I'm seeing another big push by vendors that their solution will fix education's ransomware woes
You can't make up for poor operational management by buying products
Do these free things first, then consider purchases that scale your staff
Note: #6 is for non-AD bound devices
You can't make up for poor operational management by buying products
Do these free things first, then consider purchases that scale your staff
Note: #6 is for non-AD bound devices
https://twitter.com/NathanMcNulty/status/1343985031916621829
1. For email filtering, I have a nice series here you can borrow ideas from:
blog.opsecedu.com/using-transpor…
For Office macros, it's how something like 90% of ransomware starts (rest is unpatched remote access).
At least block macros from the Internet:
microsoft.com/security/blog/…
blog.opsecedu.com/using-transpor…
For Office macros, it's how something like 90% of ransomware starts (rest is unpatched remote access).
At least block macros from the Internet:
microsoft.com/security/blog/…
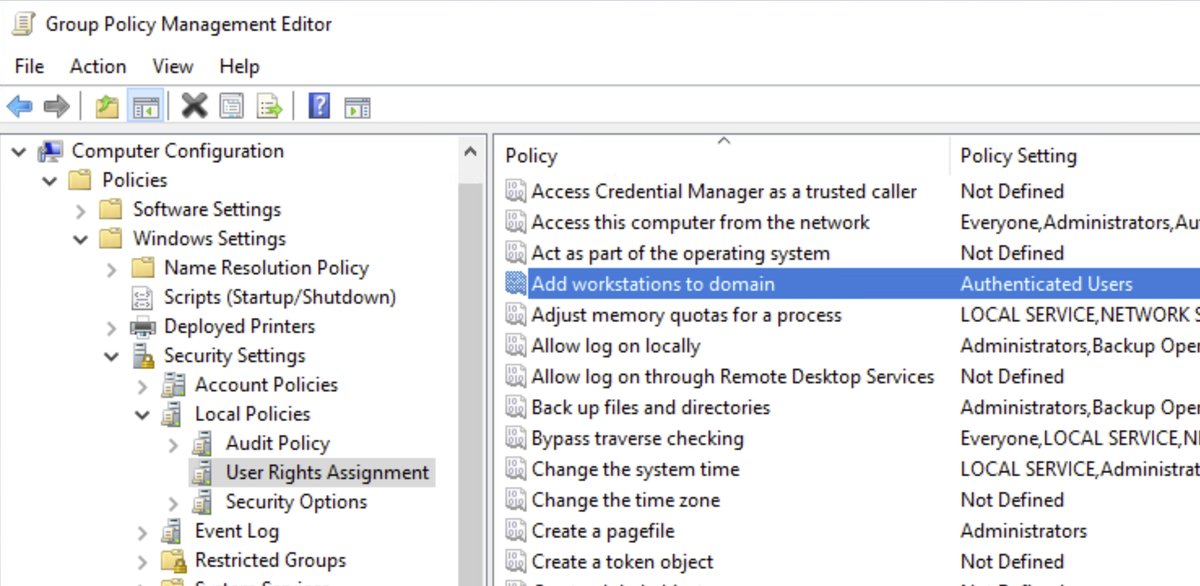
3. Attackers move around your network easily when you have the same admin accounts on many machines. Make them all unique and make them work for it.
LAPS is a simple, effective way to do this.
blog.nowmicro.com/2018/02/28/con…
See @RyanLNewington's free LAPS Web:
github.com/lithnet/laps-w…
LAPS is a simple, effective way to do this.
blog.nowmicro.com/2018/02/28/con…
See @RyanLNewington's free LAPS Web:
github.com/lithnet/laps-w…
4. Defender's ASR rules are awesome (but Defender can't be in passive mode)
Enable ASR in audit mode, monitor the logs, and enable one at a time as you identify what is safe.
There's even a Warn mode now, so you can go audit - warn - block.
E5=EZ mode:
Enable ASR in audit mode, monitor the logs, and enable one at a time as you identify what is safe.
There's even a Warn mode now, so you can go audit - warn - block.
E5=EZ mode:
https://twitter.com/NathanMcNulty/status/1348735225409335296
5. How often do you really Remote Desktop between workstations?
Let's not make edge cases the default - disable everywhere, then open it for specific use cases.
Make sure NLA is enabled, don't expose RDP to the Internet, and use Remote Credential Guard:
Let's not make edge cases the default - disable everywhere, then open it for specific use cases.
Make sure NLA is enabled, don't expose RDP to the Internet, and use Remote Credential Guard:
https://twitter.com/SteveSyfuhs/status/1303405857770631168
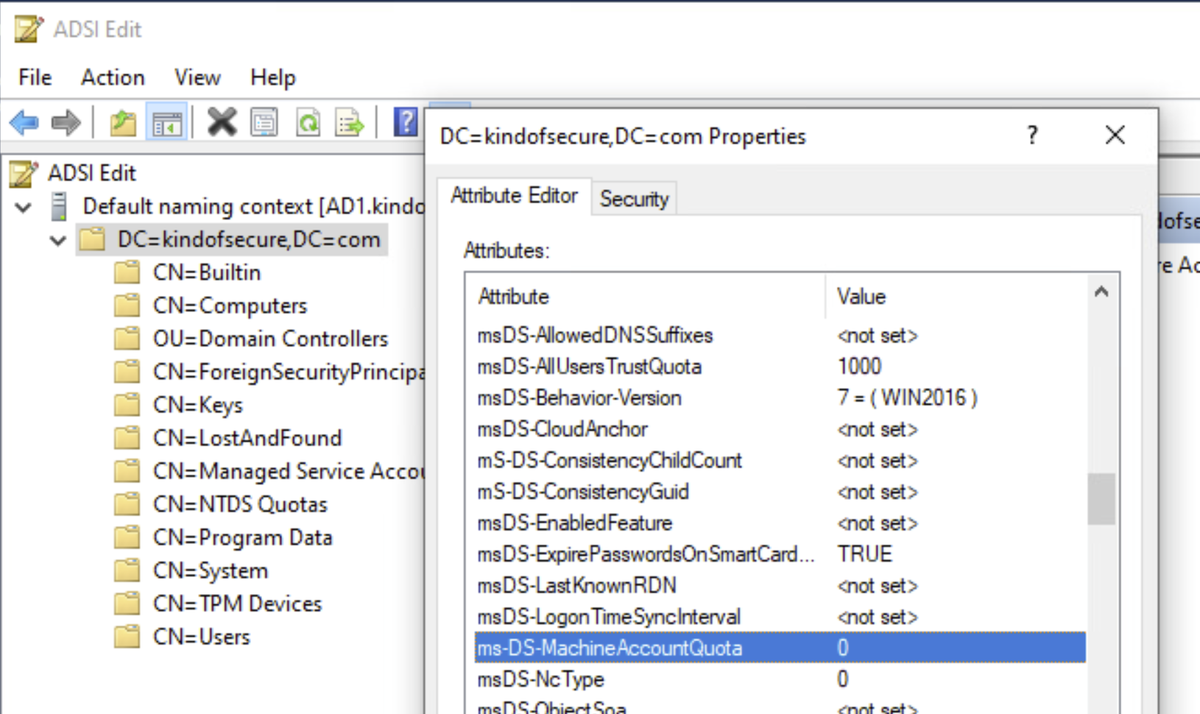
6. This is geared toward those non-AD bound systems - backup, VOIP, etc.
TrustedHosts is used for WinRM/Powershell remoting when you don't have HTTPS or Kerberos available.
Many articles just tell you to use *. Instead, limit the list to known systems:
windows-security.org/e20c9386972c5d…
TrustedHosts is used for WinRM/Powershell remoting when you don't have HTTPS or Kerberos available.
Many articles just tell you to use *. Instead, limit the list to known systems:
windows-security.org/e20c9386972c5d…
7. Patch management is damn hard
Prioritize by impact - remote access, such as VPN, needs immediate consideration. Keep an eye on Patch Tuesday notes or similar for your OS's, evaluate and rush the critical ones.
Get to automating OS patches, even if it's just test/dev first.
Prioritize by impact - remote access, such as VPN, needs immediate consideration. Keep an eye on Patch Tuesday notes or similar for your OS's, evaluate and rush the critical ones.
Get to automating OS patches, even if it's just test/dev first.
Applications are a whole different struggle. I watch our TVM in Defender for Endpoint and cry...
PDQ, PatchMyPC, and others are out there at a cost I don't think you could actually save money by doing in house. Some tools are worth paying for to scale your staff.
PDQ, PatchMyPC, and others are out there at a cost I don't think you could actually save money by doing in house. Some tools are worth paying for to scale your staff.
8. I can't stop singing praises for @mysmartlogon's PingCastle
It's so simple, hundreds of K12 sysadmins have been using it to make very meaningful improvements.
Most of the issues covered in this thread are things his singular tool identifies for you:
It's so simple, hundreds of K12 sysadmins have been using it to make very meaningful improvements.
Most of the issues covered in this thread are things his singular tool identifies for you:
https://twitter.com/NathanMcNulty/status/1282369991308763136?s=20
And honorable mention to AppLocker because I do think that is achievable for everyone. It is very flexible application allow listing.
It also works on Pro SKU's which many may not be aware of:
msendpointmgr.com/2020/09/20/doe…
Thanks to Seth for bringing it up!
It also works on Pro SKU's which many may not be aware of:
msendpointmgr.com/2020/09/20/doe…
Thanks to Seth for bringing it up!
https://twitter.com/Collab_Seth/status/1357848025767510016
• • •
Missing some Tweet in this thread? You can try to
force a refresh