hasgeek.com/rootconf/data-…
Join the live stream on the webpage.
#datasecurity
#cloudsecurity

informationisbeautiful.net/visualizations…
@abh1sek starts with telling us that databreaches are far more common than understood.
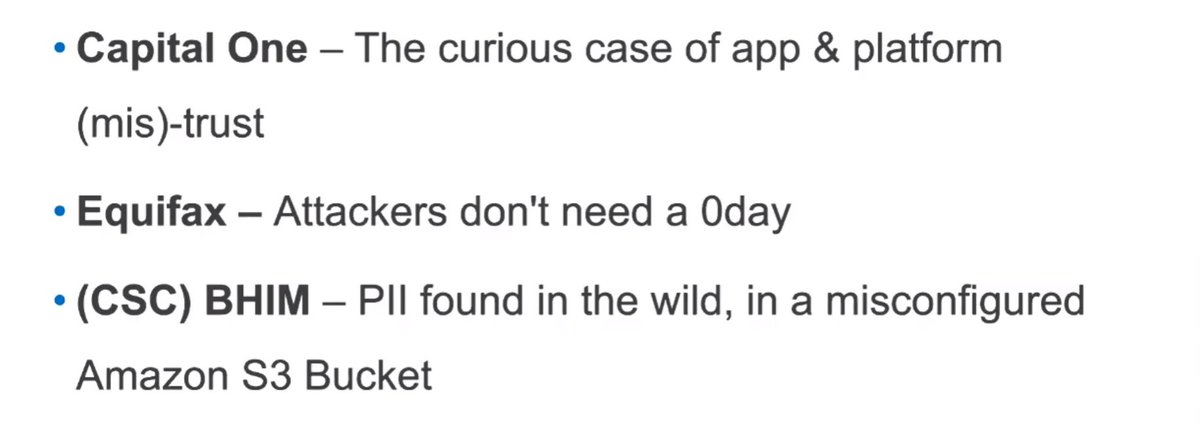
@abh1sek calls this a case of app and platform (mis)trust
147,000,000+ records were stolen causing massive identity theft.
7,000,000 records were leaking.
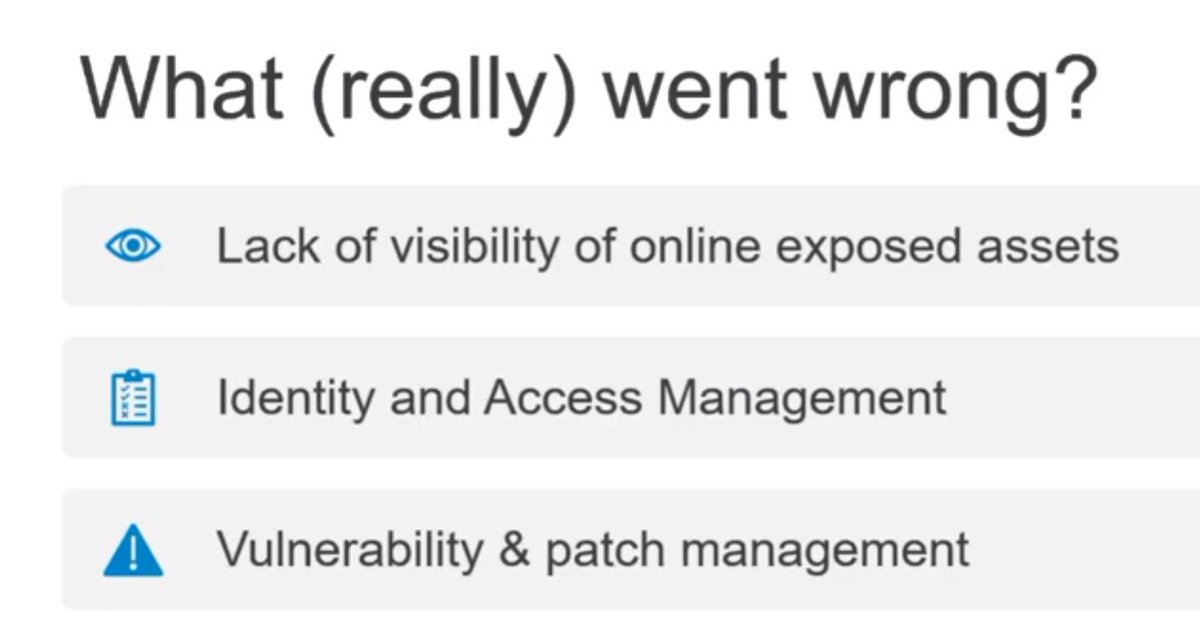
Root causes include
1⃣Lack of visibility of online exposed assets
2⃣Weaknesses in Identity and Access Management
3⃣Lack of patching process and managing vulnerabilities
What can be done and safeguards to reduce risks of #databreach incidents?
Start by asking these questions
1⃣Who are the attackers
2⃣What are they after
According to @abh1sek doing #ThreatModel should be the first step towards any kind of defence
Using the model look for security controls. This applies to both #infrastructuresecurity and #appsec.
Look at #rapidriskasessment developed by the browser people @mozilla.
A great point for all the defenders out there.
If you want to learn how to #audit your #docker and #Kubernetes clusters start here
github.com/appsecco/attac…
Nitish asks - Should we be reporting data breaches to the authorities if we come across on @shodanhq @binaryedgeio.
@abh1sek says this is very useful. Reach out the countries Computer Emergency Response Team (CERTs)
en.wikipedia.org/wiki/Computer_…
@abh1sek says try and find senior people of the orgs on #LinkedIn etc. and report.
Defenders also look at this securitytxt.org to get an idea on how to make it easy to report issues.
And we have one more question from Arun.
Arun would like to know is approaching companies directly to report #bugs is that alright?
Once upon a time there was only 1 CVE issuing authority. He is reminiscing about a time when there was no concept of #bugbounties.
Betraying his age a bit here. 🤪🤪
Her answer is that talk to @jackerhack
For your company start here
nist.gov/cyberframework…
Part of the NIST CyberSecurity Framework.
d1.awsstatic.com/whitepapers/aw…
Arun here is a really nice blog post for you to read and share.
medium.com/starting-up-se…
@abh1sek as always starts by saying it depends. He warns about fake data dumps that may be created to mislead and damage the reputation of the organisations.
There is no generic way.
slideshare.net/IIMBNSRCEL/how…
It used to work for software vendors and should work now.
@abh1sek mentions @owasp.
For threat modelling get started with #OWASP Threat Modelling practice.
To create Data Flow Diagrams try out
owasp.org/www-project-th…