NEW RESEARCH: Black Kingdom ransomware begins appearing on Exchange servers
***
A novel, if not particularly well made, ransomware is spreading to Exchange servers that haven't been patched against the ProxyLogon exploit.
(a thread)
1/15
***
A novel, if not particularly well made, ransomware is spreading to Exchange servers that haven't been patched against the ProxyLogon exploit.
(a thread)
1/15
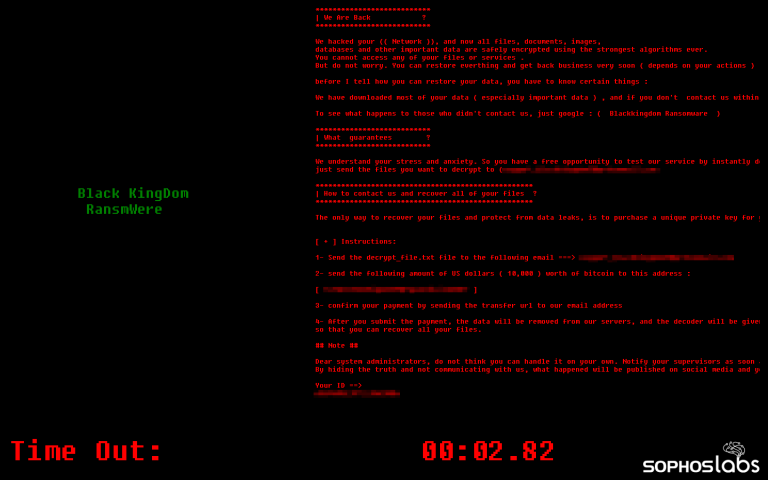
Following the #DearCry ransomware attacks reported on last week, another ransomware gang has also started to target vulnerable Exchange servers with another ransomware, called #BlackKingDom.
2/15
2/15
Sophos telemetry began detecting the ransomware on Thursday March 18 as it targeted Exchange servers that remain unpatched against the ProxyLogon vulnerabilities disclosed by Microsoft earlier this month.
3/15
3/15
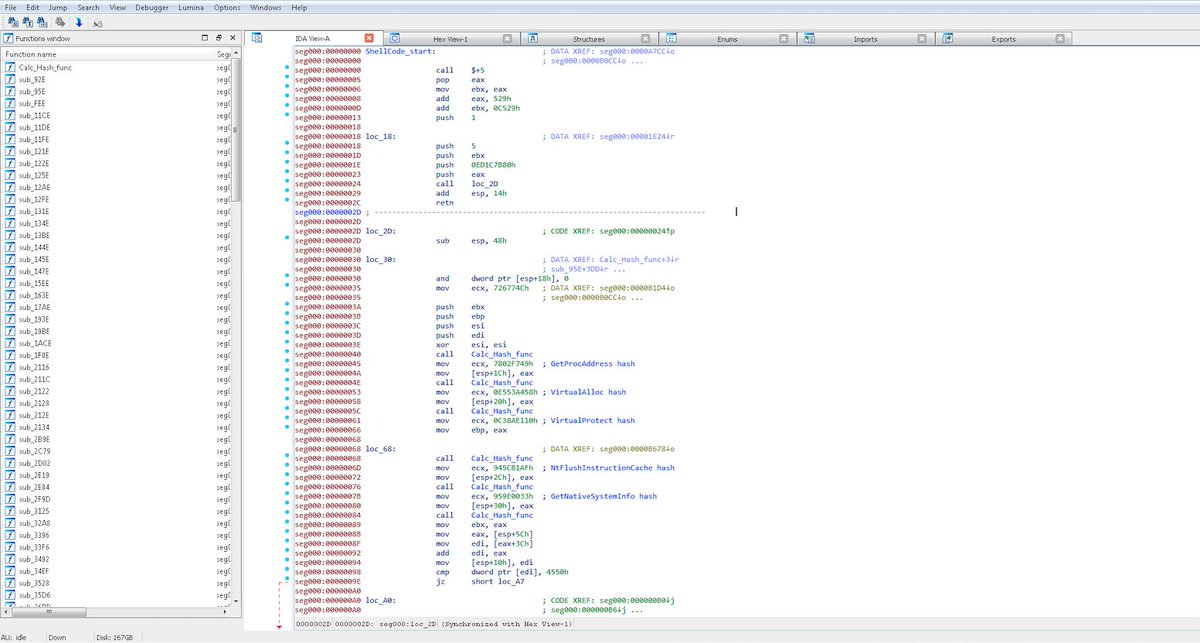
The Black KingDom ransomware is far from the most sophisticated payload we’ve seen. In fact, our early analysis reveals that it is somewhat rudimentary and amateurish in its composition, but it can still cause a great deal of damage.
4/15
4/15
It may be related to a ransomware of the same name that appeared last year on machines that, at the time, were running a vulnerable version of the Pulse Secure VPN concentrator software.
5/15
5/15
*Delivered through a webshell that was sent over Tor*
The delivery of Black KingDom was orchestrated from a remote server with an IP address that geolocates to Germany, 185.220.101.204, while the attacker operated from 185.220.101.216.
6/15
The delivery of Black KingDom was orchestrated from a remote server with an IP address that geolocates to Germany, 185.220.101.204, while the attacker operated from 185.220.101.216.
6/15
Unfortunately, because both IP addresses belong to a Tor exit node, it’s impossible to know where the attackers are physically located.
7/15
7/15
The threat actor exploited the on-premises versions of Microsoft Exchange Server, abusing the remote code execution (RCE) vulnerability also known as ProxyLogon (CVE-2021-27065).
8/15
8/15
After successfully breaching the Exchange server, the adversary delivered a webshell. This webshell offers remote access to the server and allows the execution of arbitrary commands.
The webshell ChackLogsPL.aspx was dropped here:
9/15
The webshell ChackLogsPL.aspx was dropped here:
9/15

Other filenames of webshells we have observed being used by this adversary are ckPassPL.aspx and hackIdIO.aspx.
10/15
10/15
The webshell was written to disk by w3wp.exe, an Internet Information Server (IIS) Worker Process that hosts the Exchange admin center (EAC), which Microsoft has given the internal name ECP (Exchange Control Panel):
11/15
11/15

Users of Sophos endpoint products may see the webshells detected as any of the long list of detections in this post, and the ransomware payload may be detected as Troj/Ransom-GFU, Troj/Ransom-GFV or Troj/Ransom-GFP or by the CryptoGuard feature within Intercept X.
13/15
13/15
SophosLabs has published indicators of compromise to the SophosLabs Github: github.com/sophoslabs/IoC…
Threat hunters using Sophos EDR may also use the queries posted in this article to find additional indicators of compromise on their networks.
14/15
Threat hunters using Sophos EDR may also use the queries posted in this article to find additional indicators of compromise on their networks.
14/15
Author: Mark Loman (@markloman)
We would like to acknowledge the contributions of Vikas Singh (@vikas891), Alex Vermaning (@Lexy72) and Gabor Szappanos (@GaborSzappanos) to this report.
15/15
We would like to acknowledge the contributions of Vikas Singh (@vikas891), Alex Vermaning (@Lexy72) and Gabor Szappanos (@GaborSzappanos) to this report.
15/15

• • •
Missing some Tweet in this thread? You can try to
force a refresh