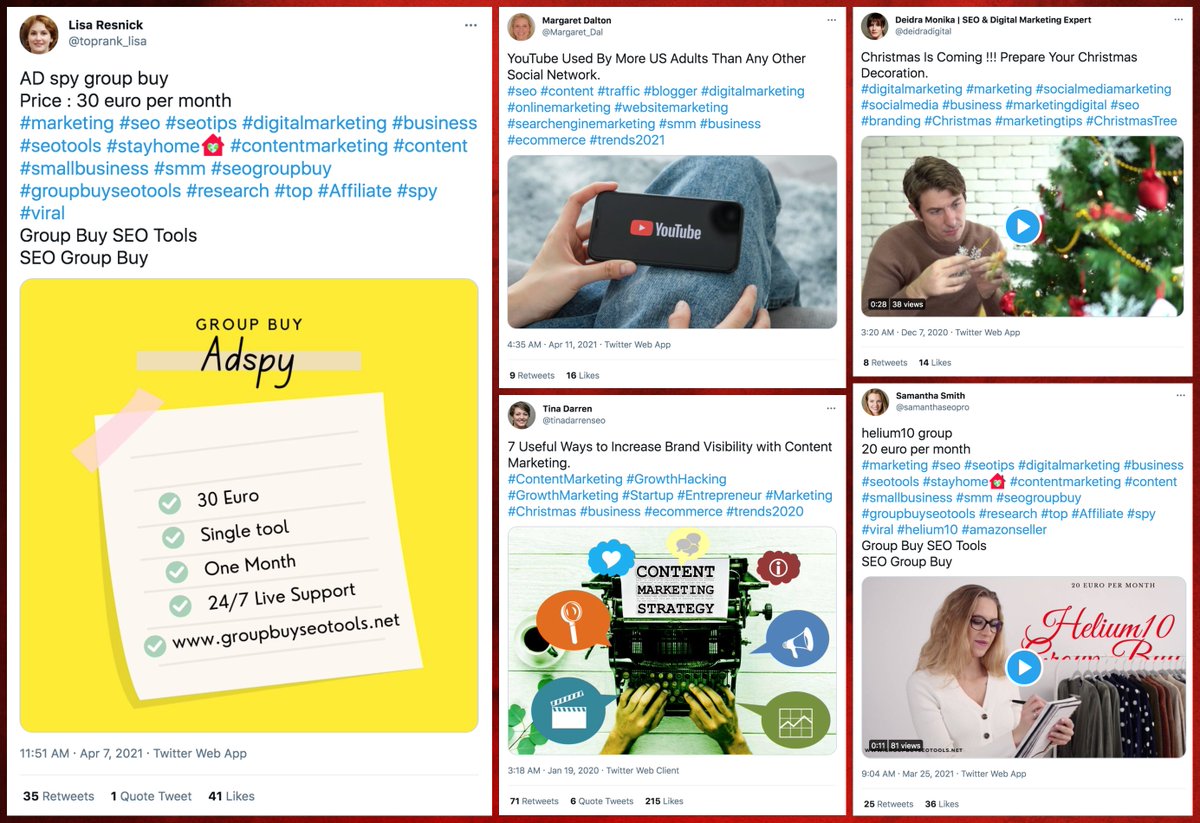
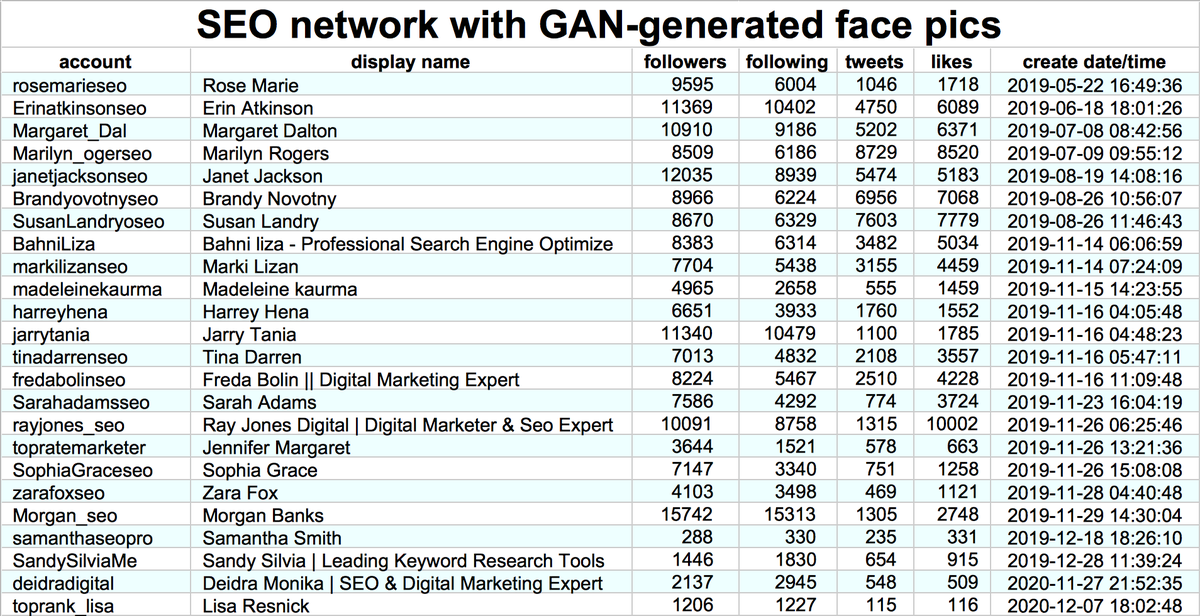
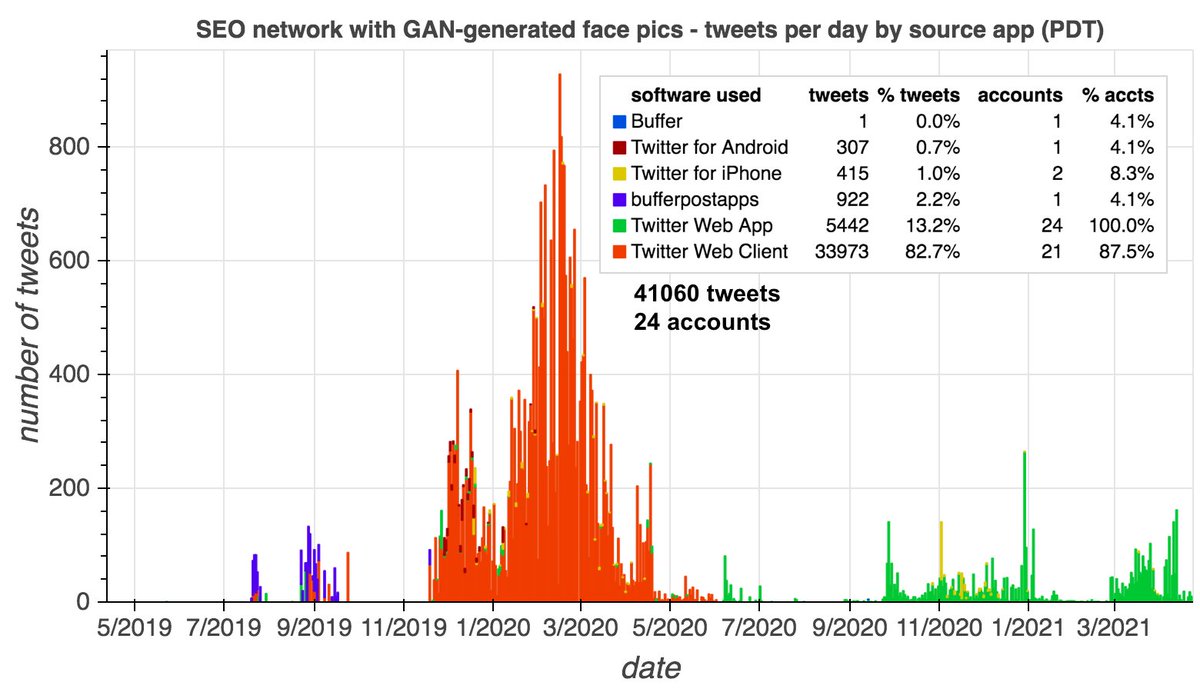
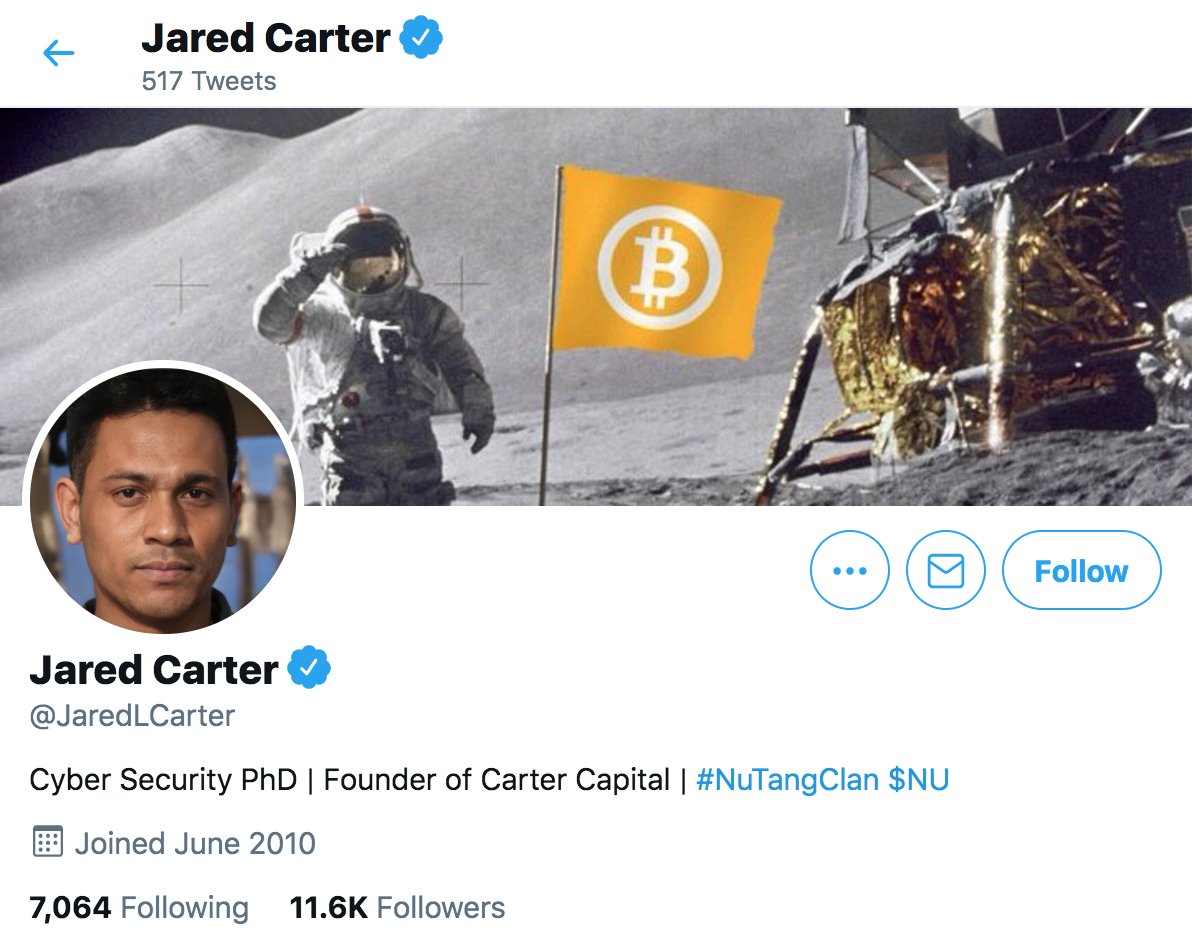
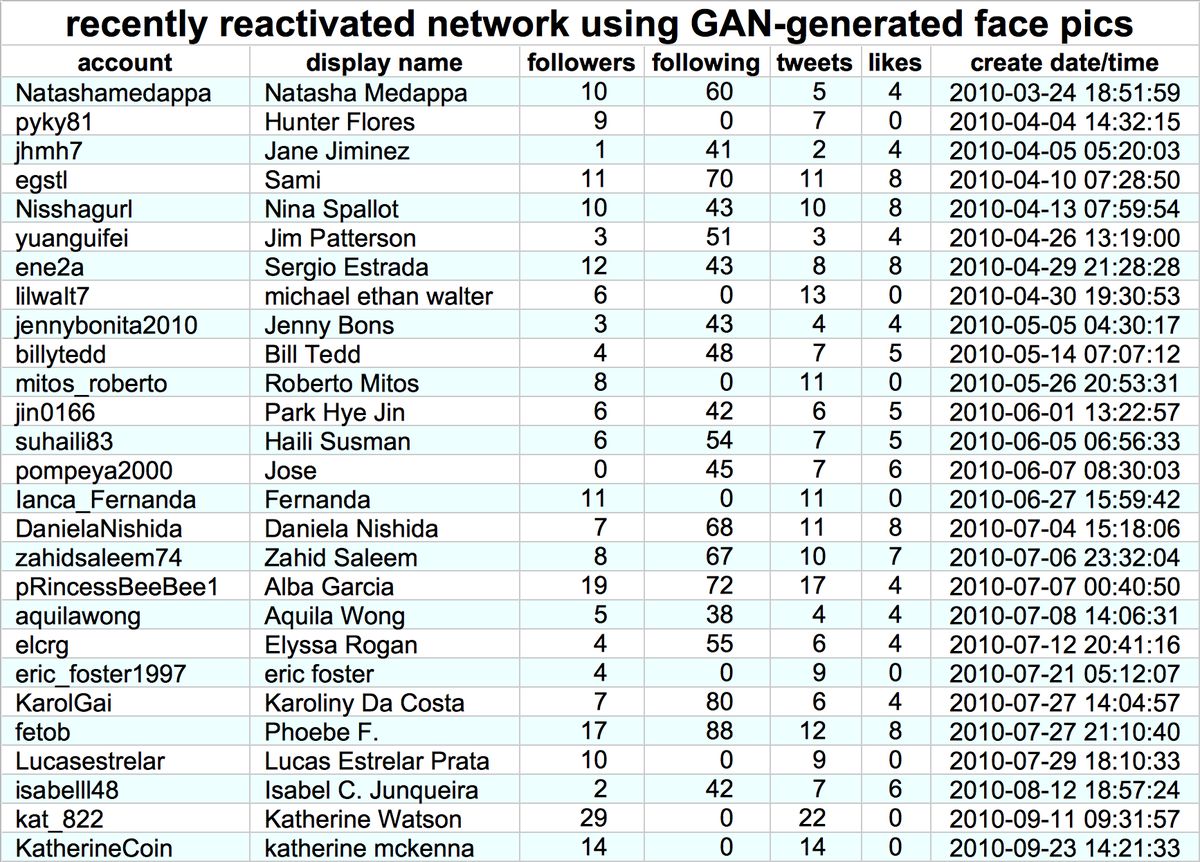
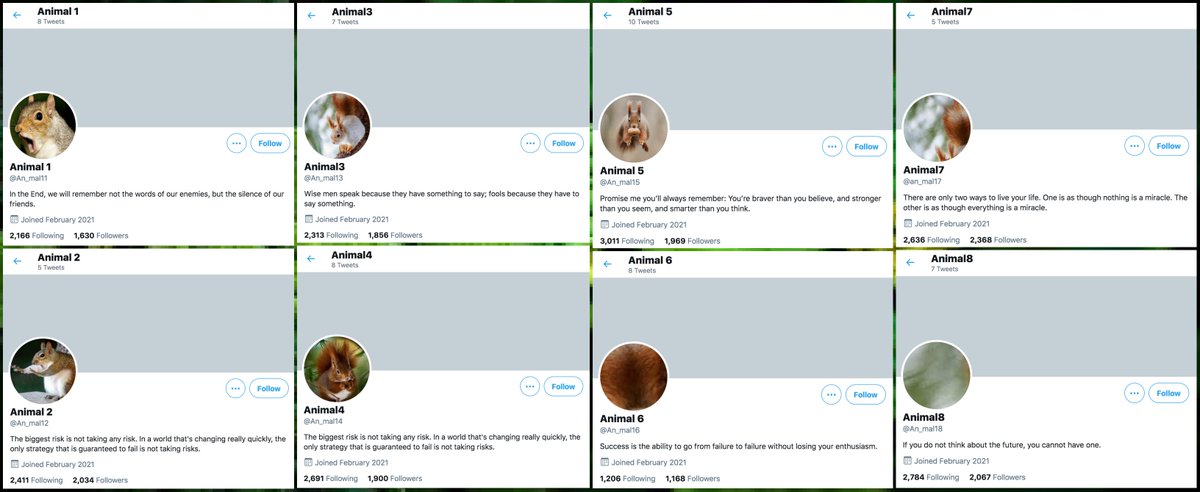
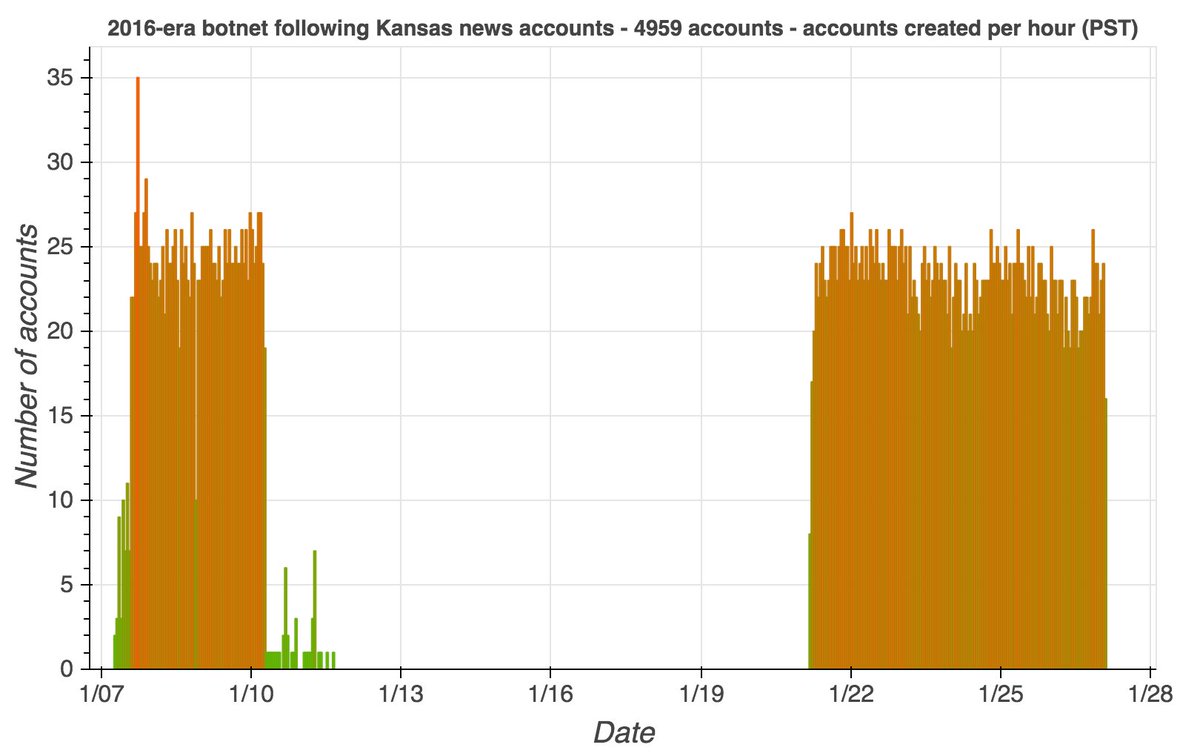
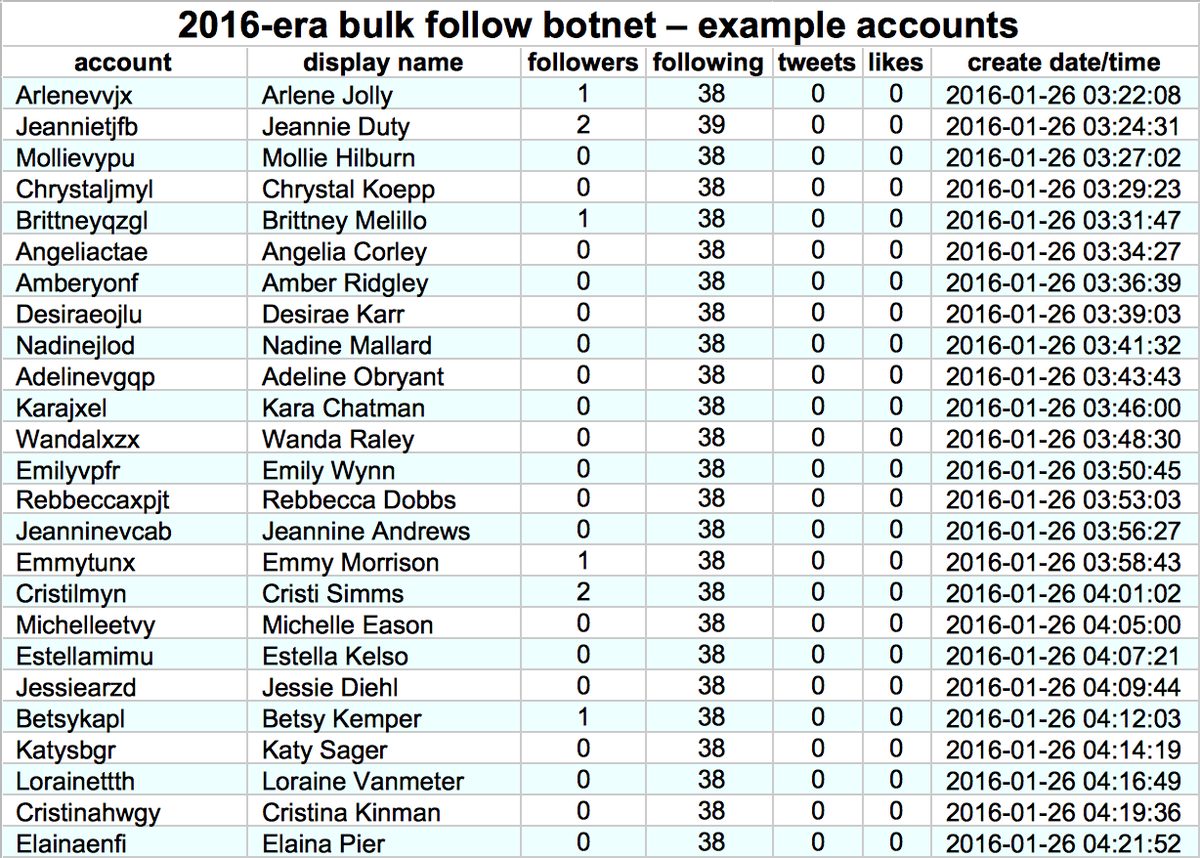
Why did this @serdaribrahimke tweet objecting to Biden's acknowledgement of the #ArmenianGenocide mostly get retweeted by accounts created this month with names ending in 4 digits? #SaturdaySpam
cc: @ZellaQuixote
cc: @ZellaQuixote

Answer: a retweet botnet, consisting of 45 accounts made between April 22nd and April 24th, 2021. All have names ending in four digits, and all (allegedly) send most of their tweets via Twitter for iPad with occasional use of Twitter for Android. 





This botnet has thus far posted no original content whatsoever. All of its 3016 tweets are retweets, almost all of which are of Turkish-language content. 



Who and what does this botnet retweet? It amplifies a variety of Turkish accounts, with content being a mix of political content (primarily objections to Biden's statement about the #ArmenianGenocide), sports, and promotional tweets. 





Despite allegedly tweeting via the Twitter iPad app, we believe these accounts to be largely automated. Most of the network's retweets are meticulously synchronized, with the botnet's first and last retweet of any given tweet coming less than half a second apart. 



Finally, who do the bots in this network follow? All 45 of them follow @imparator3438, whose tweets (mostly sports-themed) they have sometimes amplified. 40 of the 45 bots follow only this account; the other 5 appear to have followed accounts back here and there. 

• • •
Missing some Tweet in this thread? You can try to
force a refresh