NEW 👇
BlackMatter ransomware emerges from the shadow of DarkSide
1/12
BlackMatter ransomware emerges from the shadow of DarkSide
1/12
In late July, a new RaaS appeared on the scene.
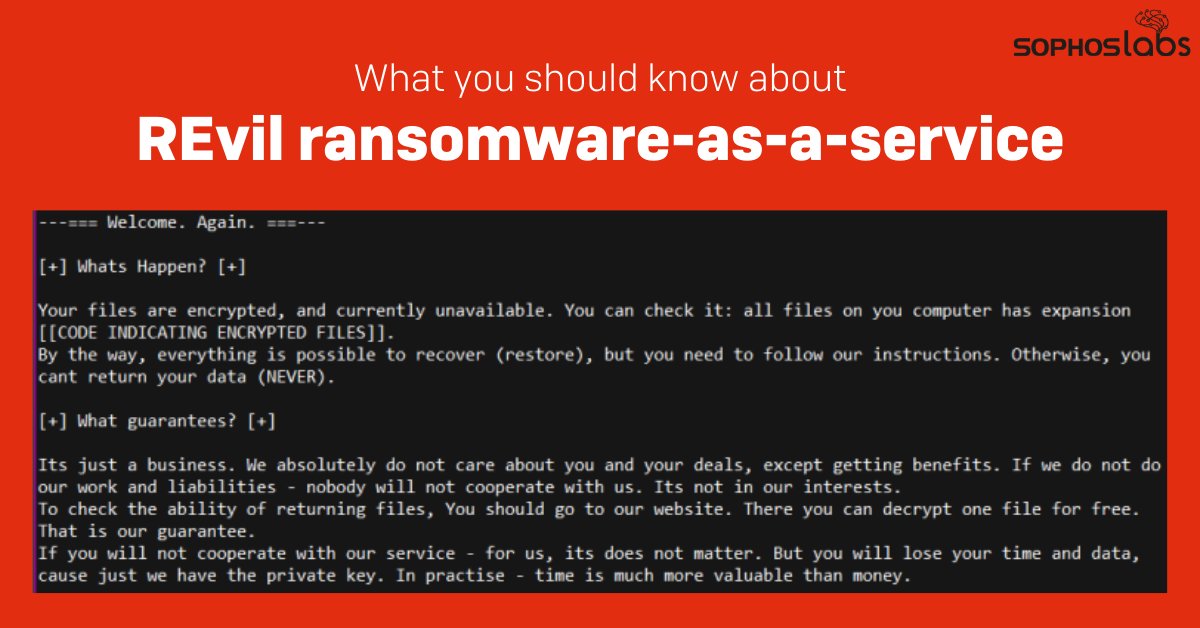
Calling itself BlackMatter, the ransomware claims to fill the void left by DarkSide and REvil – adopting the best tools and techniques from each of them, as well as from the still-active LockBit 2.0. 2/12
Calling itself BlackMatter, the ransomware claims to fill the void left by DarkSide and REvil – adopting the best tools and techniques from each of them, as well as from the still-active LockBit 2.0. 2/12

We decided to take a closer look at the malware and the claims being made by the new adversary to see what’s really going on... 3/12
The Sophos research is based on a sample of the BlackMatter ransomware, with the SHA-256 hash: 22D7D67C3AF10B1A37F277EBABE2D1EB4FD25AFBD6437D4377400E148BCC08D6.
The operators behind the BlackMatter RaaS have established a presence on the dark web. 4/12
The operators behind the BlackMatter RaaS have established a presence on the dark web. 4/12

The list of sectors and entities this threat actor says it will not attack reflect the recent global incidents involving DarkSide (Colonial Pipeline) and REvil (Kaseya) ransomware, which drew widespread and probably unwelcome attention. 5/12
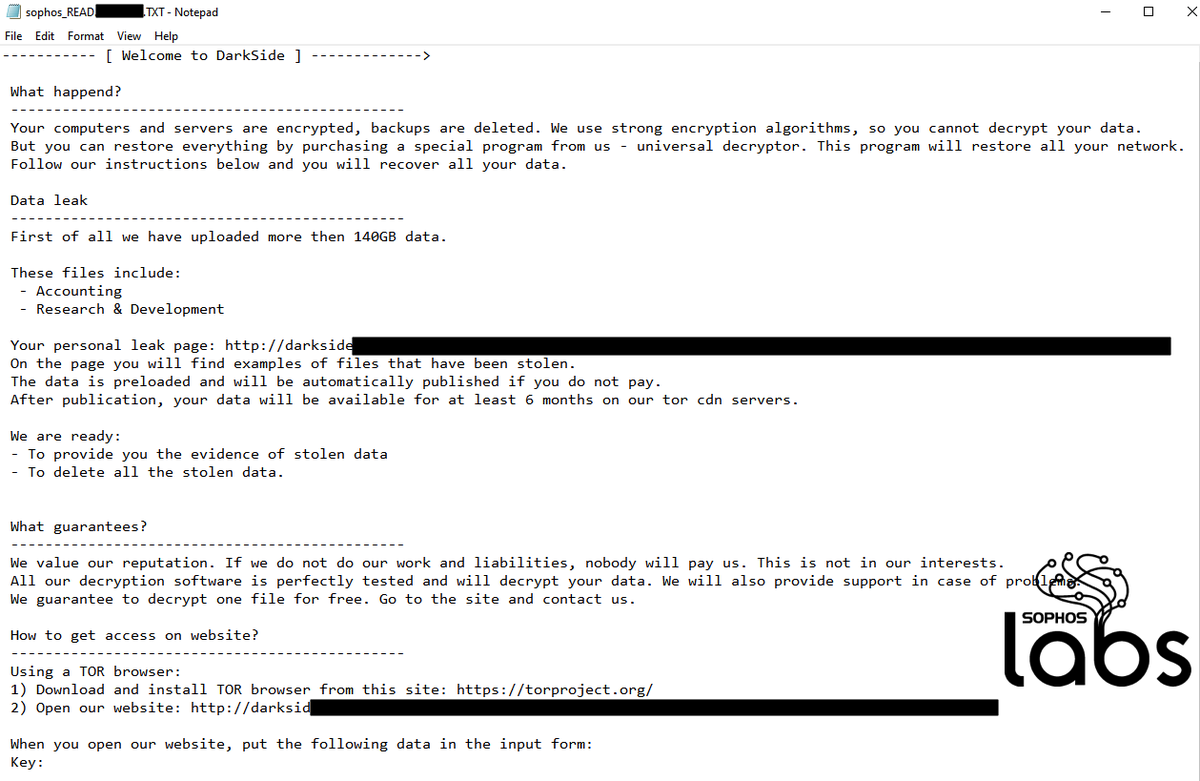
The operators behind BlackMatter claim that their ransomware incorporates the best features of DarkSide, REvil, and LockBit 2.0 ransomware. They also say that while they are closely acquainted with the Darkside operators, they are not the same people. 6/12 

To better understand the potential relationships between the ransomware groups, SophosLabs has analyzed a BlackMatter ransomware sample, and uncovered a number of technical similarities with DarkSide and the other ransomware families that are worth noting. 7/12 

To summarize our findings:
▪️The claims made recently by an alleged BlackMatter representative regarding its feature set are largely true. 8/12
▪️The claims made recently by an alleged BlackMatter representative regarding its feature set are largely true. 8/12
▪️There are a number of factors that suggest a connection between BlackMatter and DarkSide. However, this is not simply a rebranding from one to another. Malware analysis shows that while there are similarities with DarkSide ransomware, the code is not identical. 9/12
▪️In the hands of an experienced attacker, this ransomware can cause a lot of damage without triggering many alarms. It's important for defenders to promptly investigate endpoint protection alerts as they can be an indication of an imminent attack. 10/12
Note: Sophos Machine Learning automatically detects BlackMatter ransomware.
Read the full story from @markloman: news.sophos.com/en-us/2021/08/… 11/12
Read the full story from @markloman: news.sophos.com/en-us/2021/08/… 11/12
We would also like to acknowledge SophosLabs researchers @AnandAjjan and @thepacketrat, and Rapid Response manager @AltShiftPrtScn for their contributions to this report. 12/12
• • •
Missing some Tweet in this thread? You can try to
force a refresh