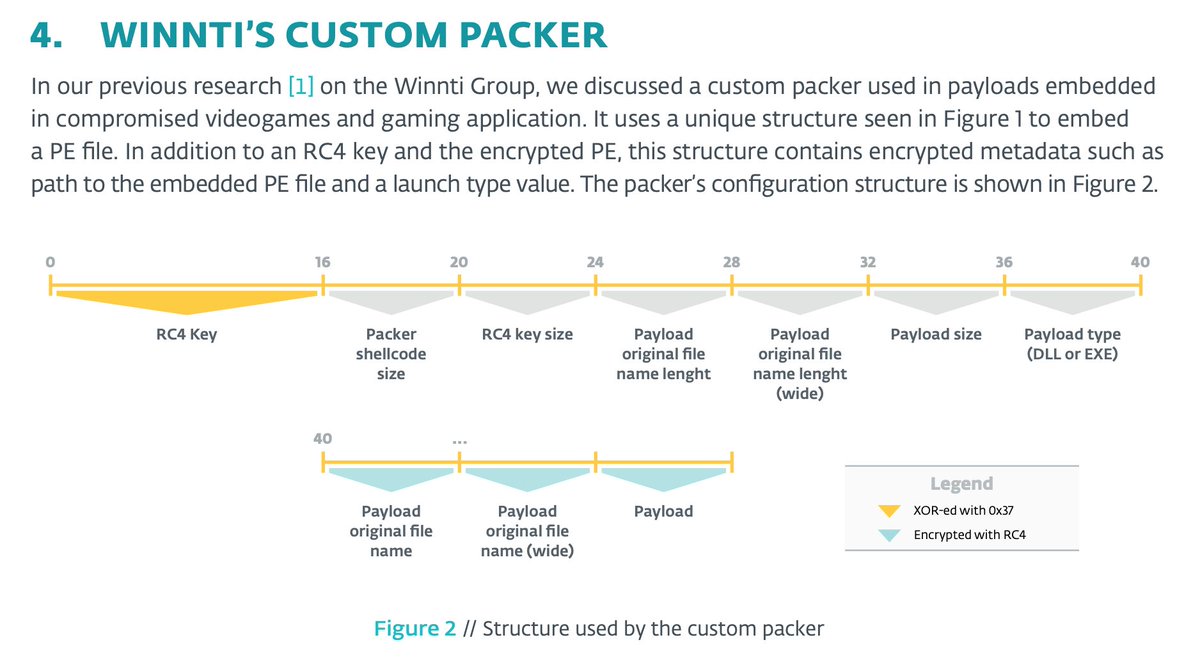
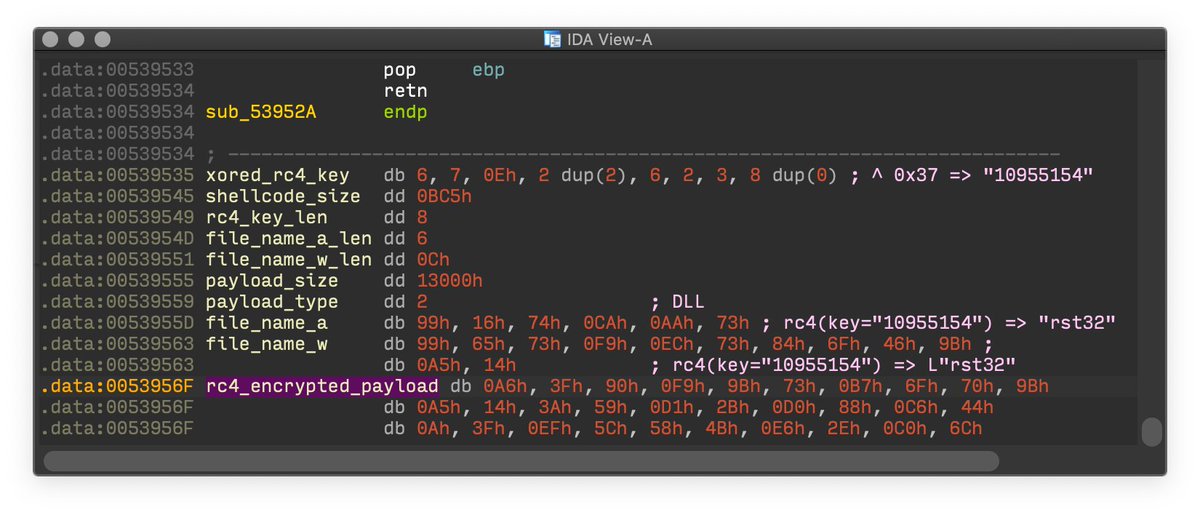
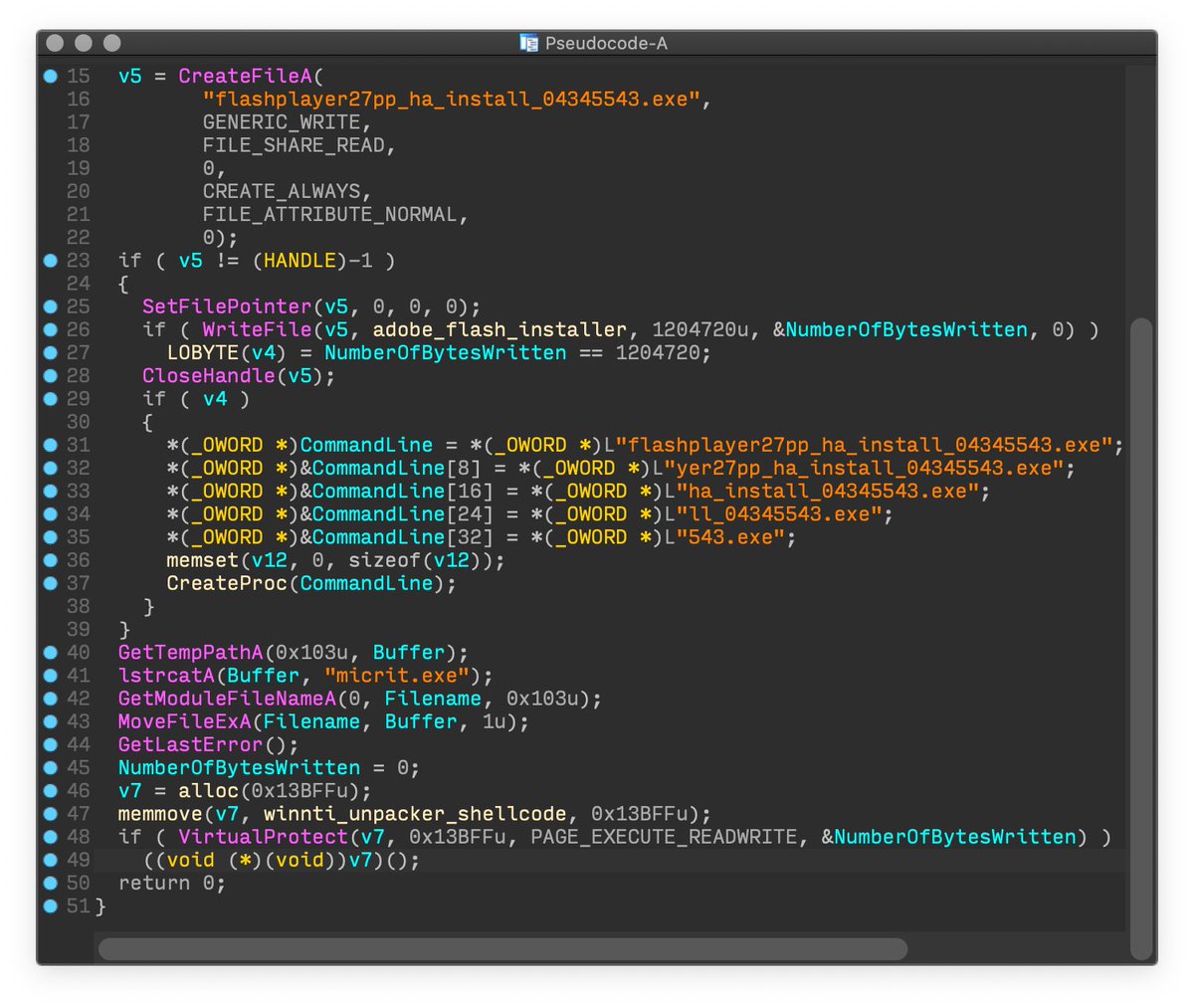
#ESETresearch confirms that malicious digitally signed AnyDesk installers are distributed from anydesk.s3-us-west-1.amazonaws[.]com. Our telemetry shows that victims are redirected there from three attacker-controlled domains: zgnuo[.]com, clamspit[.]com and domohop[.]com. 1/4 
https://twitter.com/jfslowik/status/1387535189165838336

The three domains resolve to 176.111.174[.]127, 176.111.174[.]129 and 176.111.174[.]130, in the same IP range as the C&C server, 176.111.174[.]125. It seems victims, mainly located in North America, are redirected through malicious ads from different legitimate websites. 2/4
The fake installers are malicious downloaders that download a PowerShell script b.ps1 leading, in a few cases, to Cobalt Strike, as mentioned in the analysis of a past campaign: inde.nz/blog/different…. We also observed further recon activity using BloodHound and AdFind. 3/4
We identified part of the Cobalt Strike network infrastructure but at this point we were unable to link them to a known cybercriminal campaign:
195.149.87[.]136
108.177.235[.]180 4/4
195.149.87[.]136
108.177.235[.]180 4/4
https://waystamp[.]com/static-directory/lu.gif
http://onlineceoshelp[.]com:8080/jquery-3.2.2.min.js
https://graveftp[.]com/wp-includes/adminhtml.ico
https://testsubnet[.]com/static-directory/fr.jpg 5/4
http://onlineceoshelp[.]com:8080/jquery-3.2.2.min.js
https://graveftp[.]com/wp-includes/adminhtml.ico
https://testsubnet[.]com/static-directory/fr.jpg 5/4
• • •
Missing some Tweet in this thread? You can try to
force a refresh