NEW insights ☠️
Relentless REvil, revealed: RaaS as variable as the criminals who use it
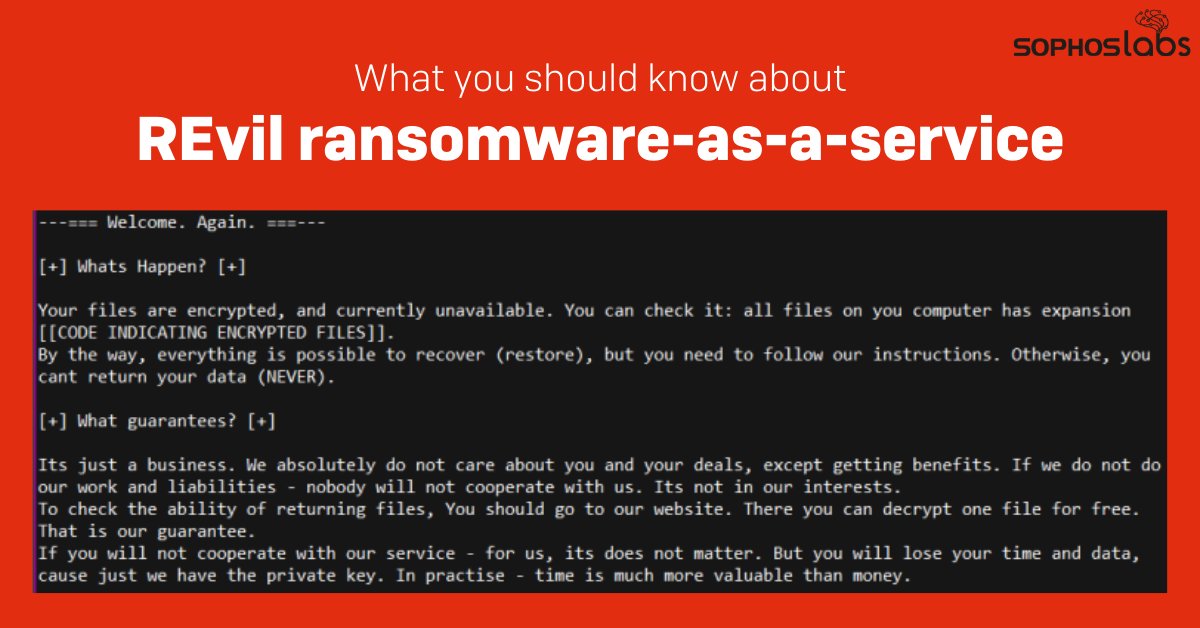
No two criminal groups deploy the ransomware-as-a-service (RaaS), also known as Sodinokibi, in exactly the same way...
(a thread) 1/11
Relentless REvil, revealed: RaaS as variable as the criminals who use it
No two criminal groups deploy the ransomware-as-a-service (RaaS), also known as Sodinokibi, in exactly the same way...
(a thread) 1/11
As attacks involving RaaS malware, including REvil, increasingly have generated attention, we wanted to pull together a common body of our knowledge about the ransomware itself, and the variety we observe in attack methods employed by the criminals who lease the software. 2/11
We've also reviewed reports from Sophos Rapid Response about attacks involving Sodinokibi/REvil where the MTR team were hired to provide incident response and cleanup. From these detailed analyses, we were able to develop a picture of a common malware being deployed. 3/11
Typical attack phases:
1. Penetration and initial access
2. Credential harvesting and privilege escalation
3. Tilling the field
4. Deployment of the ransomware
4/11
1. Penetration and initial access
2. Credential harvesting and privilege escalation
3. Tilling the field
4. Deployment of the ransomware
4/11
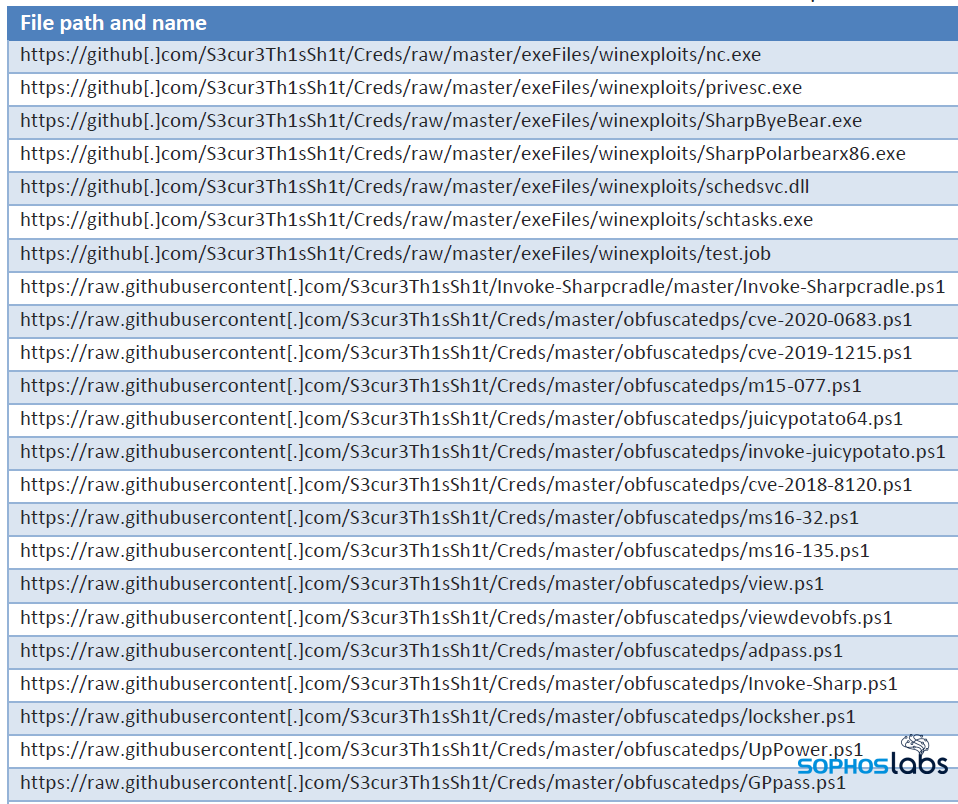
1. Common initial access methods used by criminals who attacked using Sodinokibi/REvil:
▫️ Brute-force attacks
▫️ Abuse of previously-obtained credentials/access
▫️ Piggybacking as a payload from other malware present on the target’s network.
5/11
▫️ Brute-force attacks
▫️ Abuse of previously-obtained credentials/access
▫️ Piggybacking as a payload from other malware present on the target’s network.
5/11

2. Credential harvesting and privilege escalation
If ransomware threat actors haven’t bought a stolen or phished credential, they’ll often quietly monitor the network where the computer on which they gained an initial foothold is located. 6/11
If ransomware threat actors haven’t bought a stolen or phished credential, they’ll often quietly monitor the network where the computer on which they gained an initial foothold is located. 6/11
3. Tilling the field
The attackers establish a list of internal targets, give themselves domain admin privileges, and use those privileges to shut down or otherwise hobble anything that might impede their attack. 7/11
The attackers establish a list of internal targets, give themselves domain admin privileges, and use those privileges to shut down or otherwise hobble anything that might impede their attack. 7/11

4. The final insult: deployment
Attackers have launched the ransomware payload using a wide variety of methods... Sodinokibi/REvil has a few additional options that its operators may take advantage of by launching the malware with special command flags. 8/11
Attackers have launched the ransomware payload using a wide variety of methods... Sodinokibi/REvil has a few additional options that its operators may take advantage of by launching the malware with special command flags. 8/11

(Some) guidance for IT professionals:
▫️ Monitor and respond to alerts
▫️ Use strong passwords
▫️ Use Multi Factor Authentication (MFA)
▫️ Lock down accessible services
▫️ Segmentation and Zero-Trust
▫️ Inventory your assets and accounts
▫️ Patch everything
9/11
▫️ Monitor and respond to alerts
▫️ Use strong passwords
▫️ Use Multi Factor Authentication (MFA)
▫️ Lock down accessible services
▫️ Segmentation and Zero-Trust
▫️ Inventory your assets and accounts
▫️ Patch everything
9/11
Sophos products detect various forms of Sodinokibi/REvil as Troj/Sodino-*, Mem/Sodino-*, and HPMal/Sodino-A.
Users of Sophos LiveDiscover can run SQL queries to interrogate telemetry from devices on their managed network, and hunt for unusual or unexpected behavior. 10/11
Users of Sophos LiveDiscover can run SQL queries to interrogate telemetry from devices on their managed network, and hunt for unusual or unexpected behavior. 10/11

Read more from @threatresearch: news.sophos.com/en-us/2021/06/…
And thank you to SophosLabs researchers @AnandAjjan, Hajnalka Kope, @markloman, and Rapid Response manager @AltShiftPrtScn who contributed to our understanding of REvil attacks and the malware’s behavior.
11/11
And thank you to SophosLabs researchers @AnandAjjan, Hajnalka Kope, @markloman, and Rapid Response manager @AltShiftPrtScn who contributed to our understanding of REvil attacks and the malware’s behavior.
11/11
• • •
Missing some Tweet in this thread? You can try to
force a refresh