And this, just out from @MsHannahMurphy and @SVR13: questions about the hundreds of thousands of followers that the same Huawei Western Europe execs have.
ft.com/content/0411bc…
ft.com/content/0411bc…
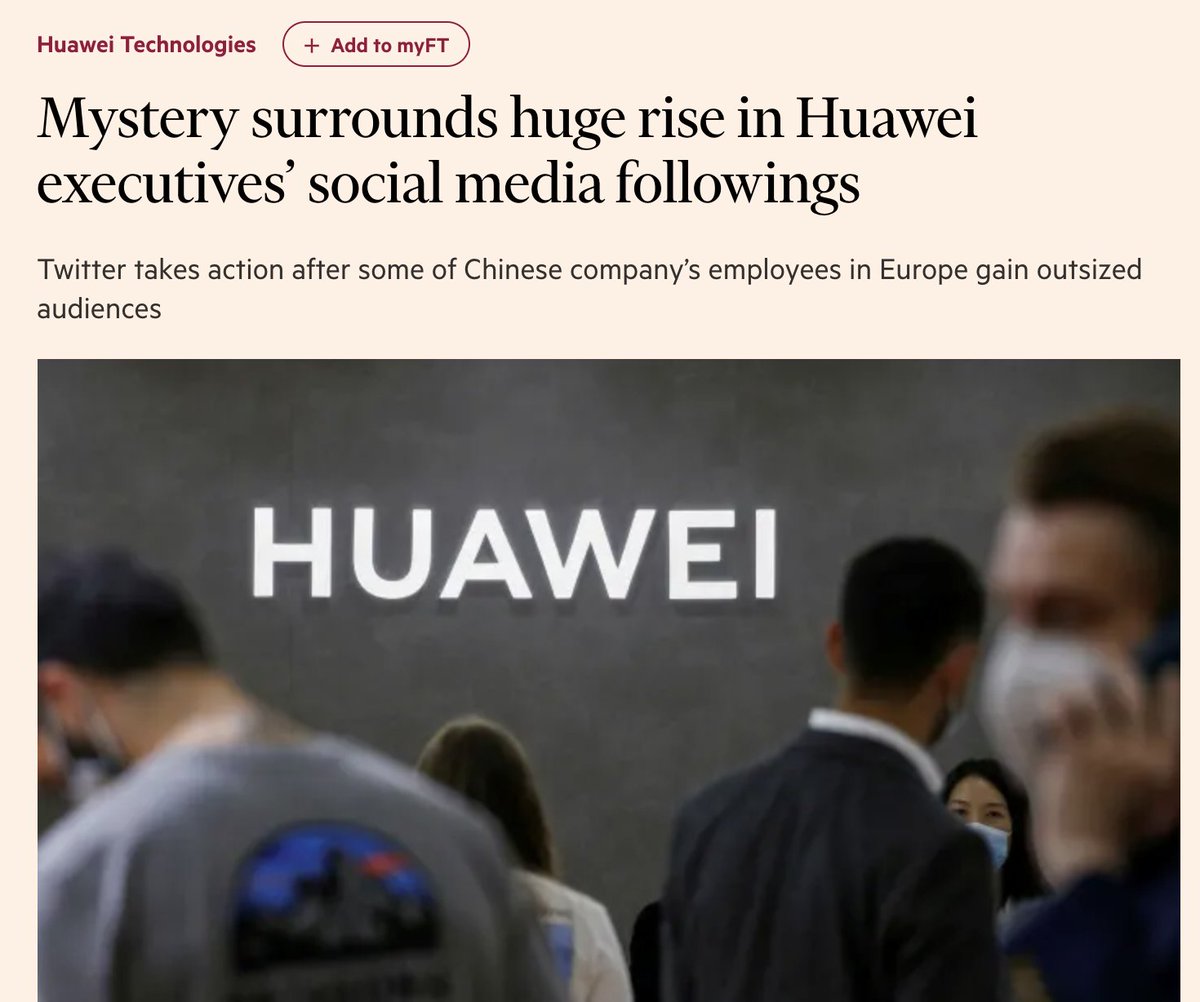
I'll leave it to others to analyse the 800k+ accounts involved in these followings, but one anecdotal sidelight on the fake network of accounts that attacked Belgium: some of its other amplification came from glambots from a network that also boosted Huawei Europe. 

Glambots = automated accounts that use profile pictures taken from glamour shoots and similar sources. 

These particular glambots amplified two things:
1. The fake pro-Huawei accounts;
2. A most likely fake screenshot of a tweet attributed to @bgarlinghouse, offering a crypto giveaway (no such tweet exists in his timeline).
1. The fake pro-Huawei accounts;
2. A most likely fake screenshot of a tweet attributed to @bgarlinghouse, offering a crypto giveaway (no such tweet exists in his timeline).
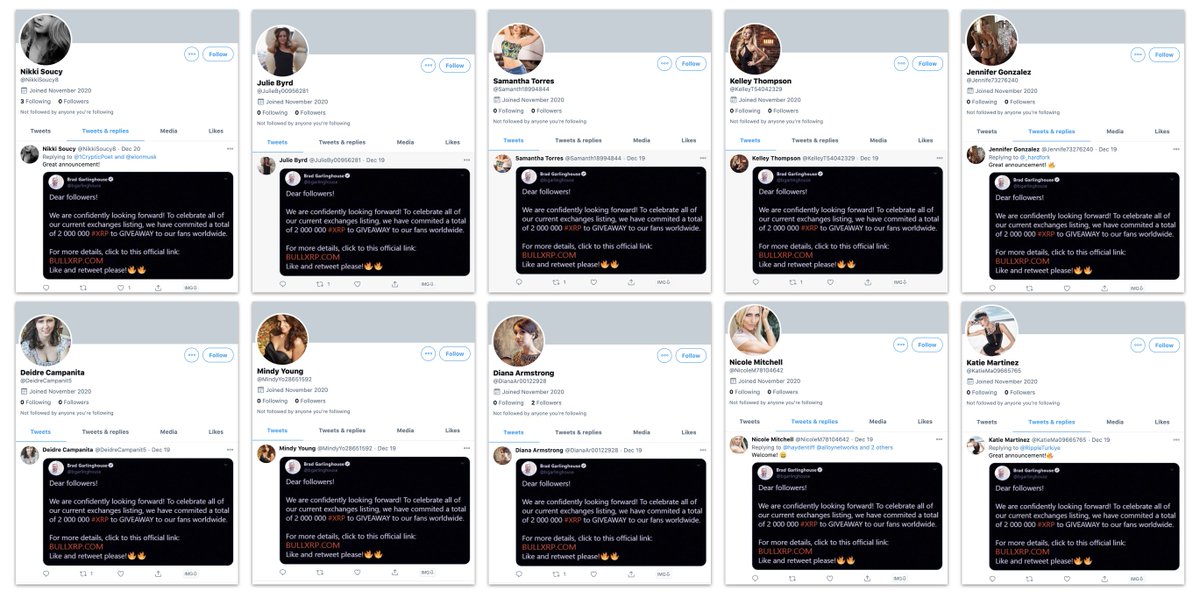
... glambots that tweeted the same screenshot of an alleged tweet from @bgarlinghouse.
The likelihood that this is *not* assets from the same network is, shall we say, remote.
The likelihood that this is *not* assets from the same network is, shall we say, remote.
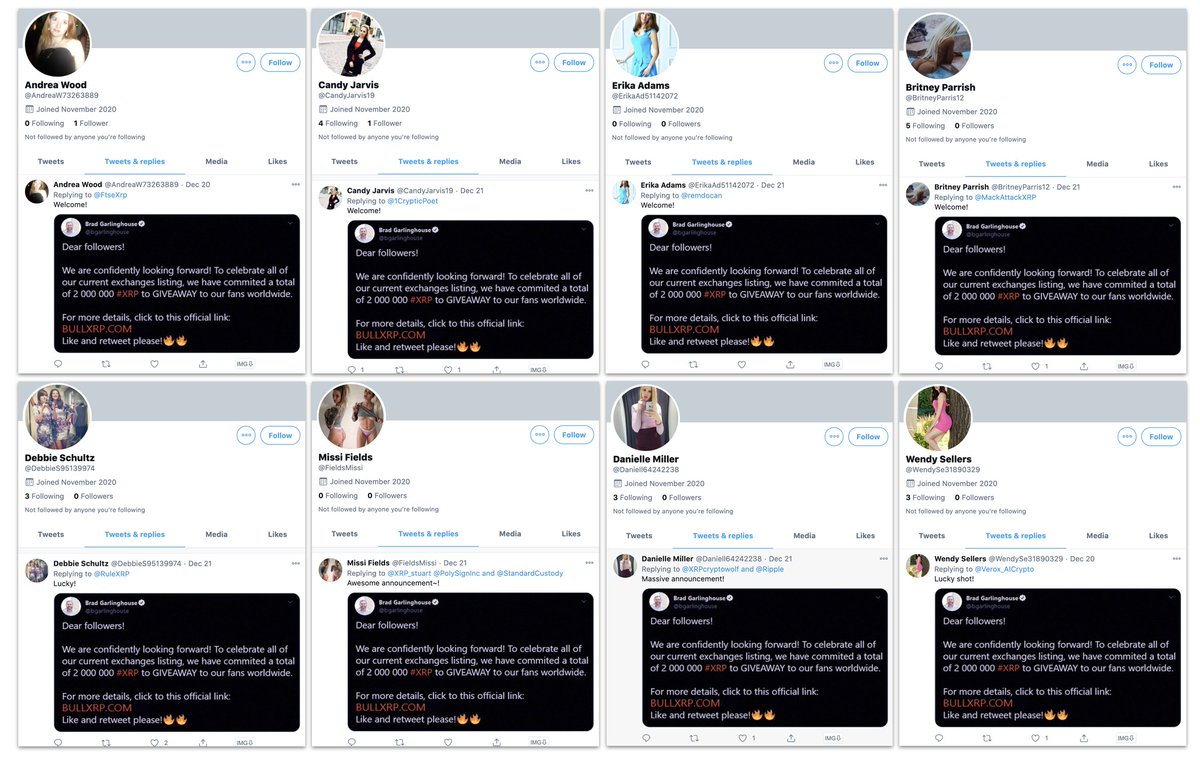
These look like throwaway rental bots, so again, not enough evidence to prove who paid for them.
But inauthentic amplification? Absolutely.
But inauthentic amplification? Absolutely.
• • •
Missing some Tweet in this thread? You can try to
force a refresh