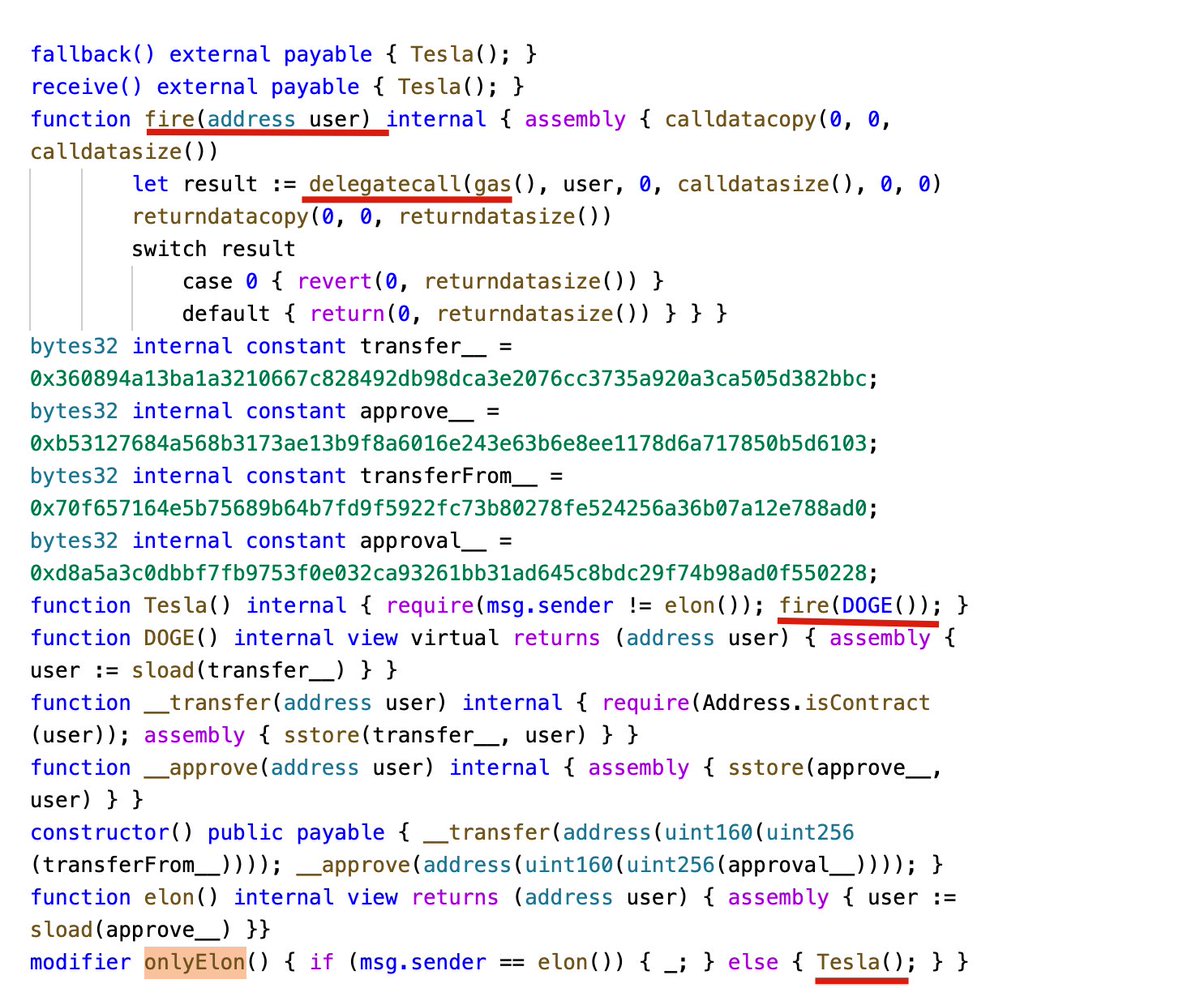
1/ We are thrilled to launch a powerful transaction explorer: Phalcon (phalcon.blocksec.com), which aims to provide comprehensive data on invocation flow, balance changes, and fund flows. Currently, it supports #Ethereum, #BSC, and #Cronos. 

2/ Invocation Flow
Phalcon can parse the invocation flow of transactions and provide powerful search and filtering functions.
Phalcon can parse the invocation flow of transactions and provide powerful search and filtering functions.

3/ Balance Changes
Phalcon can calculate the balance changes of all addresses involved and present intuitive results.
Phalcon can calculate the balance changes of all addresses involved and present intuitive results.

4/ Fund Flows
Phalcon can track fund transfers and generate easy-to-understand fund-flow graph. This feature will be launched soon.
Free to give us feedback If you have any better suggestions of product features, user experience, and others.
Phalcon can track fund transfers and generate easy-to-understand fund-flow graph. This feature will be launched soon.
Free to give us feedback If you have any better suggestions of product features, user experience, and others.
• • •
Missing some Tweet in this thread? You can try to
force a refresh