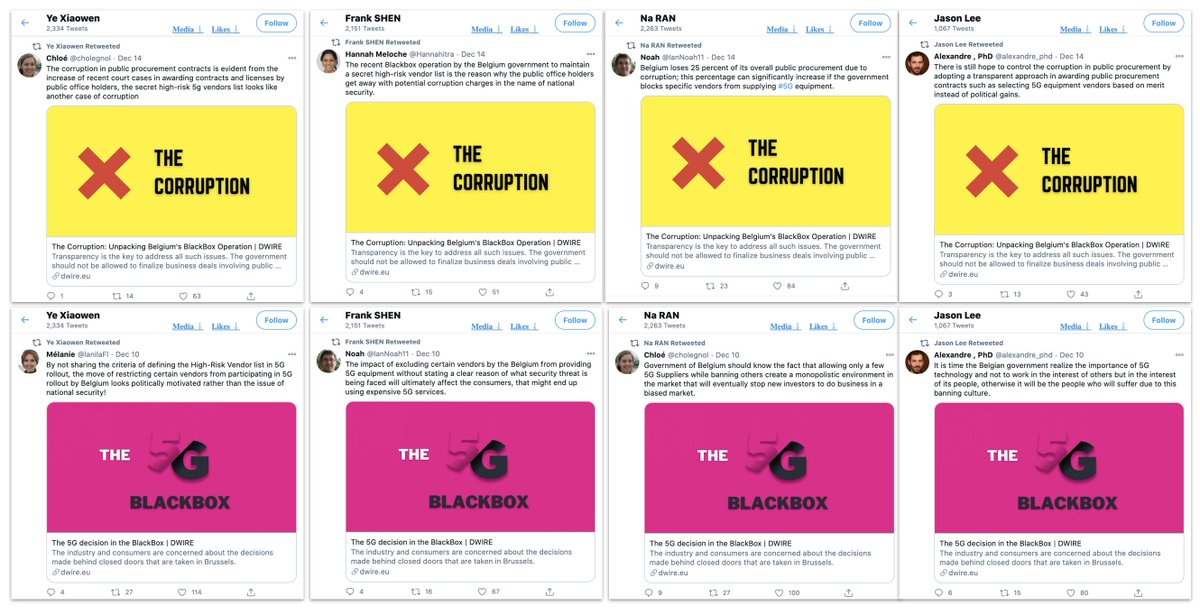
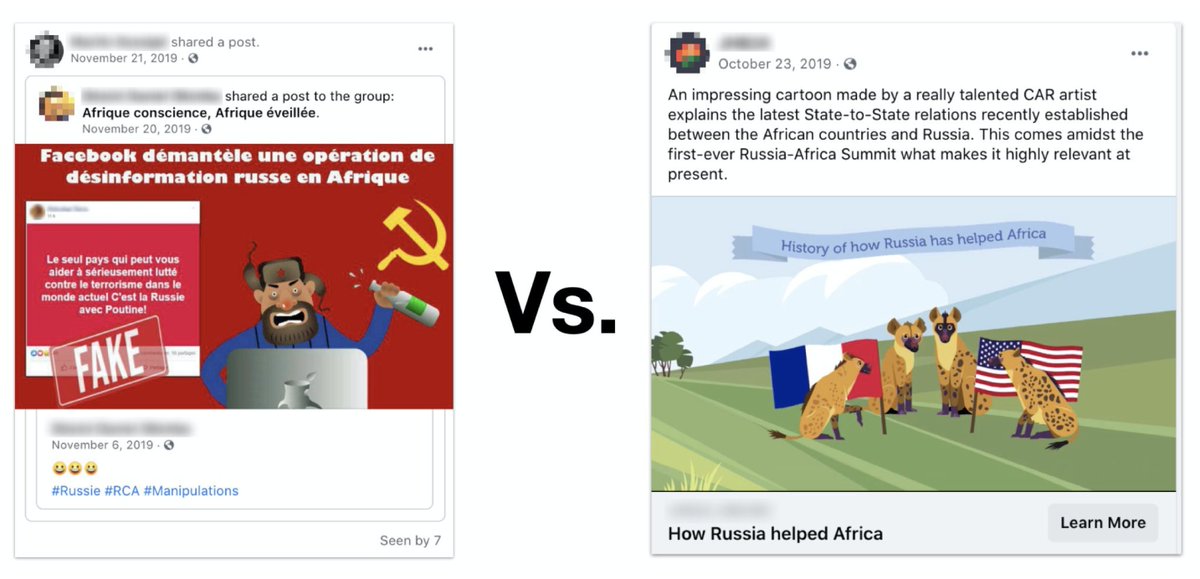
Great report by @satariano on a fake network that @Graphika_NYC (and others) found in December.
Twitter accounts with GAN faces, boosting Huawei, boosted by Huawei execs, and attacking Belgium's 5G policies.
Not enough evidence to prove who ran them.
nytimes.com/2021/01/29/tec…
Twitter accounts with GAN faces, boosting Huawei, boosted by Huawei execs, and attacking Belgium's 5G policies.
Not enough evidence to prove who ran them.
nytimes.com/2021/01/29/tec…
We found this network when it was boosted by Spamouflage, a pro-China operation.
Independently, @mvanhulten of @TI_EU and @ArbiterOfTweets of @Knack found it with different methods.
It's not a friendly environment for fake campaigns, folks.
graphika.com/reports/fake-c…
Independently, @mvanhulten of @TI_EU and @ArbiterOfTweets of @Knack found it with different methods.
It's not a friendly environment for fake campaigns, folks.
graphika.com/reports/fake-c…
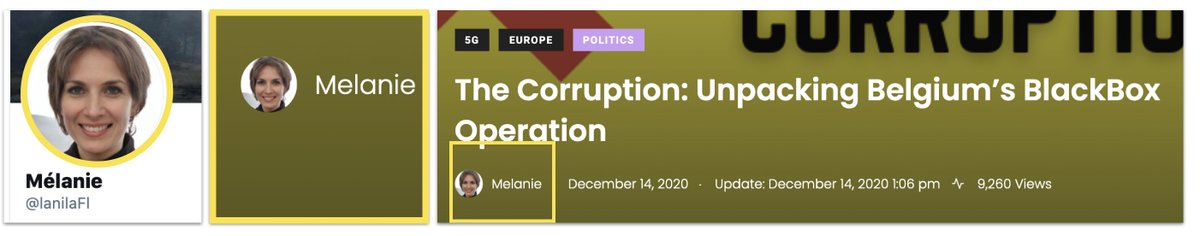
This was the first account we found.
"Alexandre, PhD", apparently a CEO.
But no surname, no indication of what he's a CEO of, and a GAN-generated profile pic.
"Alexandre, PhD", apparently a CEO.
But no surname, no indication of what he's a CEO of, and a GAN-generated profile pic.
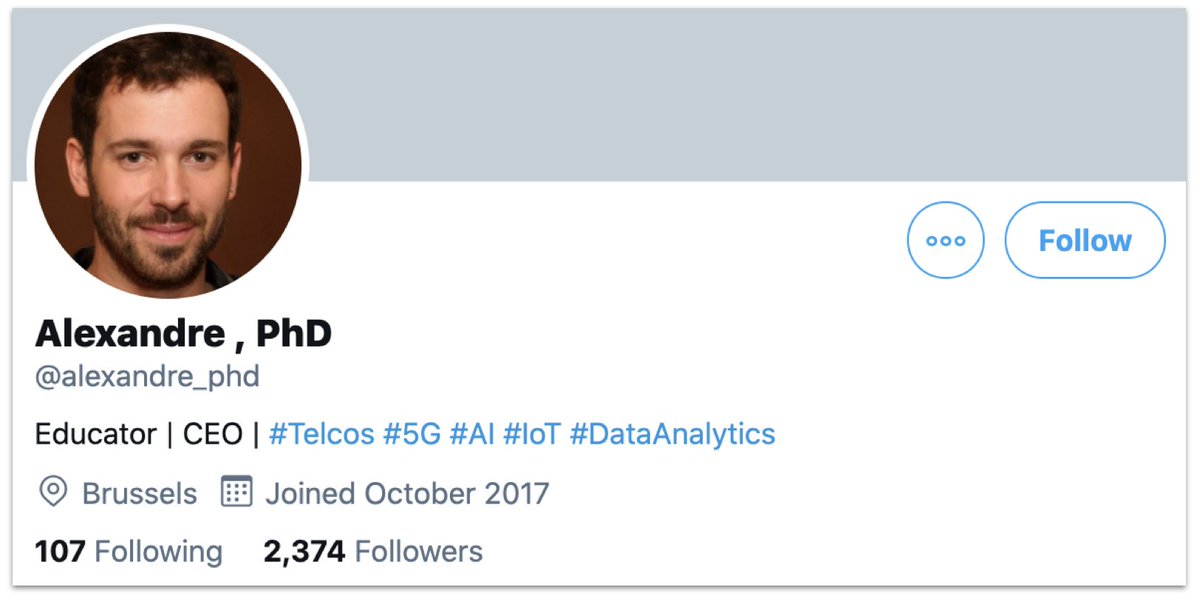
Alexandre's had a bit of an obsession with Belgium and #5G recently.
Especially, Belgium's security limitations on 5G providers, which are reportedly mainly about Huawei and ZTE.
Alexandre didn't like the Belgian approach much.
Especially, Belgium's security limitations on 5G providers, which are reportedly mainly about Huawei and ZTE.
Alexandre didn't like the Belgian approach much.
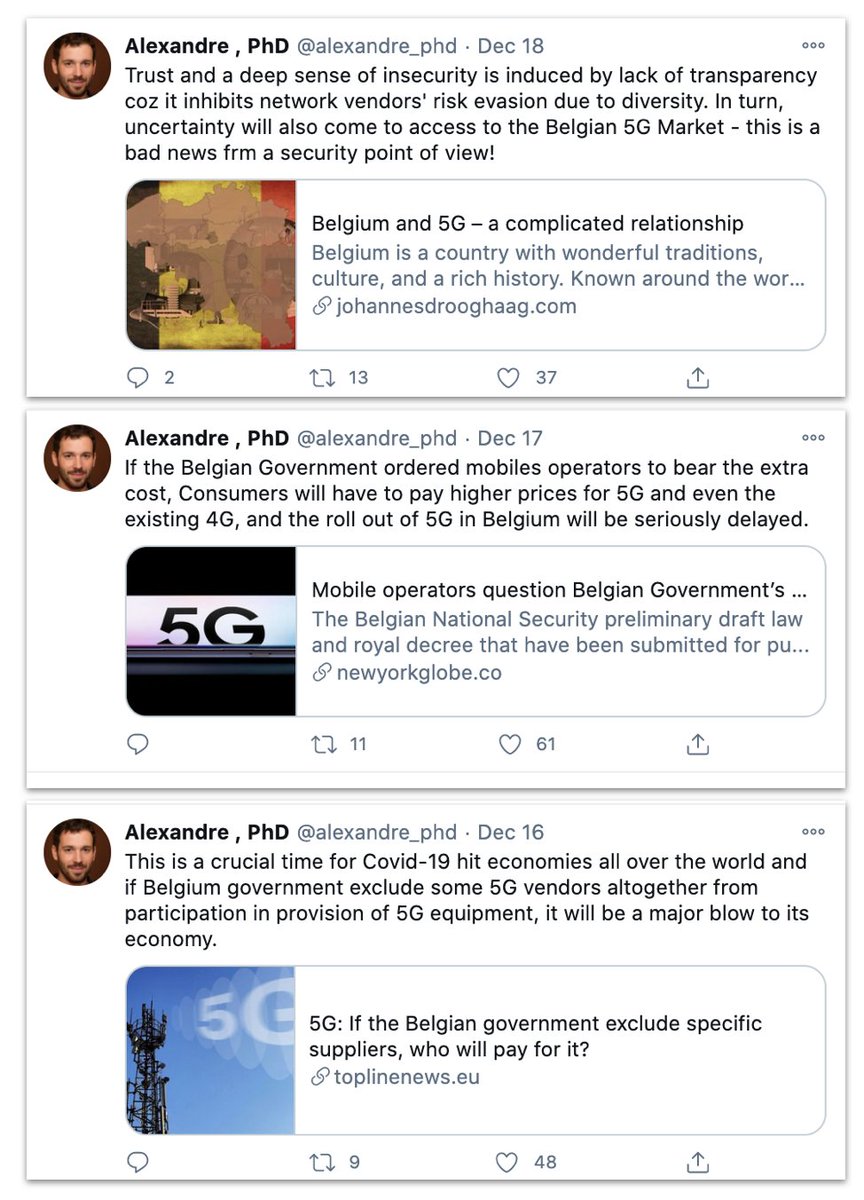
The account was created in 2017. It only started tweeting in early December, 2020, but its first posts were retweets of tweets from November 2017-18.
They were meant to be about VR, as in virtual reality. Oddly, one was actually about Victorian Railways in Australia. Awkward.
They were meant to be about VR, as in virtual reality. Oddly, one was actually about Victorian Railways in Australia. Awkward.
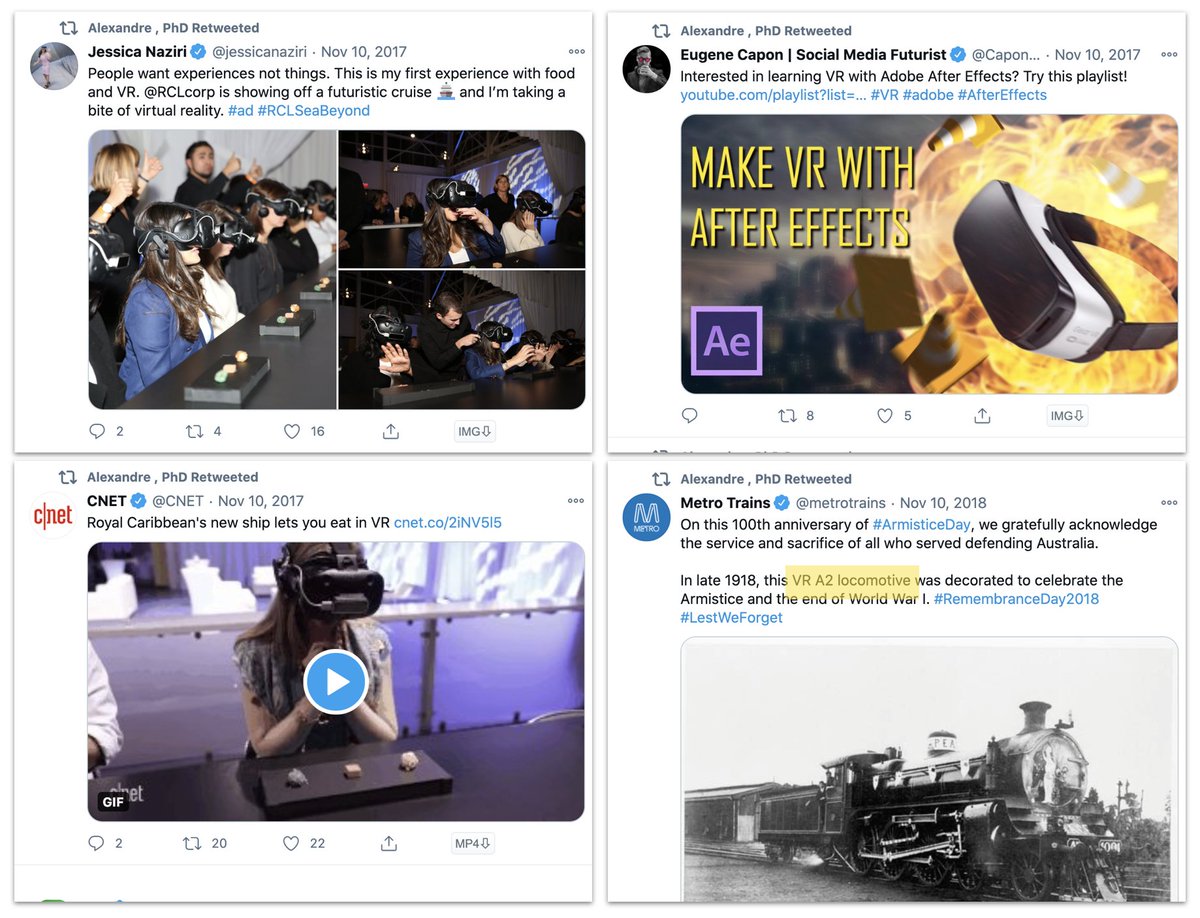
Pivoting off that account, we found 13 more that were behaving the same way, created around the same time, and all had GAN faces and similar bios - including a "best-selling author" who, um, didn't name any of his actual books. 
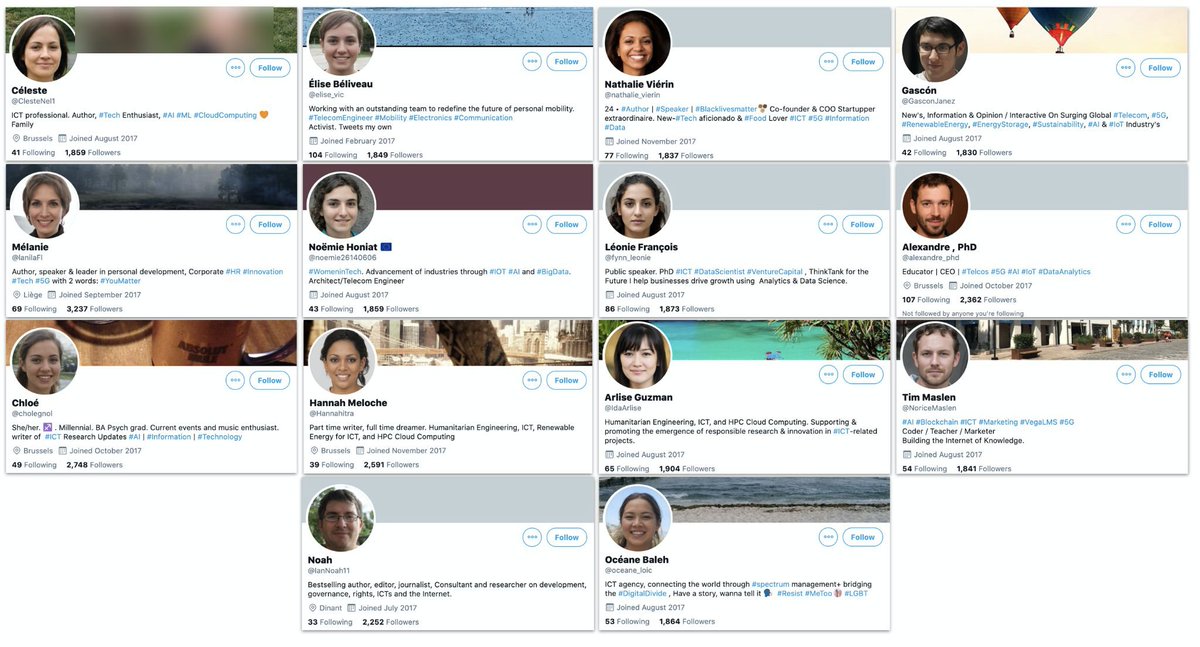
Handy rule-of-thumb way to check for obvious GAN faces on multiple accounts: reduce them all to 35% opacity and superimpose them.
Not infallible, and the GAN will get better fast, but... see how the eyeballs align?
Not infallible, and the GAN will get better fast, but... see how the eyeballs align?

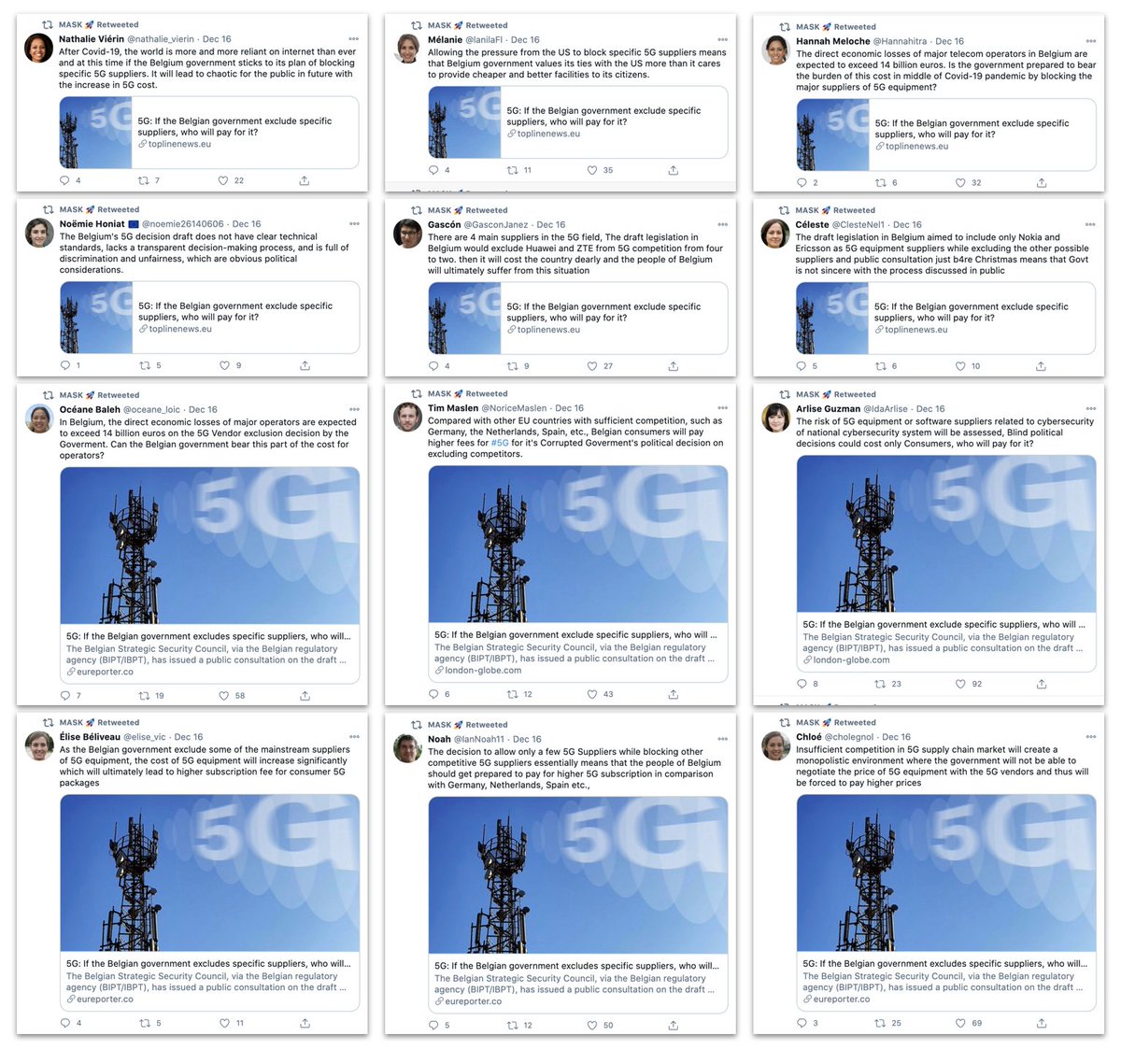
They all retweeted posts on #5G and #telcos. Character building.
Each posted 8-10 authored tweets, each a share of a web article plus a comment (usually in English), about #Belgium, #5G, #Huawei or #ZTE.
Each posted 8-10 authored tweets, each a share of a web article plus a comment (usually in English), about #Belgium, #5G, #Huawei or #ZTE.

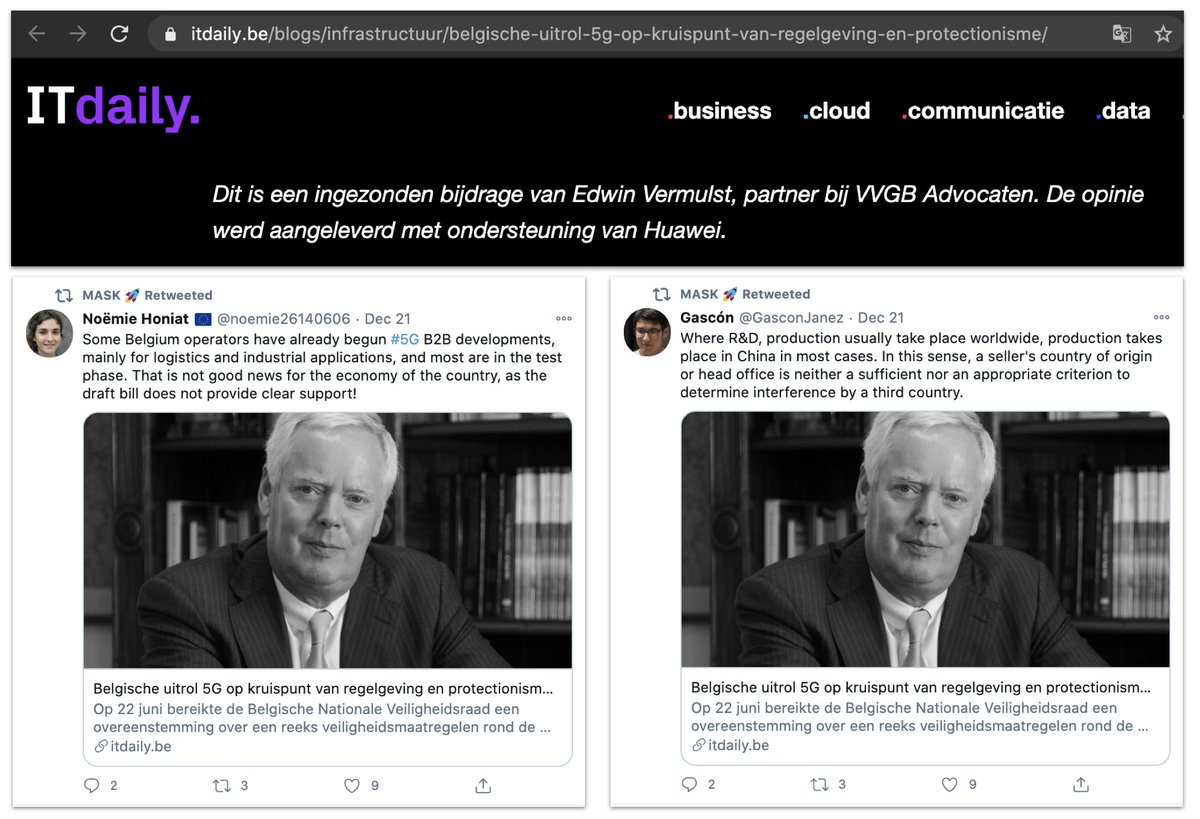
A couple of the articles were sponsored by Huawei, and labelled as such.
@satariano has some great insights into this one.
@satariano has some great insights into this one.
Looks like @ArbiterOfTweets has something interesting coming out soon, too.
"New and relatively explosive."
Watch this space.
"New and relatively explosive."
Watch this space.
https://twitter.com/ArbiterOfTweets/status/1355103350522601473
Other articles appeared independent and ran on multiple (but connected) websites.
When that happened, different fake accounts tweeted the same article from different sources - an attempt to make it harder to spot them all with a URL search?
12 assets, one article, 3 URLs.
When that happened, different fake accounts tweeted the same article from different sources - an attempt to make it harder to spot them all with a URL search?
12 assets, one article, 3 URLs.
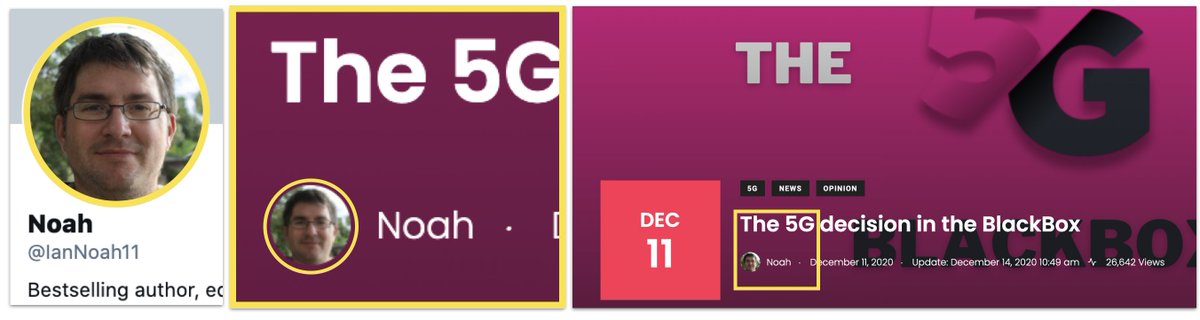
The two most aggressively anti-Belgium articles were different, though.
They were attributed to the fake personas themselves.
Looks like the operation was going for the direct approach.

They were attributed to the fake personas themselves.
Looks like the operation was going for the direct approach.
We don't have enough evidence to prove who was running the campaign. But its most important amplification (in terms of follower numbers and frequency of amplification) came from Huawei staff, including the Huawei Europe verified Twitter account. 
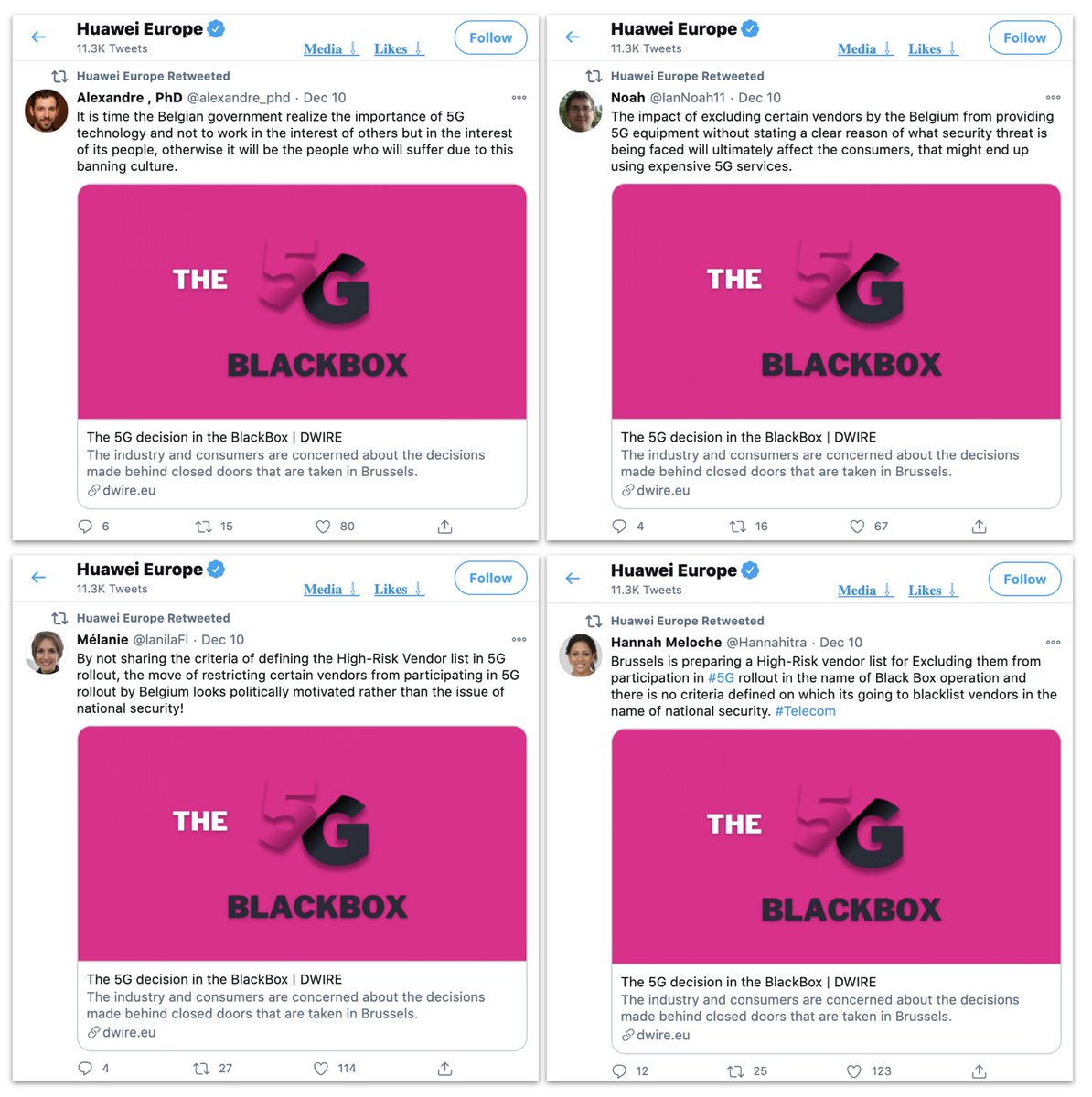
For example, here's Huawei Europe retweeting four fake accounts that tweeted the article on Belgium being corrupt.
As far as we can tell, the article was planted on a website by one of the fake accounts.
As far as we can tell, the article was planted on a website by one of the fake accounts.

Here are Twitter accounts attributed to Huawei Europe figures, including two verified ones, retweeting the fake accounts, which were tweeting the operation's articles. 

Searching for all mentions of all 14 fake accounts over the past year, and sorting the mentioners by following using @Meltwater, these are the top amplifiers.
Note the number of times each one mentioned one of the fake accounts (red box).
Note the number of times each one mentioned one of the fake accounts (red box).

A couple of things stand out about this campaign.
One was the theme. This looked like an exercise in dark lobbying: try and raise the heat on the Belgian government on an issue that's of interest to a corporate titan.
Business, not party politics.
One was the theme. This looked like an exercise in dark lobbying: try and raise the heat on the Belgian government on an issue that's of interest to a corporate titan.
Business, not party politics.

That's not unexpected, but it's important.
Most of the influence ops we've tracked so far have been in the political or geopolitical space.
Dark lobbying like this will be something to watch for more.
Most of the influence ops we've tracked so far have been in the political or geopolitical space.
Dark lobbying like this will be something to watch for more.
Second thing, though, is how many people identified this.
We found it via Spamouflage. @mvanhulten and @ArbiterOfTweets spotted sponsored posts that led there.
There's a growing community of people who can spot this stuff, explain it and expose it.
We found it via Spamouflage. @mvanhulten and @ArbiterOfTweets spotted sponsored posts that led there.
There's a growing community of people who can spot this stuff, explain it and expose it.
That's important too.
Running influence ops may seem like an attractive option, but they're going to have to be a lot less dumb than this one was to avoid getting exposed.
Running influence ops may seem like an attractive option, but they're going to have to be a lot less dumb than this one was to avoid getting exposed.
These fake Twitter accounts never had much impact while active.
But their exposure landed them in @nytimes and @knack, and not in a good way.
Was the operation worth the blowback? Let's keep watching to find out.
nytimes.com/2021/01/29/tec…
But their exposure landed them in @nytimes and @knack, and not in a good way.
Was the operation worth the blowback? Let's keep watching to find out.
nytimes.com/2021/01/29/tec…
• • •
Missing some Tweet in this thread? You can try to
force a refresh