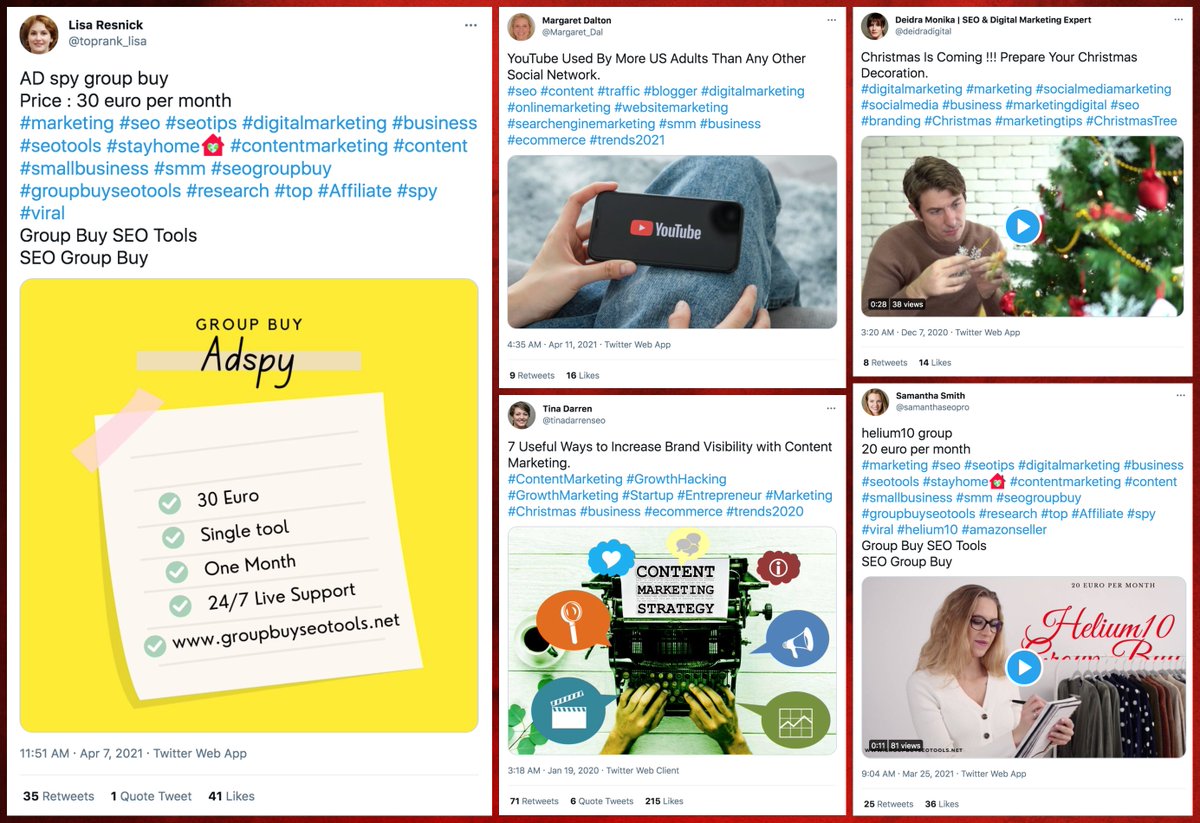
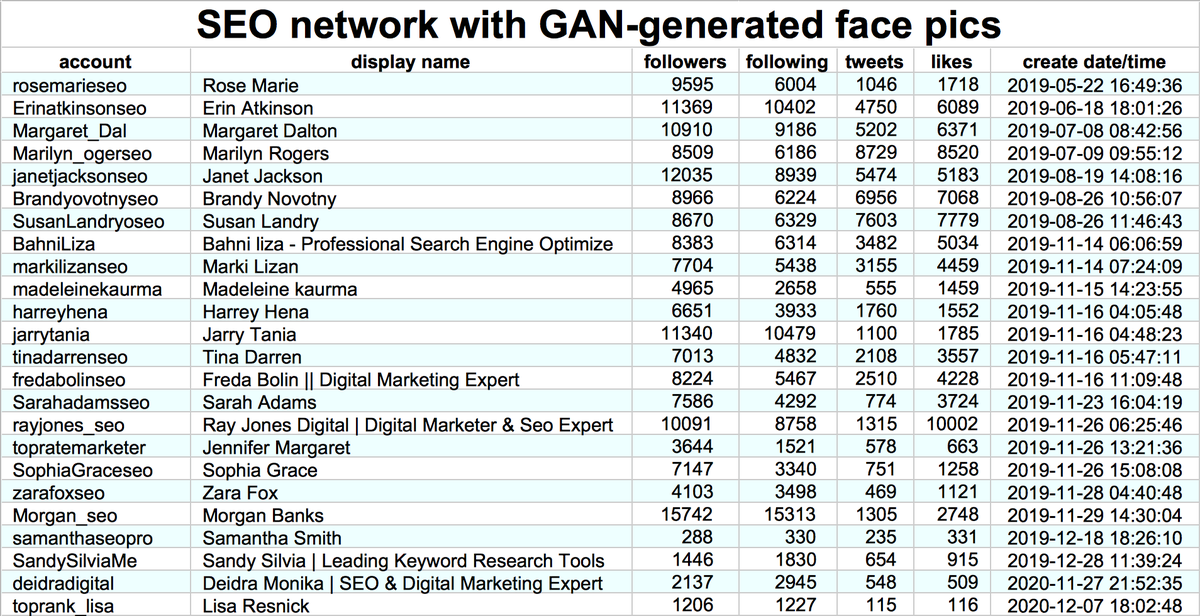
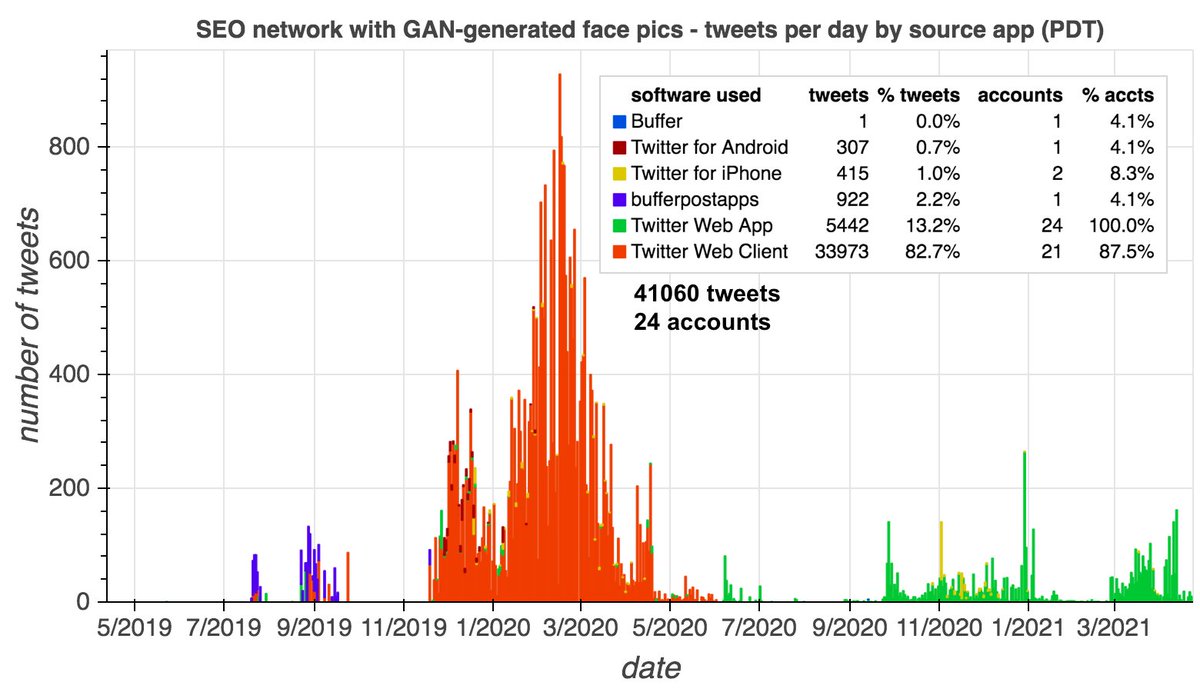
It's a great day to look at an incredibly repetitive pornbot network that tags its tweets with random numbers. #SundaySpam
cc: @ZellaQuixote
cc: @ZellaQuixote

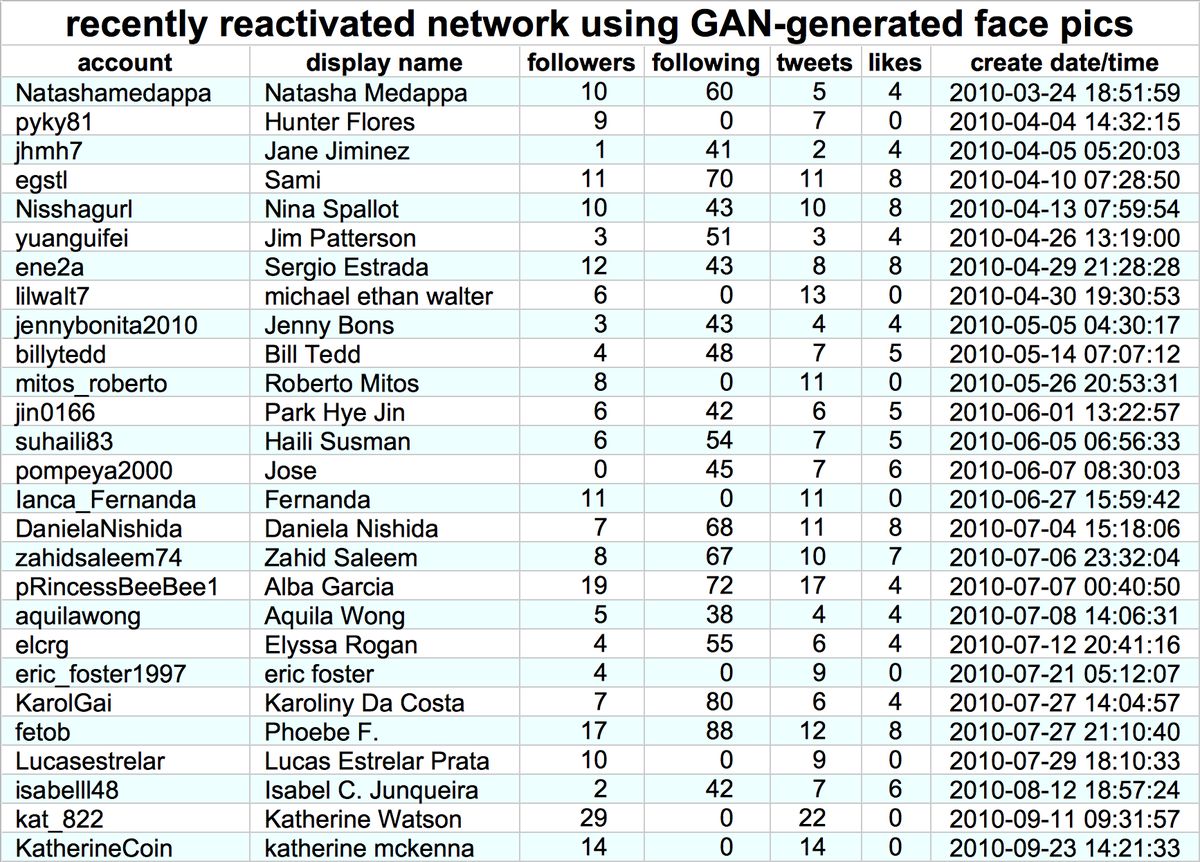
This botnet consists of 99 accounts created between 2010 and 2015 (mostly 2013). All have some variant of "p o r n" as their display name, and all were mostly dormant until mid-April 2021. 




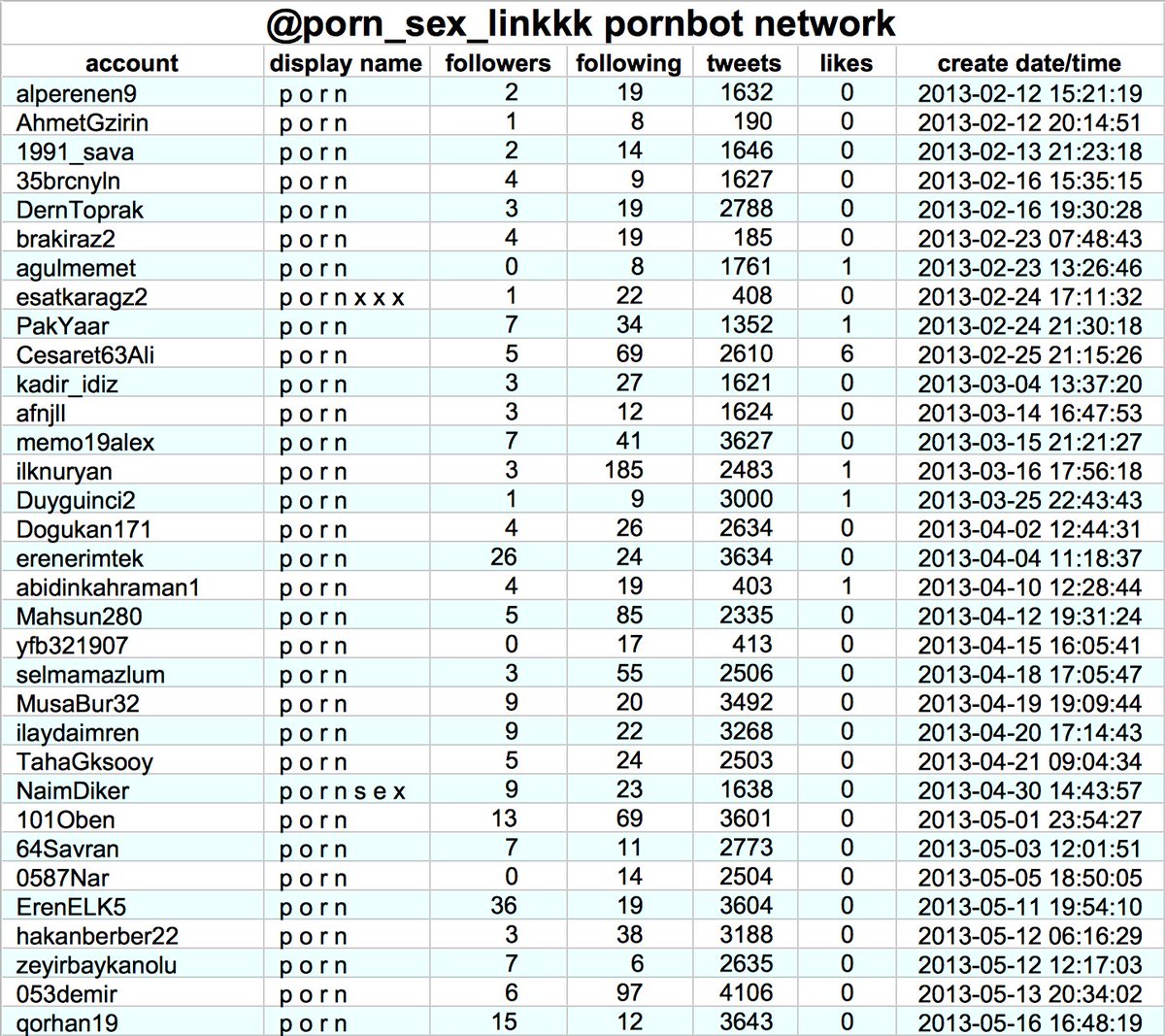


This pornbot network tweets prolifically via TweetDeck (223566 tweets from 99 accounts over the span of just two weeks). The majority of the accounts tweet round-the-clock, with some ceasing operation after a few hours or days of activity. 



Is this botnet using TweetDeck's scheduling feature to accomplish its 24/7 presence? Almost all scheduled TweetDeck tweets are posted within the first second of the minute for which they are scheduled, which isn't true of this botnet's tweets.
https://twitter.com/conspirator0/status/1237193515177857026
The botnet's tweets do have a timing anomaly, however. It began by posting its tweets shortly before the start of each minute, but it is slowly falling behind: on 4/20, it was tweeting ~10 seconds into each minute, and today (4/25) it is tweeting ~23 seconds into each minute. 

What would explain this behavior? A likely explanation is that the botnet operators wrote their own scheduling software that fails to account for some form of latency, and thus slowly falls behind schedule when run for a long period of time.
What does this botnet actually tweet? The tweets are extremely repetitive and consist of single words such as "XXX" or "video" followed by four tags of one of two porn accounts (@/porn_sex_linkkk and @/sex_porn_linkk), followed by a random number. 

The two tagged porn accounts in turn have what appear to be blogspot links that actually redirect to endless signup pages for an obscure "dating site" in multiple languages. The site is likely unsafe and we recommend neither visiting it nor providing it any information. 



• • •
Missing some Tweet in this thread? You can try to
force a refresh