I could write a book...
You gain expertise through the process of fixing things, sometimes the things you break - don't fear mistakes.
As your expertise gets deeper, you find new exotic ways of breaking things where even Stack Overflow won't save you.
Here's a few of mine :)
You gain expertise through the process of fixing things, sometimes the things you break - don't fear mistakes.
As your expertise gets deeper, you find new exotic ways of breaking things where even Stack Overflow won't save you.
Here's a few of mine :)
https://twitter.com/NerdPyle/status/1356774736164917250
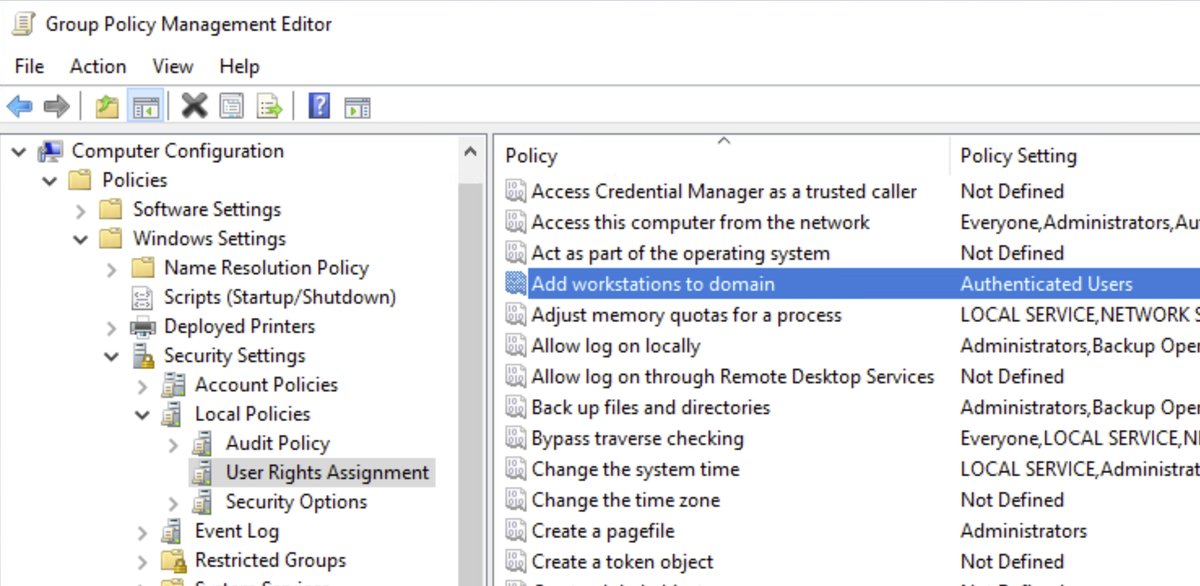
First week on a new job, ran a driver cleanup script for ConfigMgr 2007 and forgot the params - dumped the entire driver catalog
Deployed apps based on UTC instead of local time
$list | % { Restart-Computer $_ } while the server I was running it from was in the list...
Deployed apps based on UTC instead of local time
$list | % { Restart-Computer $_ } while the server I was running it from was in the list...
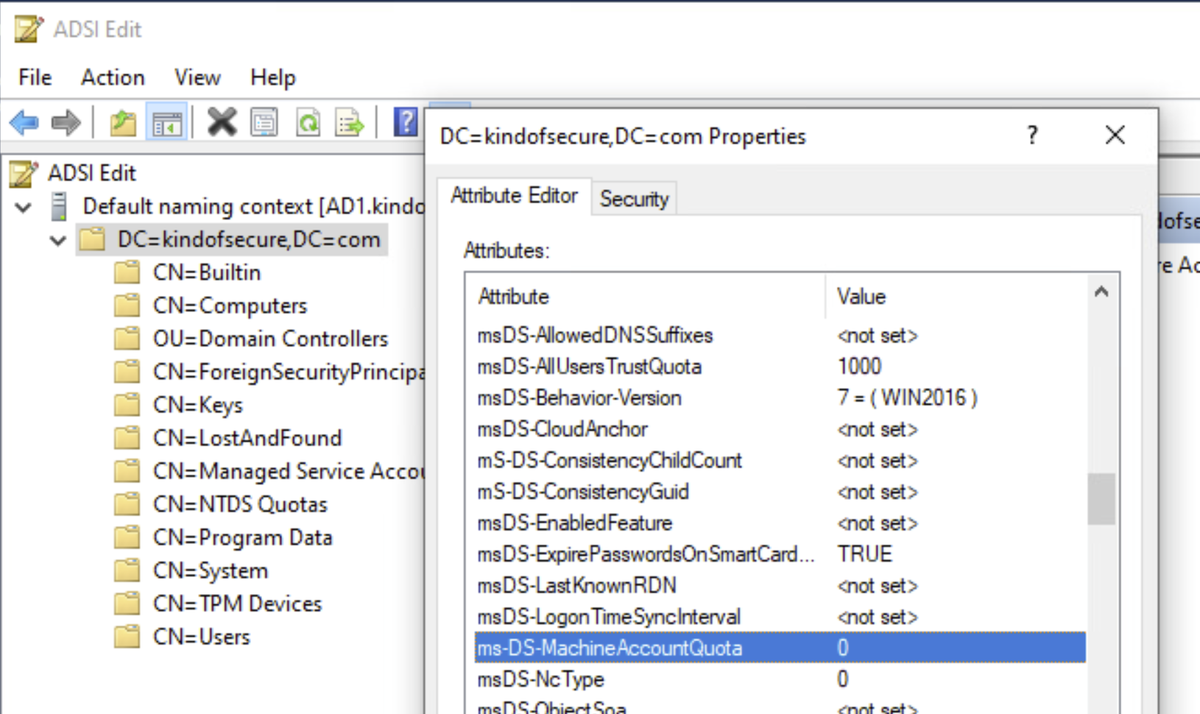
Filtered in Graylog to push a new client config without realizing it included some servers. New log sources flooded Graylog with 200GB of data.
Set up a mail flow rule to catch spoofing (from header contains domain) but forgot to specify from external... QT'd my outbound email.
Set up a mail flow rule to catch spoofing (from header contains domain) but forgot to specify from external... QT'd my outbound email.
Don't fear mistakes, fear not having the practice and experience of fixing them.
As you move up, the impact of systems breaking gets exponentially worse, and those experiences will help you recover more quickly.
Failing is part of the journey, and owning it is good for us :)
As you move up, the impact of systems breaking gets exponentially worse, and those experiences will help you recover more quickly.
Failing is part of the journey, and owning it is good for us :)
• • •
Missing some Tweet in this thread? You can try to
force a refresh