Five takedowns for CIB from the @Facebook investigative team last month.
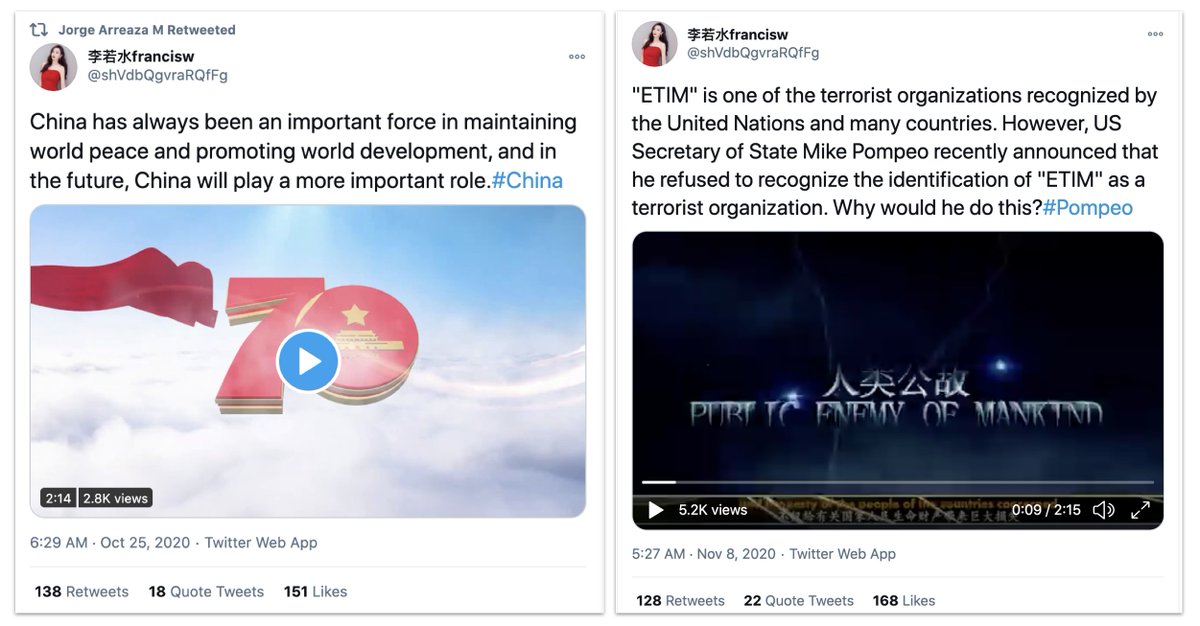
Thai military, domestic targeting
Iran, targeting Iraq, Israel, Afghanistan, UK
Iran, domestic + regional
Morocco, domestic focus
Russia, targeting the Navalny protests
Link: about.fb.com/news/2021/03/f…
Thai military, domestic targeting
Iran, targeting Iraq, Israel, Afghanistan, UK
Iran, domestic + regional
Morocco, domestic focus
Russia, targeting the Navalny protests
Link: about.fb.com/news/2021/03/f…
A range of behaviours here. Influence ops take many forms.
Fake a/cs posting to multiple pages to make content look popular
In-depth personas to seed geopolitical content
Large numbers of fakes to spam hashtags and geotags
GAN-generated faces, in bulk, but sloppily done.
Fake a/cs posting to multiple pages to make content look popular
In-depth personas to seed geopolitical content
Large numbers of fakes to spam hashtags and geotags
GAN-generated faces, in bulk, but sloppily done.
First, the Thai Military’s Internal Security Operations Command.
About 180 assets, esp. active in 2020, posting news, current events, pro-military and pro-monarchy content, anti-separatist.
Stock profile pics, some posing as young women.
Found by internal investigation.
About 180 assets, esp. active in 2020, posting news, current events, pro-military and pro-monarchy content, anti-separatist.
Stock profile pics, some posing as young women.
Found by internal investigation.

Iran (1): about 450 assets, mostly accounts, targeting Iraq, plus Israel, Afghanistan, the UK/Scotland.
Almost non-existent engagement, and - a nice touch - they took a day off on the anniversary of the Islamic Revolution in Iran in February 2021.
Almost non-existent engagement, and - a nice touch - they took a day off on the anniversary of the Islamic Revolution in Iran in February 2021.

Iran (2): <30 assets posing as geopolitical analysts and news outlets, mostly created late 2020.
Posted about domestic issues (pro-gov't), supporting Iran's foreign policy, criticizing US and Saudi foreign policy. As so often with Iranian IO.
Found by internal investigation.
Posted about domestic issues (pro-gov't), supporting Iran's foreign policy, criticizing US and Saudi foreign policy. As so often with Iranian IO.
Found by internal investigation.

Morocco: about 400 assets.
Amplifying content in groups, and posting comments and pro-government, anti-opposition content.
Initial lead from @amnesty.
Amplifying content in groups, and posting comments and pro-government, anti-opposition content.
Initial lead from @amnesty.

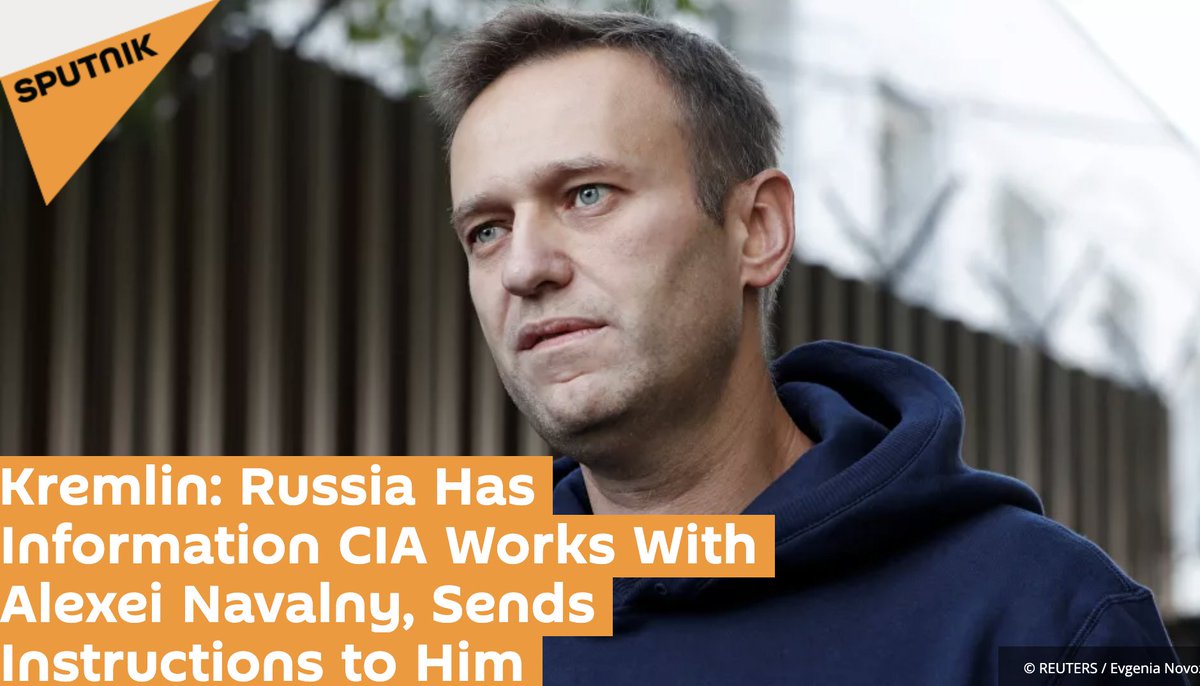
Finally, Russia. 500+ recent fake Instagram accounts targeting pro-Navalny protests.
Spammed protest hashtags & geotags w/ negative / irrelevant content. Detected and disabled soon after they started.
Hashtags incl Путинуходи, СвободуНавальному (Putin Leave, Free Navalny).
Spammed protest hashtags & geotags w/ negative / irrelevant content. Detected and disabled soon after they started.
Hashtags incl Путинуходи, СвободуНавальному (Putin Leave, Free Navalny).
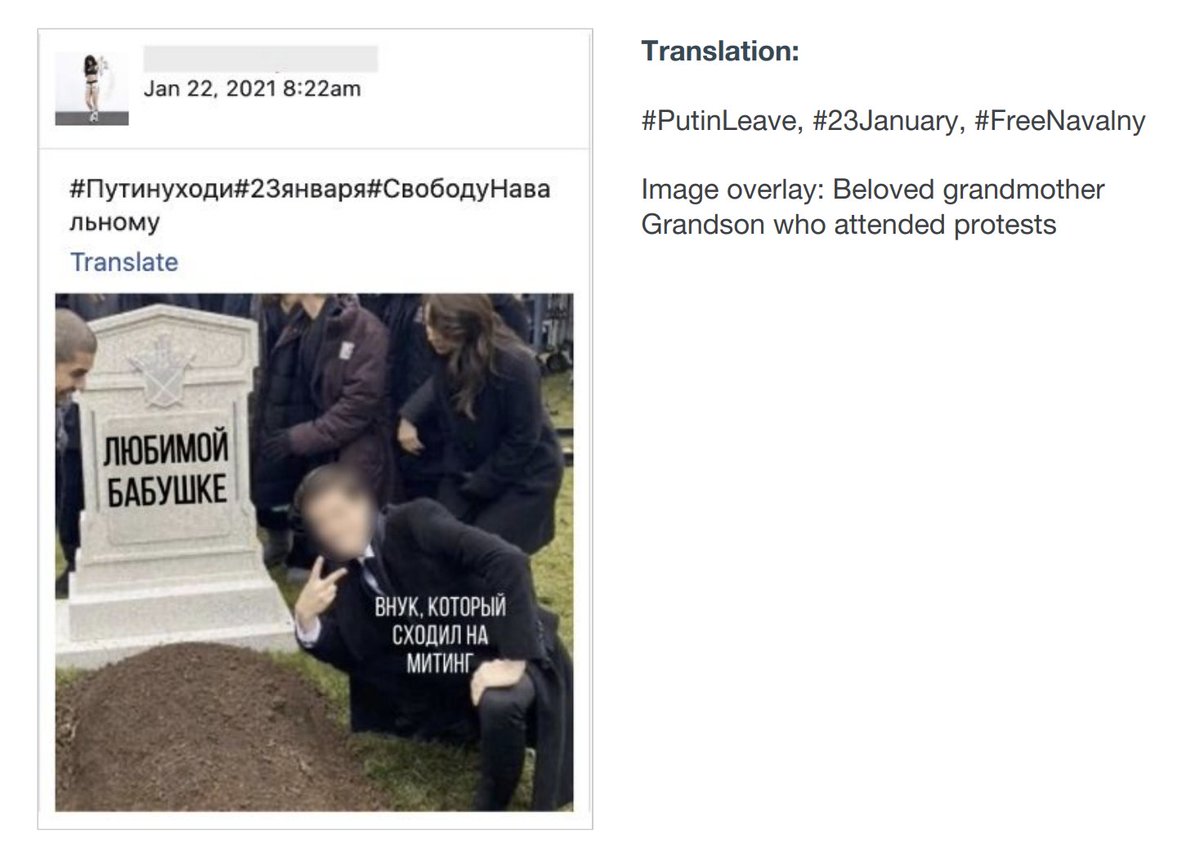
The accounts looked bulk-created and bought. Some also posted about fashion.
Some used sloppy AI-generated profile pics, which is a tactic that keeps cropping up in influence attempts. But it can make them easier to spot by eyeball, and doesn’t change behaviour signals.
Some used sloppy AI-generated profile pics, which is a tactic that keeps cropping up in influence attempts. But it can make them easier to spot by eyeball, and doesn’t change behaviour signals.

• • •
Missing some Tweet in this thread? You can try to
force a refresh