First, what makes it unique?
1/17
- Exfil over websockets
- A rather clever skimmer loader that I think may fool a lot of people
- CSS classes(!) being used to construct the URL
Intrigued? Great. Let's go
2/x
<span class="gray-hint bul-k-sup-pchat_c-om modernize css " style="display:none"></span>
Compare that to the code above and you can see how it was used to build the endpoint. Clever, no?
Here's both versions of the code and the span: gist.github.com/krautface/6f62…
7/x
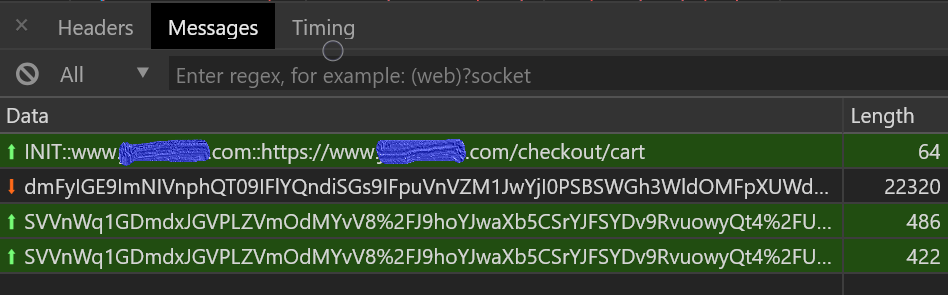
8/x
gist.github.com/krautface/2c59…
9/x
gist.github.com/krautface/1bd0…
As mentioned above, the infrastructure involved is just the one domain so far: bulksuppchat[.]com
14/x
15/x
The method to stop this attack: CSP. The connect-src setting in CSPs governs what websockets can connect to. So review your CSPs!
16/x
17/17





















