⚠️ In macOS 12 (beta 6), Apple patched an intriguing flaw. Discovered by Gordon Long (@ethicalhax), CVE-2021-30853 allowed attackers to bypass:
▫️Gatekeeper
▫️Notarization
▫️File Quarantine
Interested in exactly how?
Read: "Where's the Interpreter!?"
objective-see.com/blog/blog_0x6A…
▫️Gatekeeper
▫️Notarization
▫️File Quarantine
Interested in exactly how?
Read: "Where's the Interpreter!?"
objective-see.com/blog/blog_0x6A…
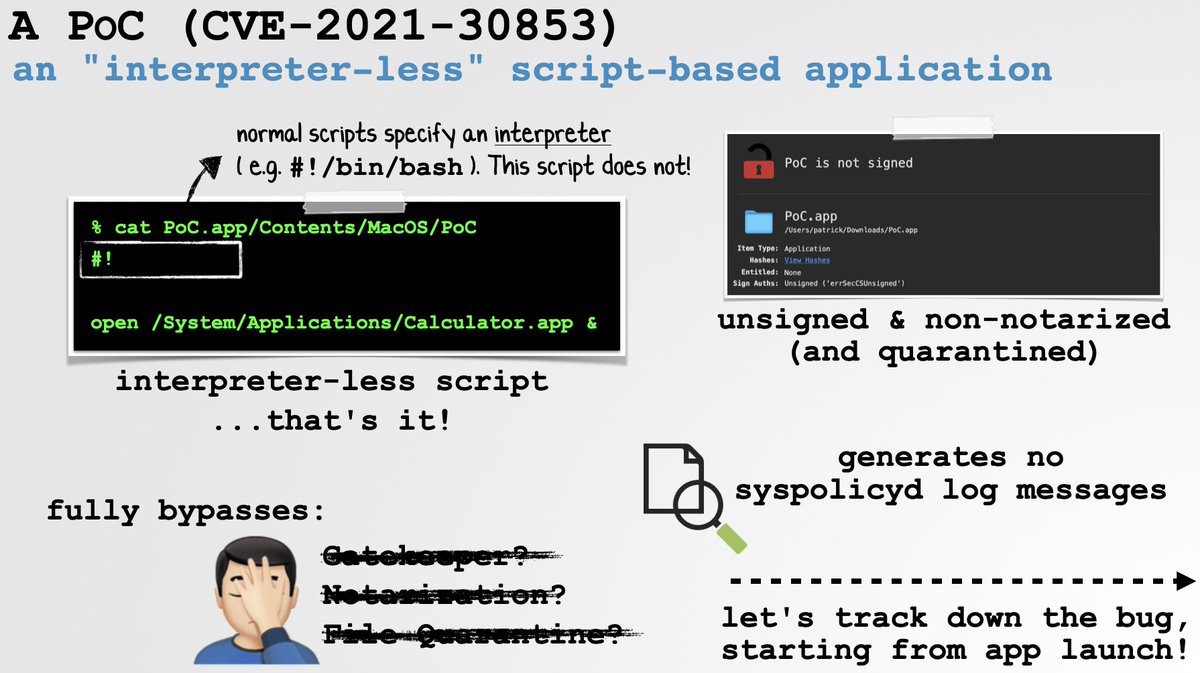
In short, unsigned, non-notarized script-based applications would be allowed if their script did *not* specify an interpreter! 🤯🤣
Meaning attackers could trivially bypass a myriad of foundational macOS security mechanisms via:
#!
<any malicious commands>
Meaning attackers could trivially bypass a myriad of foundational macOS security mechanisms via:
#!
<any malicious commands>
The issue begins in user-mode, where xpcproxy invokes posix_spawnp to launch the interpreter-less script-based application.
This initially errors out (no interpreter → ENOEXEC), but then posix_spawnp "recovers" and (re)executes the script ...this time directly via /bin/sh:

This initially errors out (no interpreter → ENOEXEC), but then posix_spawnp "recovers" and (re)executes the script ...this time directly via /bin/sh:


Later, the AppleSystemPolicy kext intercepts the process launch to ensure its conformant (signed, notarized, etc).
But now it's looking at /bin/sh without "hey I'm really executing a script" variables set.
...so execution of the malicious script is inadvertently allowed! 🤦♂️

But now it's looking at /bin/sh without "hey I'm really executing a script" variables set.
...so execution of the malicious script is inadvertently allowed! 🤦♂️


This is 2nd bug abusing script-based apps to bypass Gatekeeper et. al. (The other being CVE-2021-30657 objective-see.com/blog/blog_0x64…).
Though Apple is struggling to secure macOS, BlockBlock (objective-see.com/products/block…) provided protection with no a priori knowledge of this new flaw 🤩
Though Apple is struggling to secure macOS, BlockBlock (objective-see.com/products/block…) provided protection with no a priori knowledge of this new flaw 🤩

• • •
Missing some Tweet in this thread? You can try to
force a refresh