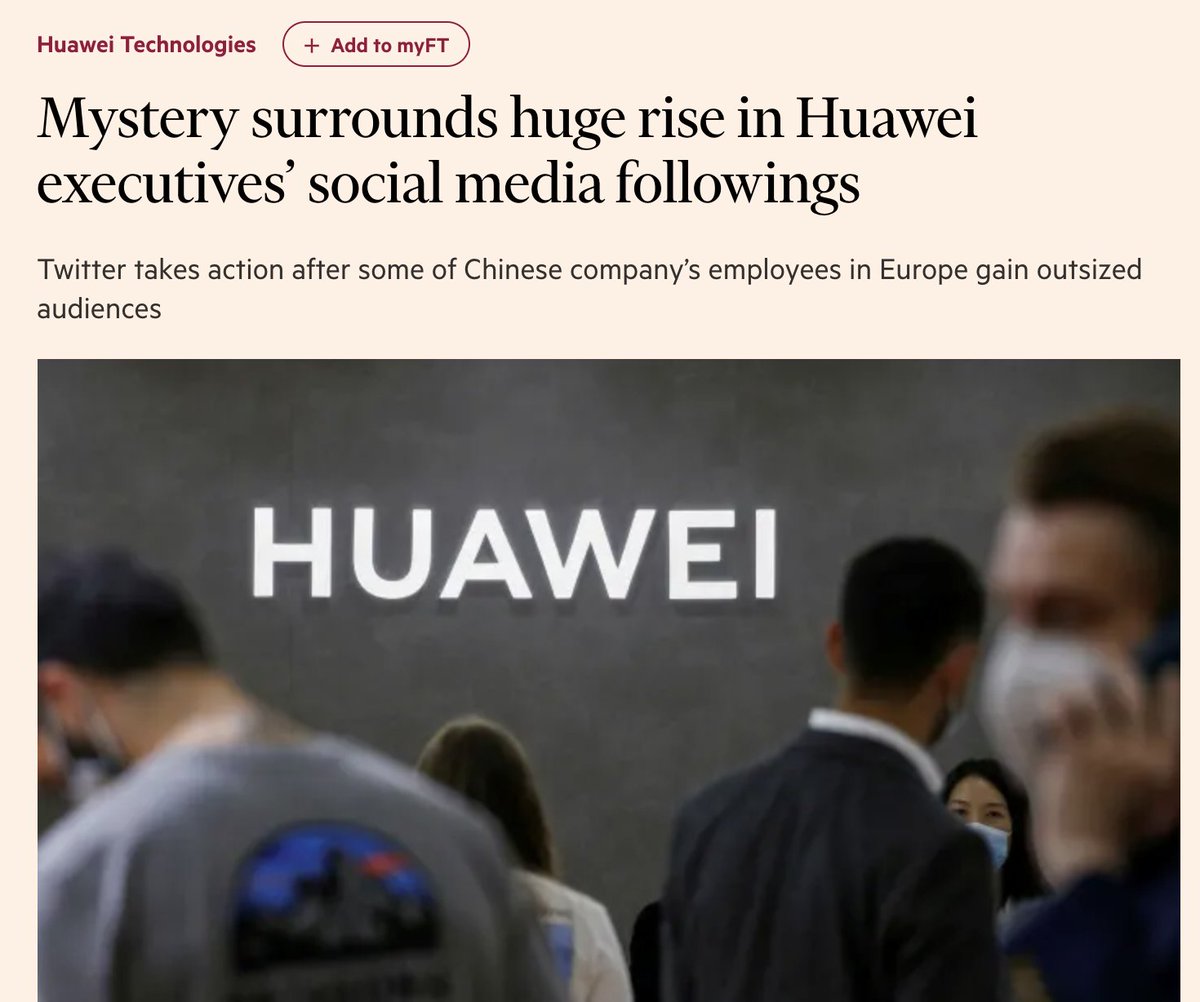
JUST OUT: Update on pro-China op Spamouflage Dragon.
Still spammy, but prolific and persistent, and getting some traction for the first time.
Over 1,400 videos in the last year.
Including geopolitical rivalry with the US.
@Graphika_NYC report: graphika.com/reports/spamou…
Still spammy, but prolific and persistent, and getting some traction for the first time.
Over 1,400 videos in the last year.
Including geopolitical rivalry with the US.
@Graphika_NYC report: graphika.com/reports/spamou…
Spamou works on YouTube, Twitter, Facebook.
Mainly videos in Mandarin, Cantonese, or Mandarin + English.
Low quality, high volume, on:
Guo Wengui (from 2018)
Hong Kong protests (2019)
Chinese achievements (Feb 2020)
US crises (early 2020)
US-China rivalry (mid-2020)
Mainly videos in Mandarin, Cantonese, or Mandarin + English.
Low quality, high volume, on:
Guo Wengui (from 2018)
Hong Kong protests (2019)
Chinese achievements (Feb 2020)
US crises (early 2020)
US-China rivalry (mid-2020)

We don’t have attribution on this op yet.
It’s persistent, well enough resourced to produce over 1,400 videos in a year, and closely tracks Chinese state messaging.
But who exactly is running it remains a question.
It’s persistent, well enough resourced to produce over 1,400 videos in a year, and closely tracks Chinese state messaging.
But who exactly is running it remains a question.
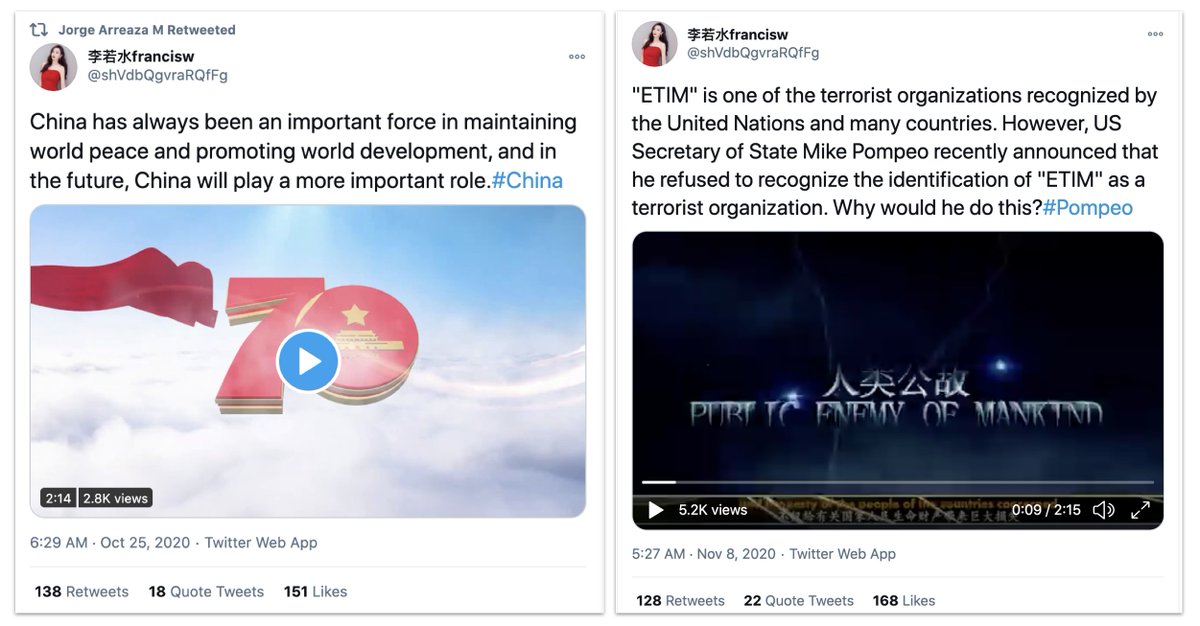
That said, a lot of the amplification it achieved (which was still modest) came from Chinese government accounts, including "wolf warriors" like @zlj517.
That's insufficient for attribution, but Spamouflage often promoted, and was promoted by, Chinese officials.
That's insufficient for attribution, but Spamouflage often promoted, and was promoted by, Chinese officials.

Spamou's prolific but profligate. The platforms have taken down tens of thousands of assets since we exposed it in 2019.
That’s kept its impact generally low, and forced it into a tactical shift, experimenting with fewer accounts with more persona.
blog.google/threat-analysi…
That’s kept its impact generally low, and forced it into a tactical shift, experimenting with fewer accounts with more persona.
blog.google/threat-analysi…
Recently, though, its most valuable asset has been division in America.
So much of its content points at events in the U.S. and says: “See? You don’t want to be like this.”
It doesn’t need to make bad stories up, just cherry-pick the worst ones.
So much of its content points at events in the U.S. and says: “See? You don’t want to be like this.”
It doesn’t need to make bad stories up, just cherry-pick the worst ones.

As @craigtimberg pointed out, that also tracks with Chinese government messaging, e.g. over the Capitol riot.
washingtonpost.com/technology/202…
washingtonpost.com/technology/202…
Don’t make the mistake of thinking this is the “Russian playbook”.
Spamou doesn’t pretend to be American, and we’ve seen no attempt to polarise US audiences.
Main audiences so far: Hong Kong, Taiwan, Venezuela, Pakistan.
Main message: China’s rising, America's fallen.
Spamou doesn’t pretend to be American, and we’ve seen no attempt to polarise US audiences.
Main audiences so far: Hong Kong, Taiwan, Venezuela, Pakistan.
Main message: China’s rising, America's fallen.

This looks like geopolitical competition for the 21st century: point to all the bad things you can find about your rival, in places where the rivalry’s acute or there’s a chance to make inroads. 

Spamou has always been low quality, low impact.
The quality hasn't improved. These images were used to illustrate a video on COVID problems in the U.S.
Comunidad de Madrid?
The quality hasn't improved. These images were used to illustrate a video on COVID problems in the U.S.
Comunidad de Madrid?

You might fairly ask why it's worth studying an operation that never seems to break out of its bubble.
Answer: because there's always the danger that they might one day get something *right*, and then it'll be important to identify and expose quickly.
Answer: because there's always the danger that they might one day get something *right*, and then it'll be important to identify and expose quickly.
Case in point: Russian operation Secondary Infektion. Nearly six years with no breakout worthy of the name. Then it interfered in the UK 2019 election.
But we, and the great @jc_stubbs, caught it before the vote, because we already knew how SI works.
reuters.com/article/britai…
But we, and the great @jc_stubbs, caught it before the vote, because we already knew how SI works.
reuters.com/article/britai…
And Spamouflage has finally started getting some breakout in some areas. Limited and sporadic, but more than it's ever had before.
Here's the Venezuelan foreign minister retweeting a Spamouflage fake account.
(No indication he knew this was a fake.)
Here's the Venezuelan foreign minister retweeting a Spamouflage fake account.
(No indication he knew this was a fake.)

This was one of a handful of persona accounts that Spamouflage began running in mid-2020.
Stock profile picture of a young lady, tweeting about geopolitical issues. Quite a few different accounts followed that pattern.
Stock profile picture of a young lady, tweeting about geopolitical issues. Quite a few different accounts followed that pattern.

This account, screen name "李若水francisw ", had a significant following from Chinese official accounts.
I would love to know how exactly they found "her".
I would love to know how exactly they found "her".

It's been through seven iterations so far. The earlier ones lasted up to two months each. Recent ones, just days.
Each time it re-spawned, it reached out to potential amplifiers, trying to get their attention.
Each time it re-spawned, it reached out to potential amplifiers, trying to get their attention.

Same with this persona. Again, apparently a young lady posting about geopolitics. The call for follows is overt here. 

This persona stole its "personal" pics from a Weibo user.
Note how the Twitter image is cropped to remove the Weibo handle.
Note how the Twitter image is cropped to remove the Weibo handle.

On YouTube, there were also persona channels amplifying Spamouflage videos - and often then deleting them a week or so later.
Unclear whether the people whose identities they claimed were actually involved in the amplification, or whether this was Spamou borrowing their names.
Unclear whether the people whose identities they claimed were actually involved in the amplification, or whether this was Spamou borrowing their names.

These channels have thousands of followers, and primarily focus on Hong Kong and Taiwan. Some of their videos get views in the hundreds or low thousands.
Still not massive, but more than Spamouflage has ever achieved before.
Note the messaging on US "democracy export".
Still not massive, but more than Spamouflage has ever achieved before.
Note the messaging on US "democracy export".

Breakouts like these were a small minority of the total output, though. The great bulk of Spamouflage posts failed to get any attention at all.
The fakeness of their accounts is one likely explanation. The clunky execution is another.
Someone broke the space bar?
The fakeness of their accounts is one likely explanation. The clunky execution is another.
Someone broke the space bar?

In fact, there's an incompetence to this operation that's sometimes almost endearing.
Voice-overs that pronounce "U.S." as "us". Mediaeval headlines ("Chinese sword!")...
Voice-overs that pronounce "U.S." as "us". Mediaeval headlines ("Chinese sword!")...

But there's a nasty edge to its content too. Finding the very worst moments of American news, and trying to portray them as typical. 

The good thing is, this operation has come under sustained pressure. Tens of thousands of fake assets taken down. Repeated exposures by the team at @Graphika_NYC, and by @FireEye.
That helps curb the spread, because it makes it harder to build any audience or momentum.
That helps curb the spread, because it makes it harder to build any audience or momentum.
But this is a persistent threat actor, apparently well resourced, capable of some adaptation.
Don't overstate its reach, but don't assume that historical incompetence automatically means future ineffectiveness - especially with Chinese state amplification.
Don't overstate its reach, but don't assume that historical incompetence automatically means future ineffectiveness - especially with Chinese state amplification.

The best way to stop operations like this achieving their goals is to keep the pressure on, keep exposing and disrupting them, and catch any tactical shifts early on.
Keep calm. But keep watch.
graphika.com/reports/spamou…
Keep calm. But keep watch.
graphika.com/reports/spamou…
• • •
Missing some Tweet in this thread? You can try to
force a refresh