A NEW ransomware enters the fray: Epsilon Red
A bare-bones ransomware offloads most of its functionality to a cache of PowerShell scripts...
(a thread) 1/13
A bare-bones ransomware offloads most of its functionality to a cache of PowerShell scripts...
(a thread) 1/13

Sophos analysts uncovered a new ransomware written in the Go programming language that calls itself Epsilon Red.
The malware was delivered as the final executable payload in a hand-controlled attack in which every other early-stage component was a PowerShell script. 2/13
The malware was delivered as the final executable payload in a hand-controlled attack in which every other early-stage component was a PowerShell script. 2/13
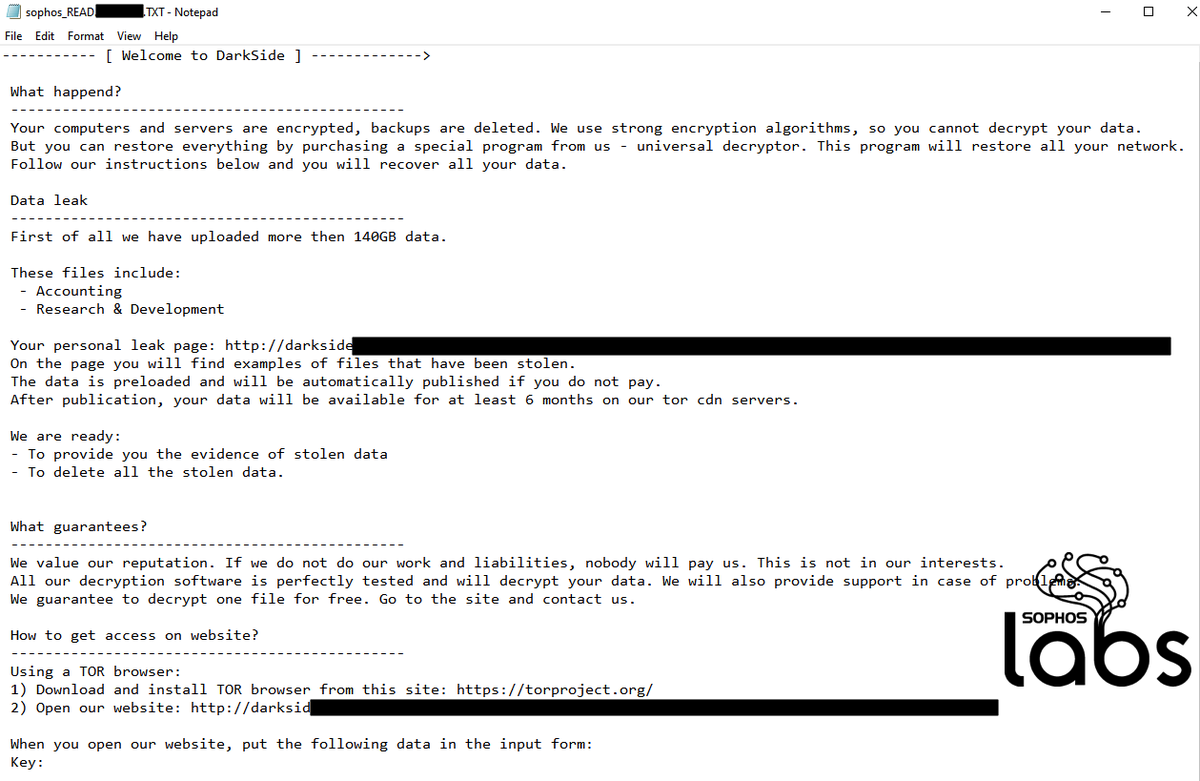
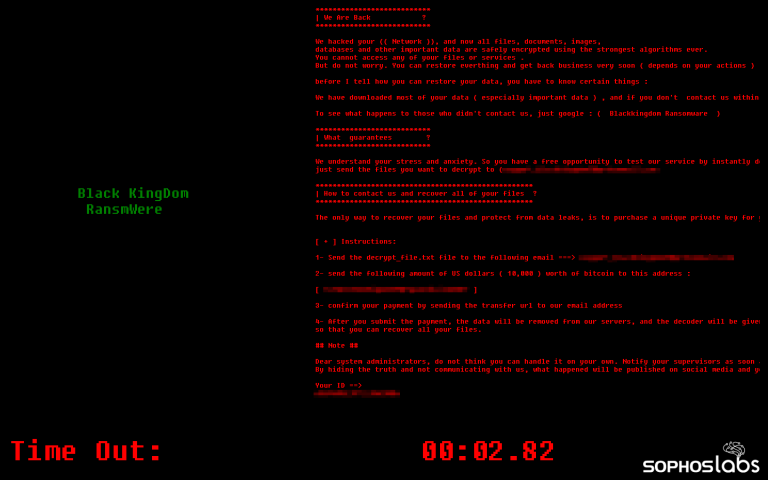
While the name and tooling were unique to this attacker, the ransom note left behind resembles the note left behind by REvil ransomware, but adds a few minor grammatical corrections.
There were no other obvious similarities between the Epsilon Red ransomware and REvil. 3/13
There were no other obvious similarities between the Epsilon Red ransomware and REvil. 3/13
It appears that an enterprise Microsoft Exchange server was the initial point of entry into the enterprise network.
It isn’t clear whether this was enabled by the ProxyLogon exploit or another vulnerability, but it seems likely that the root cause was an unpatched server. 4/13
It isn’t clear whether this was enabled by the ProxyLogon exploit or another vulnerability, but it seems likely that the root cause was an unpatched server. 4/13
From that machine, the attackers used WMI to install other software onto machines inside the network that they could reach from the Exchange server. 5/13
The name Epsilon Red is a reference to pop culture.
The character Epsilon Red was a relatively obscure adversary of some of the X-Men in the Marvel extended universe, a “super soldier” alleged to be of Russian origin, sporting four mechanical tentacles and a bad attitude. 6/13
The character Epsilon Red was a relatively obscure adversary of some of the X-Men in the Marvel extended universe, a “super soldier” alleged to be of Russian origin, sporting four mechanical tentacles and a bad attitude. 6/13

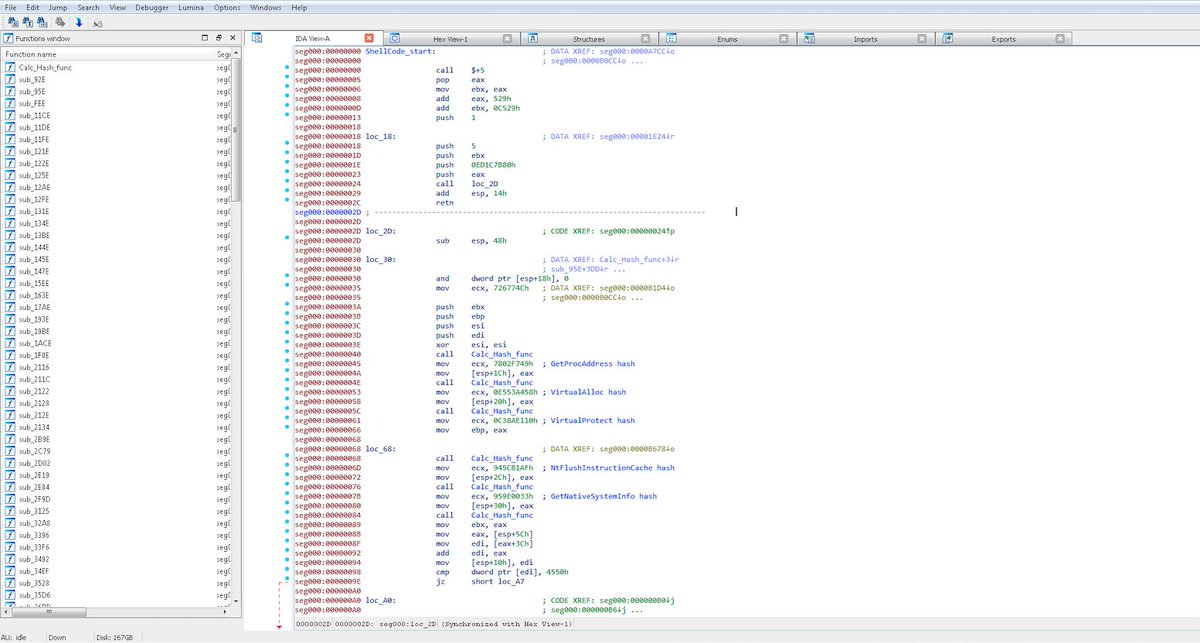
The ransomware itself, called RED.exe, is a 64-bit Windows executable programmed in the Go language, compiled using a tool called MinGW, and packed with a modified version of the runtime packer UPX. 7/13 

Strangely enough, the ransom note closely resembles the note used by REvil.
But where the REvil note is typically riddled with errors, the note delivered by Epsilon Red has gone through a few edits to make its text more readable to an audience of native English speakers. 8/13
But where the REvil note is typically riddled with errors, the note delivered by Epsilon Red has gone through a few edits to make its text more readable to an audience of native English speakers. 8/13

Detections:
Sophos endpoint products, such as Intercept X, will behaviorally detect several of the actions taken by the PowerShell scripts or the ransomware payload. The act of attempting to encrypt files is blocked by the CryptoGuard feature. 9/13
Sophos endpoint products, such as Intercept X, will behaviorally detect several of the actions taken by the PowerShell scripts or the ransomware payload. The act of attempting to encrypt files is blocked by the CryptoGuard feature. 9/13
As the ingress point for this attack appears to have been an Exchange server vulnerable to the ProxyLogon exploit chain, customers are urged to patch internet-facing Exchange servers as quickly as possible. 10/13
Sophos endpoint products can protect Exchange servers as well as Domain Controllers or workstations.
Indicators of compromise for this threat can be found on the SophosLabs Github. 11/13
Indicators of compromise for this threat can be found on the SophosLabs Github. 11/13
Thank you to @AnandAjjan, Richard Cohen, Fraser Howard, Elida Leite, @markloman, Andrew Ludgate, @AltShiftPrtScn, Nirav Parekh, & @GaborSzappanos for producing a comprehensive analysis of the threat & improving our ability to detect & block malware like Epsilon Red in the future.
• • •
Missing some Tweet in this thread? You can try to
force a refresh