It's a great day to look at a botnet with GAN-generated profile pics that links several websites with "authors" that use the same GAN-generated pics. #HolidayShenaniGANs
(GAN = generative adversarial network, the AI technique used by thispersondoesnotexist.com)
cc: @ZellaQuixote
(GAN = generative adversarial network, the AI technique used by thispersondoesnotexist.com)
cc: @ZellaQuixote
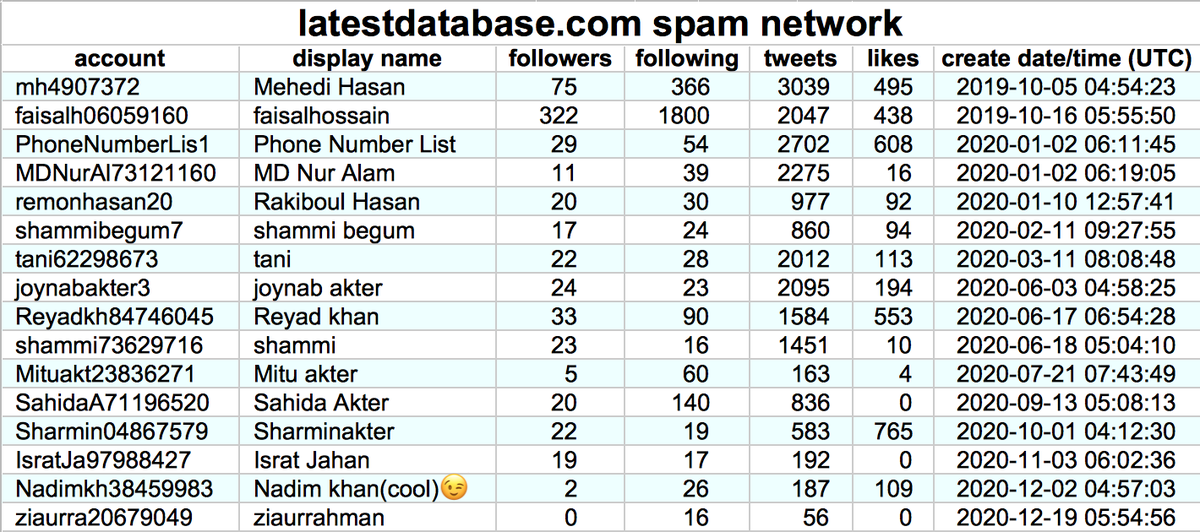
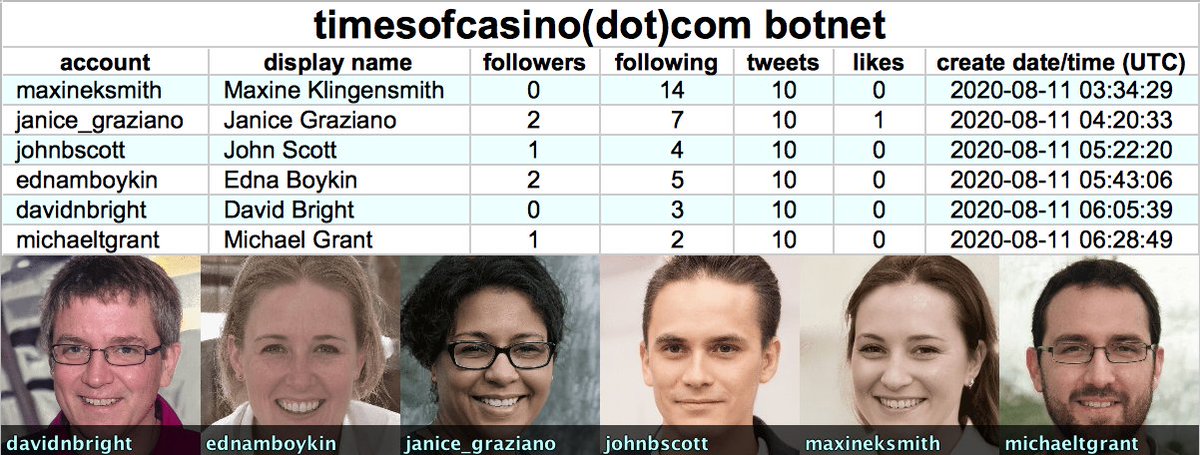
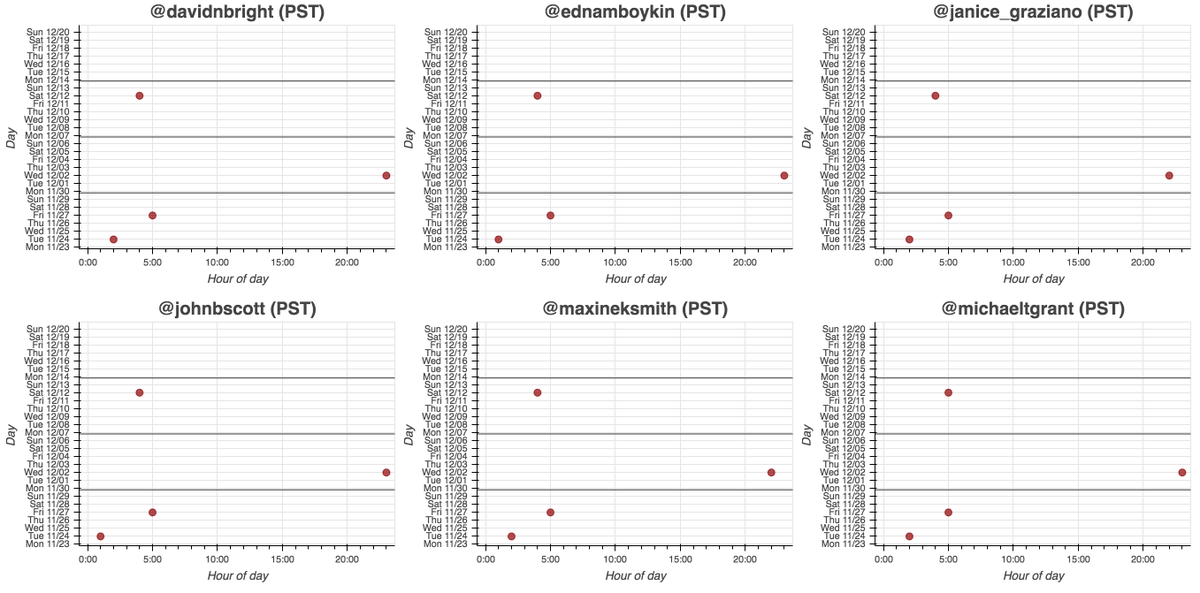
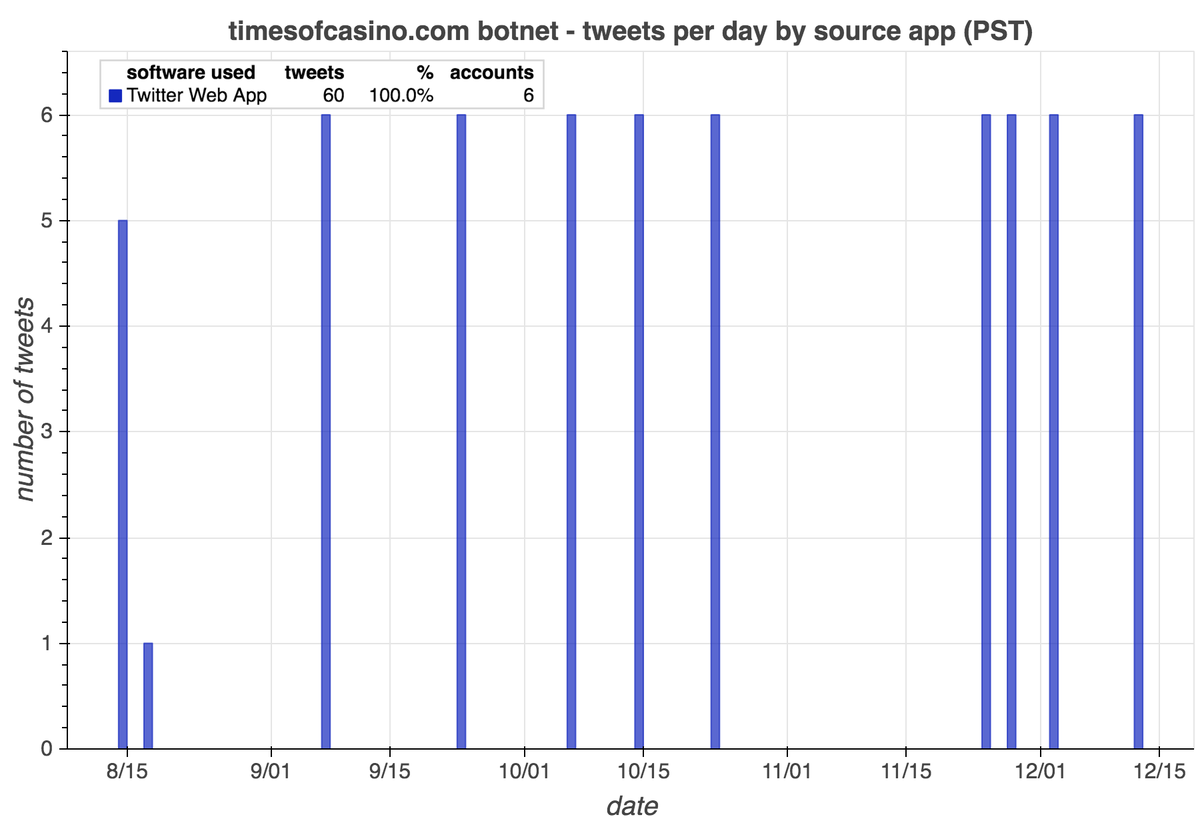
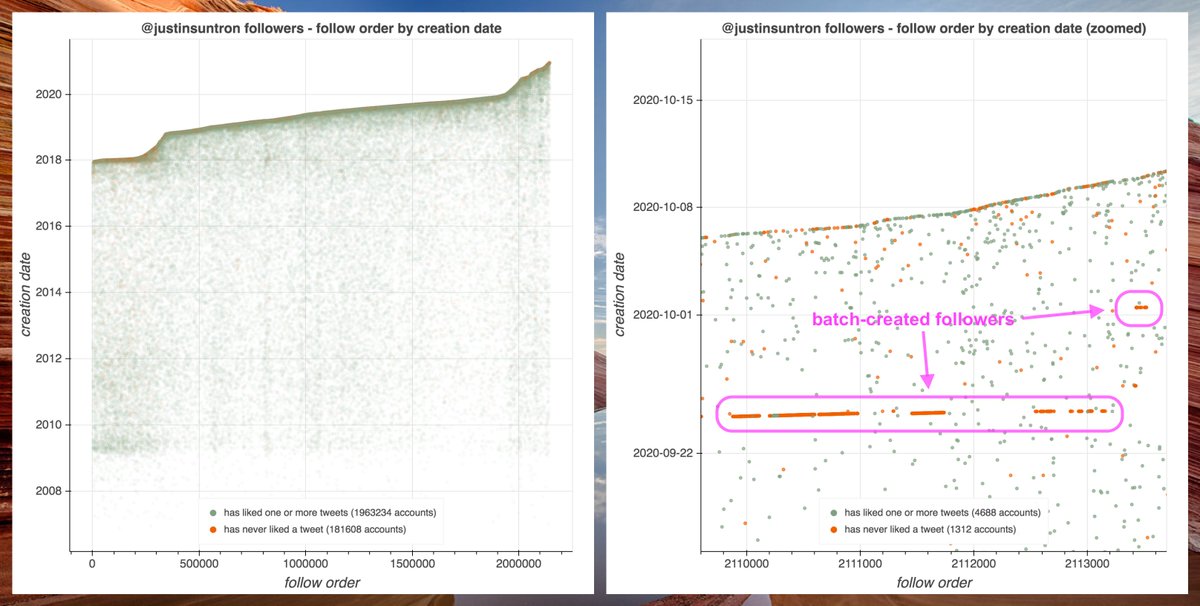
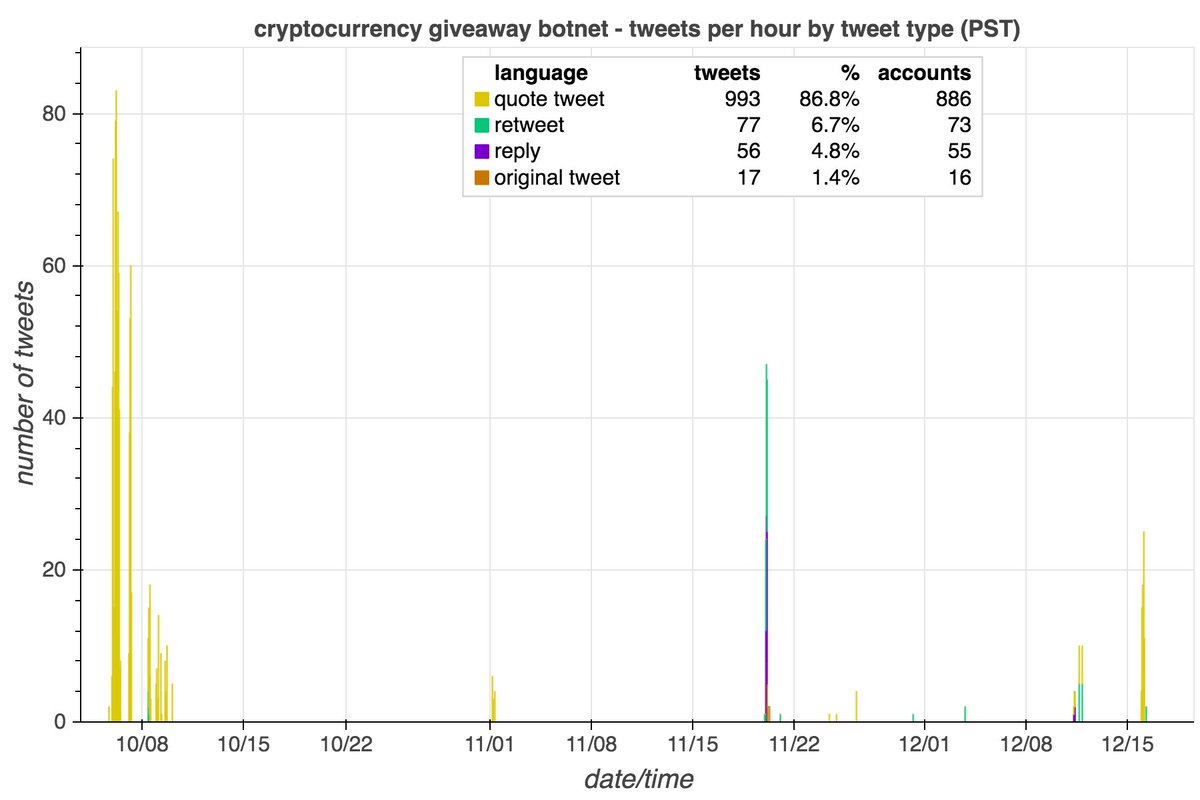
We found the first portion of this botnet a few days ago: six accounts that link timesofcasino(dot)com. As it turns out, the network is larger.
https://twitter.com/conspirator0/status/1340777590739615744
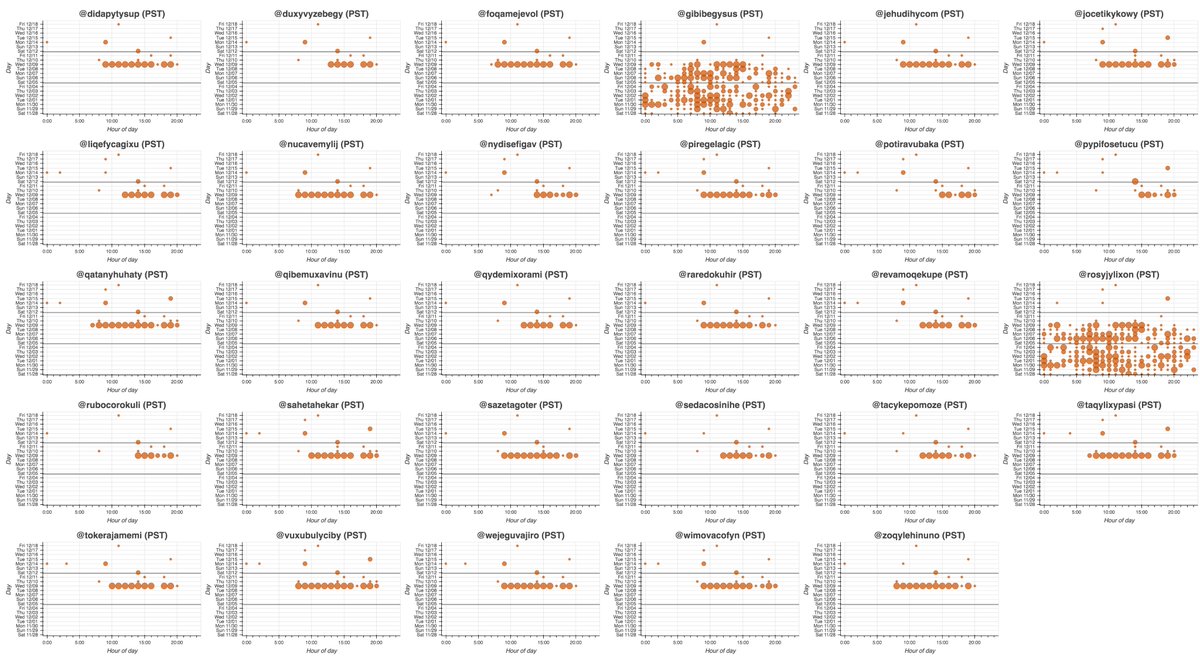
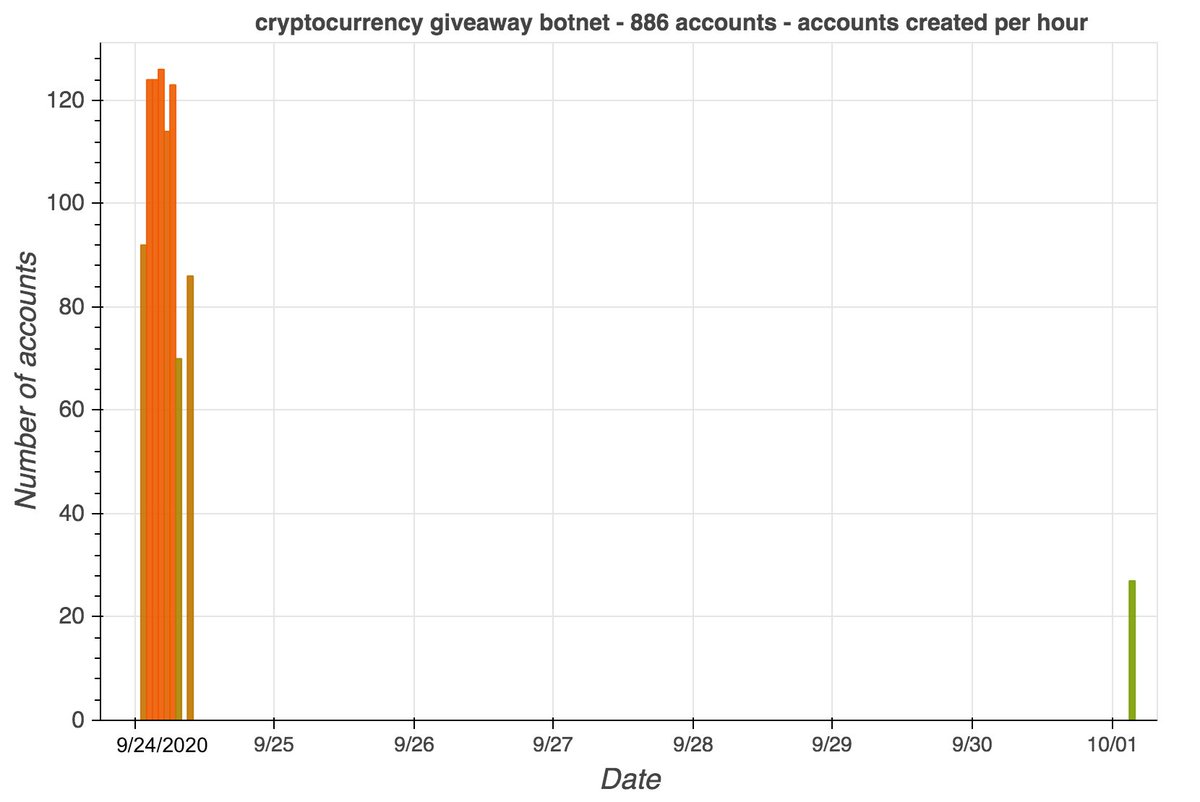
We found 60 accounts with GAN-generated pics made (mostly) in Aug 2020 that we think belong to the botnet:
• 42 accounts linking capitalbay(dot)news
• 6 accounts linking timesofcasino(dot)com
• 6 accounts linking coinnewsspan(dot)com
• 6 accounts linking namecoinnews(dot)com



• 42 accounts linking capitalbay(dot)news
• 6 accounts linking timesofcasino(dot)com
• 6 accounts linking coinnewsspan(dot)com
• 6 accounts linking namecoinnews(dot)com




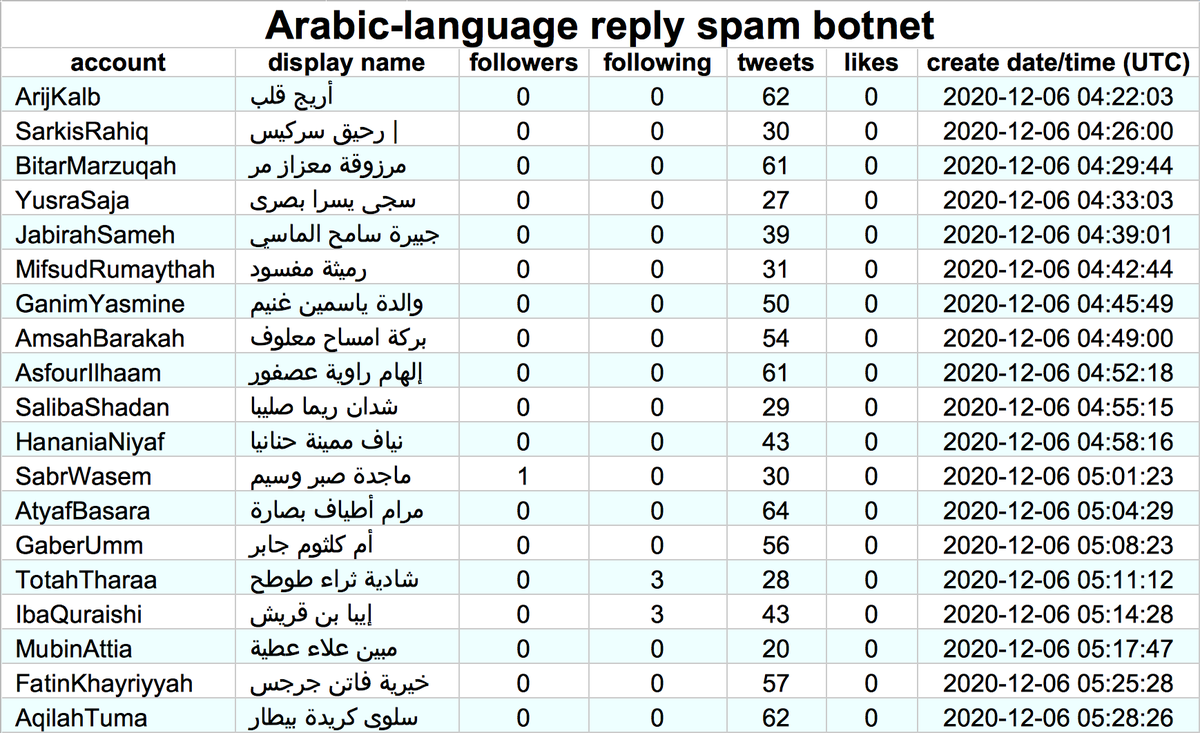
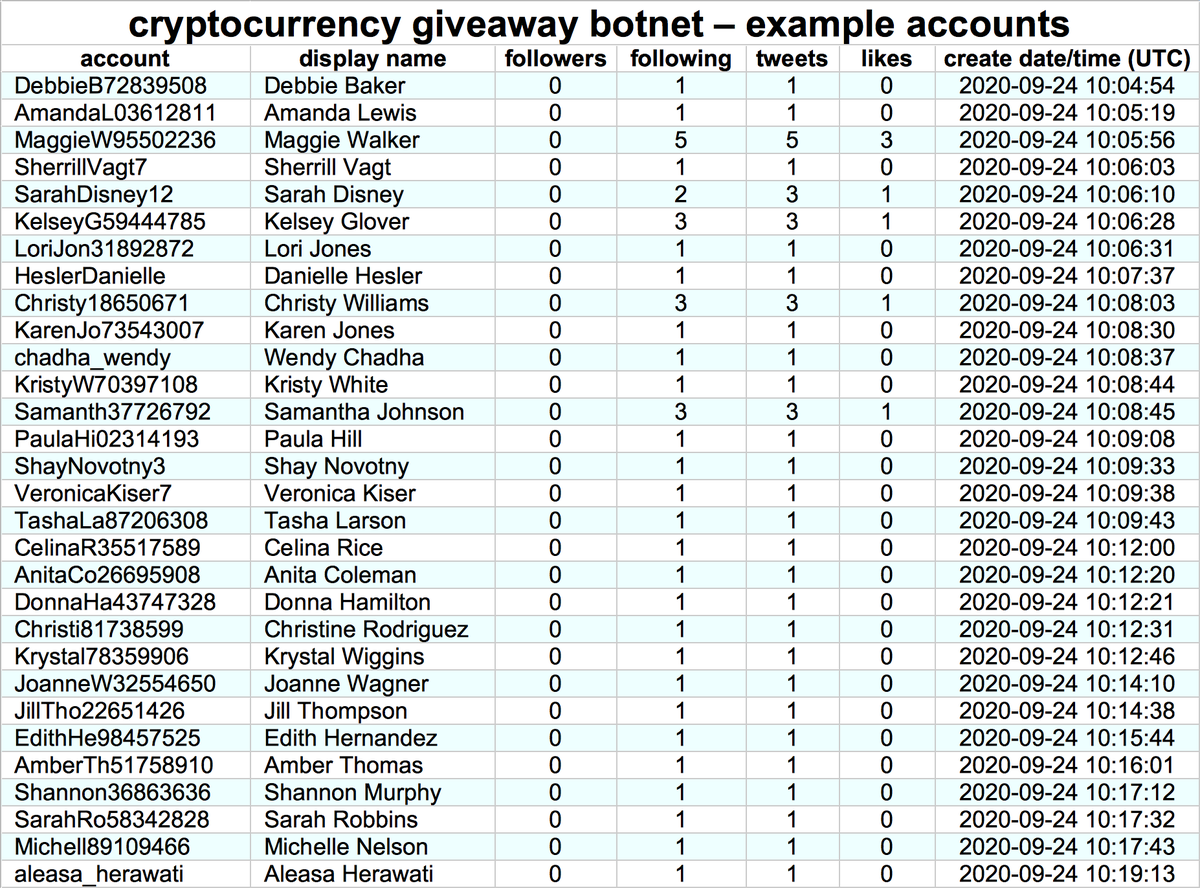
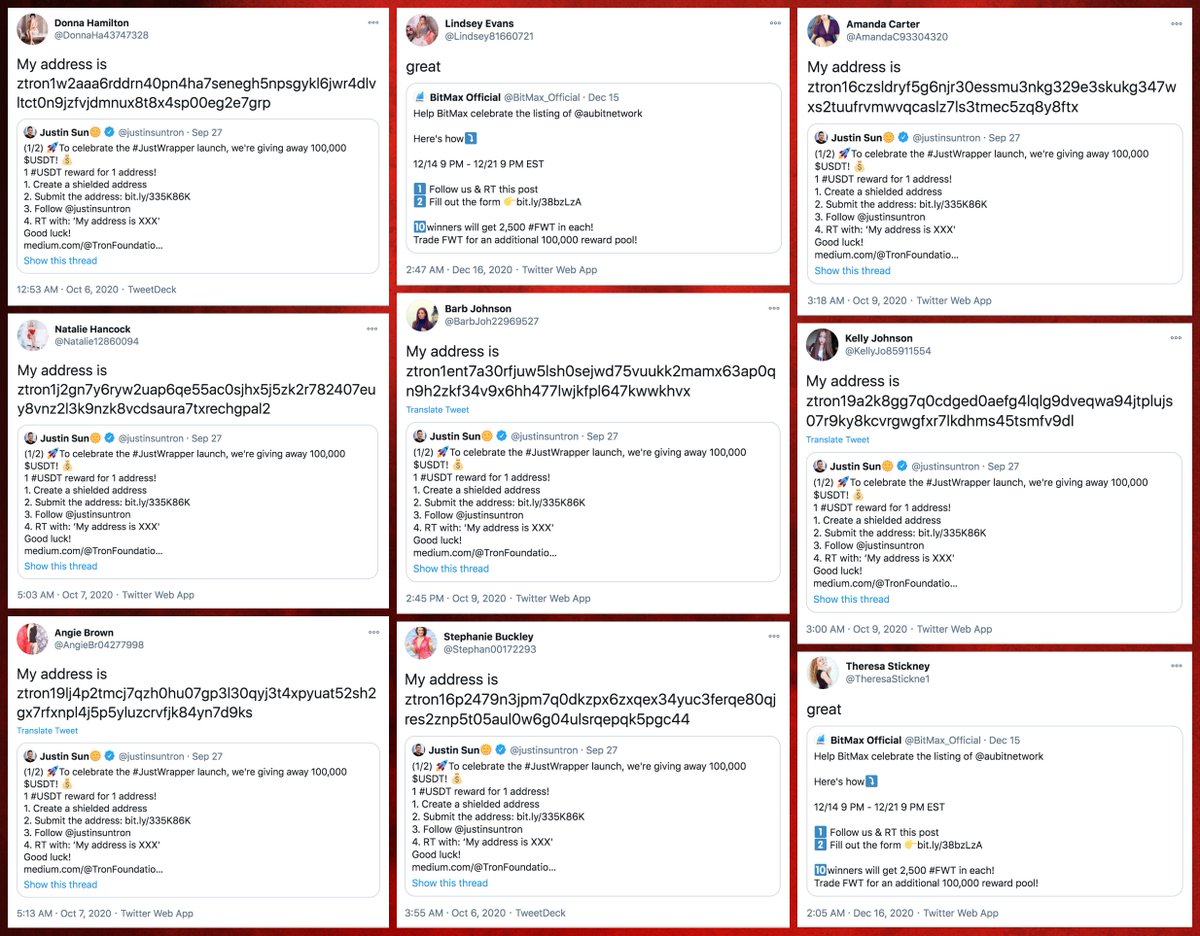
All four of the websites promoted by these 60 bots have "authors" with the same names as some of the bots linking them. The "photographs" of these "authors" are the same GAN-generated images that the bots use as their Twitter profile pics. 







Additionally, there are 5 accounts linking cryptonewsz(dot)com that we believe are also part of the botnet. These accounts are older, created in August and September 2019, but like the more recent creations, they have corresponding "authors" on the website they spam links to. 



Here are the profile pics of all 65 accounts in the botnet, as well as the result of blending their images together. As is the case with all unmodified StyleGAN face pics, the major facial features (especially eyes) are in the same place on all 65 images. 



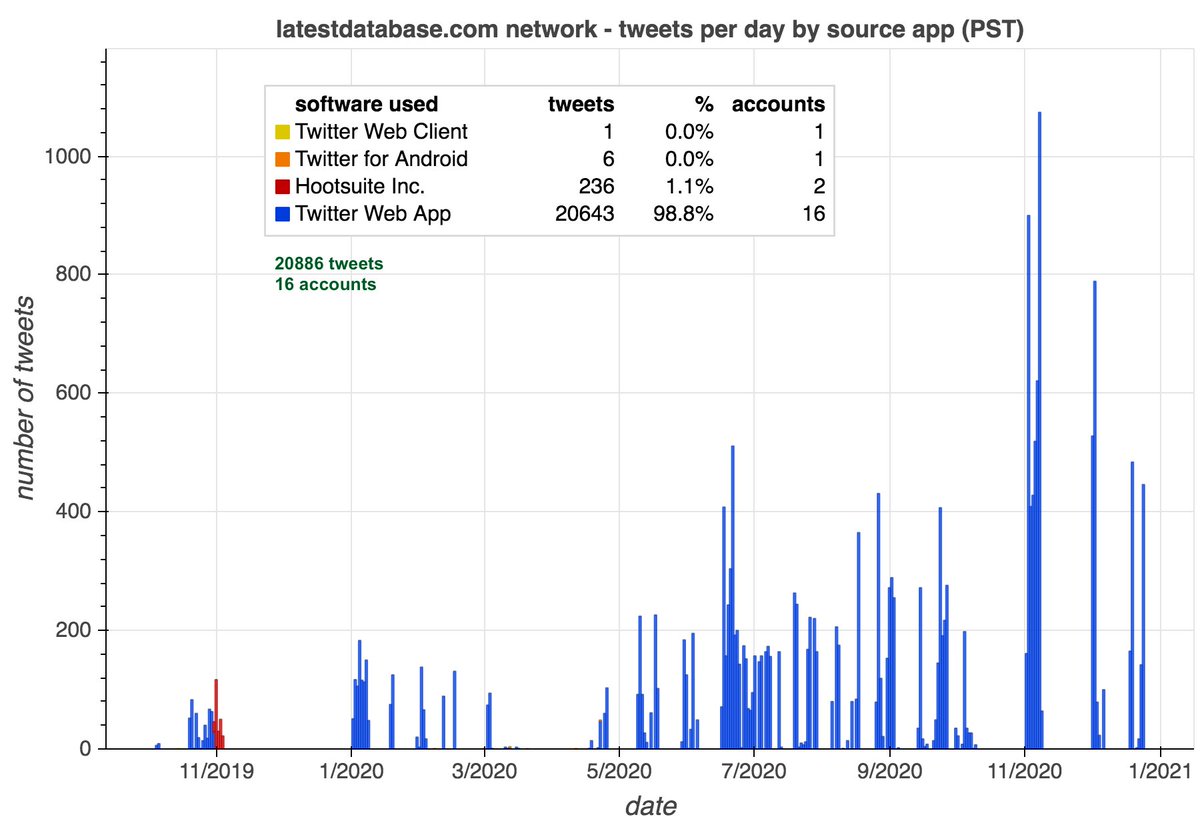
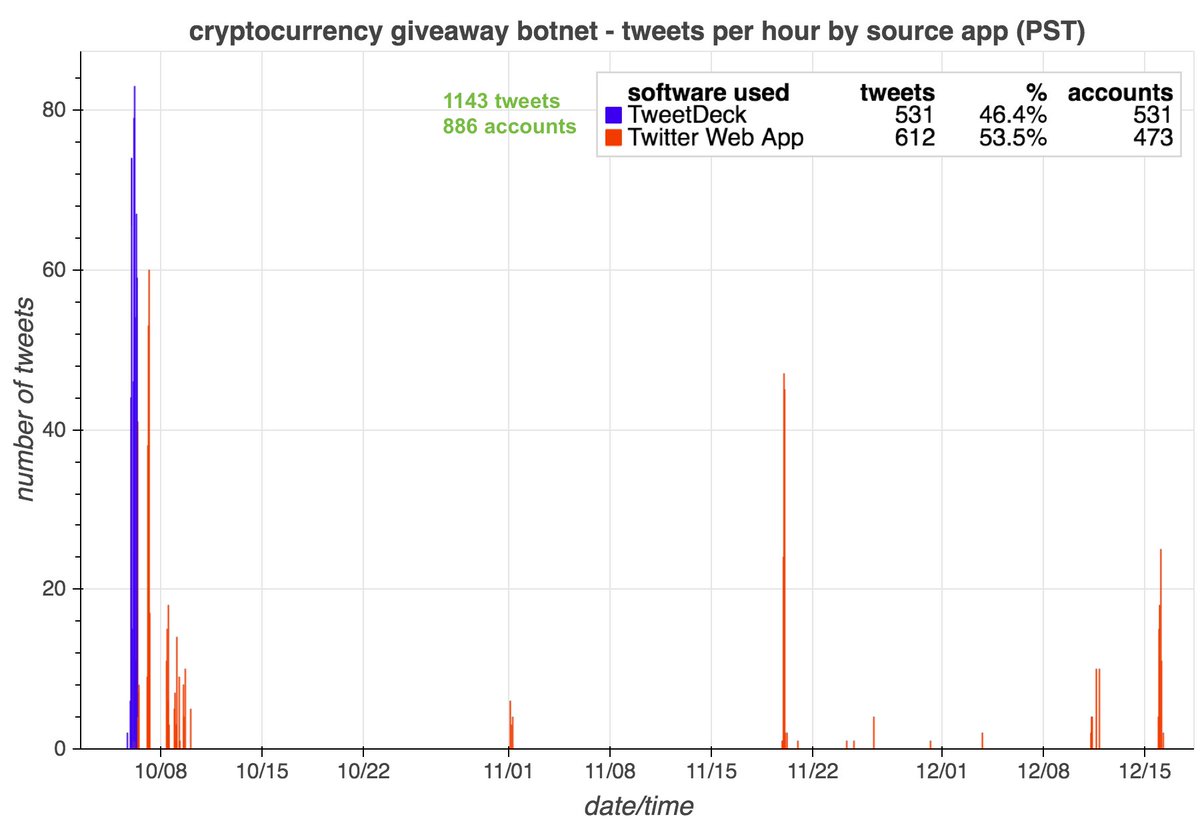
All 65 accounts in this network (allegedly) sent all of their recent tweets via the Twitter website, although we suspect they're automated anyway. The older members of the network (the 5 accounts that link cryptonewsz(dot)com) have also used dlvr(dot)it. 

What do these websites link? Mostly the five cryptocurrency and online gambling websites they promote (and are supposedly "authors" of), but there are occasional links to medium blogs and major cryptocurrency websites as well. 

H/T @EJGibney, who found portions of the network featured in this thread.
• • •
Missing some Tweet in this thread? You can try to
force a refresh