JUST OUT: 9 takedowns in our April CIB report. Primarily domestic ops:
👉Palestine, linked to Fatah;
👉Azerbaijan, linked to individuals associated with defence ministry;
👉Central African Republic, linked to local NGO;
(More in next tweet...)
about.fb.com/news/2021/05/a…
👉Palestine, linked to Fatah;
👉Azerbaijan, linked to individuals associated with defence ministry;
👉Central African Republic, linked to local NGO;
(More in next tweet...)
about.fb.com/news/2021/05/a…
👉Mexico, 1 network linked to local election campaigns, 1 linked to a local politician and a PR firm;
👉Peru, 1 linked to a local party and an advertising firm, 1 linked to a marketing entity;
👉Ukraine, 1 linked to people associated with the Sluha Narodu party,
And...
👉Peru, 1 linked to a local party and an advertising firm, 1 linked to a marketing entity;
👉Ukraine, 1 linked to people associated with the Sluha Narodu party,
And...
👉Ukraine, 1 network linked to individuals and entities sanctioned by the US Treasury — Andrii Derkach, Petro Zhuravel, and Begemot-linked media + political consultants associated with Volodymyr Groysman and Oleg Kulinich.
Deep dive in the report. about.fb.com/news/2021/05/a…
Deep dive in the report. about.fb.com/news/2021/05/a…
A few highlights:
The Palestinian op is fascinating. Linked to Fatah, and it tried most of the tricks in the IO book. They even created fake accounts to pretend to be family members of their main fake accounts.
And tried to hire unwitting freelancers to write for them.
The Palestinian op is fascinating. Linked to Fatah, and it tried most of the tricks in the IO book. They even created fake accounts to pretend to be family members of their main fake accounts.
And tried to hire unwitting freelancers to write for them.

The Azerbaijan case is interesting: the investigation started by looking into 2 off-platform Android apps that tried to trick people into giving up their Instagram credentials. That led to finding this influence operation.
Same actors, but two separate sets of activity.
Same actors, but two separate sets of activity.
The operation linked to Derkach and co. targeted Ukrainian politics, not the US, and it behaved like an influence operation for hire.
Two odd things about this operation.
First, structure. Three teams, each linked with a different politician, but all working together to mislead people. They didn’t just promote “their” politicians, but other ones too, even competitors.
First, structure. Three teams, each linked with a different politician, but all working together to mislead people. They didn’t just promote “their” politicians, but other ones too, even competitors.
That’s typical for operations that rent out their amplification infra.
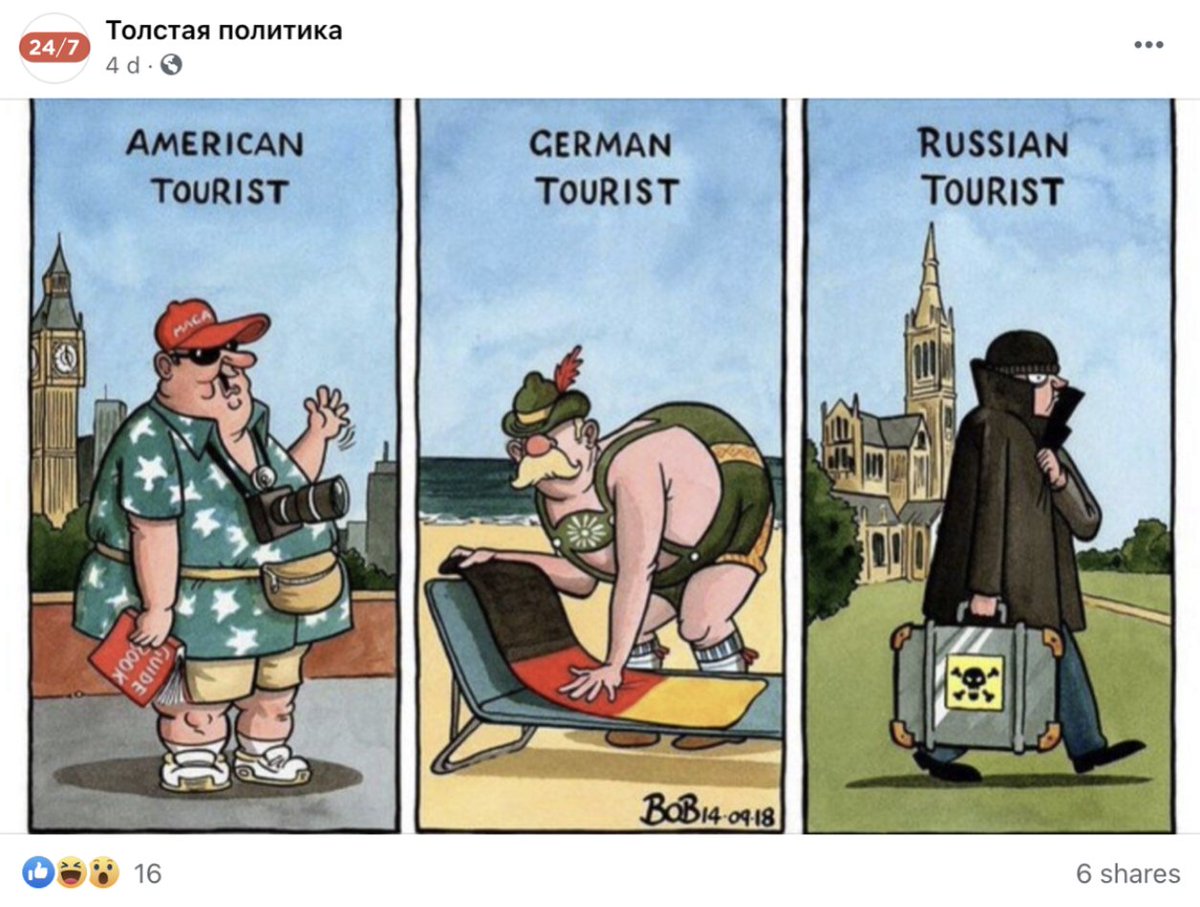
The other odd thing was its anti-Russia content.
A consistent drumbeat of articles and memes - most of them copied from elsewhere, like this copy of @bobscartoons.
A consistent drumbeat of articles and memes - most of them copied from elsewhere, like this copy of @bobscartoons.
We’ve seen a fair few influence ops from Ukraine in the last couple of years, almost all targeting domestic audiences. But we’ve also seen a growing wave of public analysis and exposure of them.
OSINT community, you rock.
OSINT community, you rock.
• • •
Missing some Tweet in this thread? You can try to
force a refresh