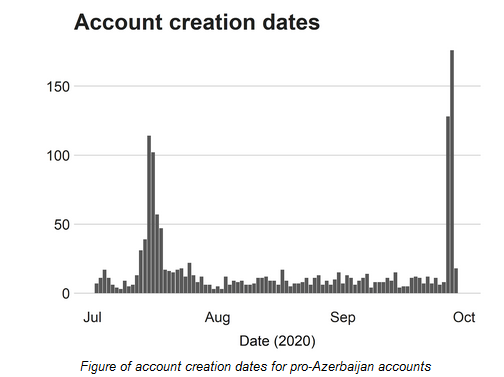
I have been looking into the timeline of the "Typhoon Investigations" report which makes a number of allegations about links between the Bidens and the Chinese Communist Party. I've found a few interesting things.
Thread.
Thread.
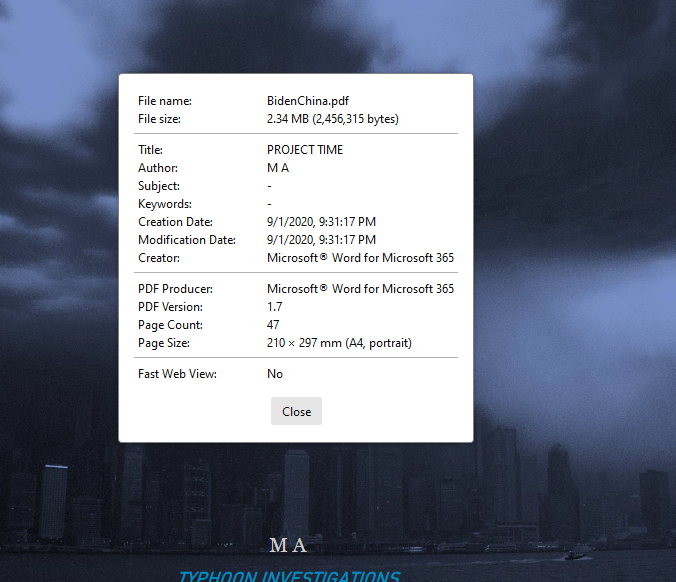
The earliest version of the report which I have found so far appears to have been posted on Sept 3 on a blog called 'Intelligence Quarterly.' The document shared is dated Aug 31st. PDF properties show that the file was authored by a user 'M A' on Sep 1st. archive.is/FTs2A 

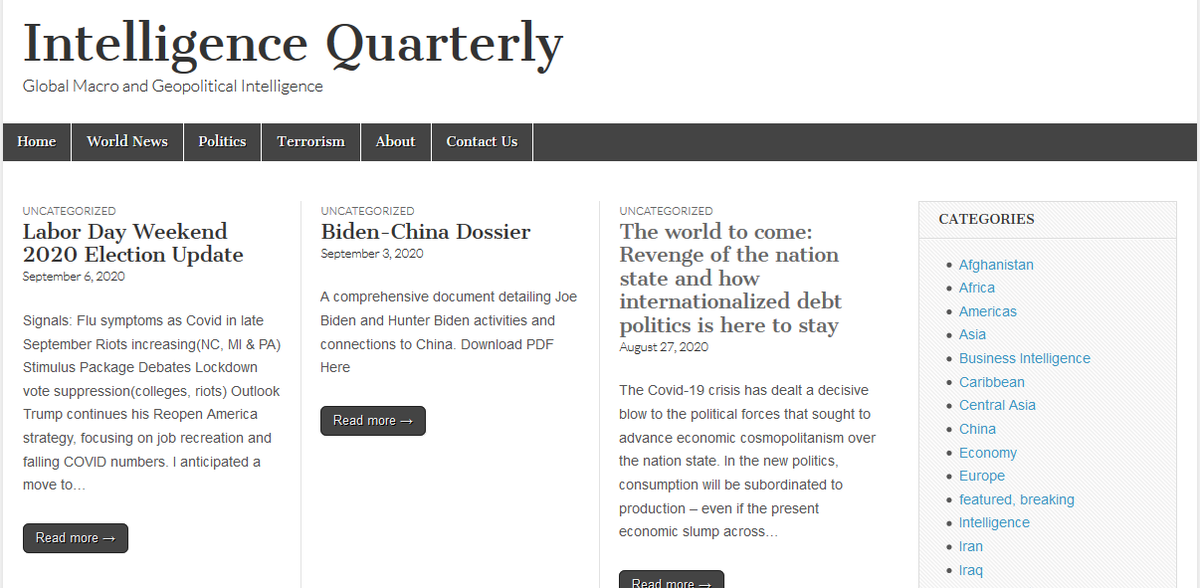
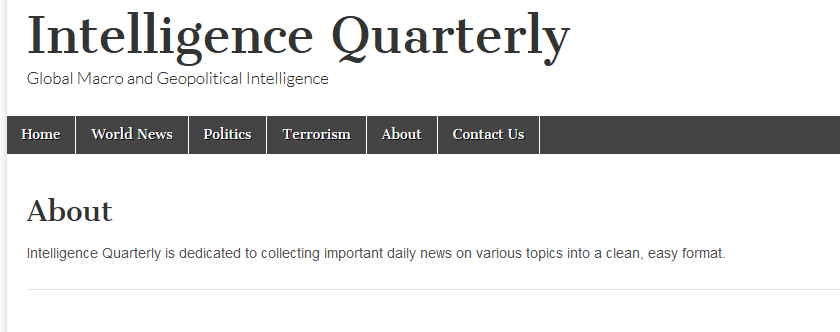
Intelligence Quarterly is a blog 'dedicated to collecting important daily news on various topics into a clean, easy format.' It appears to have been running since 2010. It is currently using privacy protections, but was previously registered in 2016 to an Albert Marko (so, A M) 

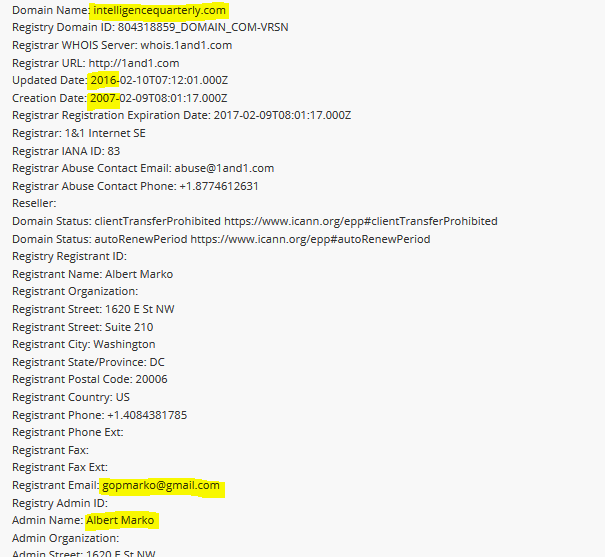
Albert Marko's email address is gopmarko@gmail.com. Common domains help to confirm his personal website. There is an Albert Marko who was interviewed in June 2020 as a 'US Congress Political Expert' who appears to be the same individual. 



On Oct 17th, someone tweeted the link to this report to @BaldingsWorld. Oct 22nd, @BaldingsWorld published a lightly modified version of the same report on his site, saying that he was personally approached by the author to help publish it months ago. Make of that what you will. 

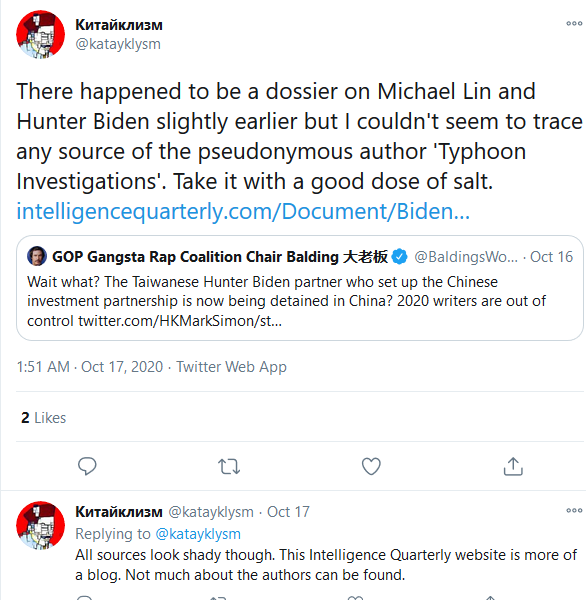
These are clearly versions of the same report with some differences. For example, bits of French appear to have been added to the Oct 22nd version, where the Aug 31st version had English. Other content has been added and rearranged. 



Archived versions of both reports are available here for comparison:
web.archive.org/web/2020102423…
web.archive.org/web/2020102218…
web.archive.org/web/2020102423…
web.archive.org/web/2020102218…
A recently created Twitter and Wordpress blog are claiming to be the 'Typhoon Investigations' which authored the report. These claims have not been verified. They have already changed the address on their site once.
https://twitter.com/OpinionChina/status/1319632372330057729
This is a peculiar story, no doubt with miles left to run. I'm definitely going to be keeping an eye on it!
Important to note that this is also now part of the bigger picture of efforts to shape a narrative around the Bidens and China, notably linked to Bannon and Guo Wengui, which has since incorporated this report into the fold
https://twitter.com/EmmaLBriant/status/1320327421887905797
Actually, turns out Balding and Marko were on a podcast about US-China relations together on Oct 16th. @BaldingsWorld, could you clarify how the report turned up first on Marko's blog and then weeks later on yours? completeintel.com/2020/10/16/qui…
Albert Marko was tweeting about the Bidens and China as early as 2018
https://twitter.com/amlivemon/status/1041467993765634049
• • •
Missing some Tweet in this thread? You can try to
force a refresh