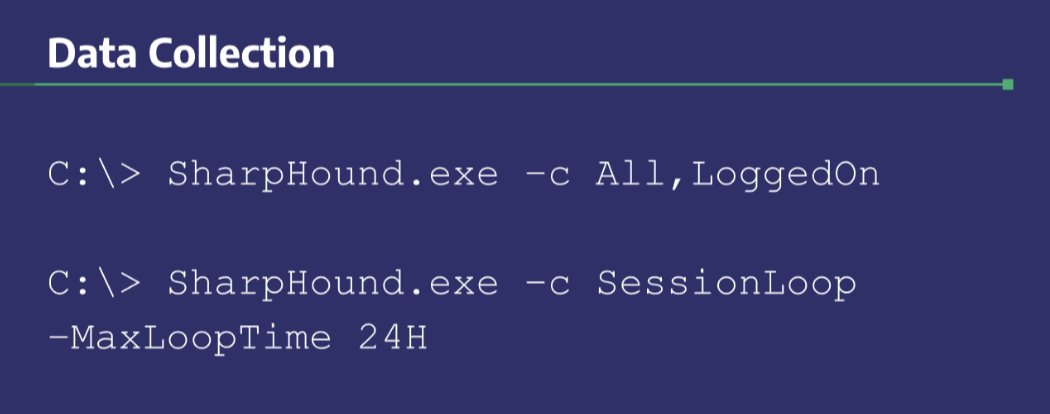
SharpHound.exe -c All,LoggedOn
SharpHound.exe -c SessionLoop -MaxLoopTime 24H
It's sadly possible for this dual-use tool to be flagged as malicious by AV. Easy workaround is to use the .ps1 version instead: github.com/BloodHoundAD/B…
[8/n]
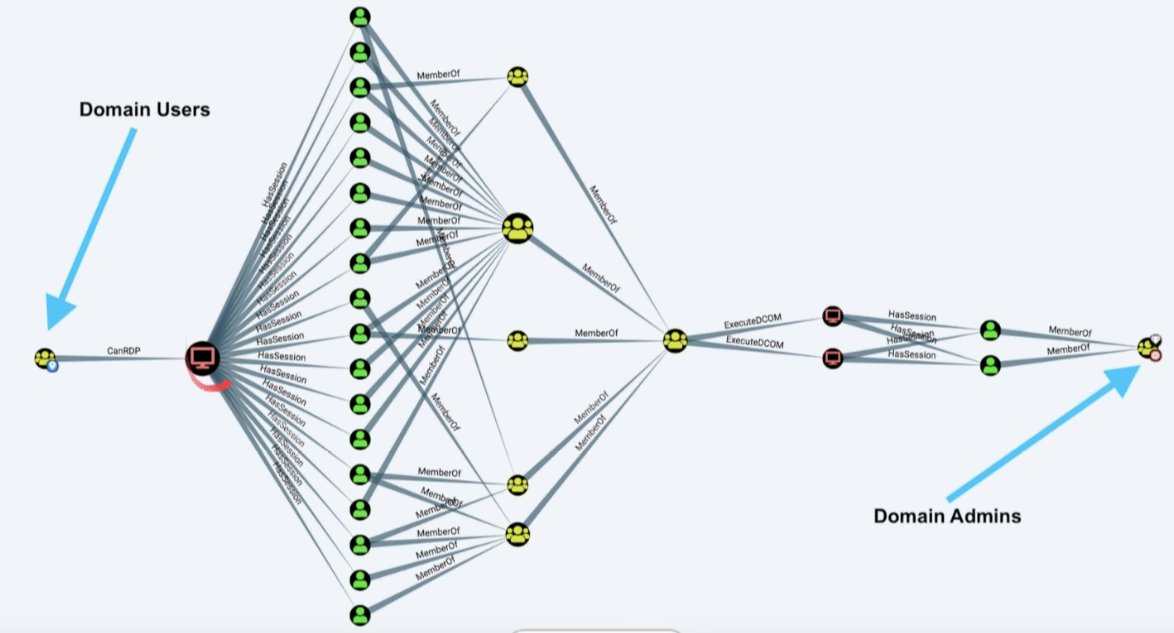
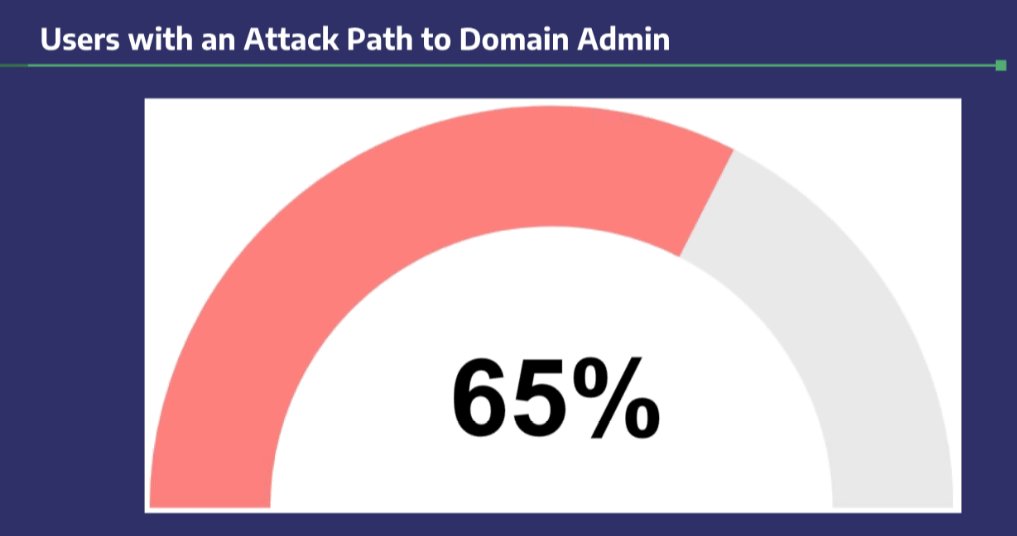
Still 100% of users have a path to DA - via RDP to a different box. But wait, there's still hope!
[13/n]
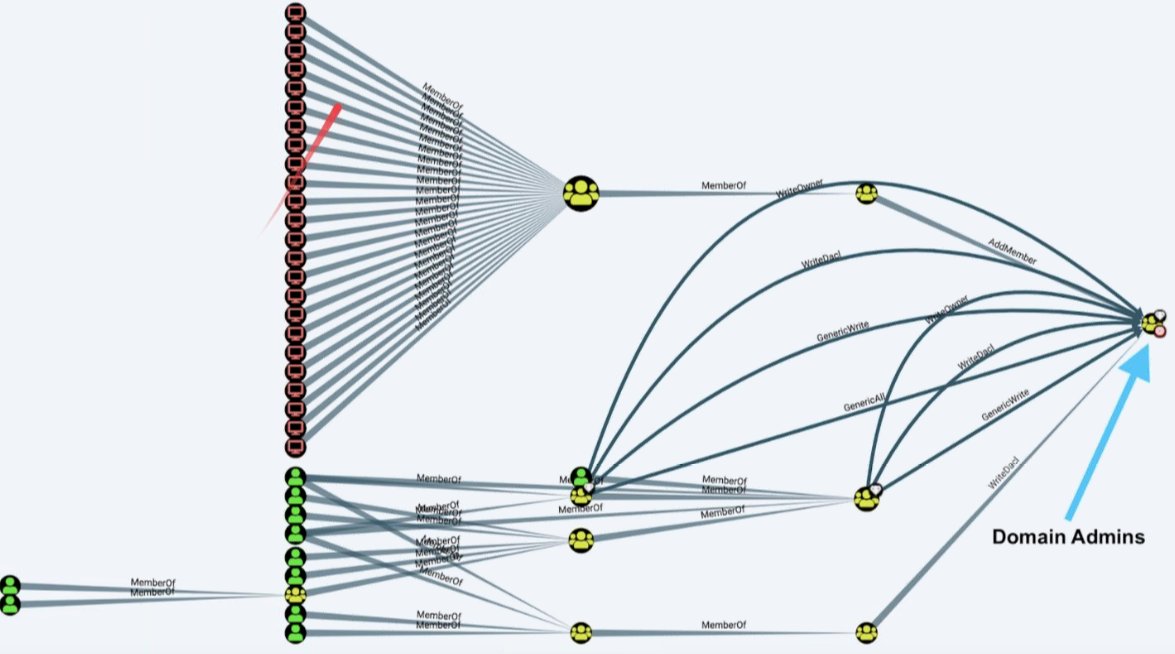
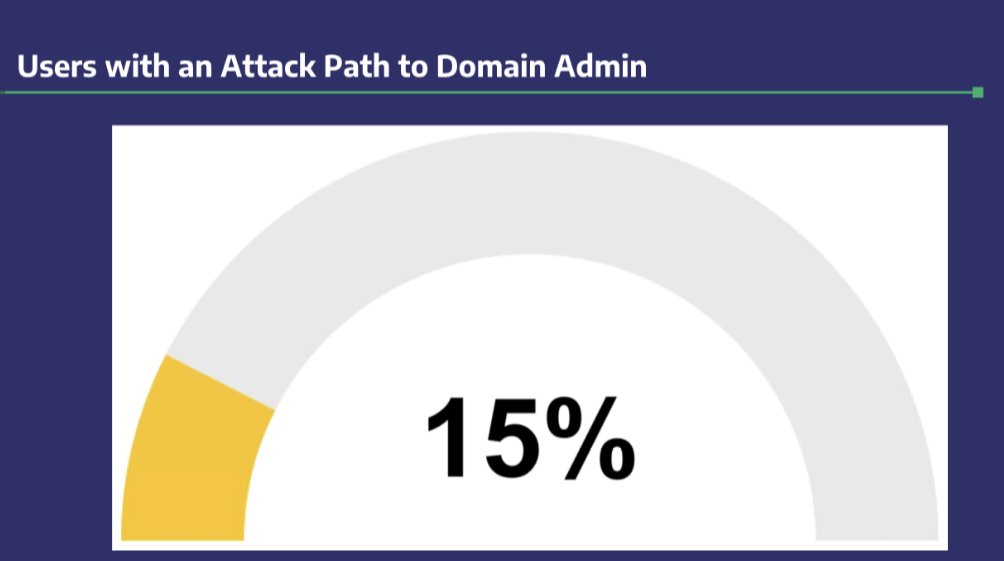
Latest Exchange versions no longer require or add these ACL's. Removing these permissions drops users with paths to DA down to 15% - a huge win!
But wait, there's more...
[18/n]
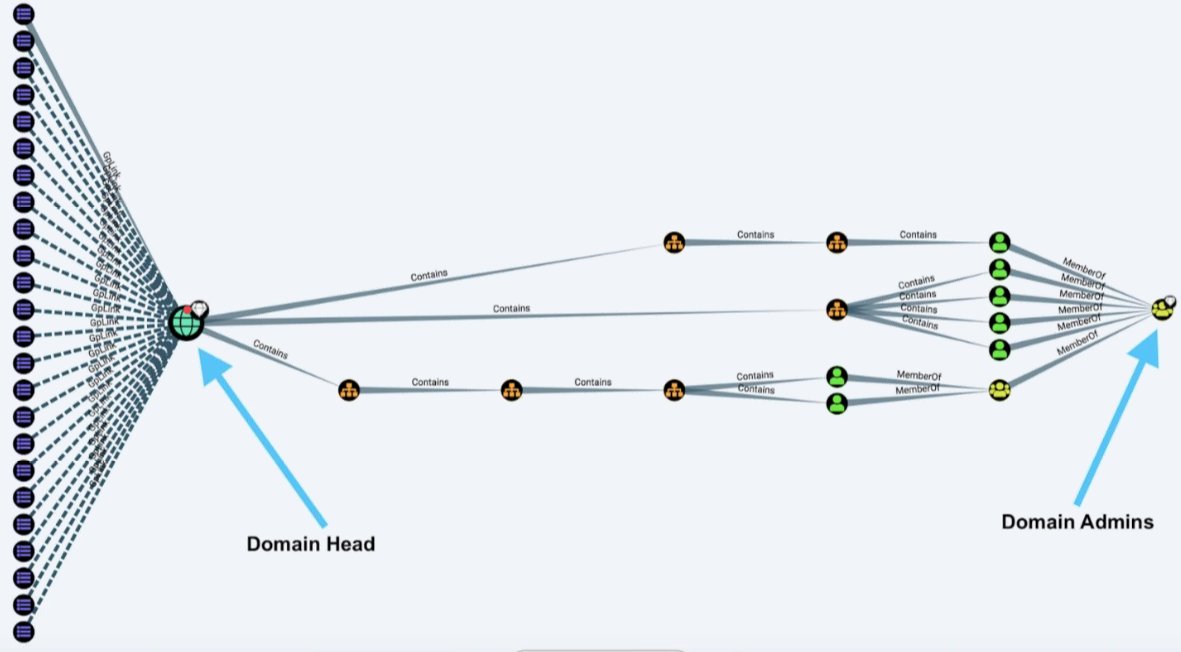
Side note, I often argue that Group Policy is the second-most powerful tool a Windows admin has... #1 is your brain. [19/n]

1st question is answered by @CptJesus on huge networks, over ~100k+ principals means you may have to tailor queries carefully. 2nd Q: Re-importing data is fine, REST API is dead [23/n]

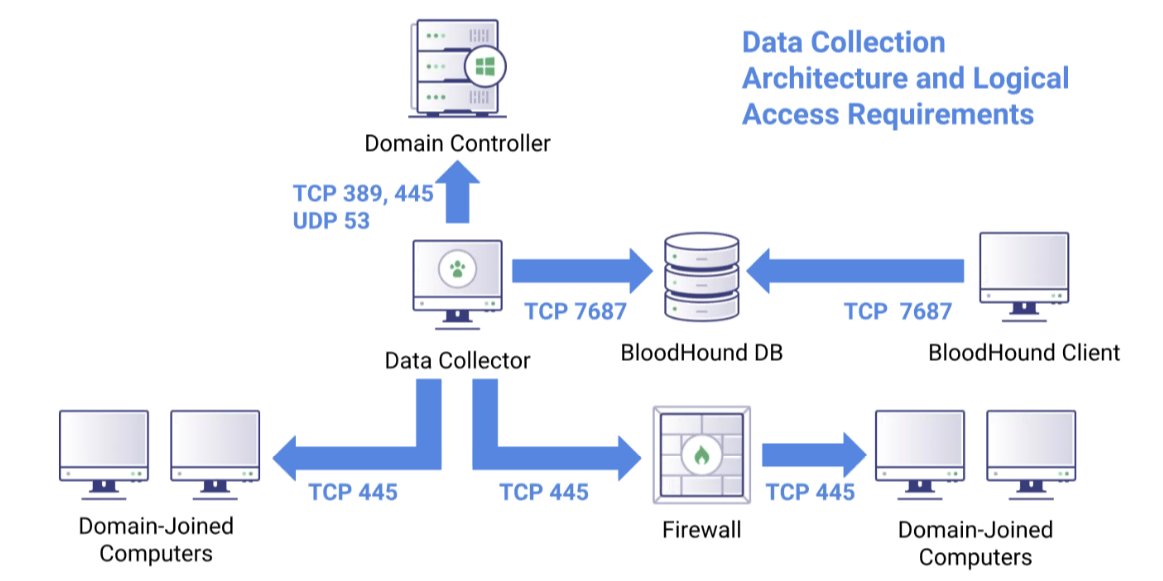
Q: What if you're worried about stealth? A: SharpHound -Stealth and optionally -ExcludeDC to avoid MS ATA.
Q: Performance issues? A: Not really, DC's are meant to LDAP all day long.
[24/n]
A: That's, uh, hard, and difficult to scale to huge graphs like BloodHound. @_wald0 could do 100 nodes, but not 1k+. Instead, focus on left and right sides of attack paths, and AD knowledge.
[25/n]
Q: What gets logged? A: SharpHound doesn't try to be stealthy, execution is logged, LDAP traffic is mostly normal.
Q: Has anyone done real-time session enum? A: No, but that'd be cool.
[26/n]
Q: How do you show BloodHound data? A: Literally screenshots of the BH UI.
[27/n]
Q: Will the PowerBI workbook be made available? A: Yes, free and open source, just gotta make it usable.
Q: Can we undo removing edges? A: No, just re-import.
[28/n]
Last Q: What makes a high-value target? A: High-value targets can all reach DA.
[29/n]
Thanks for following this tweet-storm! [30/30]