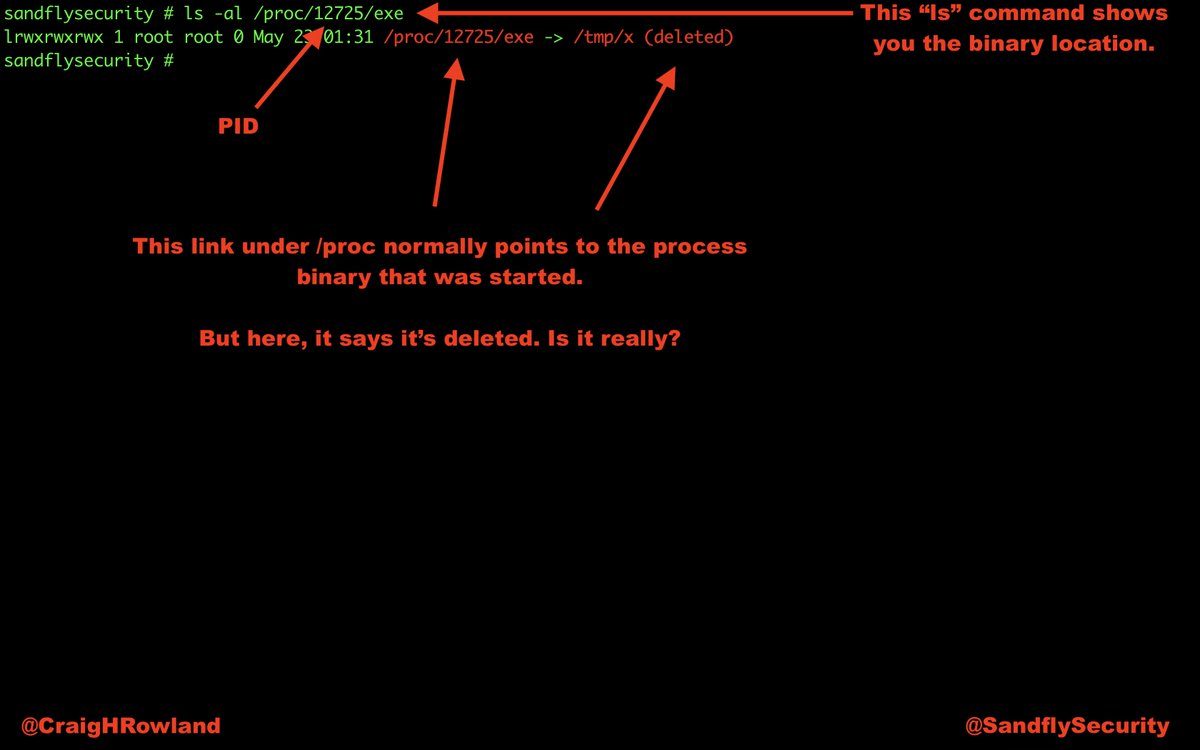
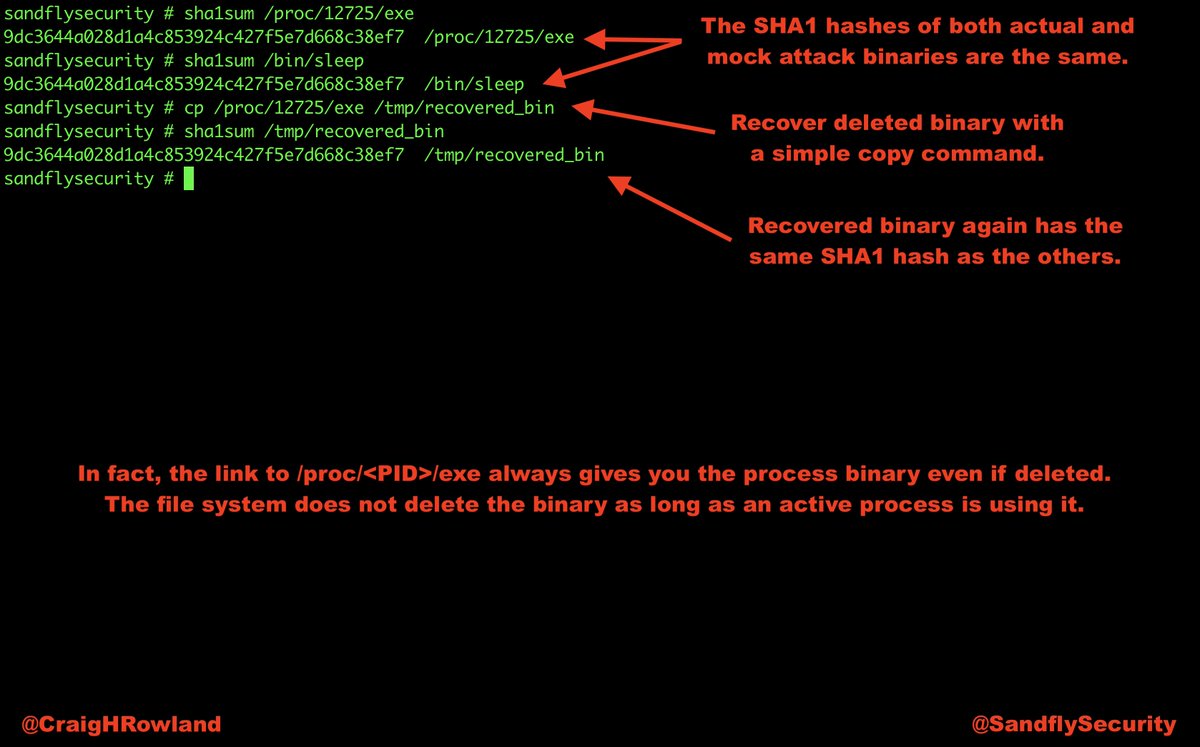
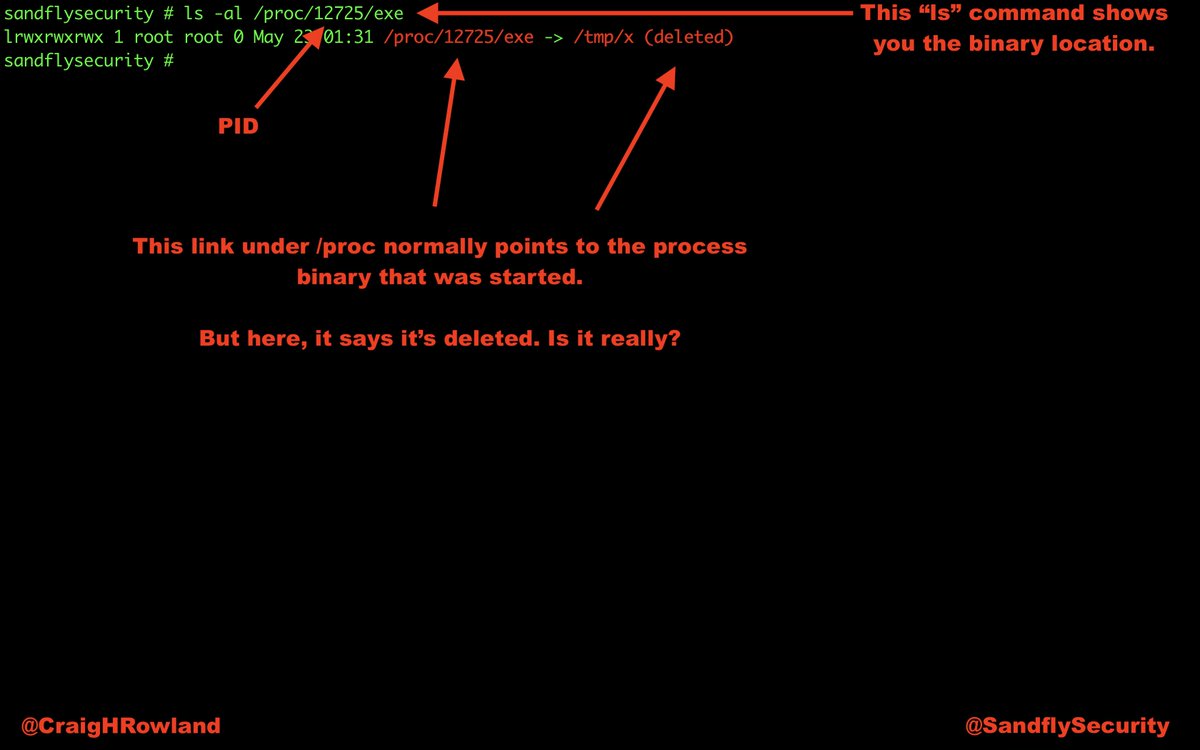
But if you remember /proc/<PID>/exe you can recover any deleted binary.
#DFIR #threathunting #forensics
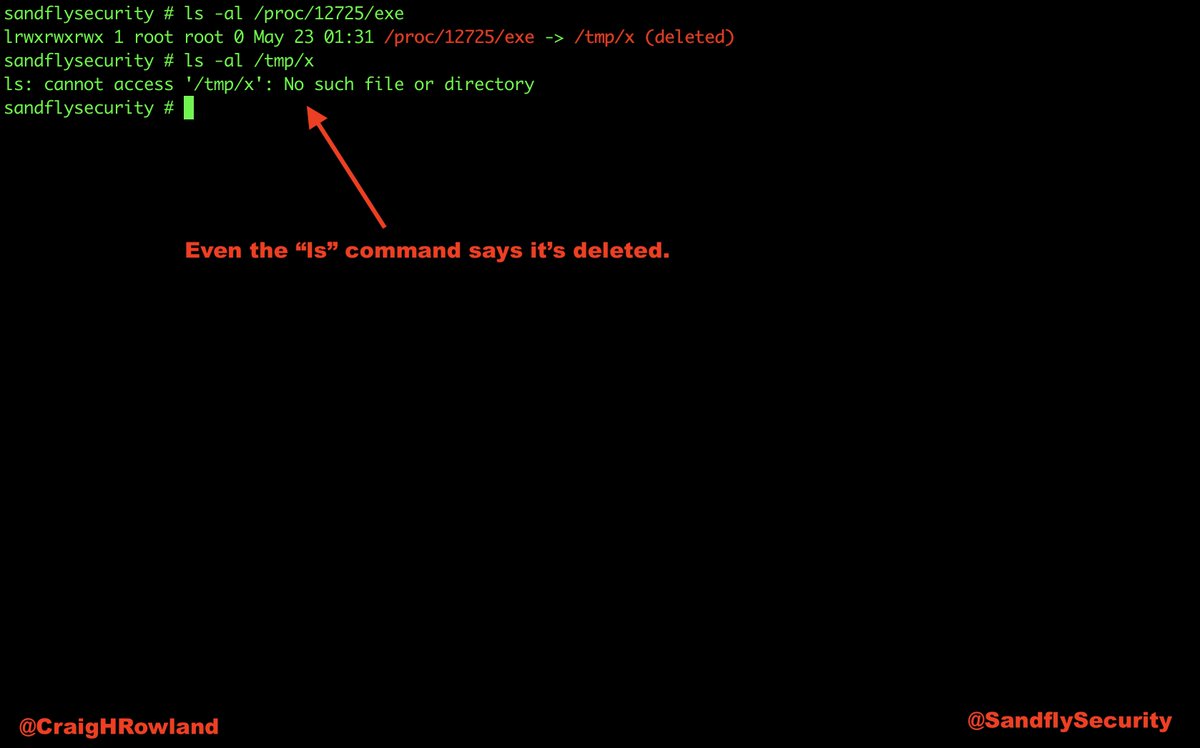
cd /tmp
cp /bin/sleep x
./x 3600 &
[1] 32031
rm x
This copies the sleep command as "x" under /tmp and runs for 3600 seconds. Then, delete "x" so the binary appears removed. Practice on it.
#DFIR #threathunting #forensics

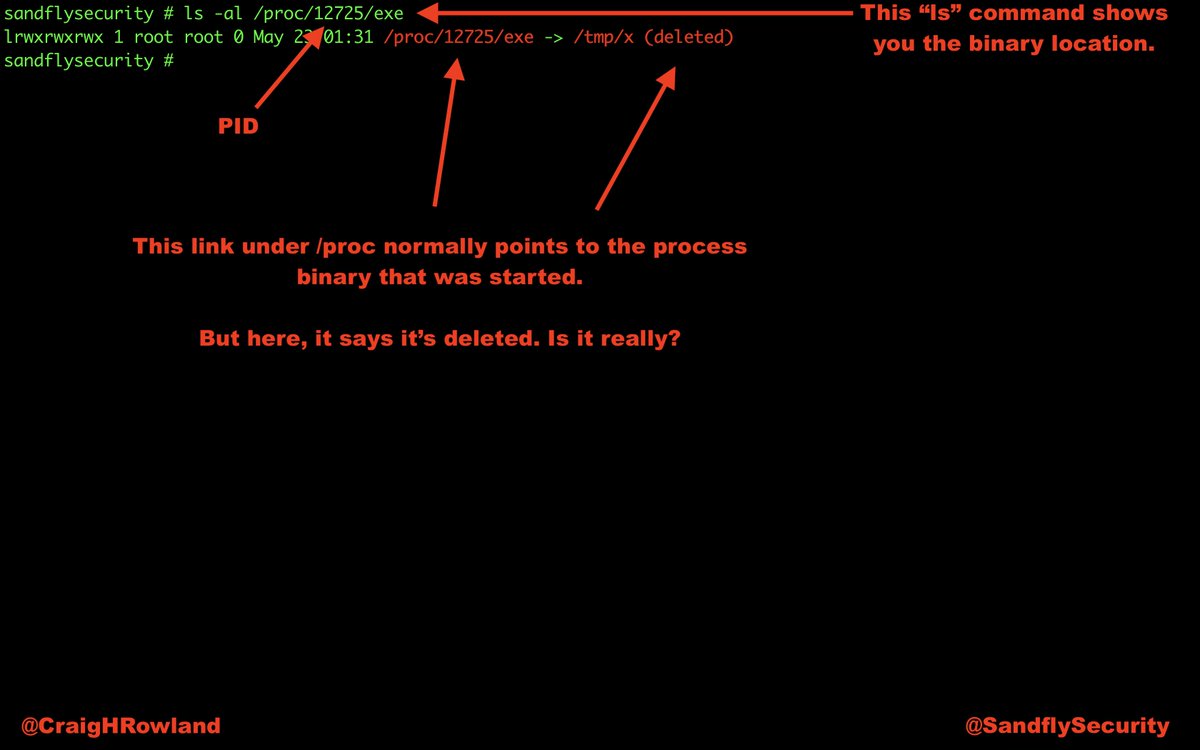
ls -al /proc/32031/exe
lrwxrwxrwx 1 root root 0 May 23 19:39 /proc/32031/exe -> /tmp/x (deleted)
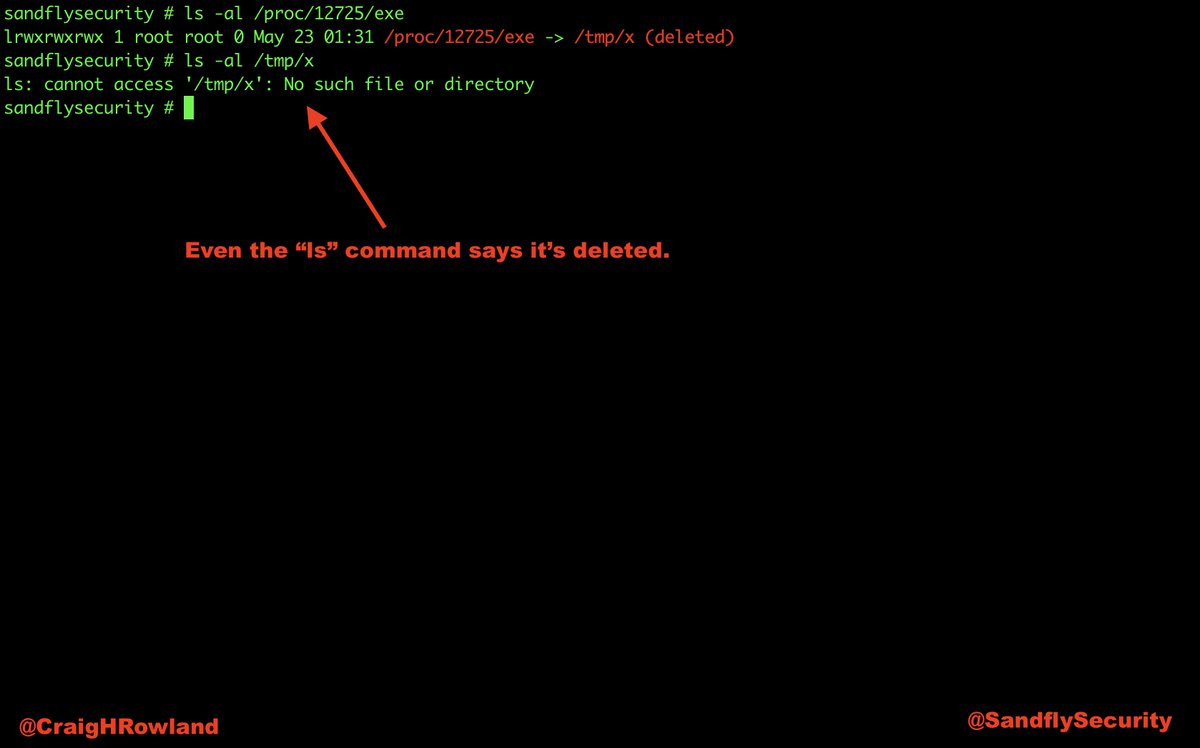
But, #Linux will not delete the file as long as a process still has it open.
#DFIR #threathunting
cp /proc/32031/exe /tmp/recovered_bin
#DFIR #threathunting #forensics #sandflysecurity
#DFIR #threathunting #forensics #sandflysecurity
#DFIR #threathunting #forensics #sandflysecurity