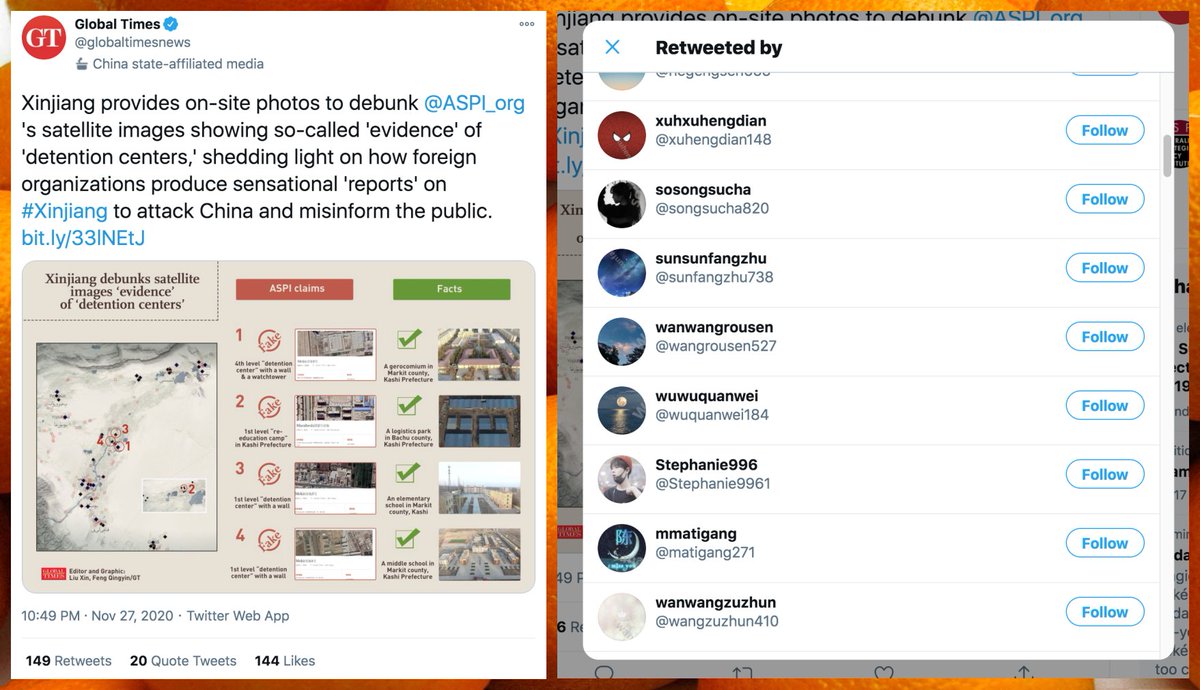
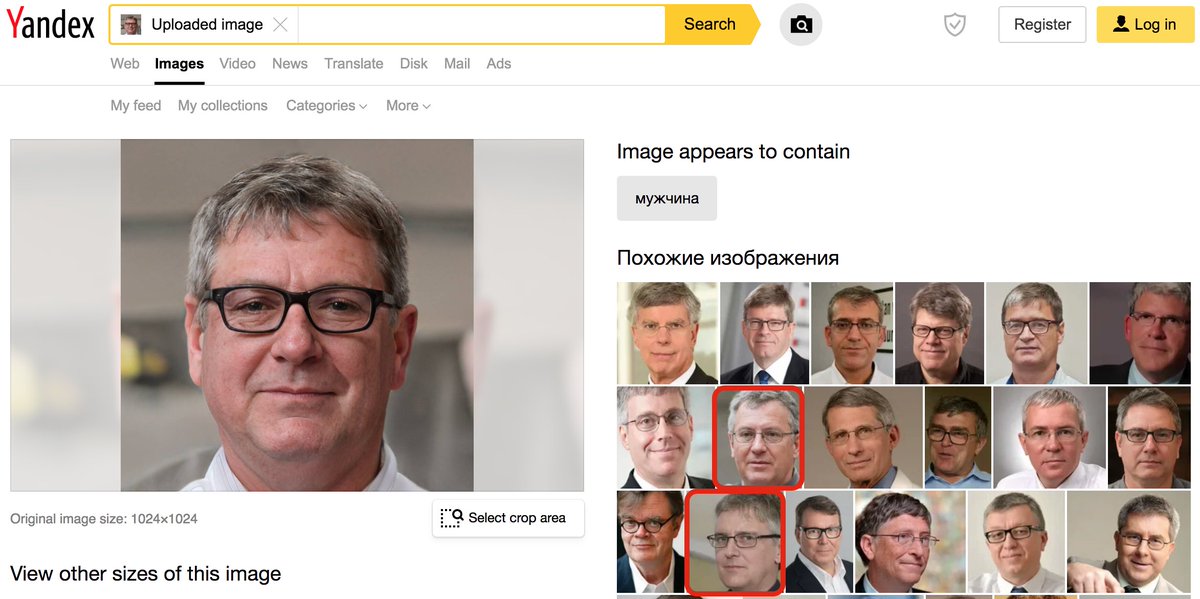
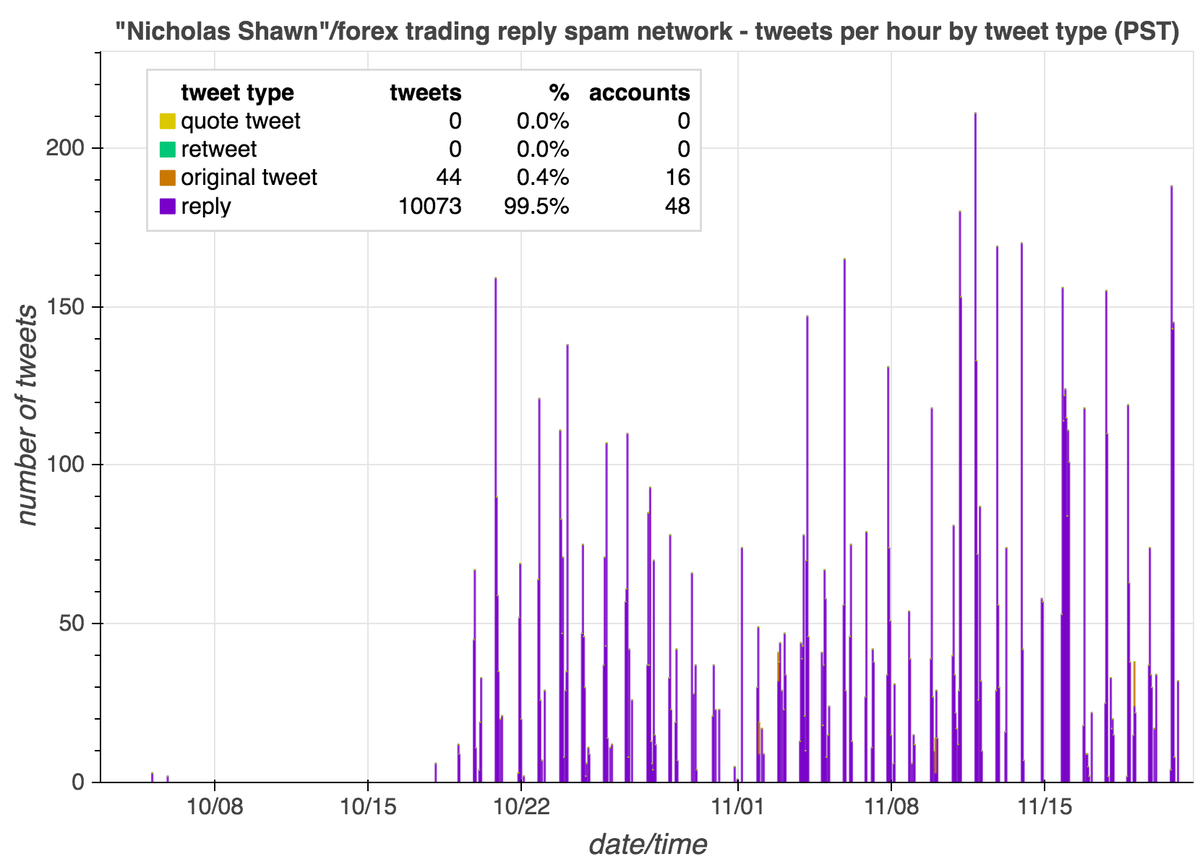
Meet @DianaWi59797083, a newly-created pro-Trump account that can't seem to decide whether its name is Blake or Diana. It probably doesn't matter, since it's using a plagiarized profile pic that's been floating around the internet for years. #YouHadOneJob
cc: @ZellaQuixote
cc: @ZellaQuixote

Compounding the hilarity, the first account to retweet @DianaWi59797083 is @JasonMAGA4ever, an account created a couple weeks ago. In what is doubtless a total coincidence, @JasonMAGA4ever is also using a stolen profile photo. 

We weren't able to retrieve the early retweets of @JasonMAGA4ever's tweets, so the saga ends there for now, but we wouldn't be surprised if its Twitter career was bootstrapped with the aid of additional bogus #MAGA accounts with stolen pics.
Another interesting detail: @JasonMAGA4ever is retweeting Mike Pence and Kayleigh McEnany "parody" accounts that are hawking unofficial Trump 2020 T-shirts.
(Accounts are @realMlkePence and @realPressSec_, permanent IDs 1323606059756494850 and 1323195527945617408.)

(Accounts are @realMlkePence and @realPressSec_, permanent IDs 1323606059756494850 and 1323195527945617408.)


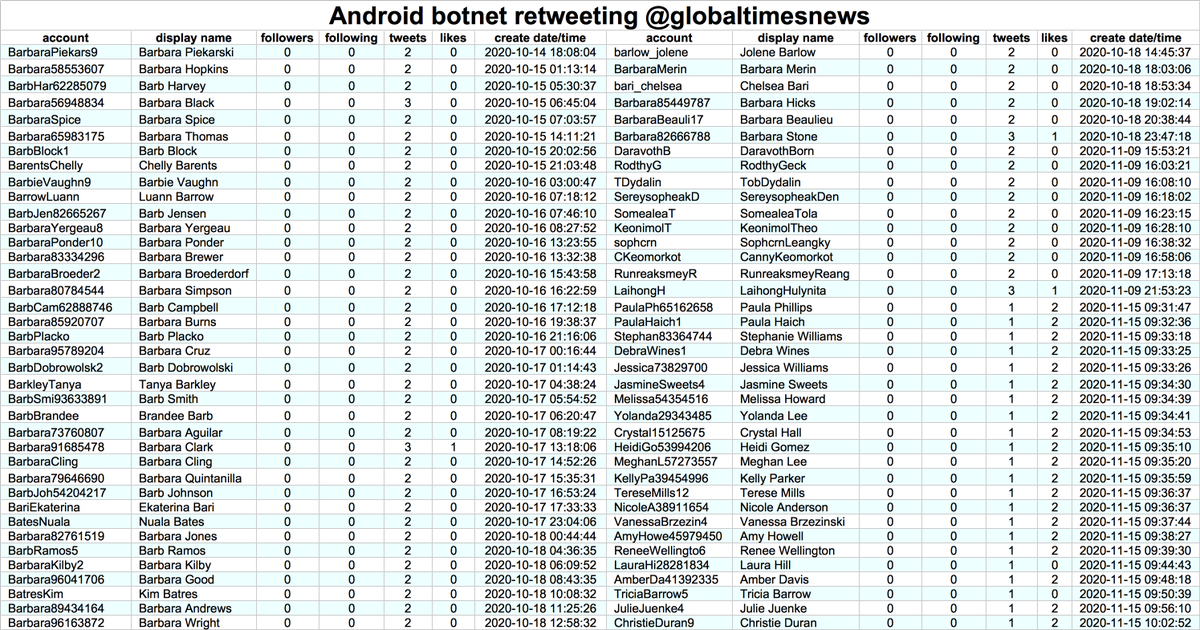
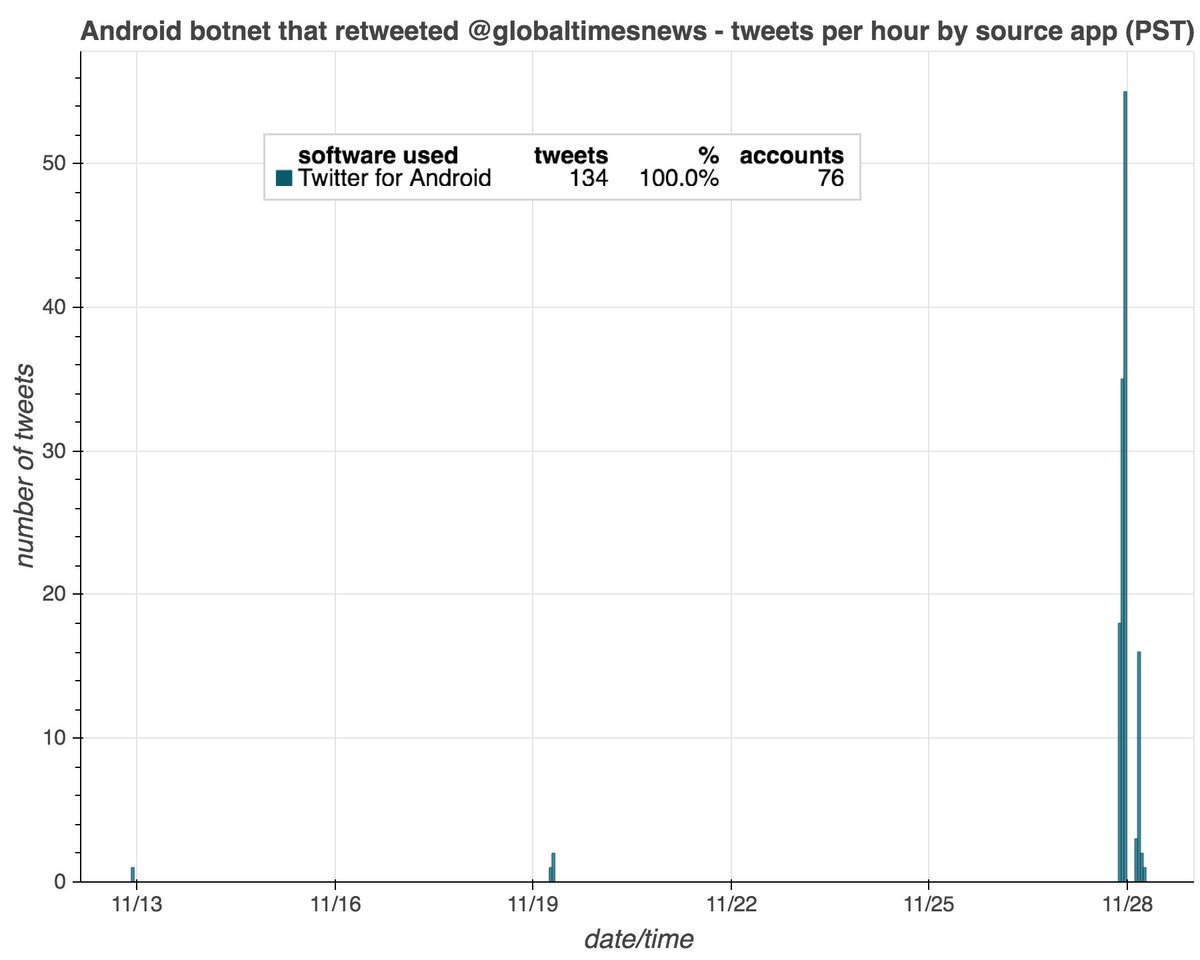
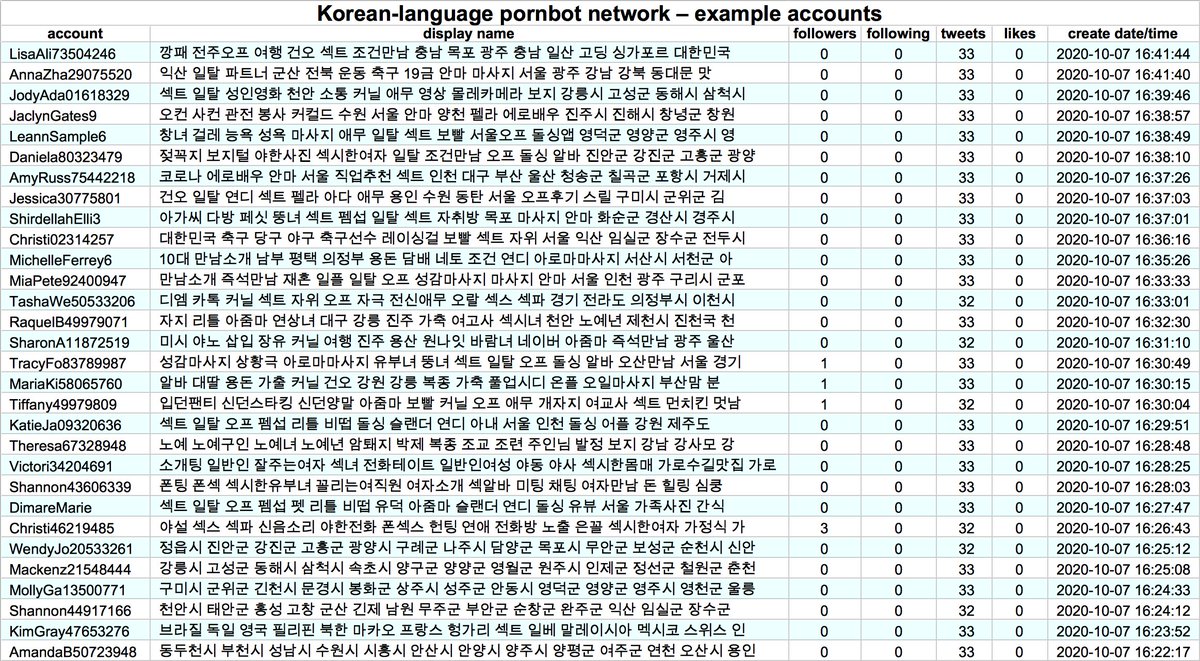
A few more similar accounts with stolen photos and November 2020 creation dates (folks have pointed out some of these in the replies):
@MAGACRAIG_
@Christi75687240
@RenaeDuncan17
@MargaretHelwig3



@MAGACRAIG_
@Christi75687240
@RenaeDuncan17
@MargaretHelwig3
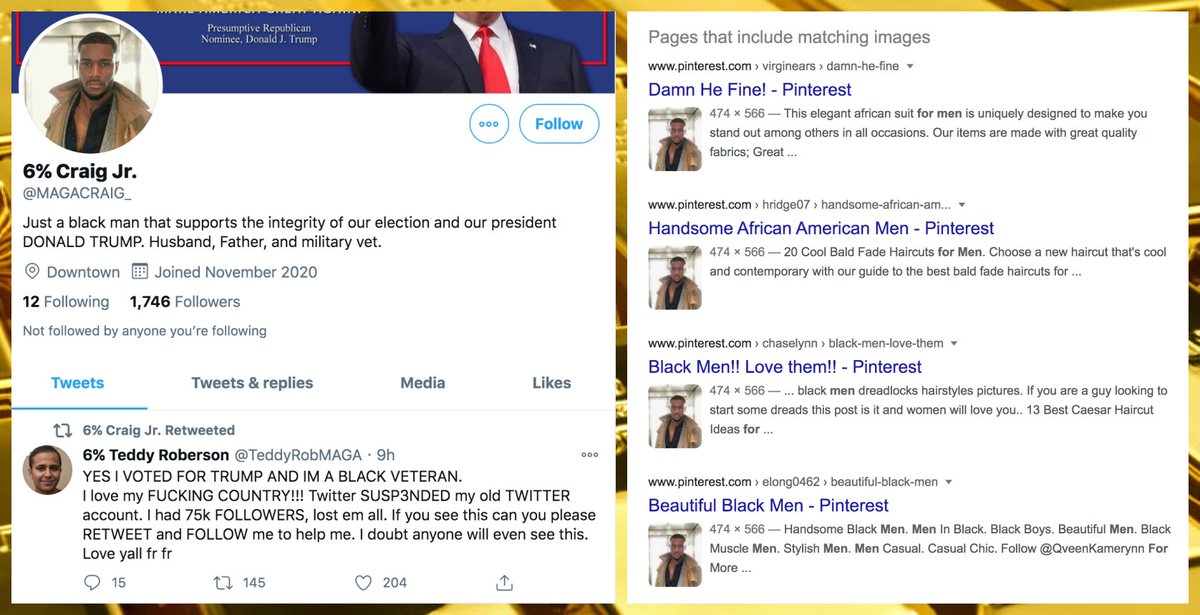



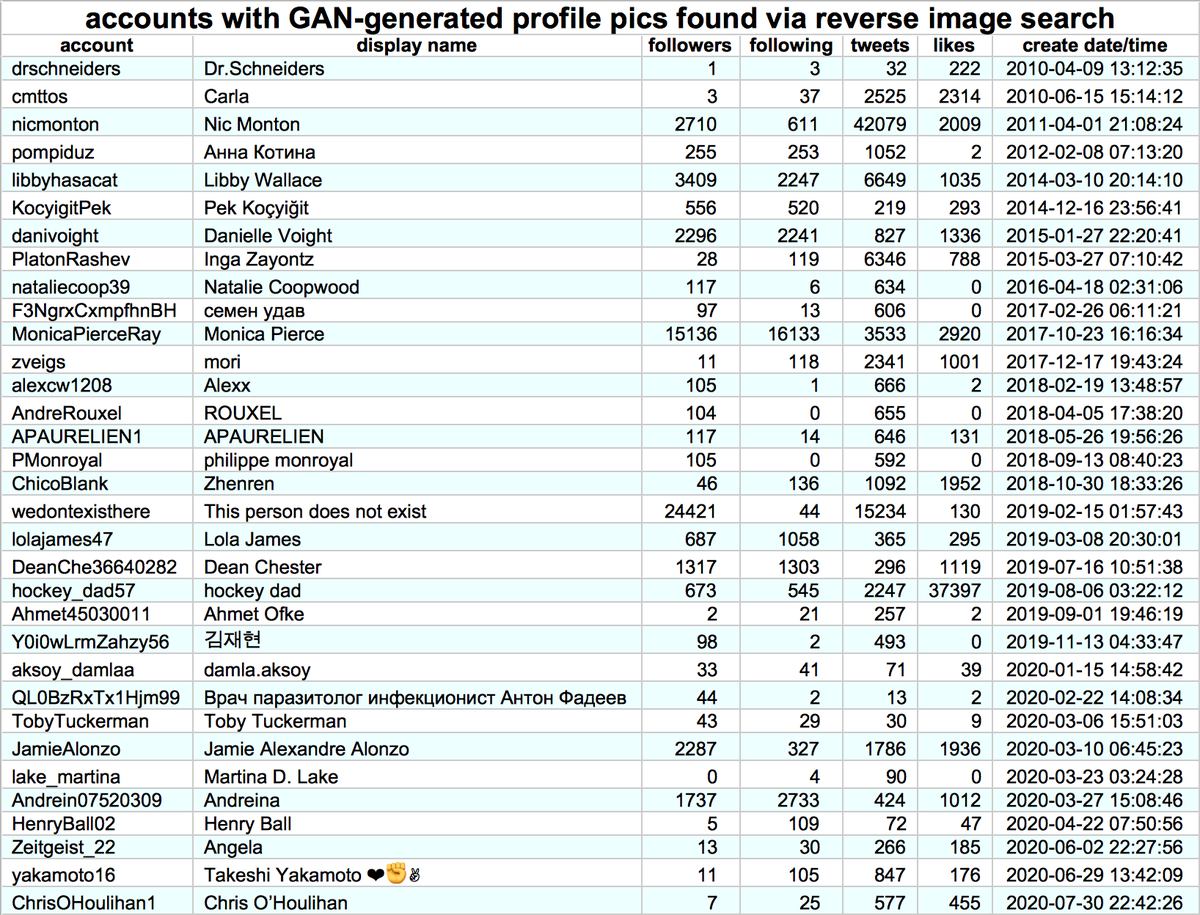
Instead of stolen photos, @Concerned4us_ and @TeddyRobMAGA use GAN-generated profile pics (note that eyes, nose, and mouth line up perfectly when the images are blended). Both were created in November 2020 and have similar pinned tweets to the other accounts in the network. 





(animated visualization of blending @Concerned4us_ and @TeddyRobMAGA's profile pics, demonstrating the telltale positioning of major facial features common to face pics generated by StyleGAN/thispersondoesnotexist)
• • •
Missing some Tweet in this thread? You can try to
force a refresh