NEW: AMSI bypasses remain tricks of the malware trade
Malware developers continue to try to sabotage or evade Microsoft’s Anti-Malware Software Interface in “fileless” and living-off-land attacks...
(a thread) 1/13
Malware developers continue to try to sabotage or evade Microsoft’s Anti-Malware Software Interface in “fileless” and living-off-land attacks...
(a thread) 1/13

As Windows 10 and the latest generation of Windows Server platforms have risen to prominence, malware developers and malicious actors have increasingly aimed to evade detection by taking out those platforms’ anti-malware traffic cop: Microsoft’s Antimalware Scan Interface. 2/13
AMSI, introduced in 2015, provides a way for software to talk to security products, requesting scans of files, memory, or streams for malicious payloads in a vendor-agnostic way. 3/13
AMSI is a very attractive target for malware developers.
Almost since the day AMSI was introduced, attackers (and security researchers) have created tools to attempt to bypass or disable AMSI. 4/13
Almost since the day AMSI was introduced, attackers (and security researchers) have created tools to attempt to bypass or disable AMSI. 4/13
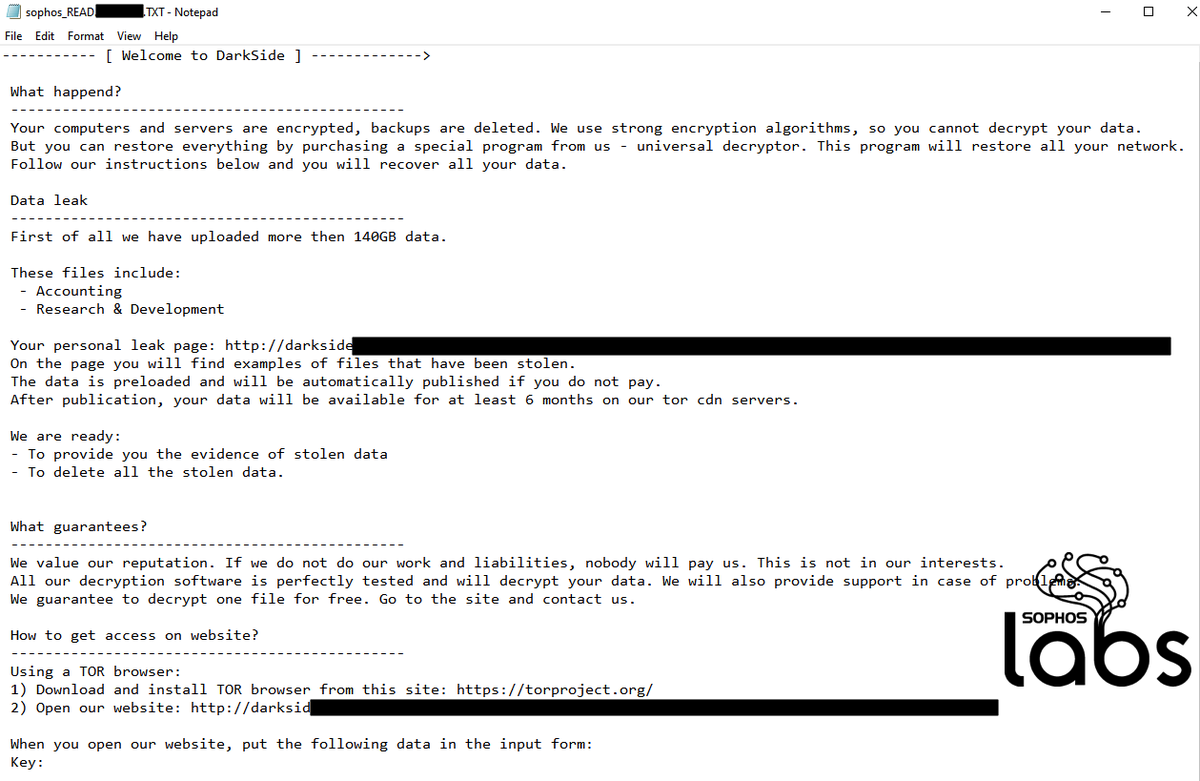
In our report, we examine the most commonly encountered AMSI bypass methods in use, and examine how they are used by malware we’ve observed to attempt to evade defenses on Windows systems. 5/13
In May of 2016, PowerShell hacker Matt Graeber published a one-line AMSI evasion in a tweet.
This bypass is now widely detected and blocked as malicious content (as any 5-year-old public exploit should be).
However, malware actors still use versions of it... 6/13
This bypass is now widely detected and blocked as malicious content (as any 5-year-old public exploit should be).
However, malware actors still use versions of it... 6/13
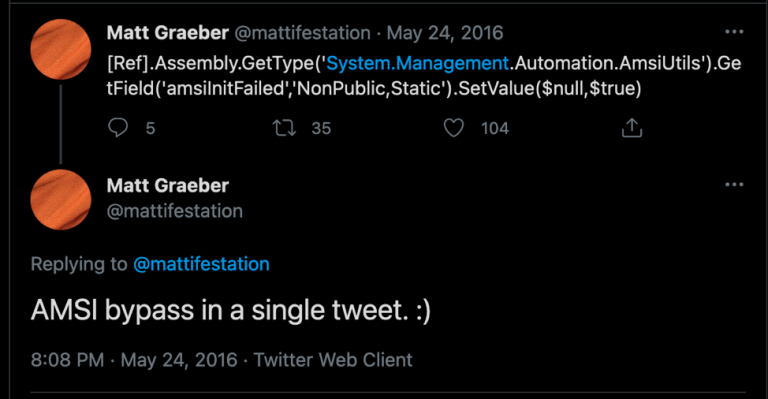
... And we detected a recent use of the same bypass that connected to a remote server to obtain a PowerShell-based malware downloader.
This appears to have been part of a Proxy Logon-based attack that attempted to load a Meterpreter backdoor DLL from a server in Russia. 7/13
This appears to have been part of a Proxy Logon-based attack that attempted to load a Meterpreter backdoor DLL from a server in Russia. 7/13
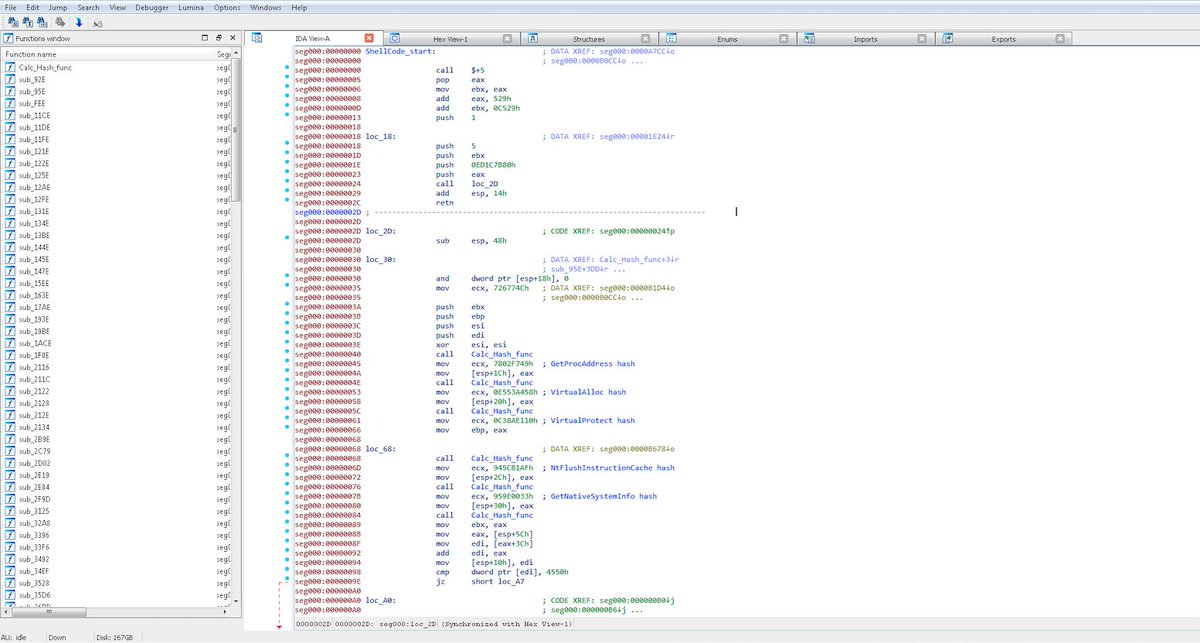
While manipulation of the properties of the AmsiUtils interface is still a common method of attempting AMSI bypass, over 98 percent of the bypass attempts we see in recent telemetry focus on a different approach: tampering with the code of the AMSI library itself. 8/13
Another well-worn method of bypassing AMSI is based on a method revealed by Cornelis de Plaa in 2016 that fools PowerShell into loading a counterfeit version of amsi.dll.
It’s fairly straightforward in its original implementation: 9/13
It’s fairly straightforward in its original implementation: 9/13

Other techniques of evading AMSI generally involve either downgrading scripting engines to versions from before AMSI was available or otherwise staying away from processes that interact with AMSI altogether. 10/13
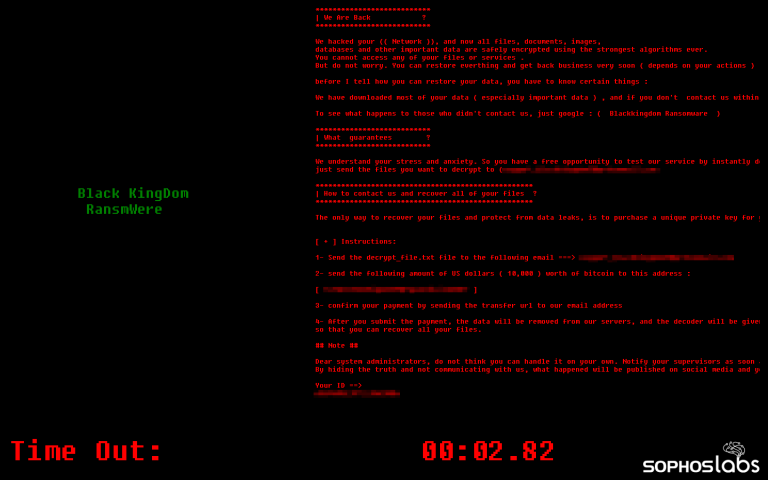
Given how prevalent LOL tactics have become, particularly in ransomware operator intrusions, AMSI can play a particularly important role in keeping Windows 10 and Windows Server systems from being compromised. 11/13
A defense in depth, leveraging a blend of detections at the endpoint and on the network, is critical in blunting many of these intrusions before they can do damage. 12/13
Read more from @thepacketrat: news.sophos.com/en-us/2021/06/…
And thank you to Rajesh Nataraj and Michael Wood for their contributions to this report.
13/13
And thank you to Rajesh Nataraj and Michael Wood for their contributions to this report.
13/13
• • •
Missing some Tweet in this thread? You can try to
force a refresh