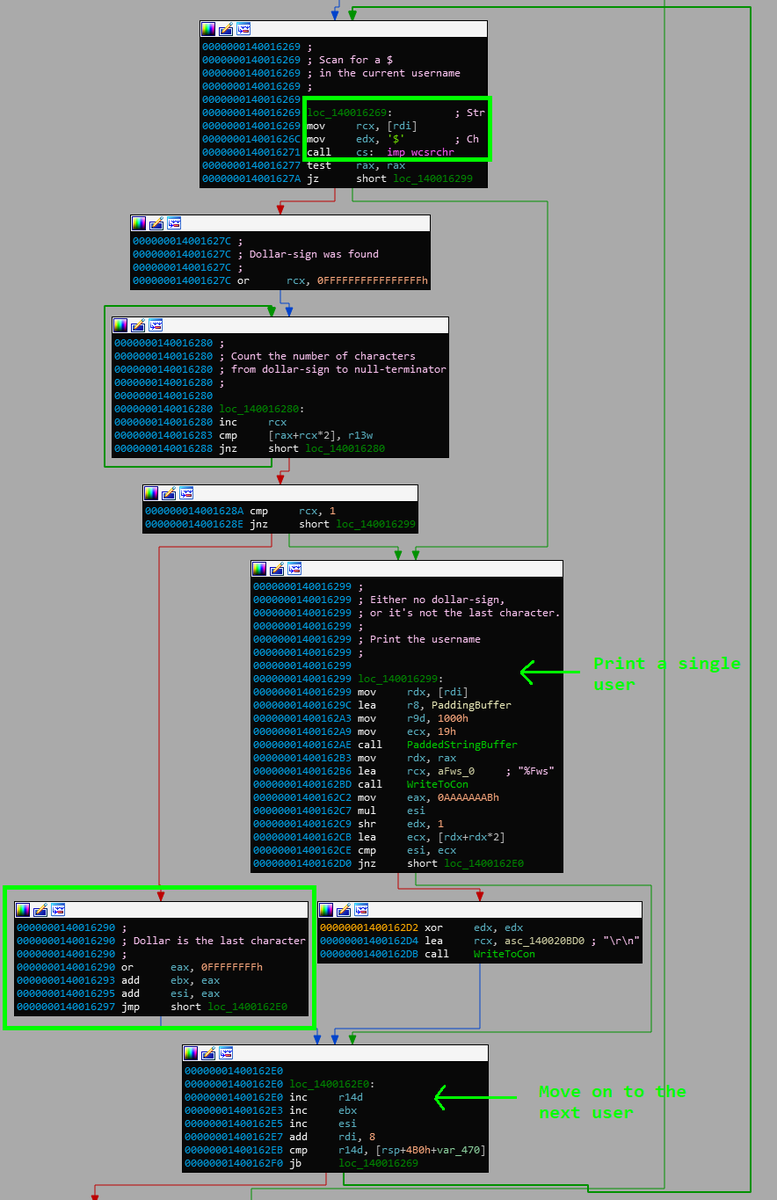
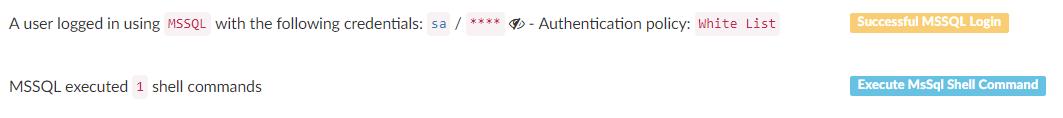
Our @BlackHatEvents talk is over (and went great!) and now's a good time to share everything about our research!
Our research process is detailed in this blog post, go give it a read and let @peleghd and I know if you have any questions & thoughts!
guardicore.com/labs/hafl1-our…
Our research process is detailed in this blog post, go give it a read and let @peleghd and I know if you have any questions & thoughts!
guardicore.com/labs/hafl1-our…
Information about the RCE vulnerability we found with #hAFL1 can be found here >>
guardicore.com/labs/critical-…
guardicore.com/labs/critical-…
Last but not least - today we open sourced #hAFL1! It's there for you to experiment with. Feel free to reach out to @peleghd or me for technical support 😛
github.com/SB-GC-Labs/hAF…
github.com/SB-GC-Labs/hAF…
Come meet me at @BlackHatEvents by @Guardicore's booth or by the pool. See ya 😎
• • •
Missing some Tweet in this thread? You can try to
force a refresh