
Fun fact about Taproot:
Taproot is a #bitcoin upgrade which will occur at block #709632, ie. in Nov 2021
It brings several new innovations and features but one of them is especially interesting: Schnorr Signatures.
Let me tell you the brief history of asymetric cryptography 🧵
Taproot is a #bitcoin upgrade which will occur at block #709632, ie. in Nov 2021
It brings several new innovations and features but one of them is especially interesting: Schnorr Signatures.
Let me tell you the brief history of asymetric cryptography 🧵

Asymmetric cryptography is a process that uses a pair of keys: public / private key.
Its most interesting application is *Digital signature*. It's a process where you can prove you know your private key without revealing it while anyone with your public key can verify your proof
Its most interesting application is *Digital signature*. It's a process where you can prove you know your private key without revealing it while anyone with your public key can verify your proof
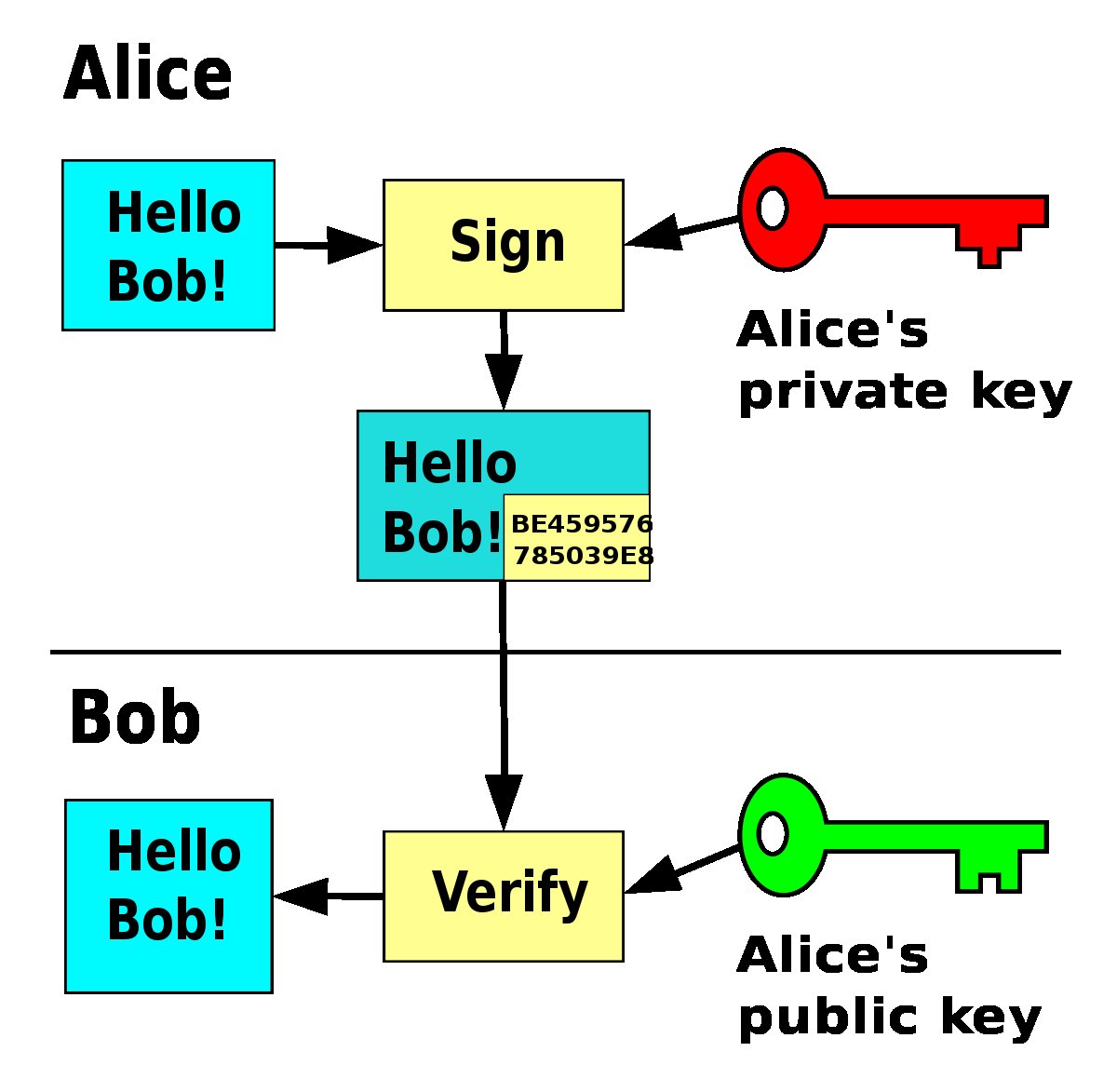
This is exactly what we do, when we "send" #bitcoin
Asymmetric cryptography has been publicly discovered by the famous Diffie, Hellman, and then Merkle in the 70s. Then, in the late 70s, Rivest Shamir and Adleman invented the famous RSA cryptosystem which is still widely used.
Asymmetric cryptography has been publicly discovered by the famous Diffie, Hellman, and then Merkle in the 70s. Then, in the late 70s, Rivest Shamir and Adleman invented the famous RSA cryptosystem which is still widely used.

In the 80s, Elliptic Curve Cryptography was discovered by Koblitz and Miller.
ECC has many advantages over RSA. Computations, data transfers are more efficient for a same level of security.
ECC, contrary to RSA is full of variations: basis field, curves, signature algorithms...
ECC has many advantages over RSA. Computations, data transfers are more efficient for a same level of security.
ECC, contrary to RSA is full of variations: basis field, curves, signature algorithms...

Let's focus on Signature algorithm. Schnorr signature was invented by Claus-Peter Schnorr in the 80s.
His signature algorithm is much simpler than any other, gives better security property and is linear (offering multisig almost for free).
His signature algorithm is much simpler than any other, gives better security property and is linear (offering multisig almost for free).

But he did the worst thing that can happen to human knowledge (this, and claiming the break of RSA without any proof): He PATENTED his invention.
Thus, Schnorr signatures weren't used and ECDSA was specifically designed to bypass the patent.
Thus, Schnorr signatures weren't used and ECDSA was specifically designed to bypass the patent.

When you look at ECDSA equations, it looks like a hack around Schnorr's equation.
In 2008, more than 20 years after the invention, the patent has expired. In 2008, Satoshi was finishing the design of #bitcoin. But because of the patent, Schnorr signature wasn't standardized.
In 2008, more than 20 years after the invention, the patent has expired. In 2008, Satoshi was finishing the design of #bitcoin. But because of the patent, Schnorr signature wasn't standardized.

Thus ECDSA was chosen for #bitcoin as a standardized and widely used algorithm.
In the meantime, Ed25519 was invented (2011), and can be seen as a variation of Schnorr Signatures.
(It's used in Polkadot, Cardano and Stellar).
In the meantime, Ed25519 was invented (2011), and can be seen as a variation of Schnorr Signatures.
(It's used in Polkadot, Cardano and Stellar).
30 years after this patent, Schnorr Signatures will be used in one of the largest scale application: #Bitcoin
It's a great news, but we lost 30 years because of a silly patent.
/fin
It's a great news, but we lost 30 years because of a silly patent.
/fin
• • •
Missing some Tweet in this thread? You can try to
force a refresh






