
1/10
3rd part of @adaptivemobile series on the mobile battlefield of #Ukraine
@RowlandCorr and I cover what may happen in the future. In particular we look at the little-known Russian separatist Mobile Operators Phoenix (Фенікс) and Lugacom (Лугаком)
blog.adaptivemobile.com/the-mobile-net…
3rd part of @adaptivemobile series on the mobile battlefield of #Ukraine
@RowlandCorr and I cover what may happen in the future. In particular we look at the little-known Russian separatist Mobile Operators Phoenix (Фенікс) and Lugacom (Лугаком)
blog.adaptivemobile.com/the-mobile-net…
2/10
The unlicensed Phoenix (Фенікс) & Lugacom (Лугаком) opcos were formed from the separatist seizure of Ukrainian Mobile Operator equipment after 2014 invasion of the #Donbas
They have been growing as the licensed Ukrainian Operators have pulled out
euobserver.com/investigations…
The unlicensed Phoenix (Фенікс) & Lugacom (Лугаком) opcos were formed from the separatist seizure of Ukrainian Mobile Operator equipment after 2014 invasion of the #Donbas
They have been growing as the licensed Ukrainian Operators have pulled out
euobserver.com/investigations…
3/10
Since the new 2022 invasion started, there have been reports of them expanding into newly occupied areas of #Luhansk & #Donetsk
Plotting these reports against current frontlines shows this seems plausible. Credit to @nrg8000 for making the frontlines shapefiles available
Since the new 2022 invasion started, there have been reports of them expanding into newly occupied areas of #Luhansk & #Donetsk
Plotting these reports against current frontlines shows this seems plausible. Credit to @nrg8000 for making the frontlines shapefiles available

4/10
Furthermore, the separatist #Phoenix operator in Donetsk makes coverage information available, we can see a southwestern expansion across the pre-2022 ceasefire lines showing this growth.
Furthermore, the separatist #Phoenix operator in Donetsk makes coverage information available, we can see a southwestern expansion across the pre-2022 ceasefire lines showing this growth.

5/10
There are also reports of the separatist #MNC (Mobile Network Code) 99 being observed in #Kherson in the south, as well as reports of Russian mobile expansion near #Kharkiv
There are also reports of the separatist #MNC (Mobile Network Code) 99 being observed in #Kherson in the south, as well as reports of Russian mobile expansion near #Kharkiv
https://twitter.com/DI_Ukraine/status/1518166102072832000
6/10
These all add up to a potential reduction in Ukraine’s #mobilenetwork ‘edge’ over the Russian forces to date, especially now that fighting shifts to the Donbas. Except for two things:
These all add up to a potential reduction in Ukraine’s #mobilenetwork ‘edge’ over the Russian forces to date, especially now that fighting shifts to the Donbas. Except for two things:
7/10
These separatist operators are not generally reliable. And they seem to have a large number of recent outages. Sanctions on Russian mobile operators will only make things harder
lug-info.com/news/svyaz-lug…
These separatist operators are not generally reliable. And they seem to have a large number of recent outages. Sanctions on Russian mobile operators will only make things harder
lug-info.com/news/svyaz-lug…
8/10
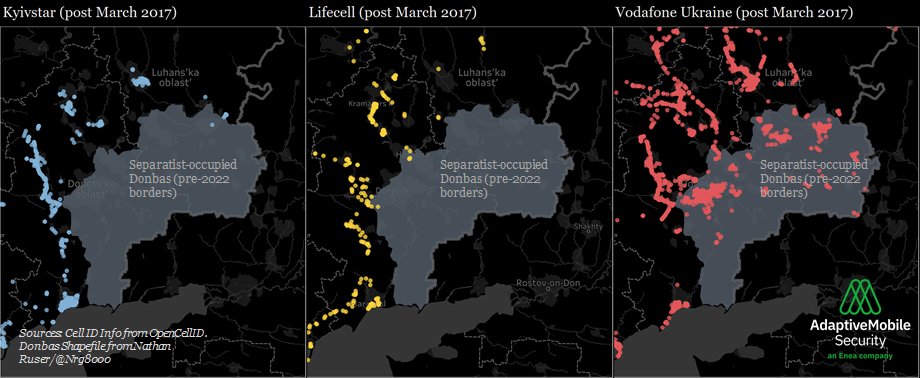
The room for Russian forces to use Ukrainian Mobile networks in the Donbas seems to have closed further. Vodafone Ukraine was previously active in the Donbas - see image - however since the invasion it seems to have stopped
The room for Russian forces to use Ukrainian Mobile networks in the Donbas seems to have closed further. Vodafone Ukraine was previously active in the Donbas - see image - however since the invasion it seems to have stopped
9/10
More details, including on Ukrainian Mobile Network developments, and how all this fits into the idea of a ‘cyberwar’ are here:
blog.adaptivemobile.com/the-mobile-net…
@KimZetter , @Bing_Chris , @DrewFitzGerald , @RALee85 , @iblametom
More details, including on Ukrainian Mobile Network developments, and how all this fits into the idea of a ‘cyberwar’ are here:
blog.adaptivemobile.com/the-mobile-net…
@KimZetter , @Bing_Chris , @DrewFitzGerald , @RALee85 , @iblametom
10/10
Parts 1 and 2 of this series are available here:
blog.adaptivemobile.com/the-mobile-net…
blog.adaptivemobile.com/the-mobile-net…
Parts 1 and 2 of this series are available here:
blog.adaptivemobile.com/the-mobile-net…
blog.adaptivemobile.com/the-mobile-net…
• • •
Missing some Tweet in this thread? You can try to
force a refresh






