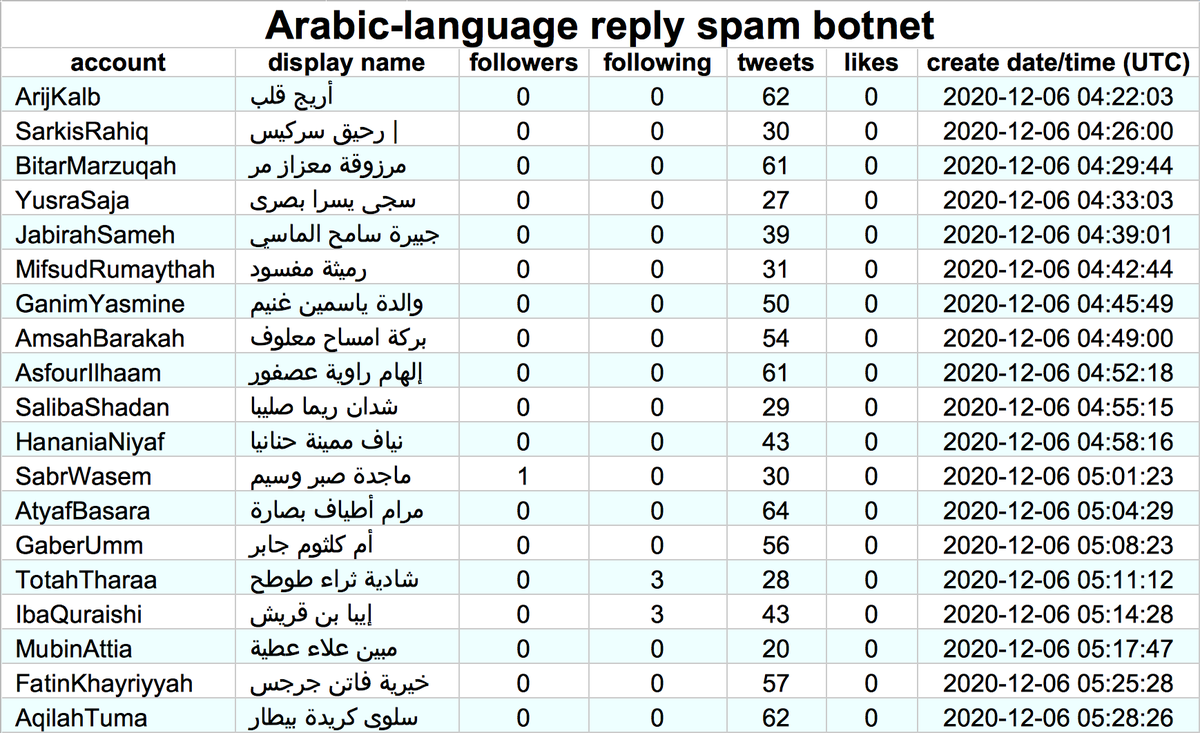
If you're looking for spammy Twitter accounts with stolen profile pics peddling #InsertCountryNameHerePhoneNumberLists and #Email #Lists, this botnet's for you.
cc: @ZellaQuixote
cc: @ZellaQuixote

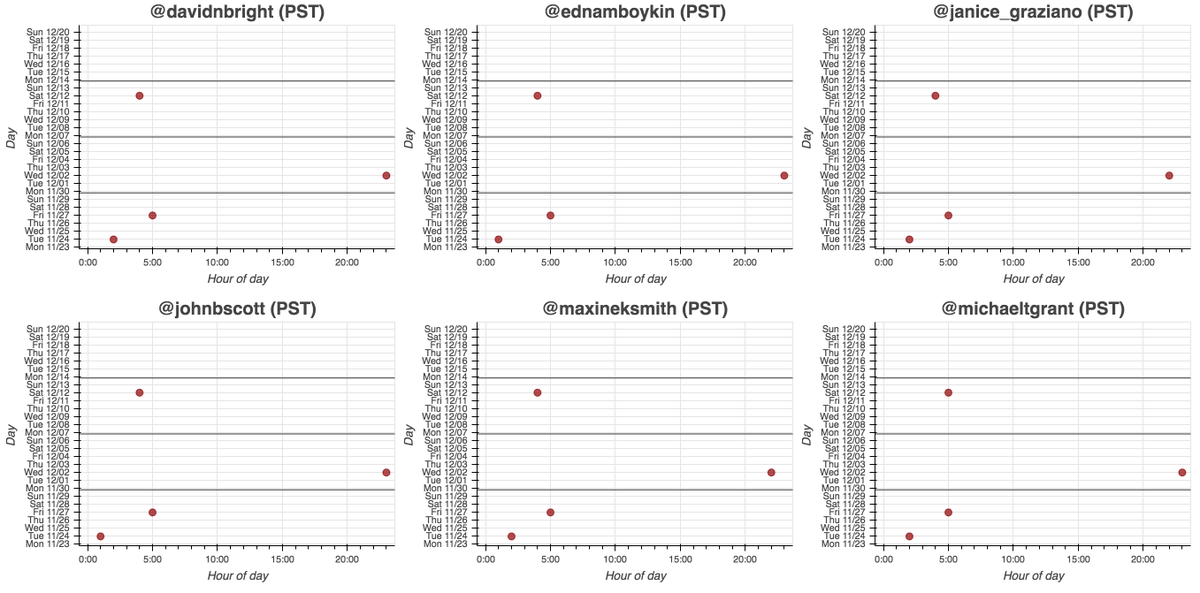
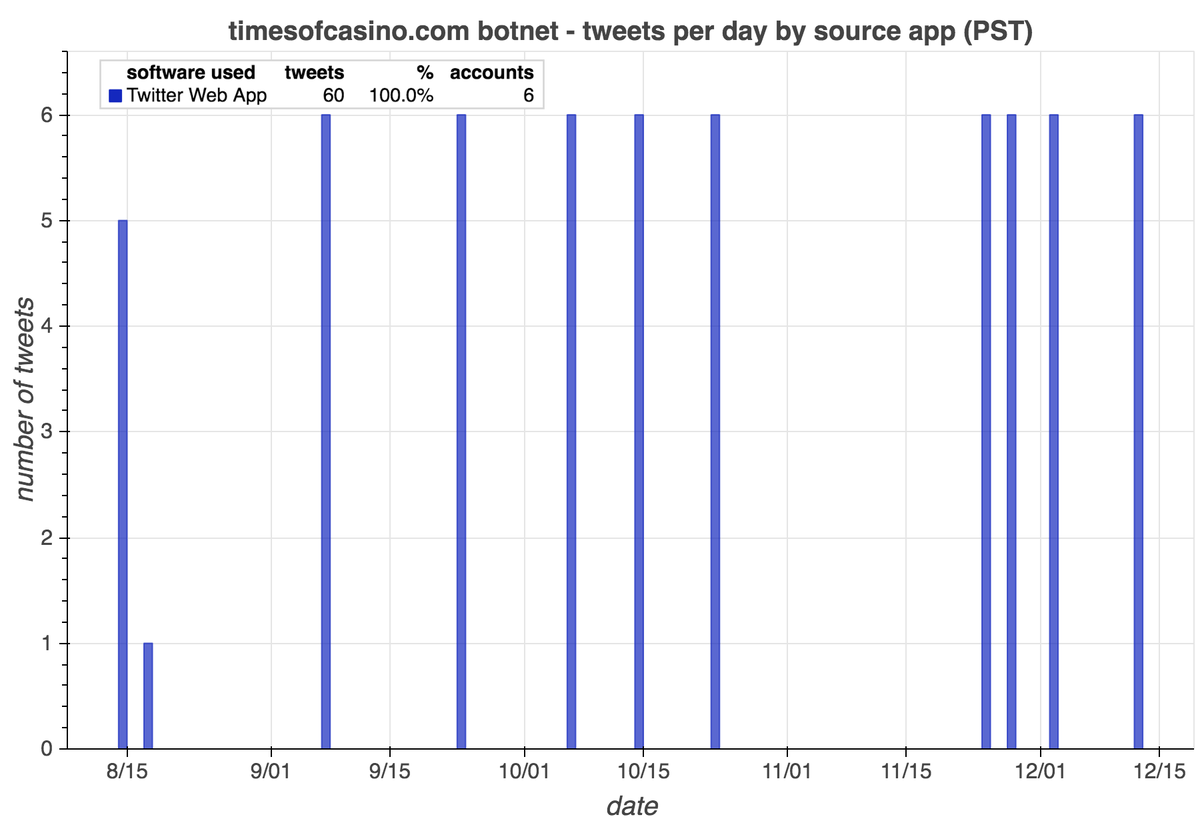
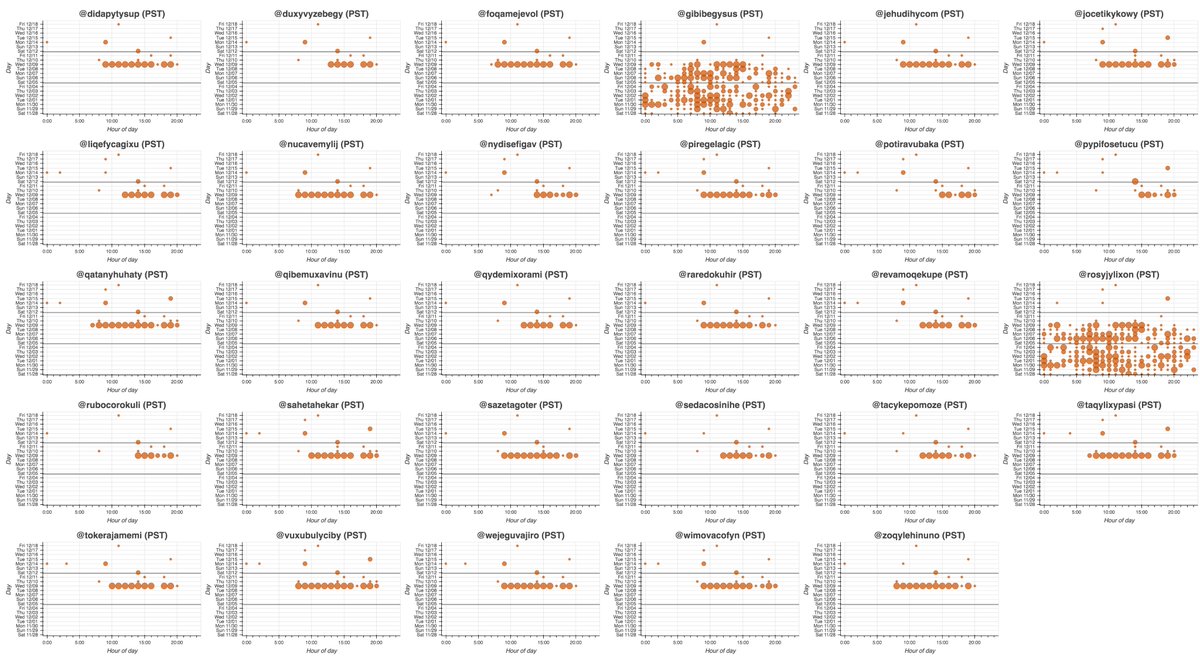
We found a network of 16 accounts tweeting links to latestdatabase(dot)com, all but two of which were created in 2020. These accounts tweet on extremely similar schedules and (allegedly) posted all of their recents tweets via the Twitter web app. 


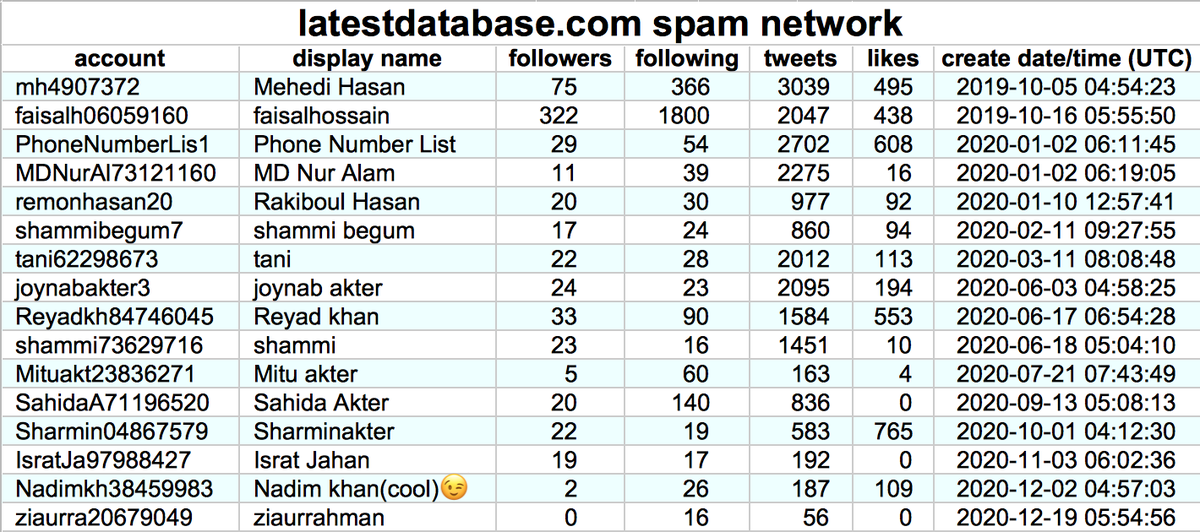
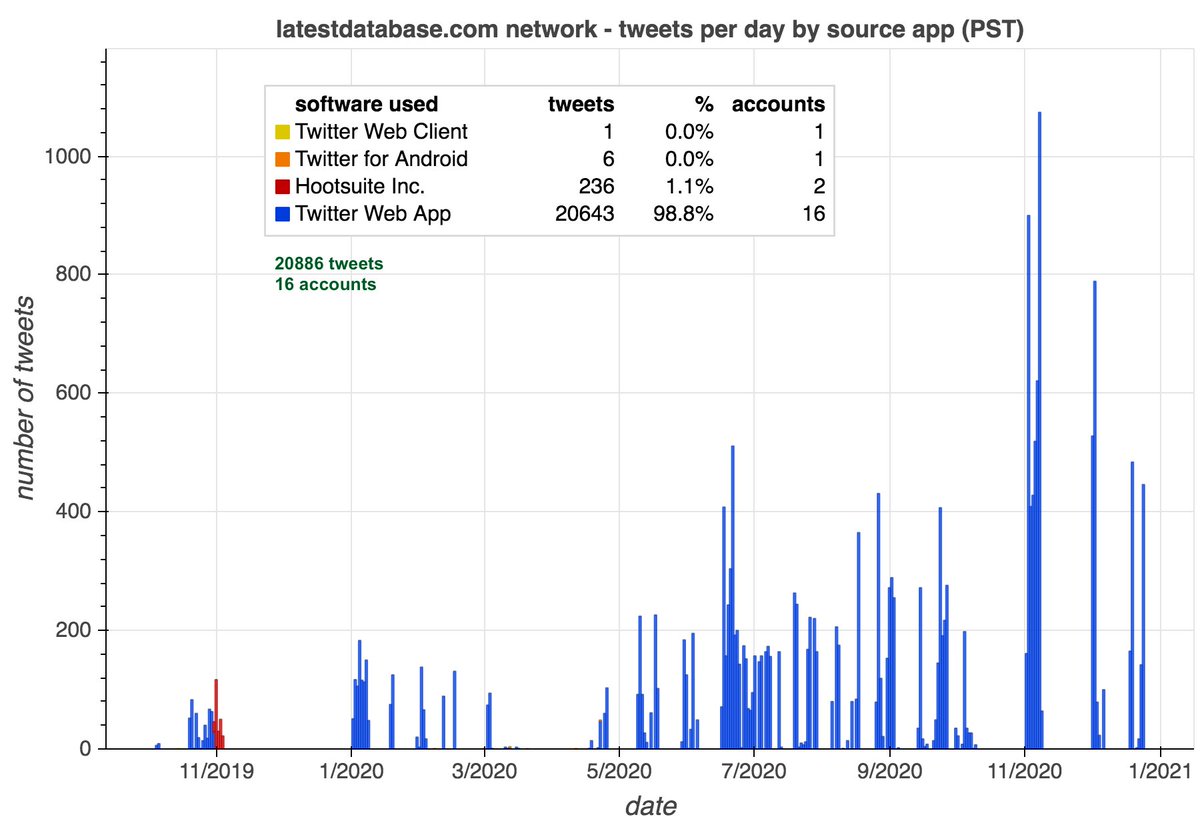

Although other sites turn up occasionally, the majority of the network's content is tweets linking latestdatabase(dot)com, a website that supposedly sells lists of people's email addresses and cell phone numbers. (As always, be wary of clicking links to unknown websites.) 







This botnet is repetitive, with many tweets duplicated verbatim on multiple accounts. Most tweets contain hashtags of the form #<country>emaillist or #<country>phonenumberlist, and variants thereof. 





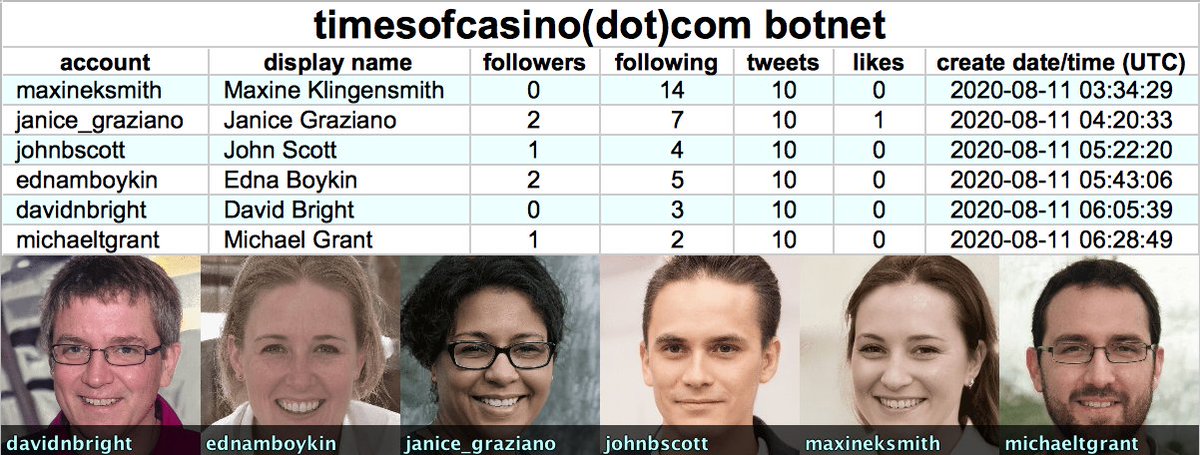
Unsurprisingly most (and possibly all) of the accounts in this network use stolen profile pics. We found Google reverse image search superior to TinEye and Yandex for tracking down this particular network's profile pics. 
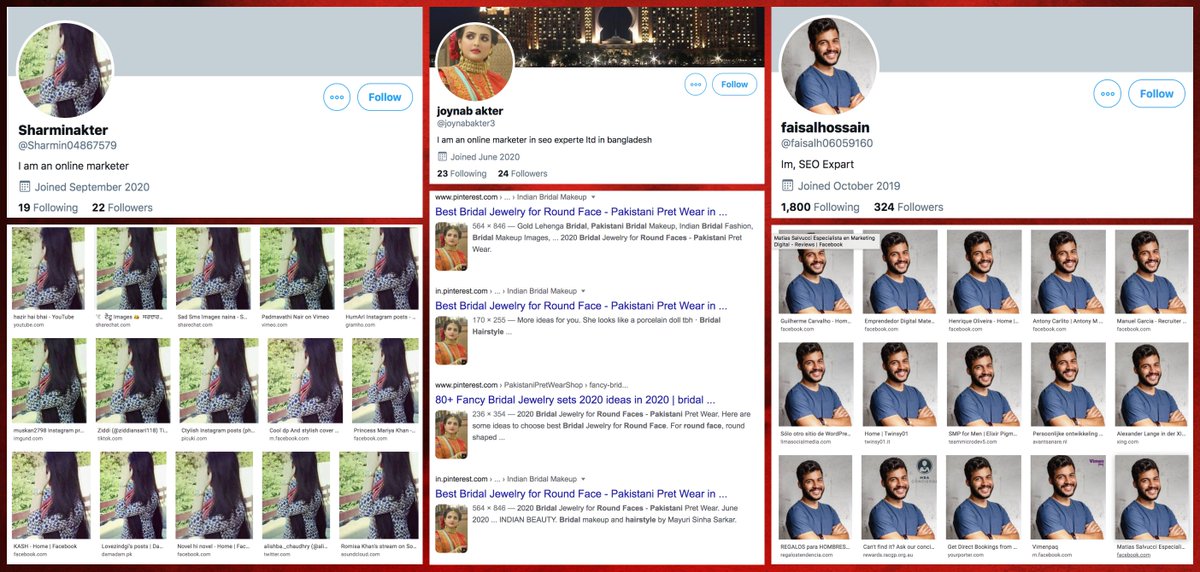
• • •
Missing some Tweet in this thread? You can try to
force a refresh